What Is CyberArk? A Brief intro on various CyberArk Architectures
CyberArk is a security device utilized to guard privileged accounts through password management. It maintains records of passwords at an organization and guarantees password change over all the administrations through cryptographic control.
As a component of information security, it is utilized by around half of Fortune 500 organizations worldwide.
These organizations include American Express, NASA, British Petroleum, Deutsche Bank, PwC, UBS, MetLife, Suncor, and many others.
The core competencies of CyberArk include on-demand password management, authentication, and verification, information security, and business process security.
CyberArk is positioned among other leaders in the market for on-demand password management and has a significant market share.
CyberArk Architecture
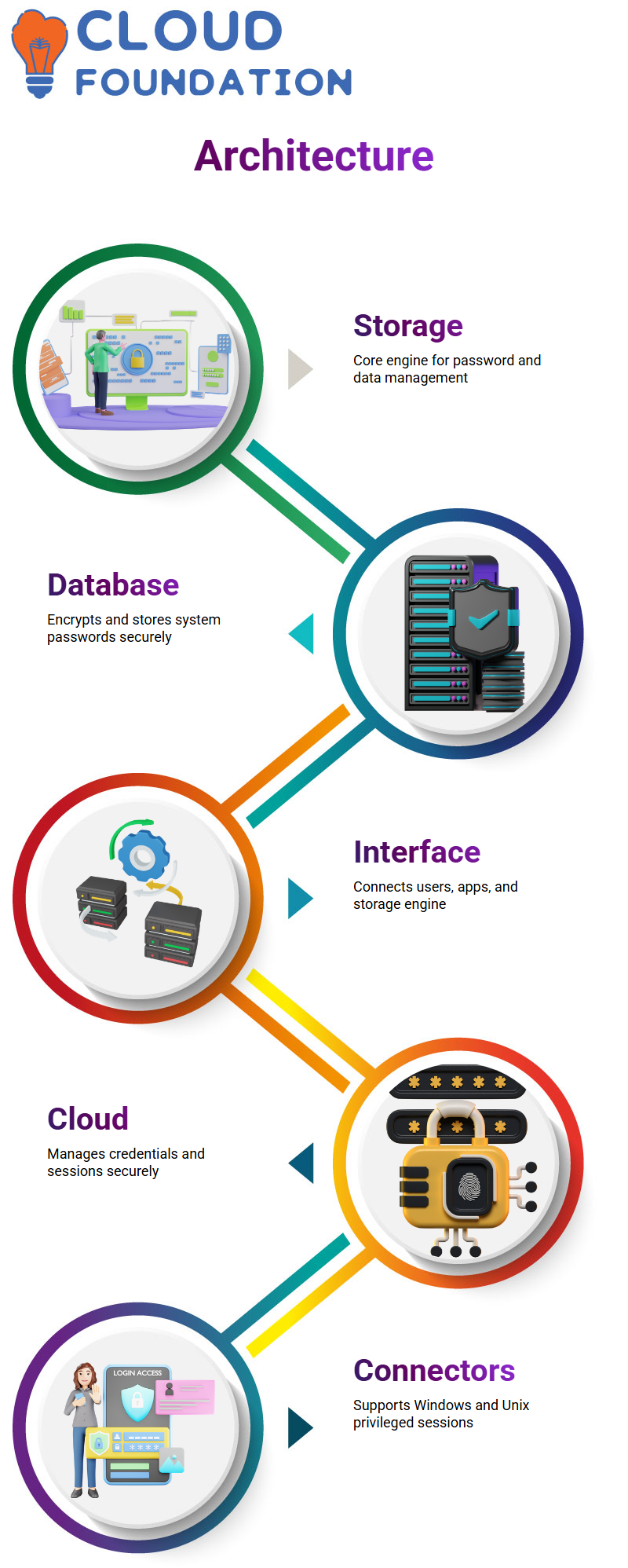
The architecture consists of following elements: Storage Engine – Storage engine is an essential part of the CyberArk tool and works as a tool’s brain.
