What is Ping Identity?
Ping Identity is an enterprise Identity Management Ping and access control system that assists enterprises in the process of protecting and managing the identities of their users across a wide variety of applications and devices.
Customers are provided with an experience known as ping identity SSO (Single Sign-on), which enables them to access a variety of applications via a centralized and user-friendly platform.
In addition to this, it gives administrators the ability to control who can access their applications and resources.
Ping Cloud Identity is an identity and access management (IAM) system that is hosted in the cloud and provides users with the ability to gain safe, unified access to apps hosted both on-premises and in the cloud.
Users only need to log in once to gain access to all of their applications; they are not required to re-enter their credentials at each subsequent step.
Introduction to Ping Identity
Ping Identity OIDC also provides administrators with extensive control and management tools for user access. Administrators can create new user accounts, edit existing ones, delete user accounts, assign users roles and permissions, and restrict access to applications. In addition to this, they can monitor user activity, create customized access controls and constraints, and identify any Ping identity security risks.

In addition to providing a single sign-on (SSO) experience, it can also be used to authenticate users through the usage of Ping Identity multi-factor authentication. gaining access to software to use it. The utilization of hardware tokens, one-time passwords, or biometric authentication is all viable methods for accomplishing this goal.
Ping Identity gives businesses a platform that is dependable and risk-free for regulating and managing user identities and access. Users can also take advantage of a Ping Identity single sign-on experience, which makes it much simpler for them to access the programs they use.

It offers administrators the ability to build up precise access controls, limit access to their applications and resources, and identify any security risks.
Overview of Ping Identity: What Is Ping Identity?

Ping Identity is a firm that specializes in identity and access management (IAM), and the company’s product, PingFederate, is a federated identity management (FIM) solution that is enterprise-grade and built on open standards.
By integrating standards-based identity technologies such as WS-Trust and SAML, PingFederate enables businesses to provide authentication and single sign-on (SSO) for mobile apps, sites, and devices.
The acronym “identity single sign-on,” or “SSO,” refers to a system that gives users access to a variety of applications with only a single set of login credentials. Users are able to safely connect in too many applications with a single username and password rather than having to remember several credentials for each application.
It also makes the authentication procedure simpler for users by requiring them to remember only one set of credentials rather than multiple sets. In addition, since users only need to log in once, identity SSO can give enterprises significant insights into user behaviour and preferences. These insights can help organisations better serve their customers.
This may be accomplished through the use of Ping identity configuration. PingFederate can be installed in a variety of configurations to meet the needs of businesses of all sizes, regardless of whether those businesses use a centralized ping identity authentication system or a federated network to maintain user identities. PingFederate can be installed in any of these configurations to meet the needs of businesses.
Authenticating an individuals identify is a process that verifies their claimed identification to others. This is often accomplished through the use of several distinct procedures, including biometrics, passwords, tokens, and several other types of identification.
Authenticating a person’s identity is a security measure that ensures only those who have been granted permission can access a restricted resource or piece of information. Authentication of identification helps people protect themselves from identity theft and other fraudulent acts.

Ping Identity Ldap
Lightweight Directory Access Protocol, or LDAP for short, is a protocol for accessing and managing directory services including authentication and authorisation information. LDAP stands for “Lightweight Directory Access Protocol.” A local area network (LAN) or the internet are both examples of networks that utilise this set of standards and protocols to facilitate the transfer of data from one node to another. LDAP is used for managing user accounts, passwords, access control and authorization, and other information that is connected to identity management. It is also used for authenticating users, which is a part of identity management.
Definition of ping identity? or Define ping identity?
Ping Identity is and identity and access management (IAM) company that helps organizations securely access applications on-premises and in the cloud and protect themselves from advanced cyber threats.
It offers identity and access management solutions that help companies connect users securely to the right technology resources while protecting their data and making sure they meet enterprise and regulatory requirements.
Ping Identity is a system for identity and access management that lets businesses secure, control, and monitor access to web applications, web services, and Ping Identity API (application programming interfaces). Users can access a variety of applications with a single set of credentials thanks to the capacity of single sign-on (SSO) as well as multi-factor authentication (MFA) that is provided by it. User provisioning, password management, and identity governance are some of the other services it offers.
What does ping identity do and what is ping identity used for?
Ping Identity is an identity and access management software used to securely manage and protect digital identities.
