Centrify Tutorial – The complete reference on PAM
Introduction:
Hello people!!!
Are you looking for something interesting to learn?
This blog will help you to learn new Technology that is Centrify.
Centrify is a (PAM) Privileged Access Management and Zero-trust Management.
Centrify will be discussed in-depth in my blog. Let’s get started.
What is Centrify?
Centrify lets users join their IT Infrastructure by joining access, authentication, and identity for UNIX and LINUX within the Microsoft Active Directory.
Centrify is a leading provider for privileged access management solutions enabling digital transformation at scale.
Centrify gives Integrated cloud-based and software solutions that use Microsoft Active Directory to audit access, protect Centrally, and govern applications, mobile devices, and Cross-platform Computers.
Centrify PAM (Privileged Access Management):
Centrify recreated as (PAM) Privileged Access Management with the new Cloud-native services that will stop the trending cause of Breaches and secure the hybrid Infrastructure – Privileged Access Abuse.
Who requests they can access by deleting the local accounts and reducing the number of passwords and accounts?
Let me tell you some of the Benefits and Features of Centrify:
- Manage Privileged Accounts:
Invent privileged accounts on devices, applications, and systems for subsequent management. It also gives app-to-app passwords Management (AAPM).
- Delegate and Elevate Privilege:
Privileges are allowed on the achieved devices by Centrify Managers to logged-in customers.
- Pioneering Innovation:
Centrify has a PAM market, inventing many of the organizations-firsts and important ways of safeguarding the present enterprise in contradiction of today’s top cause of information breaches-privileged contact management. Therefore, users enjoy the benefit of having Centrify PAM.
- Built for Cloud:
Centrify PAM, involved in zero-trust values, delivers the performance, scale, and flexibility that isn’t likely by a legacy PAM approach, planned for the information ill-suited and center to locking access to the hybrid of the cloud IT organizations.
- Flexible deployment:
We trust in providing our users with different choices when organizing the PAM Centrify. Centrify offers different kinds of (SaaS) software-as-a-service.
And user-managed arrangement options. Whatever your choice, you can tick on Centrify PAM to see your opportunities for deployment, high scalability, availability, and use.
- Ease of operations and Use:
Upgrades must not stop over you and need operational finances beyond your early investment. Must a query arise, our specialists are always assuring and available a timely reply?
- Built for Digital change production:
Centrify easily handles privileged access workloads of modern, global enterprises by leveraging an intelligent gateway connector framework and advanced machine learning technology. PAM is not for network and databases systems in your information center. It must also extend to the multi-cloud and cloud environments anywhere massive elasticity and scale are the standards.
- Industry acceptance:
Centrify has received many awards from the business, including Gartner peer insight, community user choice, one creation identity top ten (IAM) identity, and access management frost and vendor.
Where does this Technology Use?
Datacenter infrastructure, databases, and network devices aren’t the only things that may benefit from privileged access control.
Cloud and multi-cloud systems may benefit from this Technology, where vast size and flexibility are the standards.
In addition to securing significant information clusters, it may be used to automate DevOps.
It covers the most comprehensive spectrum of Supported platforms, use-cases, and attack surfaces on the market, allowing us to expand and adapt to new demands.
It can manage the privileged access Management workloads of today’s worldwide corporations.
Intelligent Gateway Connectors and cutting-edge machine learning technologies are being used.