The storage engine communicates with other components of the tool to perform various functions. It consists of following major functionalities:
Database
The database in the storage engine holds all system passwords. It also protects various passwords by encrypting and storing them in different files.
Interface
The interface’s job is to communicate with storage engine, users, and applications.
The database serves as a channel for communication between the storage engine & interface.
The interface, users, and applications all communicate via kernels of an operating system. The operating system’s kernel is in charge of providing a user interface.
Privilege Cloud architecture
Customer environment
The customer’s environment will consist of their own private network and computers that have been configured to meet all applicable security standards.
Privilege Cloud:
Privilege Cloud gives your company the ability to securely store, cycle, and isolate credentials (for both human and nonhuman users), manage organizational sessions, and deliver scalable risk reduction to an organization.
Client configuration for Privilege Cloud consists of:
Connector for Windows supports privileged sessions with Windows-based targets.
Secure Tunnel client, optional for SIEM Syslog and CyberArk Remote Access offline configuration.
The Unix connector allows privileged sessions with Unix host machines (PSM for SSH).

CyberArk Training

CyberArk Privileged Access Solution Architecture
Your company’s IT department, on-call administrators, and remote administrators, among others, will have a safe place to store, transmit, and exchange all administrative passwords thanks to the Privileged Access Security solution.
You can be certain that your company’s credentials are safe using Privileged Access Protection since it employs numerous levels of security (such as a firewall, VPN, authentication, access control, encryption, and more).
The Privileged Access Security solution is simple to implement and can be up and running in a short amount of time.
There are many application programming interfaces (APIs), a Web interface, and a Windows Client that may all be used to access and control a system.
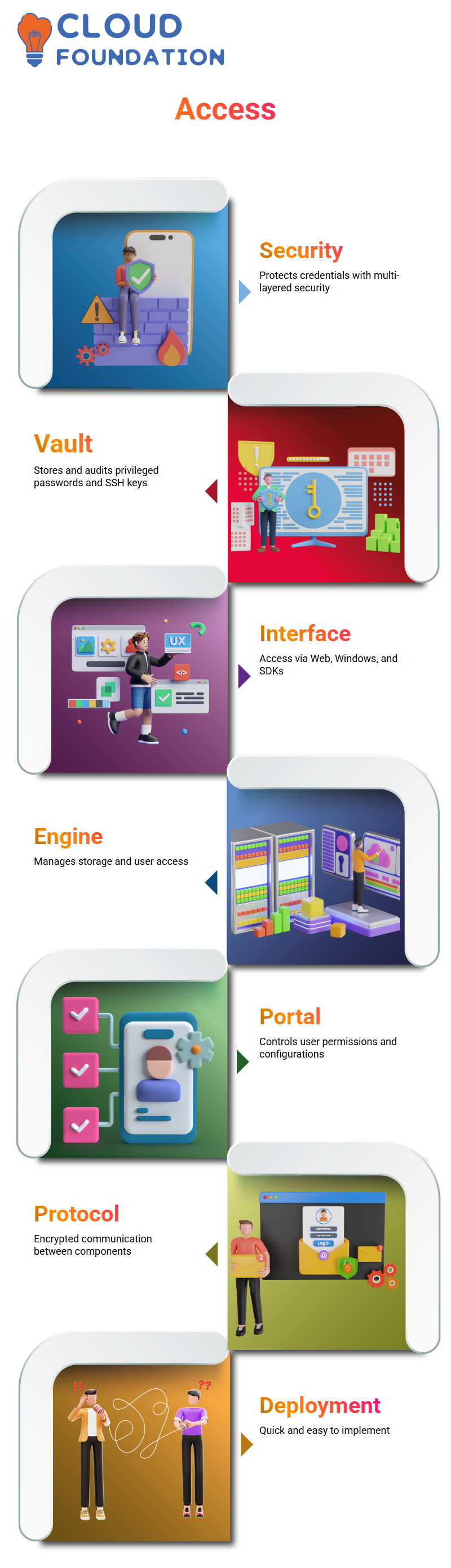
Privilege Cloud Portal is the interface for configuring and controlling user permissions to your company’s resources.
