CA Identity Manager Training

Hello there! What’s up, everyone?
A new CA Identity Manager Training blog is here.
New and most powerful software is being developed in today’s globe.
Let’s begin with a quick introduction of CA Identity Manager first.
Using CA Identity Manager, businesses can securely provision, manage, and off-board employees across all of their on-premises and cloud-based applications.
- What is CA Identity Manager?
Users’ onboarding, modification, and off-boarding across all corporate systems to the cloud are automated with the help of CA Identity Manager, a trustworthy user provider, and manager.
- Where is this technology used?
Capabilities and procedures for doing business in the context of an association may be found in CA Identity Manager.
Employer onboarding and off-boarding are supported, access requests are monitored, and character personality assessments are automated.
And CA Identity Manager training teaches you how to identify the many features, functions, and advantages of CA Identity Manager.
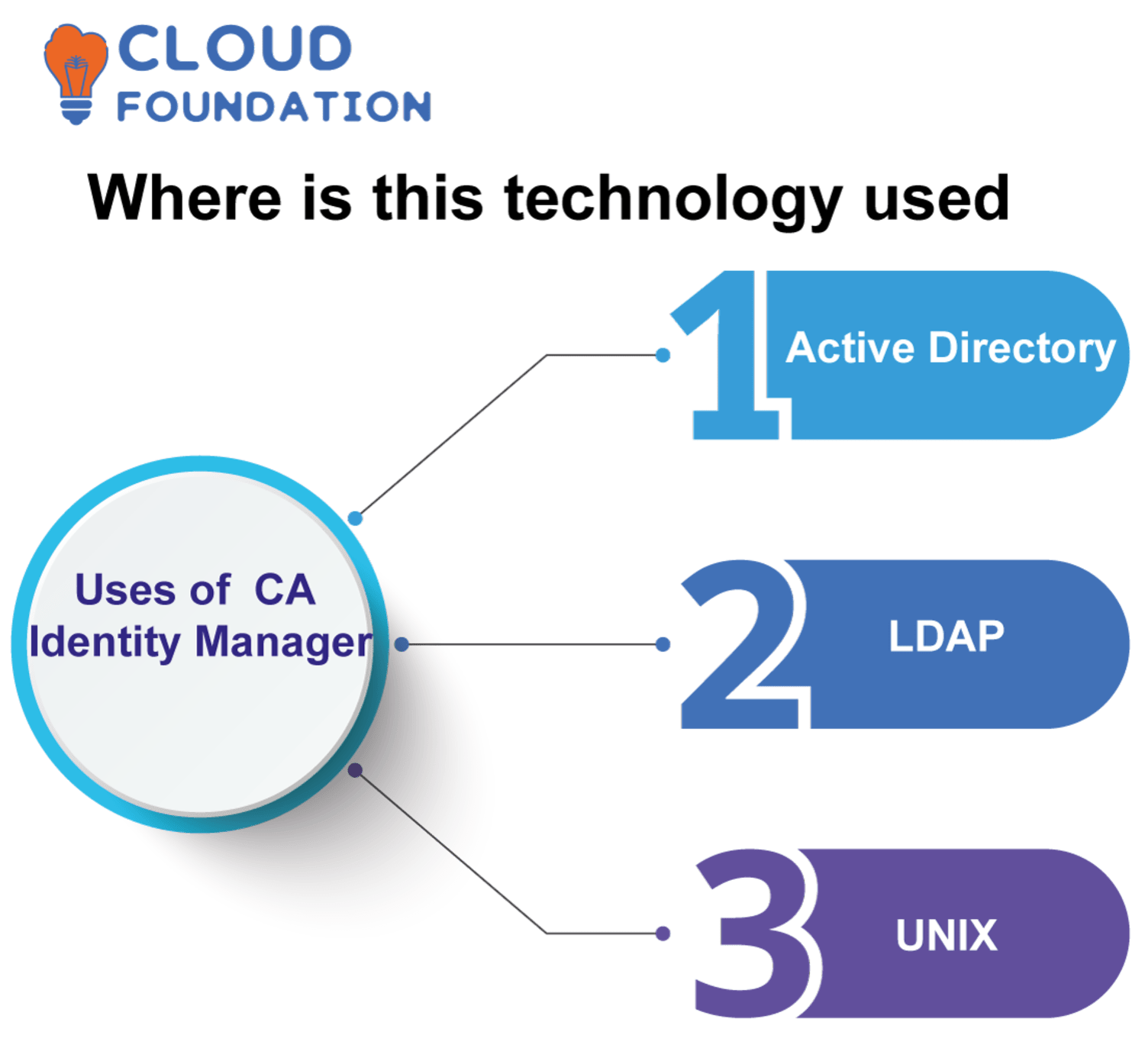 Use endpoints like Active Directory, LDAP, and UNIX for account provisioning, such as this.
