Azure Run Books | Azure Role Assignments
Launching Azure Runbooks
Take for example you would like to begin employing runbooks in Azure V2 by a drag and drop graphical way of launching imaginary machines.
You have a resource group with a group of VMs and you are going to make life easy with a PowerShell sequence to explain this in a different way, I have an online Windows VM just waiting to showcase the concept and how it can be implemented in a real-life situation
What happens here is the first thing you will do is to put the resources into a runbook.
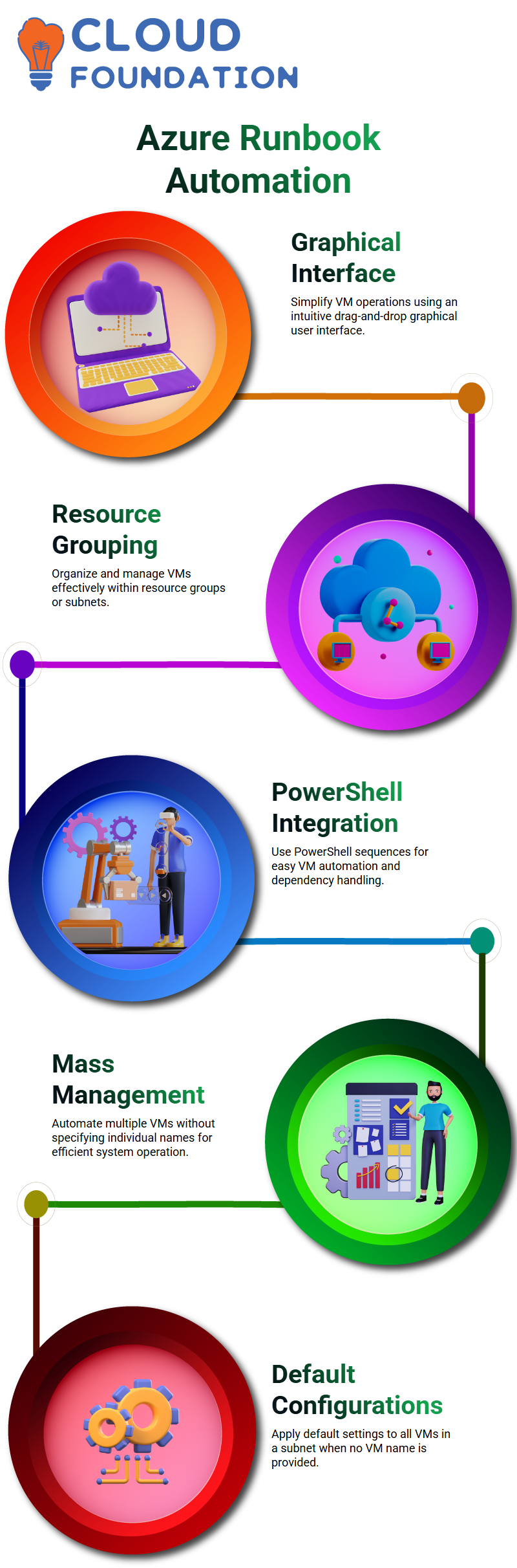
Inside this graphic user interface, you can do operations such as formulate and supervise solo VMs, get all VMs in a resource group, or operate VMs in a subnet that you are interested in and it is really easy to use for that The operations are such that they change as per your needs In addition to the above, the runbook refines user relations with fewer mouse clicks and thus, it is easy for you to specify the dependencies that each step of the process needs
How Azure Automation Refines Your System
Kickstarting a VM in Azure is a piece of cake. If you only specify the resource group name and the VM name, you will witness a sequence of the VM’s state that is changing from ‘stopped’ to ‘updating’ and then to ‘running’ By doing so a number of VMs will be started by the Azure if you don’t mention explicitly the VM name
This attribute is extremely useful for easy mass resources management. What’s amazing is that the graphical view in the Azure runbook arrangements several alternatives like securing individual VMs, all VMs in a resource group, or those within the confines of a subnet as well.
If a VM name is not provided, the setup is by default applied to all VMs in the subnet.
Azure Runbooks for Disaster Recovery
The maximum capacity of Azure Automation is fully demonstrated when it comes to disaster recovery situations. Imagine a site that is not only secondary but also not always active. In the incident of a primary site failure, Azure’s automation is used to start resources in the secondary region without any flaws.
The use of secondary sites only when something catastrophic happens is an economical advantage for companies. By means of Azure’s high SLA uptime, you can pinpoint the time and place when the secondary sites should be enabled Runbooks are vital in the process as these are already created scripts that accomplish the movements between them.