Vault allows businesses to store, organize, regularly update, and retain a full audit trail of all SSH keys and privileged passwords.
There are two main components that make up a Privileged Access Security solution architecture.
The first part includes Storage Engine (or “the server” or “the Vault”), which stores everything and is in charge of protecting it when it’s idle and granting authorized users access to it.
The second part is
Windows interface,
Web interface, and
software development kits (SDKs) that allow the Storage Engine to talk to users and applications.
CyberArk’s Storage Engine and Interface talk to one another through the Vault protocol, a safe and encrypted method of communication.
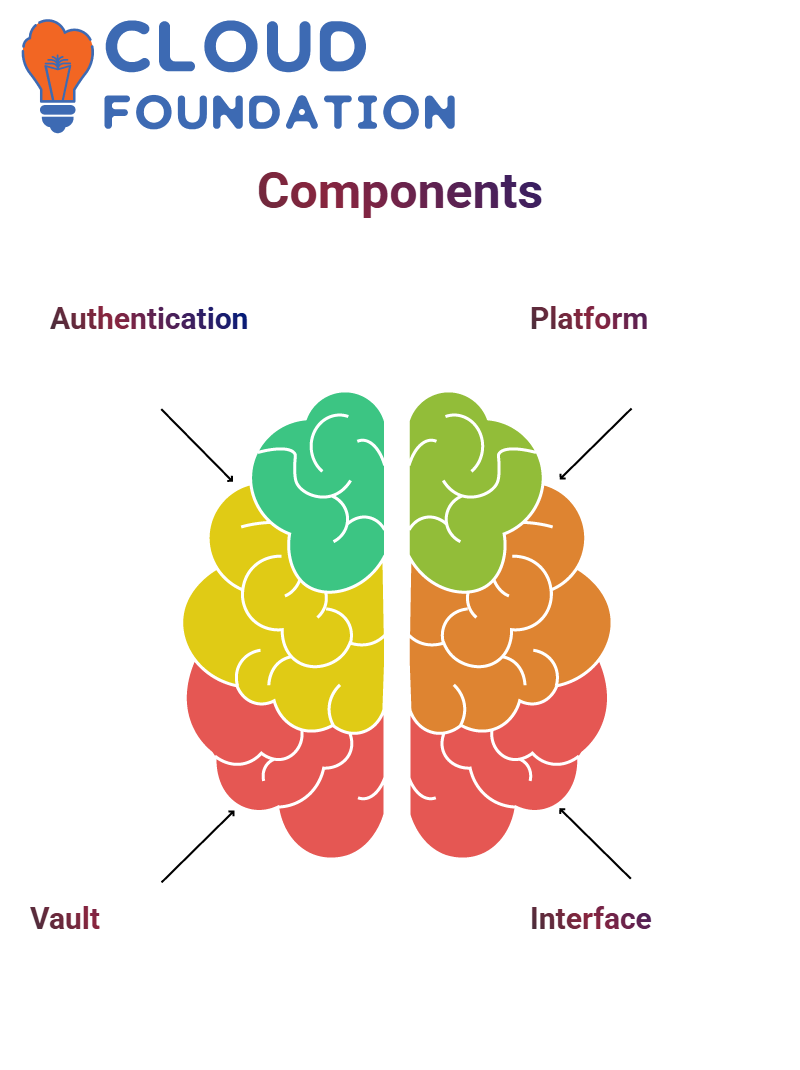
CyberArk Components:
Authentication Engine, Password Vault, etc.
