Saviynt Tutorial
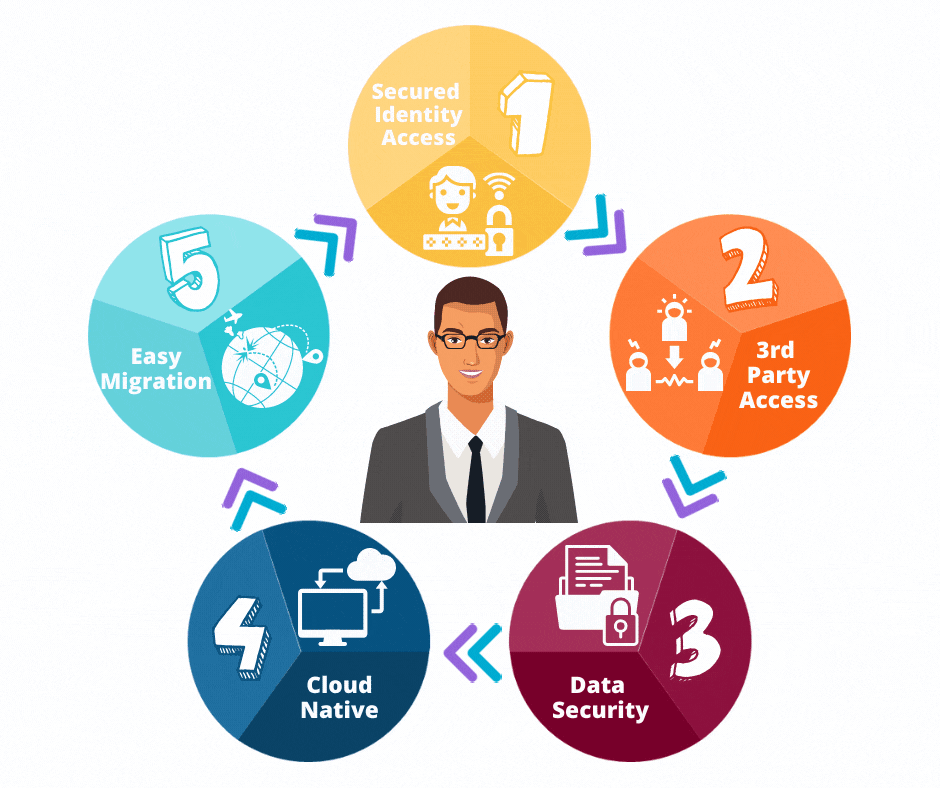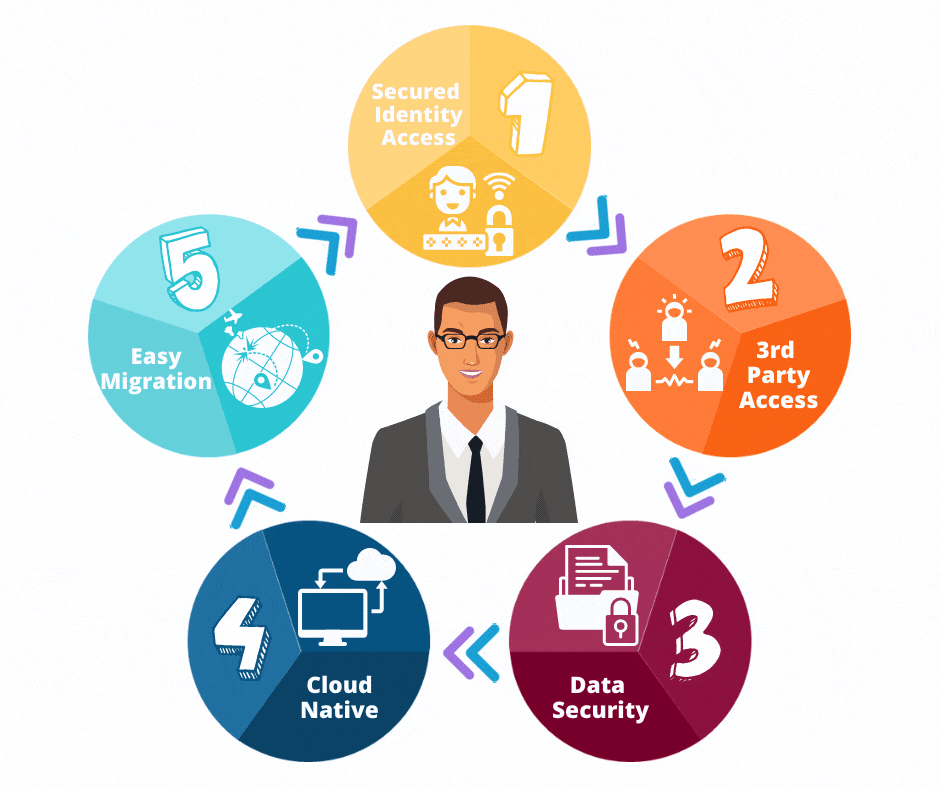