One fine point here is that runbooks are really able to advisor the indispensable tasks not by just checking the primary server’s status — that’s the role of Azure Site Recovery — while they do so in a very positive way only
Azure Tools for Cross-Cloud Automation
Azure Automation’s attractiveness is related to the adaptability it has where it can direct automation to be done no matter regardless of whether it is hybrid or AWS managed. Azure runbooks are the best assistant to help you standardize your workflows during the day It simply needs the insight of the connected units for the execution to take place without a hitch
Without any problems, Azure can operate updates on on-premises systems by the help of runbook workers This function permits uninterrupted and automated exposure no matter what background is used. The formation in Azure Portal or PowerShell is simple and productive.
Creating Usage Azure Runbooks
Azure enables you to get started with the tradition runbooks with the help of the provided template Do you need a PowerShell, Python, or graphical runbook? You can use any way you like You also have the possibility to develop a tradition runbook if you don’t want to exploit templates from the Azure gallery.
Through the application of ritual runbooks, you can prescribe the process sequentially The canvas is the place where you can insert the resources, and you are all set Azure not only entitles you to revise automation to your targeted needs but also makes cloud management possible for both system administrators and developers.
Azure Governance for Useful Resource Management
It is requisite to set up governance apply when controlling Azure resources as this is key to their watch. businesses to keep control, unusually large or medium-size companies that are commencing their cloud voyage.
Compute, storage, and networking are the three main resources in any Azure environment. Mishandling of these resources can lead to exorbitant costs, notably in large-measure deployments.
Exploiting Azure to Avoid Widespread Pitfalls
Securing paid for only what you use is one of the advantages and disadvantages of Azure’s charging model. Unlike resources that are on-premises, Azure always cost, involving instances you do not actively run.
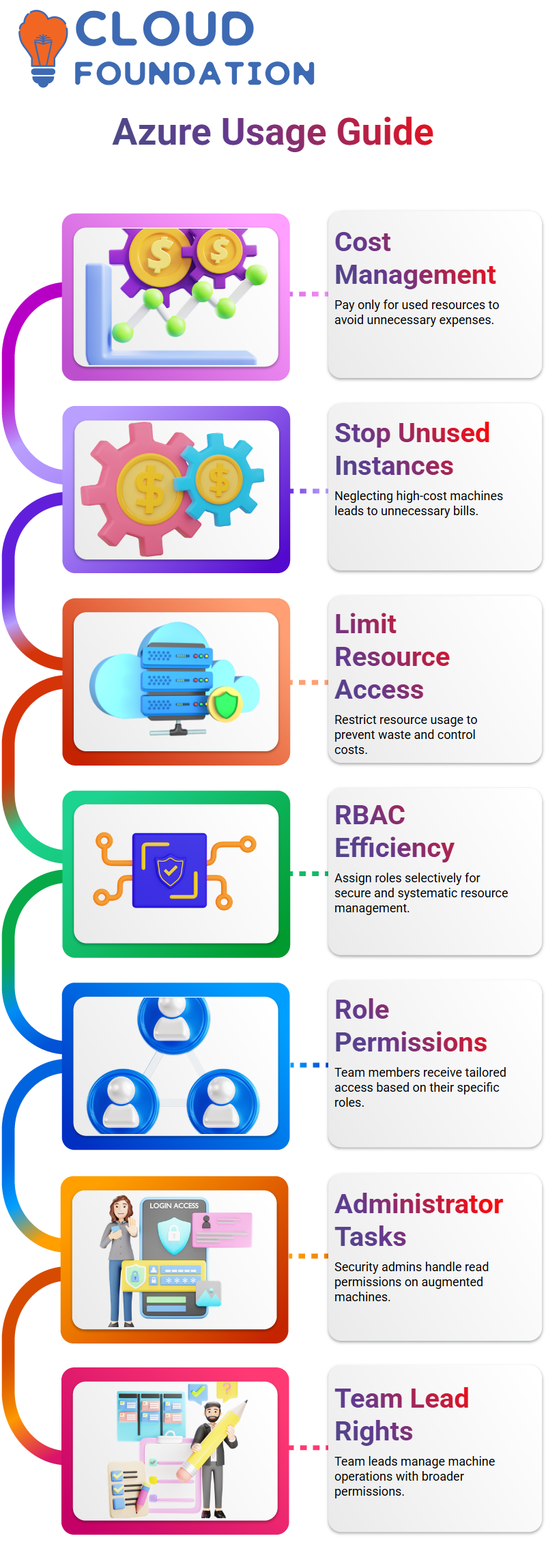
For case, neglecting to stop a high-configuration cyber machine on Azure might cause you to have unnecessary bills. To deal with these and other similar issues, it is mandatory to limit the resources and only permit access that is purposeful This tactic not only guarantees that resources are used capably but also leads to a reduction of unnecessary costs
Rule-Based Access Control in Azure
RBAC of Azure is a pioneering solution to the problem of managing resources’ access in a selective and a particular manner The members of a team or a user can have clearance depending on their role and hence be able to direct Azure resources in a safe and systematic manner capably
For sample, if a security administrator might only be entitled to have read permissions for the augmented machines specifically, a team lead can have rights to the area of triggering and stopping these digital machines as they like
Azure Resource Manager Hierarchy
The hierarchy of the Azure Resource Manager is a structure that expresses resources in hierarchical order, i.e., beginning from the root management group and then the whole downtime.