Use endpoints like Active Directory, LDAP, and UNIX for account provisioning, such as this.
CA Identity Manager may all be utilized by provisioning roles, policies, and linkages between functions, tasks, and events.
Delegate administration allows users to administer their accounts and provide services logically and consistently.
Comply with Segregation of Duties regulations (SOD)
To make routine operations like self-enrollment on-demand possible, configure and implement workflow procedures.
- How does this technology work?
Using CA Identity Manager, you may construct character data for an association’s specific business jobs and cycles. Assists in customers’ on- and off-boarding; allows the organization to manage access requests; and automates personality accommodation processes.
CA Identity Manager helps IT businesses increase operational efficiency and effectiveness by offering a flexible and adaptable personality to the boarding establishment that can put together your character data within the context of your unique business responsibilities and procedures…
 As a result, it makes it easier for companies to handle user access requests. It automates identification compliance procedures when bringing on new employees or terminating existing ones. It may be installed in minutes rather than days through pre-configured use cases and virtual appliance deployment.
As a result, it makes it easier for companies to handle user access requests. It automates identification compliance procedures when bringing on new employees or terminating existing ones. It may be installed in minutes rather than days through pre-configured use cases and virtual appliance deployment.
CA Technologies provides a comprehensive approach to dealing with the character of executives by combining technology with extensive administrations and educational contributions. CA Technologies provides the knowledge and proven methods to help you implement personality on the board in a way that delivers quick results now and in the future.
- In what ways may this technology be beneficial?
Improved client provisioning, greater working capacity, reduced risk of security breaches, decreased help desk overburden, and an assurance that individuals can’t access systems they shouldn’t have access to are just some of the benefits of CA Identity Manager.
Secret word methods for CA Identity Manager let you establish rules and constraints that govern the construction, lapse, and usage of client passwords.
It is possible to develop complex password policies if you set CA Identity Manager to work with CA SiteMinder.
- To learn this technology, what are the prerequisites?
Working knowledge of a network board, Unix, Linux, Windows stages, systems administration, and distributed computing is excellent for learning about this technology.
Basic knowledge of the IT sales environment will be a plus.
- What are benefits do we get from CA Identity Manager?