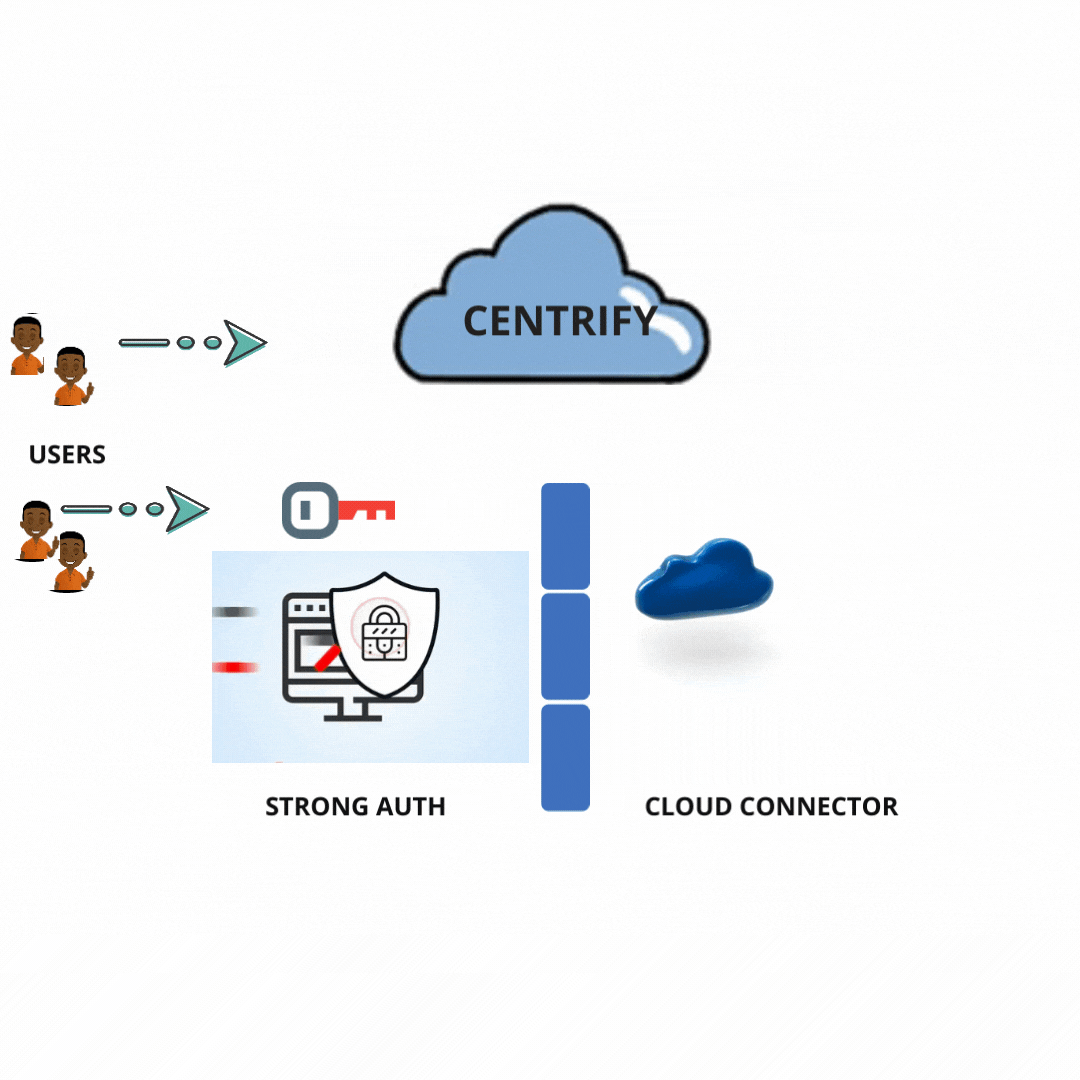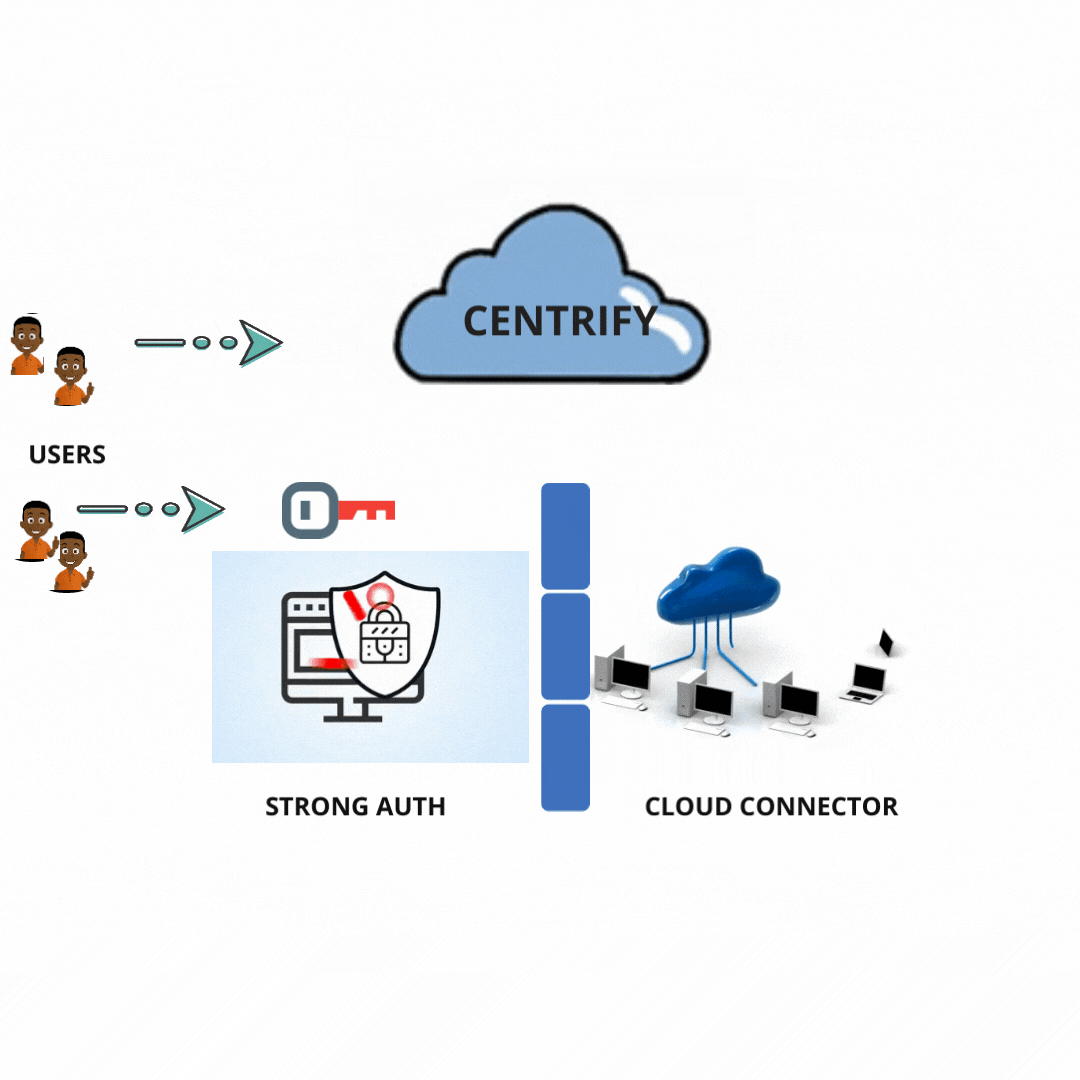