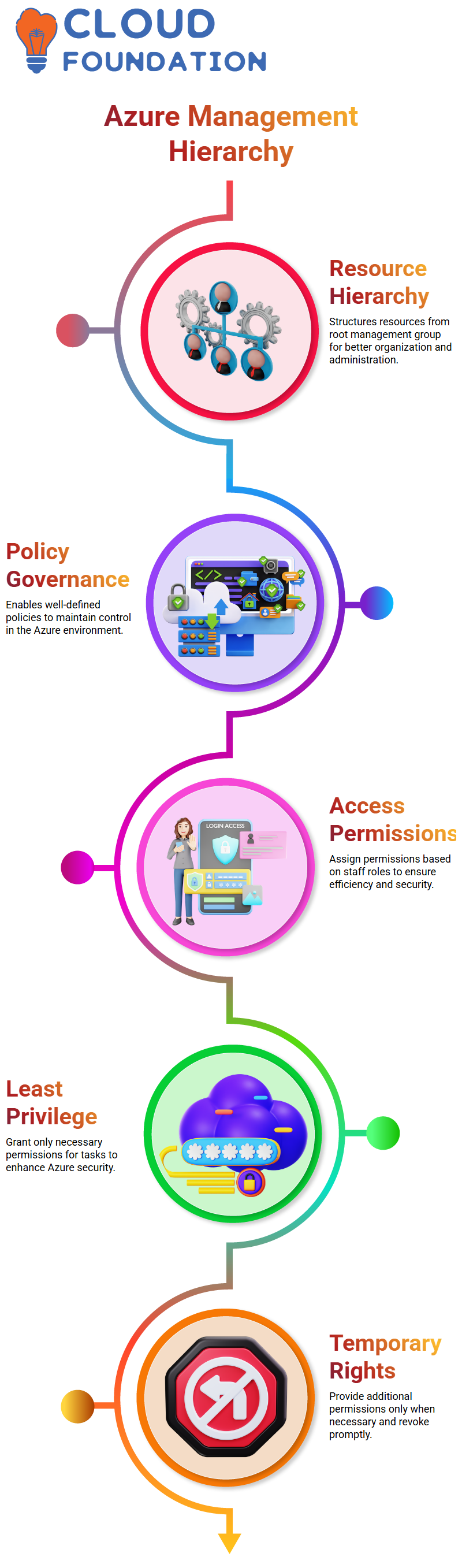
This means that you can control more and more groups of resources, subscriptions, and resource groups, therefore, making it easier for you to administer them more and more swiftly and in the apt levels of quality.
By adopting this type of hierarchy, organizations can govern well-defined policies and keep their Azure environment in check.
Least Access Permissions in Azure
Managing Azure, is imperative in having permissions assigned according to the staff’s specifications of their positions. See to it that I do not have the right permissions for my legitim and specified tasks via a lie detector test, and avoid unexpected tasks that may give me problems
Least privilege permission is the most important security concept in Azure This is the act of giving the right permissions just for the daily tasks, i.e., minimum requisite privileges If someone needs extra rights for a task at Azure, these permissions should be granted only for the period that it is mandatory and then taken away.
Granting of Permissions in Azure
Suppose that you are in an azureCloud_Storage with the need for permissions for the performance of an action like monthly backups Instead of them being always granted, I advise that you do this for a short time, and then cancel it as soon as you are done with your task This strategy in Azure is a good option: it stops unauthorized access and reduces the chances of the task being accidental.