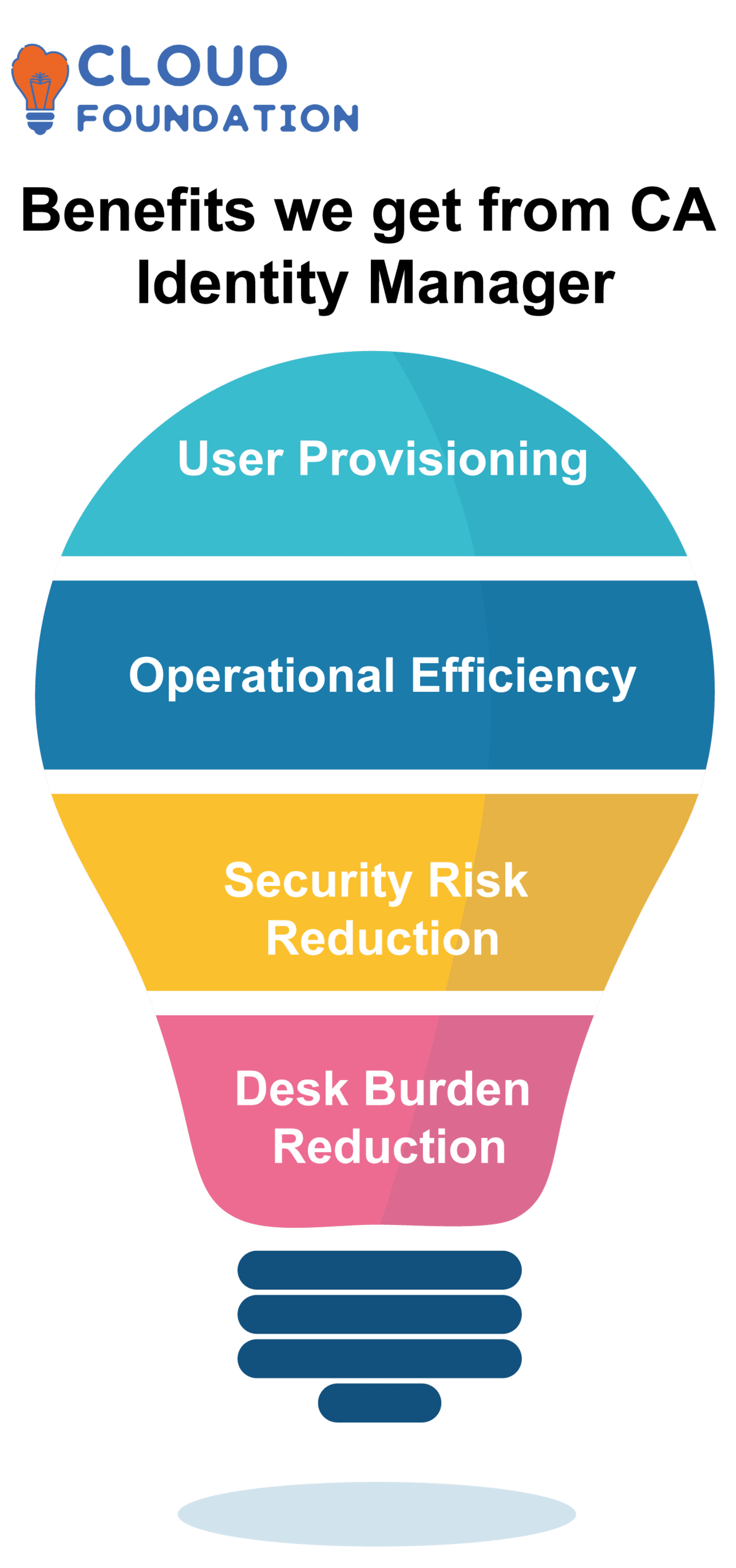 User provisioning, operational efficiency, security risk reduction, and help desk burden reduction are some of the benefits of CA Identity Manager. It guarantees that people can’t access systems they shouldn’t be able to.
User provisioning, operational efficiency, security risk reduction, and help desk burden reduction are some of the benefits of CA Identity Manager. It guarantees that people can’t access systems they shouldn’t be able to.
The following are some of the advantages:
- It creates a critical foundation for identity management.
- As a second step, try to prevent non-compliant provision actions from occurring.
- When granting access to people based on their jobs, do not rely on guesswork.
- Allow users to seek and approve access to the system without the assistance of the support desk.
- Once an employee or contractor has done their work, revoke their access to the apps they require to do their job.
- When business processes change, swiftly adjust the identity management infrastructure.
- What are the steps you have to follow for the Certification?
 You’ll need to register for the certification exam on the official website following the course.
You’ll need to register for the certification exam on the official website following the course.
When conducting the Exam, you must observe the following rules:
A computer-based test is used for the Exam.
- You’ll have to take the Exam on your own time. •
Procter may request that you display the area around you to prevent fraud.
You may be removed from the Exam if Procter uncovers any questionable conduct.
- What types of training will I get to learn in this course?
Two online training programs are now offered in response to the rising popularity of this type of training.
 This form of instruction allows you to learn when and where you choose. You’ll get access to pre-recorded PDFs and videos for self-study, as well as groups that are open 24 hours a day, seven days a week, to answer your questions.
This form of instruction allows you to learn when and where you choose. You’ll get access to pre-recorded PDFs and videos for self-study, as well as groups that are open 24 hours a day, seven days a week, to answer your questions.
During this training session, you will ask your trainers any questions you may have about any of the topics covered. They will be able to answer them for you as well.
For newcomers, I strongly recommend that you use the Live Instructor option, as it will be beneficial to you all.
I recommend that you join CloudFoundation because they offer training in both areas.
Here, I would like to summarize that
An organization’s particular business roles and procedures need that CA Identity Manager technology to arrange identity information following these requirements. To get the most out of this technology, I’ll help you sign up with CloudFoundation.
Please feel free to voice any concerns you may have about this new technology in the comments section below.
So, the greatest of the best, go ahead and do your thing.

Shailja
Author
Develop the mind, spark the future; change the world with Technology.