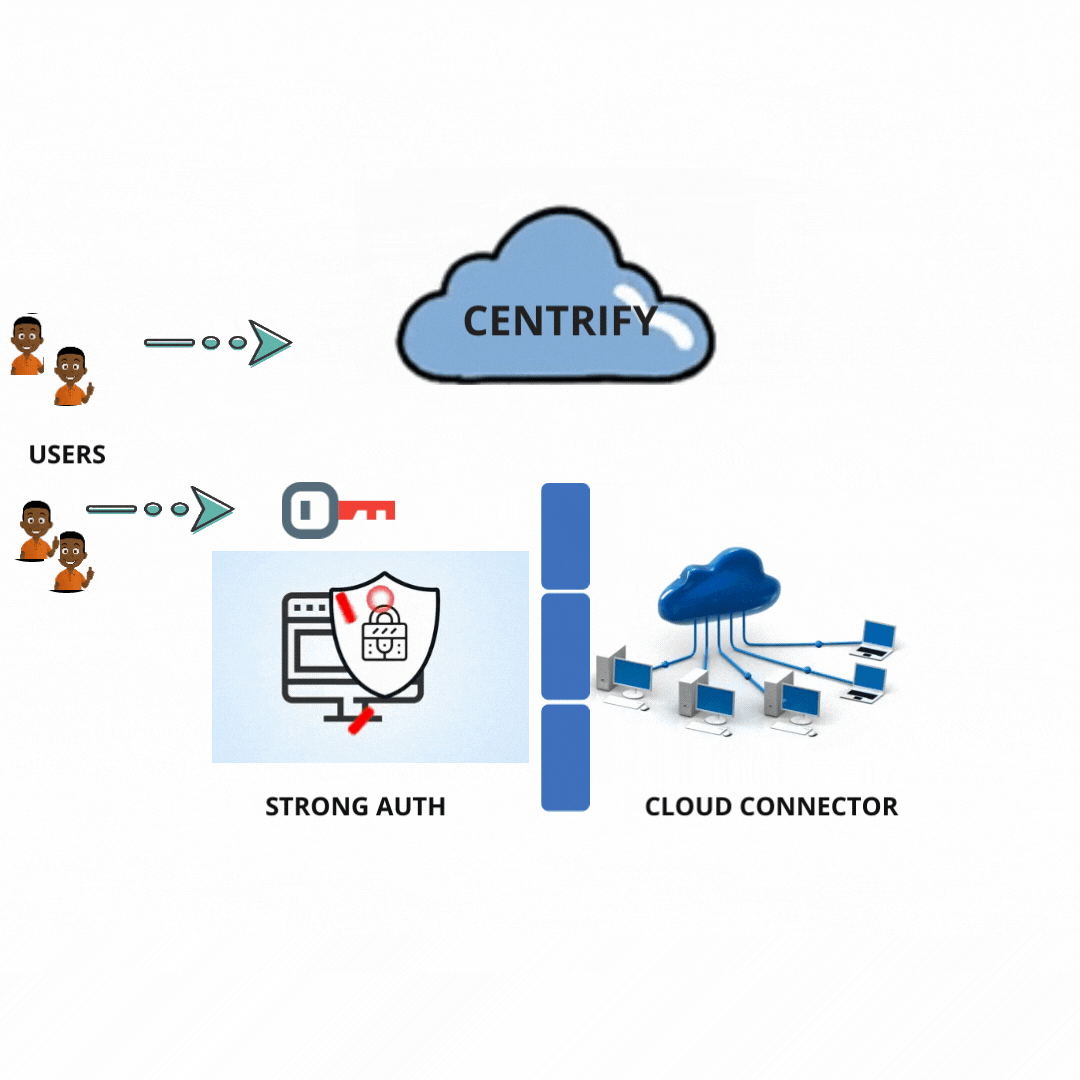