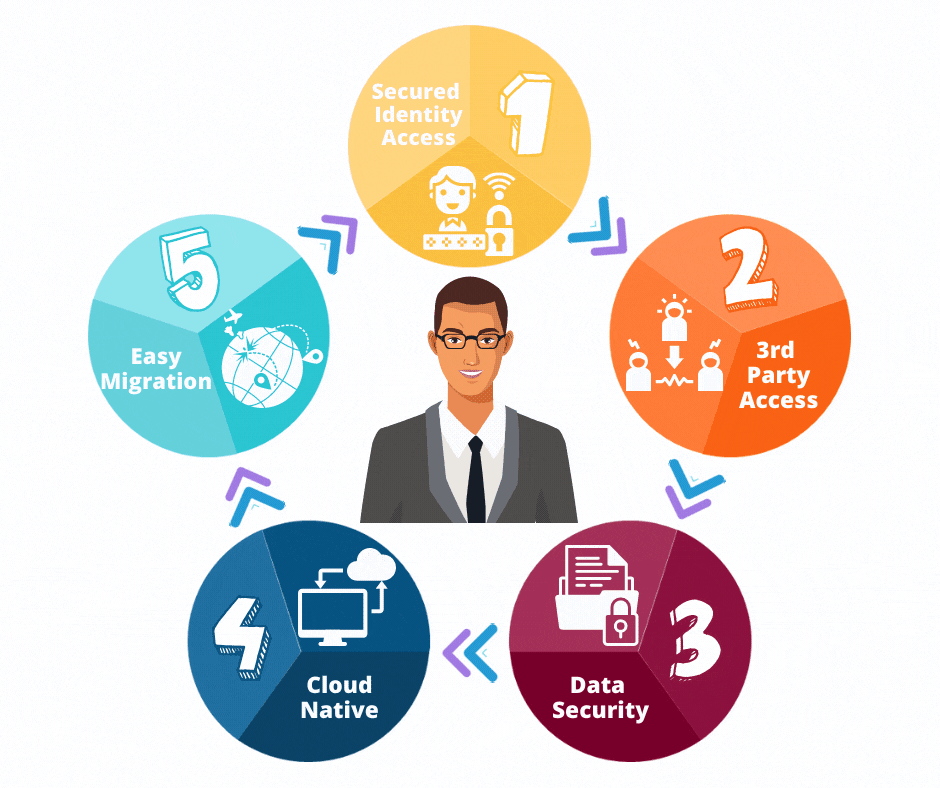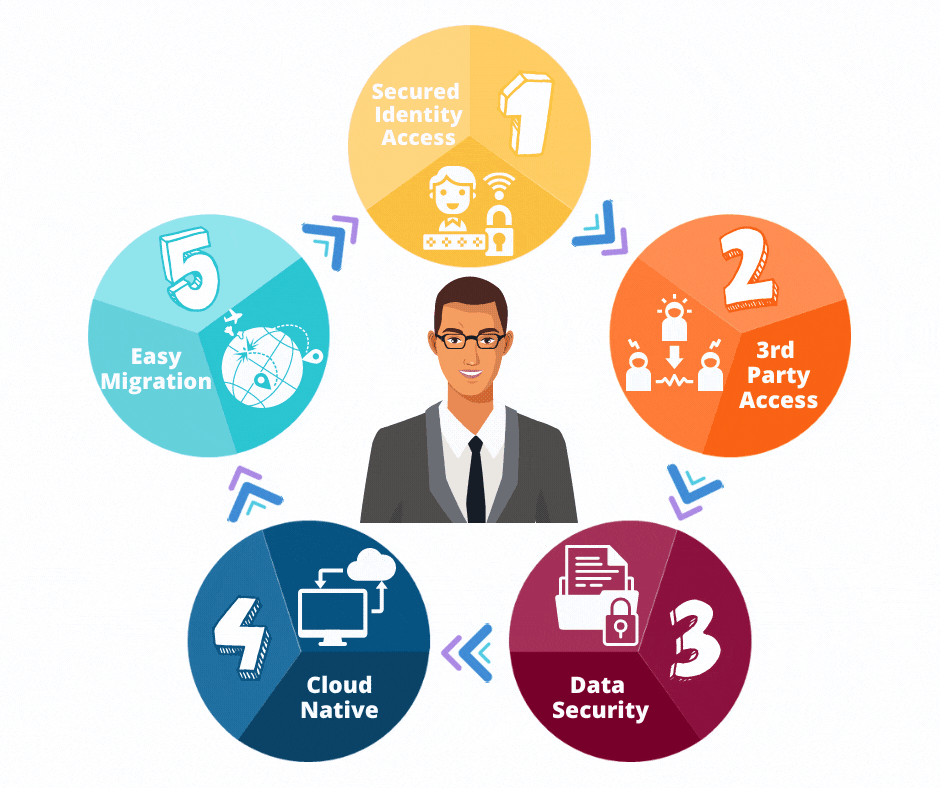
There you are, Bonjour!