Platform: On-Demand Interface: Web CyberArk Architecture
The following is a detailed description of various components of CyberArk:

CyberArk Online Training

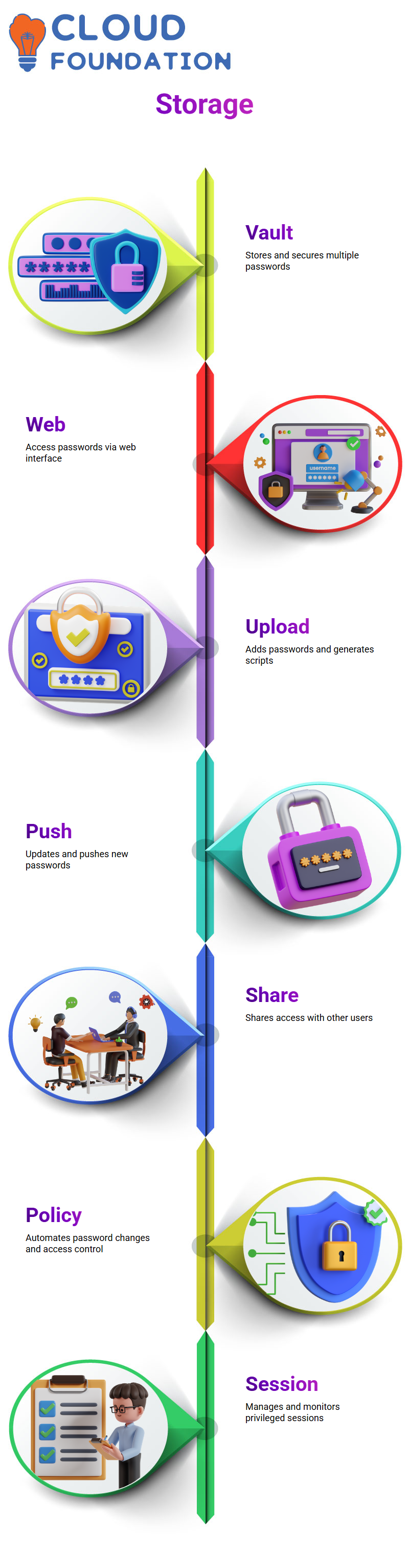
Storage Engine:
The storage engine, a server or vault, holds multiple passwords.
It also ensures securing the passwords and providing access to them as and when needed.
CyberArk Password Vault Web Access:
The password vault web access component communicates with the storage engine to add and remove passwords. It also provides access to passwords through a web interface.
CyberArk Password Vault Application:
The password vault application communicates with a vault web access component to add and remove passwords.
It also provides access to passwords.
CyberArk Password Upload Utility:
CyberArk password upload utility can upload multiple passwords to the privileged account security solution. It also generates script files that contain passwords.
CyberArk Web:
CyberArk web can be used to upload multiple passwords to the privileged account security solution.
Password Upload Utility for API:
CyberArk password upload utility for API can upload multiple passwords to the privileged account security solution.
Password Push Utility: CyberArk password push utility can push new passwords to the privileged account security solution.
It also updates existing passwords.
Password Share Utility:
The password share utility can be used to share access privileges with other users.
CyberArk Central Policy Manager.
This component changes old passwords automatically and supplies new passwords. It also takes care of monitoring and logging in to make sure that users are getting access to the accounts to which they are supposed to have access.
CyberArk Privileged Session Manager.
This component allows companies to have a controlled way of communicating with their clients and customers. It offers protection to privileged accounts by maintaining passwords automatically.
It also allows companies to have a single point of contact for all the privileged accounts, making it easy to resolve any issues. Privileged Session Manager for Web. This component allows companies to have a single point of access for all their applications and services. It also allows companies to have a consistent user interface and experience.
Privileged Session Manager for Web UI.
This is a web-based interface for the Privileged Session Manager, which allows companies to monitor and manage privileged sessions. It also allows companies to have a uniform way to interact with their users.