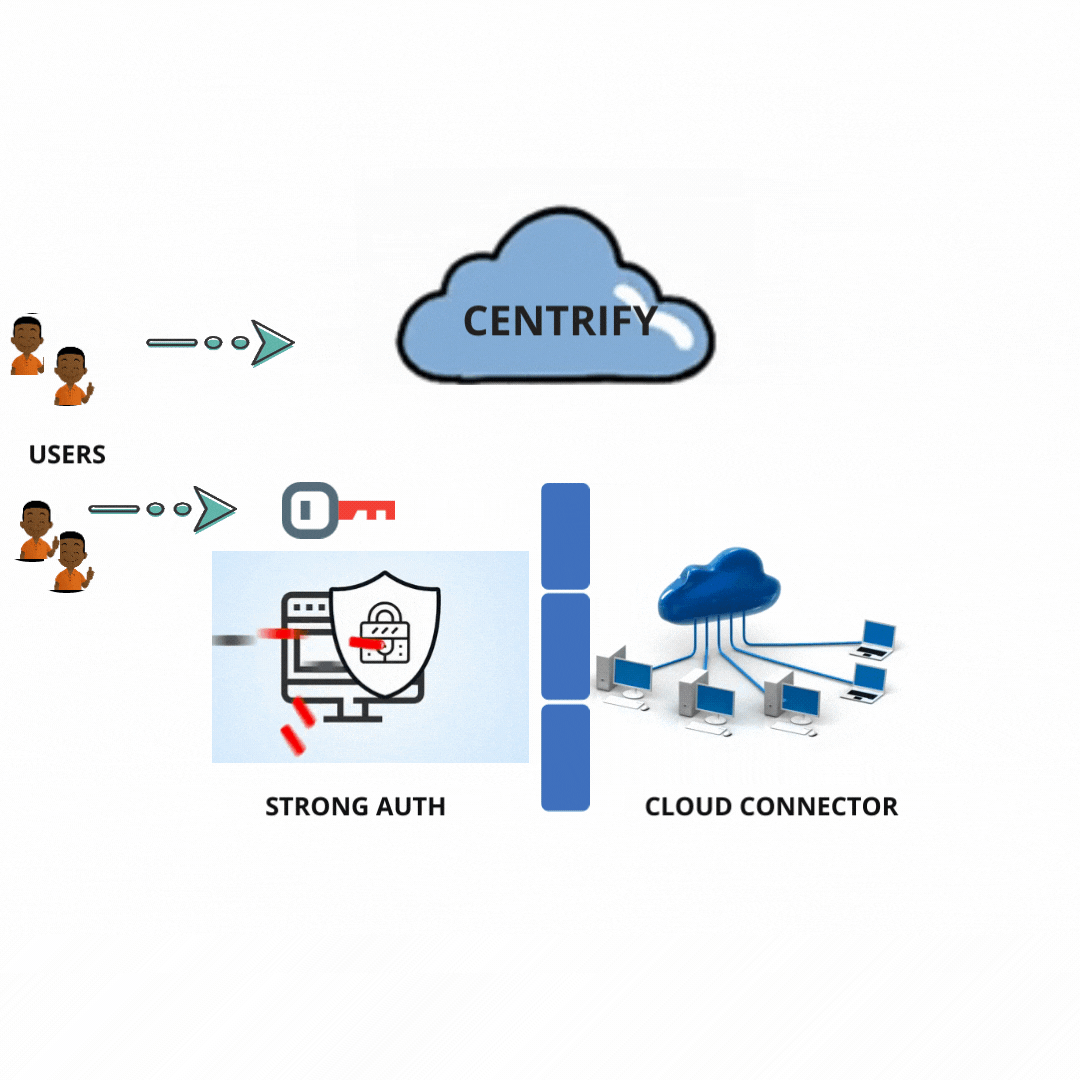
How does this technology work?