It is used to protect customer data, maintain secure access to resources, and securely manage customer accounts.
It also allows customers to securely access their accounts from any device, anywhere in the world.
Ping Identity offers its clients a complete range of identity and access management tools. These products give customers the ability to safely access apps, services, and data from any device, regardless of their location.
Their solutions allow for single sign-on, offer federated identity management, give safe access to Ping Identity Api Security, and connect with both cloud-based and locally hosted-apps.
Ping Identity oauth also provides a variety of identity governance and administration solutions, which may assist in the management of user access, give secure authentication, and safeguard client data.
Ping Identity is a solution for identity and access management (IAM), which enables businesses of any size to implement single sign-on (SSO), multi-factor authentication (MFA), user provisioning, identity governance, and access management.
It gives businesses the ability to safeguard their data and apps and maintain control over who has access to what. The protection of users and the data they store is facilitated by the use of these technologies, which also make it simpler for businesses to satisfy compliance obligations.
Moreover, Ping Identity provides a variety of services, including identity advice, installation, and maintenance. This makes it easier for businesses to establish and maintain identity and access management systems that are compliant and secure.
In addition, the solutions offered by Ping Identity are designed to connect seamlessly with the apps and authentication systems already in place.
How Does Ping identity Work?
Ping Identity works by using a process called authentication to verify a user’s identity. Authentication is the process of confirming that a user is whom they say they are.
While entering into their online accounts, users using a security system known as Ping identity mfa (multi-factor authentication ) are required to present two or more pieces of proof (sometimes referred to as “factors”) in order to have their identities confirmed.
The criteria can include anything from something you know (such as a password or security question) to something you have (such as a phone or key fob) to something you are (such as a fingerprint or iris scan) (like a biometric scan). Multiple Factor Authentication (MFA) provides an extra layer of protection to assist in preventing unwanted access to sensitive information.