CyberArk Benefits
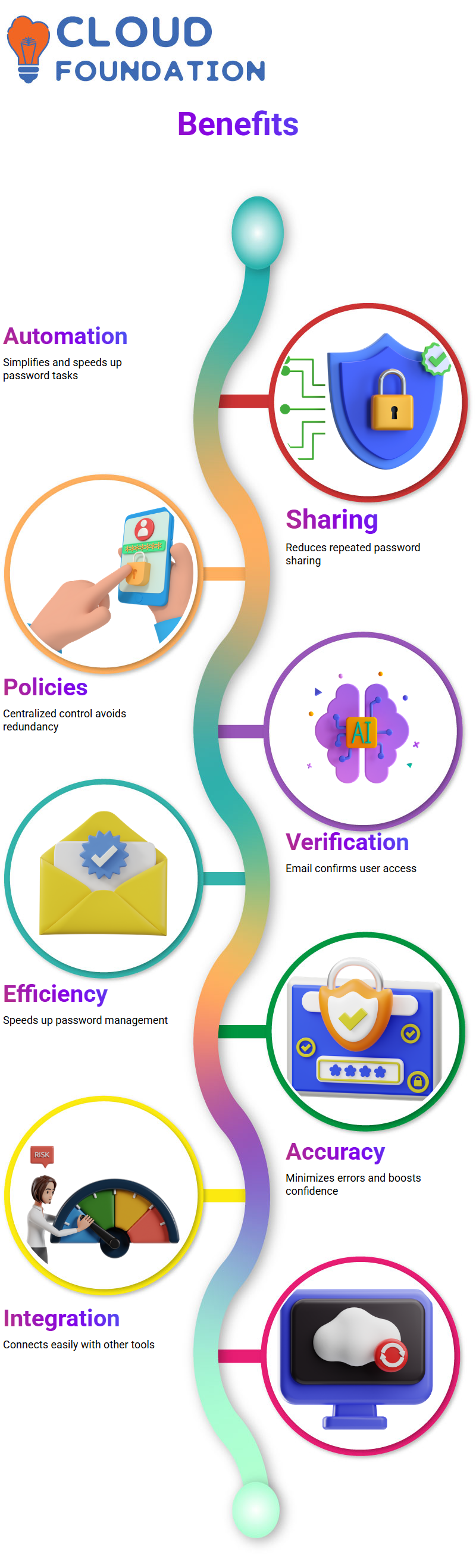
The following are the benefits of CyberArk:
Automated password management – CyberArk tool provides automated password management that simplifies a time-consuming task of password management. Also, it increases the speed of password management in organizations.
Increased password sharing – CyberArk tool provides a password management solution; there will be no need to share the passwords multiple times. Hence, there will be less time consumption in sharing different passwords.
Lack of redundancy in updating policies – CyberArk has centralized control over managing password policies, there will be no redundancy in updating policies.
Password verification through email – CyberArk software comes up with an email verification feature, and it becomes easy to confirm a user’s access and presence at a workplace.
Increased password management efficiency – CyberArk delivers an effective password management solution, and there will be less time consumption in managing passwords.
Increased accuracy and confidence in password management – CyberArk contributes less time consumption in managing passwords. Also, there will be less chance of error in password management.
Integration with other tools – It allows integration with other tools, and it becomes easy to integrate the CyberArk tool with other applications and services.
Digital Vault:
A digital vault is a secure place in the network where you can store your confidential data.
CyberArk Career Path
The CyberArk career path is designed to help you find a rewarding position in CyberArk. As you progress through your career, you will have an opportunity to work on various exciting projects using your technical and interpersonal skills and receive multiple training and mentoring. Software Engineer, CyberArk
As a member of a CyberArk team, you will be able to work on various exciting projects and a competitive salary and benefits package. Requirements BS in Computer Science or a related field, 2-5 years of relevant experience
Written, Strong verbal, and interpersonal skills Ability to multi-task.
Systems Engineer:
CyberArk Requirements
BS in Computer Science or its related field
2-5 years of relevant experience in written, Strong verbal, and interpersonal skills Ability to multi-task and prioritize Must be able to travel 20% of the time
Solution Engineer:
CyberArk Requirements BS in Computer Science or a related field
2-5 years of relevant experience
Solution Architect:
CyberArk Requirements
BS in Computer Science or its related field 2-5 years of relevant experience
CyberArk Open-Source Alternative and CyberArk Software Competitors
Following are the several Alternatives and Competitors of CyberArk Software.