Limiting the use of correct permissions only in Azure is very much important. Extra permissions often engage much trouble. As an exemplar, in the case when a user wants to start a VM or to stop it in Azure you are supposed to permit permission for a particular action only and nothing else to do this.
Role-Based Access Control in Azure
To correctly represent permissions in Azure, I make use of the role-based access control system Mainly, the jobs that are available are Owner, Contributor, and Reader Yet, the Owner is the most powerful role in Azure that can decide who gets access, whereas the Contributor and the Reader are restricted to only their functions
Furthermore, Azure furnishes the possibility of a more exhaustive role assignment for representation, I’ve allocated assignments, like Storage Queue Data Reader, to a user so that his access is inside the limits and without any influence on other resources
Applying Permissions Across Azure Atmosphere
If I take advantage of Azure Blueprints, I would be able to duplicate the assigned characters and permissions to other setting like production or staging. This capability of Azure makes sure that time is conserved and nothing is changed during the process of replication, thus, stability is across the resources.
To set up access control in Azure, I first govern the management group on the Azure portal and then proceed with a list of jobs that I think are will fit the best. The management group is a attribute in Azure that gives an easy-as-possible feeling for me to deal with the entire access system by just a few clicks.
Detailing Groups and Jobs in Azure
It is my sincere suggestion that you assign permissions to groups instead of individual users in Azure since this is the optimal for the company’s sequence at any given time. This minimizes bureaucracy in case people move from one department to another in the organization.
Practically, it is my ultimate goal that I will come up with the Azure Active Directory groups that follow the organizational departments. Next, I provision rights for the delineated groups inside the Azure podium to make governance and growth potential uninterrupted.
Azure’s Thorough Role Assignment
Azure gives us the option to delimit jobs that are applicable to individual services, for case, Logic App Contributor or Data Factory Operator. If a user, for demonstration, requires access to a resource group in Azure, first of all, I specifically set their permissions to match their jobs.
By taking advantage of Azure’s granular access control, I am able to allocate access to container instances, logic apps, or augmented networks What is more, this level of detail within the confines of the Azure stand supplies that every user or group has distinct-cut permissions with no confusion.
Role Assignments in the Azure Portal
To put it simply, if you’re managing resources in Azure, role assignments administer to manage or oversee. as your useful gateway to permissions control .If you are working with a online network or dealing with synthetic machines, one of the feathers in the Azure cap is role-based access that, in turn, confirms that only the permissions required are given.
For illustration, by assigning functions to users who log in to a synthetic machine, Azure helps the user fix these permissions to meet the resource requisites of the project going on The Cloud system indeed saves money by reusing the names of role assignments, so services such as storage accounts, SQL security management, etc. are become smoother with the role assignment system of Azure.
Every once in a while, you might need a new role that is not standardized in Azure and yet meets your particular guidelines for the security aspect of your tasks Azure can always control that too Making use of norm assignments in Azure, you are able to set up explicit permissions, you can name individual users to be the only people able to do certain things or at the other end of the spectrum, protect the evidence of the team.
I find it extremely interesting that we have the ability to develop multiple permission groups and specify tradition rules employing Azure–a aspect that breathes life into the resource management game.
It is in their will that people sometimes feel like verifying which parts are given to users via the Azure dais An option in Azure will unveil the characteristic of seeing the role assignments assigned to each user As an illustration, a person can obtain a user role of owner, a view role, or a contributor role—all are displayed live through Azure’s dashboard This ability in Azure is surely the right hand of the administrator in terms of cognizance the permissions and their tracking
Another way that decentralization is achieved is by checking a user’s direct management level for any role assignment of the user there. Capitalizing on Azure management groups permits for the aggregation and simplification of different role assignments, hence giving you the ability to view all role assignments directly attributed to a user on the other hand, you can also use PowerShell or Azure CLI to get a lot more reports on the assignment of specialized tasks to people the method described here in Azure is like a one-stop shop where resource management becomes instantly easier
My typical lane of going into role assignments in Azure is that I frequently use PowerShell or Azure CLI to acquire more full knowledge firsthand from inside These two instruments are extremely helpful to me on whom, what, and which jobs and permissions are assigned to a user in the different resources at a unicenter level the Azure’s facilitation to able to integrate these tools also entitles highly accomplished users to have more flexibility in the system
If you are in need of permission rights to certain resources through the service alone or you are in a wider search to see if any of your processes violate Azure, the dock supplies you with facility for setting the mode of the task by yourself and thus to make it smoother.

Vanitha
Author