Most of the businesses are away from adopting innovative changes. On the other hand, other business organizations are implementing cloud technologies to embrace business transformation.
An organization has to deal with several activities as each employee will handle every task. They gotta access to the Organization’s information. But there is the risk of stealing confidential information as every employee access the company data.

So, here comes the need for IAM technology, which helps manage individual access to the data and applications by providing high-level security.
IAM has several tools, but in this blog, I would like to talk about the advanced IAM tool, i.e., Saviynt.
We have already had a talk regarding Saviynt in our previous blog. So, here we will discuss how to find suitable training from this Saviynt Tutorial Blog.
Let’s get started!
What is Saviynt?
A popular cloud-based Identity and Access solution, Saviynt, encourages modernization and minimizes migration anxieties for enterprises. For large-scale businesses, this IAM platform is ideally suited for successful transitions and automated identity operations.
Saviynt provides a unified platform for securing apps, data, and infrastructure for cloud and on-premises environments. Advanced risk analytics and intelligence are combined with fine-grained privilege control by Saviynt, making it a leader in IGA 2.0 implementations.
Saviynt provides a unified cloud and enterprise platform for securing applications, data, and infrastructure. Cloud-native IGA Identity Governance and Administration technology from Saviynt safeguard your most confidential data. By limiting access to resources to only those who need them and for a limited period of time, improves the effectiveness and responsiveness of your business.
What are the features of Saviynt?
A few of the features offered by Saviynt IAM technology include the following:
- The Saviynt Control Exchange provides a control repository and a Unified Controls Framework cross-mapped across business-critical legislation, industry standards, platforms, and control types in order to track, remediate, and document compliance activities.
- Deploy rapidly and get the benefits sooner rather than later to support your mission.
- For digital transformation, Saviynt’s platform integrates across on-premise, hybrid, cloud, and multi-cloud environments, enabling governance for digital transformation plans.
- Improve security across departments and agencies by implementing Zero Trust techniques.
- Based on data sensitivity, Saviynt’s Data Access Governance (DAG) allows agencies to set access controls.
- Saviynt’s breadth and depth of risk kinds and levels, along with fine-grained entitlements, lessen the burden of Cloud Smart transformation.
Are there any modules included in this technology?
We can’t say modules because there are no particular modules in this technology. But, few advanced products are offered through Saviynt. They are:
- Third-Party Access Management: Confidently emerges with the third parties and monitors organizations, people, and parties.
- Privileged Access Management: Prevents exceeding permitted accounts based on usage and eliminates the risk of access from unauthorized accounts.
- Identity Governance and Administration: Offers user-friendly experience and makes sure regarding right access at the right time.
- Application Access Governance: Monitors automated stable controls and decreases the risk during cross-application SoD management.
- Data Access Governance: protects the sensitive data by gaining access visibility and prevents them from getting into the wrong access.
How does this technology help the Organization?
Saviynt is unique among IDAM technologies since it enables enterprises to design and enforce IAM policies and integrate IAM services to meet audit and compliance needs.
Saviynt has a number of OOTB connectors that can connect to an application and enable provisioning and reconciliation right now… Moving applications, data, and IT workloads to the cloud have many advantages for public sector organizations. Cloud Smart standards may still be breached if the right identification controls are not in place.
In order to achieve security and compliance objectives, it is difficult to protect sensitive personal information. The Saviynt enterprise intelligent cloud platform supports your goal by unifying identity governance, granular application access, and privilege access.
Where can this technology be used?
Saviynt has considerably improved IAM’s capabilities. Its products allow it to give the correct access at the right moment for everyone who needs it. Out-of-the-box capabilities are great, reducing the need for extensive customization.
We have developed Saviynt as an intelligent and scalable enterprise Identity Management system. As part of the user onboarding/entitlements provisioning, a wide variety of connectors can be used to connect with various target systems.
Third-party solutions can integrate requests, approvals, and certifications using this technology’s comprehensive set of APIs. For systems that necessitate manual intervention, this platform provides a variety of integration types and encourages the use of a variety of ticketing systems. It has a wide range of features and a variety of ways to integrate them.