Ping Identity uses a combination of multi-factor authentication methods such as passwords, one-time passwords, biometrics, and mobile devices to ensure that only the right person has access to the system.
When a user attempts to log in, Ping Identity will check their credentials against a database to make sure they are whom they say they are.
If the credentials match, the user will be granted access; if not, they will be denied. Additionally, Ping Identity can be used to provide secure access to web applications and services, ensuring that only the right person has access to the right information.
Why ping identity & what are the Benefits of ping identity?
Ping Identity is a leading provider of identity and access management solutions that lets customers protect their digital identities and use apps on any device, anywhere, at any time. With a secure and unified approach to identity and access management, Ping Identity lets organizations confidently speed up their business while protecting the digital identities of their customers, employees, and partners.
Benefits of ping identity?
Centralize Identity Management
Stop giving out passwords that aren’t safe
Reduce the chances of unauthorized access and accounts that have been abandoned.
Protect user information and stop account takeovers.
Ping identity integration link all types of identities to the apps and resources they need.
Make the user experience as smooth as possible.
Advantages Of Ping Identity
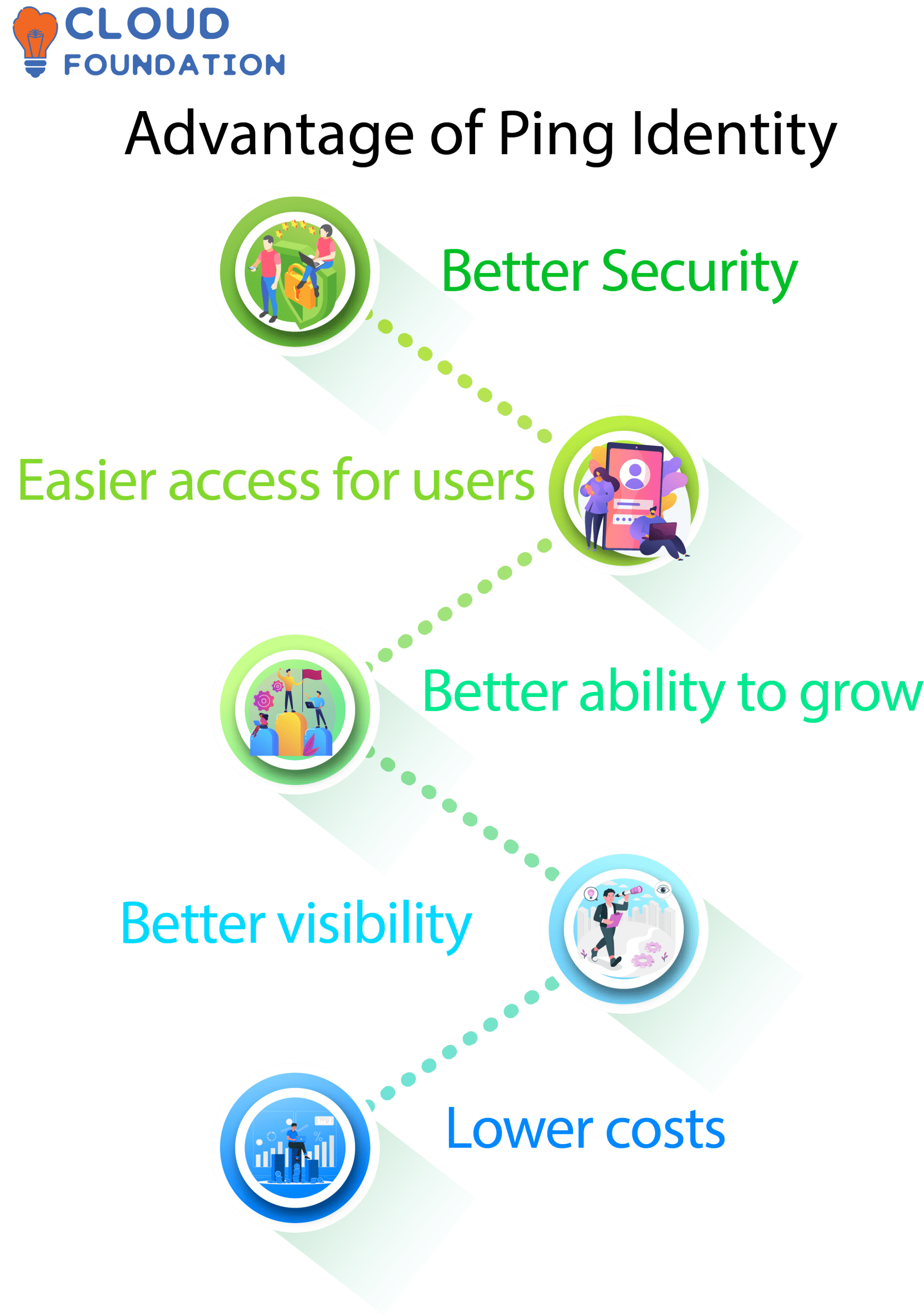
Better security: Ping Identity has a secure authentication process that can help keep your information and data safe. It can also add an extra layer of protection against threats and people who are out to harm.
Easier access for users: Ping Identity is made so that users can get to their accounts and data with just one click. This can make it easier for users to find the resources they need and give them a better overall experience.
Better ability to grow: Ping Identity is made to grow quickly and can handle a large number of users. It can also be used to connect multiple identity providers, which makes user accounts easier to manage.
Better visibility: Ping Identity makes it easier for administrators to see what users are doing and how they are getting in. This makes it easier to spot suspicious activity or attacks.
Lower costs: Ping Identity can make it cheaper to manage user accounts and authentication systems and to give people access to resources.