Centrify allows the Retire legacy and redundant identity stores by handling the Non-windows Identities from the Active Directory.
The Centrify Migration Wizard fastens the deployment by bringing its group and user data from sources like passwd/etc/and NIS+, NIS into Active Directory.
Centrify provides UNIX PowerShell tools and command-line designed to allow administrators to achieve UNIX data and Centrify Zones and Active Directory groups and accounts.
These are the Command-line tools crafted very carefully to support the Different types of Output choices so they can integrate with the provisioning scripts and in-house automation.
What are the Prerequisites to learn Centrify?
The following summarizes the hardware and software that should need to learn Centrify:
- Database
- Cache
- Load balancer
- Certificate for the Centrify PAM Authentication.
- License key
- Background, web, TCP relay, and also management nodes
- Supported Redis Versions, etc
And the requirements are needed upon your performance and also scale-out.
What are the uses of Centrify?
- Join Linux and UNIX systems to Active Directory without installing software on the domain controller or modifying schema.
- Automatically access systems for identity-related risks.
- Apply consistent security policies and central manage compliance reporting.
- Associate access rights to individuals through their Active Directory accounts. Centrify reporting on who has access to what systems.
- Users have the right to access only those systems required for business purposes based on their job role.
- Reduces the stay compliant and cyber risk:
The digital environment plays a significant role in educational organizations in the world. It is necessary to protect the authorized access to the student, research information, and faculty.
Top Centrify competitors:
- CyberArk
- Beyond Trust
- Thycotic
- IBM
- Oracle
- One identityCentrify Differentiators:

About the Centrify Certification Program:
Centrify certification is for all Centrify customers and partners. Can achieve certification by getting 80% or more.
Future scope:
Nowadays, the priorities for PAM have been increasing. Everyone is interested in taking the course which helps to grow their future.
Here you got the best course Centrify which helps build knowledge in Privileged Access Management.
When it comes to the future scope, you will have good opportunities in MNCs.
Career Opportunities with Centrify:
- Cybersecurity advisor for identity and access management
- Linus (Sysadmin)-Technical architect
- Cybersecurity advisor for identity and access management
- Security specialist-identity access management agent (CyberArk)
- Senior system analyst-LINUX
- Linux system administrator
- Linux, red hat Linux specialist systems engineer
- Unix sysadmin
Companies using Centrify:
- Federal Emergency Management Agency (US).
- Social Security Administration (US).
- Oracle
- Apple
- Raytheon
- RTX
Types of Training:
There are two types of Training are available:
- Self-paced
- Instructor led-live Training
What are the best Training platforms?
CloudFoundation, the excellent online training platform, is my recommendation for training platforms.
You may choose between self-paced and instructor-led-live Training; however, I recommend instructor-led-live Training due to the difficulty of juggling two jobs while also taking a new course.
For this reason, Instructor-led-live Training is a better option for both time and money management.
Conclusion:
Well, now we’ve come to the end of this blog.
Before I wrap up this blog, I want to conclude the whole writing in a few lines.
Centrify provides integrated software and cloud-based solutions that use Microsoft Active Directory to govern, protect centrally, and audit access to cross-platform computers, mobile devices, and apps.
If you are a working professional, Online Training is the best choice. To have a deeper understanding of the Technology, Enroll Now at CloudFoundation.
They will help you get a proper career path, and I expect you to acquire a job in a well-known company.
Good Luck!!!

Divya
Author
Hello all! I am gonna pop you with the information that will make your life easier.