So, as we know about this technology so far, can you guess what advantages it offers its users?
- As with any linked program, organizations can define as many fine-grained parameters as they like, such as read-only, update/delete/replace, or shift access based on the circumstances.
- Saviynt’s fine-grained visibility of entitlements enables the establishment of risk-based features that, for example, highlight access risk tied to a specific organizational or compliance duty.
- Saviynt’s fine-grained entitlement visibility allows it to enforce compliance constraints like Segregation of Duty (SoD) both within and between apps.
- Templates, reminders, and repetitive workflows may be created with minimal effort and without the need for technical expertise.
- Management can focus their efforts on regions that pose a serious threat because of Saviynt’s ability to direct their attention to those areas.
In the IT world, the future is unpredictable; what would be the scope for Saviynt in the future?
With the help of countries like Russia and the United Kingdom, Saviynt has expanded its reach.
For Saviynt, this means integrating modern technologies to protect data, manage infrastructure, and ensure that users have access only to the information they need.
As a result, Saviynt’s performance is poised to undergo a significant overhaul. A few of the aspects on which this technology focuses are listed below.
- Determine the amount of access and risk by creating a universal inventory of all permissions.
- The goal is to standardize procedures across the firm and mine and design roles.
- Keep track of all changes to a user’s position and keep a thorough audit trail of those changes
- The language most usually heard in the corporate world
- Data visualizations and reporting can help businesses make better decisions. Hmm, this technology seems cool, right! So, have you thought about the prerequisites that one needs to possess before learning this course?
As Saviynt is an IAM technology, it demands some prerequisites for gaining knowledge. So, an individual who will learn this technology needs to possess the requirements below. They are:
Knowledge regarding the IAM platform is needed as Saviynt is advanced cloud IAM technology. Having experience will help you better under this security tool.
You need to know Java and MySQL programming skills to learn this course.
So you might wanna know what types of training you will be getting?
Training for this Course is available in two types
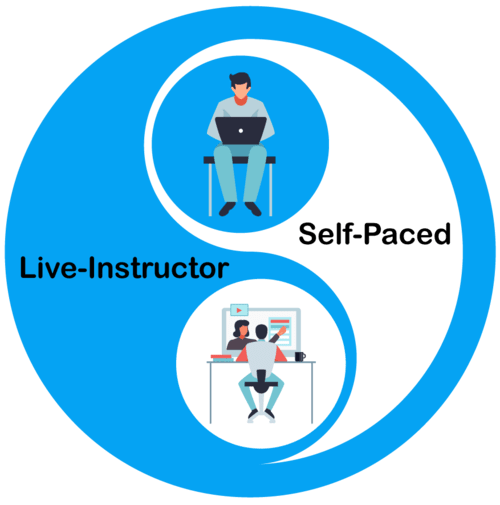
Live-Instructor: in this method, you will get an instructor who will explain the procedure from every detail and the demos and real-time projects.
Self-Paced: in this method, you will get pre-recorded videos and PDF materials to independently learn this course. You will also contact a 24/7 support team to clear the queries.
If you’re a bit experienced person, you can choose the Self-paced training. However, if you do not know this technology, I recommend you go for live-instructor training.
Which training platform will be conducive to choosing any of these training types?
Saviynt is the subject of numerous blogs, websites, and videos. However, if you’re serious about advancing your career, you’ll need to go to school.
CloudFoundation has the greatest tutorials in my opinion, based on my personal experience. The greatest tutors will assist you in learning the material in a systematic manner.
Your qualifications and CV must be updated to reflect your completion of the course once you have passed the certification exam. Afterward, you’ll be able to ace interviews and land jobs at reputable multinational corporations with the guidance of our expert trainer.
On the whole, I would like to summarize that,
Software solution Saviynt is the best for managing identity and security. It provides a single platform for organizations to safeguard their apps, data, and infrastructure.
With today’s issues in governance and security, it helps your organization to be better prepared.
Consider taking a course and earning a certificate upon completion. My recommendation is to enroll in lessons at CloudFoundation, where you will receive great instruction.
Clear your doubts with the help of precise videos and PDf materials, as well as an instructor. Make sure you’re well-prepared and give it you’re all.
Make sure you pass your certification exam with ease.
Grab the Opportunity…
Make it more interesting!
If any information needs to be included in this Saviynt Tutorial blog, comment down and keep me informed. Also, check out our previous blogs to find other exciting and trending technologies.
Gracias!

Bhavani
Author
Being tech-savvy, I would like to explore massive and sophisticated technologies and make learning them a joy.