Features Of Ping Identity
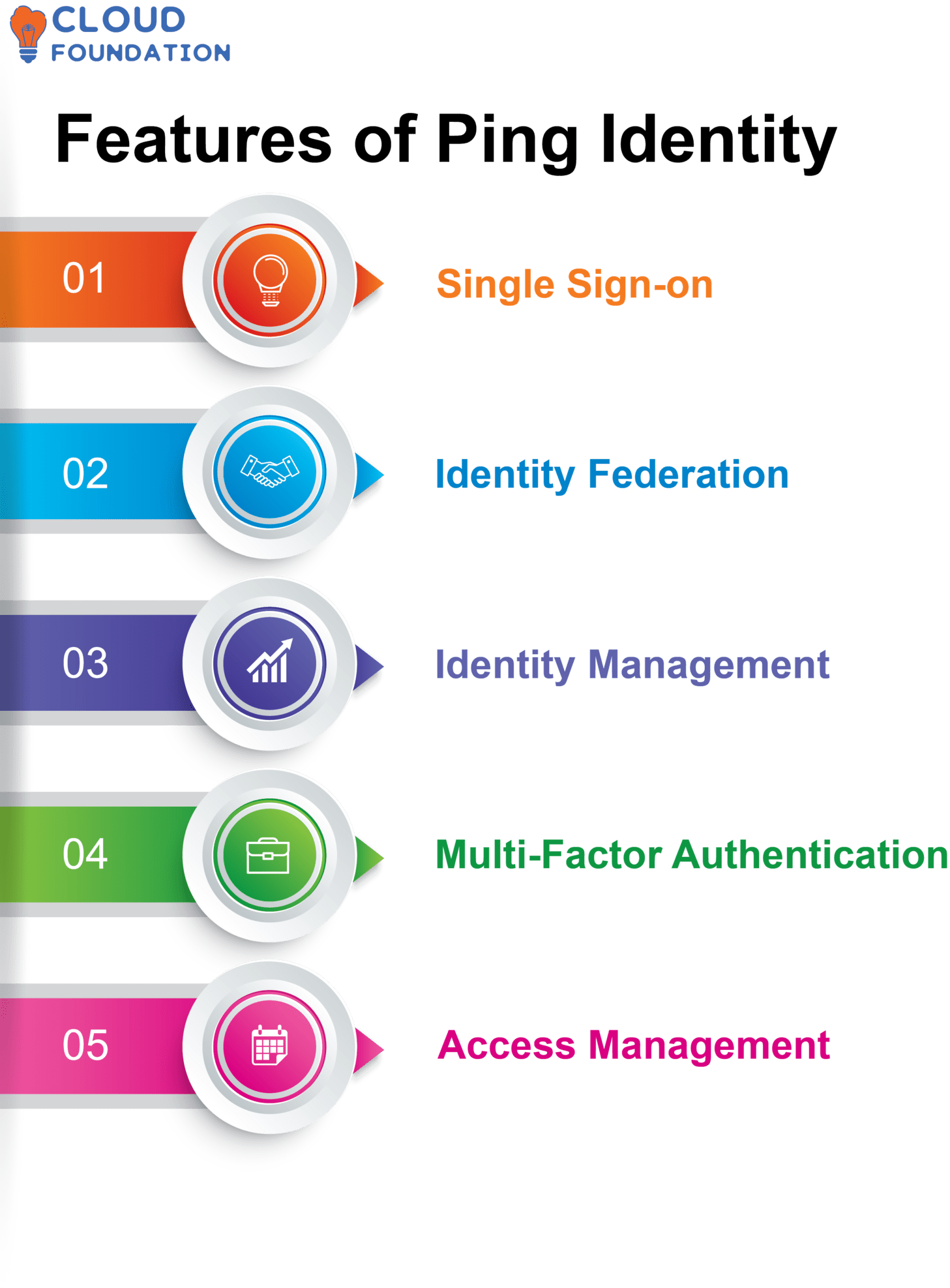
Single Sign-On (SSO): Gives users secure access to the applications they need to do their jobs, but they only have to sign in once.
Ping Identity Federation: This helps organizations securely share identity and access information with partners, customers, and suppliers.
Identity Management: This lets organizations make user identities and access control policies, manage them, use them, and keep them safe.
Multi-Factor Authentication: This makes applications safer by requiring more than one way to prove who you are before you can use them.
Access Management: This lets companies decide who can use which apps and data on what devices.
Ping Identity Oauth2: Ping Identity OAuth is an authorization protocol that enables a third-party application to obtain limited access to a user’s protected resources, such as an API, without the user having to reveal their credentials in order to do so.
Ping Identity Partners
Identity partners are companies or other types of organisations that can be called upon to verify a user’s claimed identity. Companies such as Google, Microsoft, and Apple are some examples of identification partners. Other examples of identity partners include government agencies such as the Department of Motor Vehicles, financial institutions such as banks, and other businesses.
The information that identification partners offer regarding a person’s identity, which may include the person’s name, address, age, and other characteristics, can then be used to authenticate the identity of a user. The provision of safe authentication as well as access to services and apps is impossible without the participation of identity partners.
What are the best ways to learn Ping Identity?
Several online courses are available for ping identity to help you learn about it. These include workday basic training videos and Ping identity blogs.
Ping Identity training video is available to you so that you can refer them whenever you need.


Shreshtha
Author
Life is a long lesson in humility – Life is either a daring adventure or nothing at all.