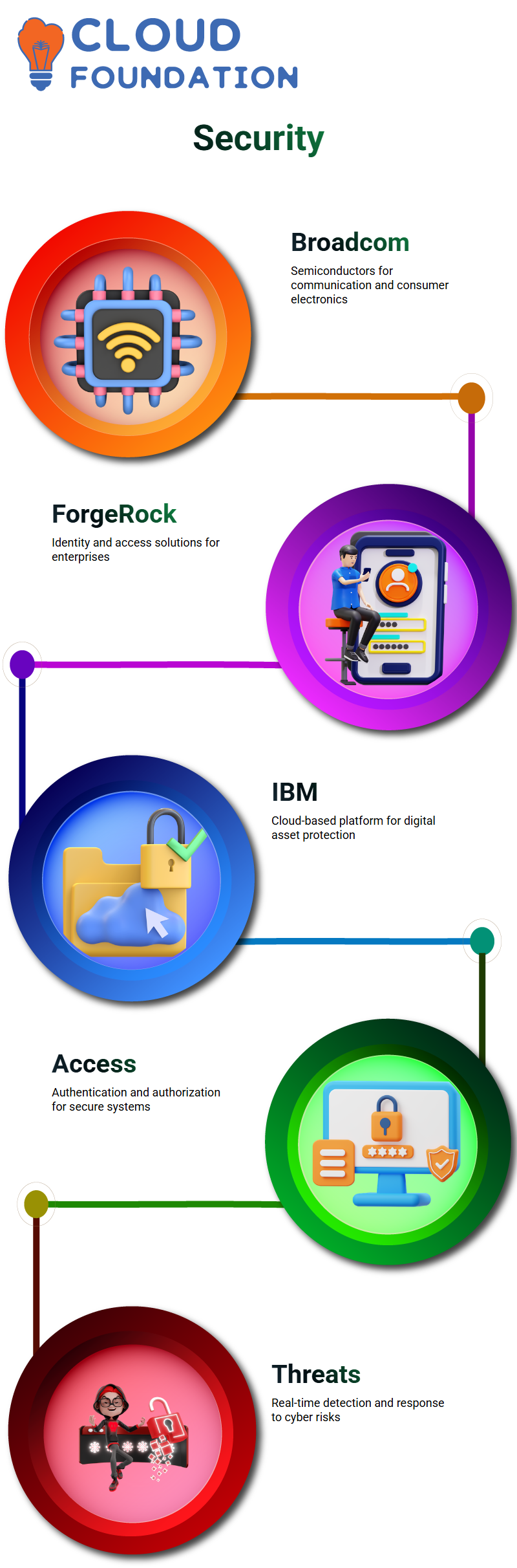
Broadcom
Broadcom is a significant semiconductor supplier of specialized integrated circuits (IC) for communication, networking, and storage applications. It develops processors, software, and chipsets for mobile phones, digital TVs, tablets, and other consumer electronics. Broadcom is a major Ethernet supplier.
ForgeRock
ForgeRock is a powerful access management, identity, and privacy service company that helps enterprises securely link people, devices, and things. ForgeRock’s identification solutions help enterprises build and safeguard customer trust and data. They serve giant corporations, government agencies, and small and medium-sized businesses.
IBM Security Verify Access
IBM Security Verify Access is a complete cloud-based technology that protects digital assets against cyber threats. It protects apps, data, and devices with robust security controls. Using
cutting-edge technology, IBM Security Verify Access detects and responds to cyber threats in real-time platform’s simplicity lets enterprises install the service without a security team.
Its scalability and flexibility allow enterprises to quickly their security procedures easily.
IBM Security Verify Access offers authentication, authorization, secure access control, data leakage prevention, and threat detection and response. It is very configurable, and businesses may tailor it to their needs.
IBM Security Verify Access emphasizes authentication and authorization.
Okta
Okta is a secure, single sign-on (SSO) service for organizations. Its cloud-based technology secures user identities, access privileges, and credentials across numerous applications, websites, and databases. It centralizes user authentication and authorization, letting users log in to different apps and websites with one set of credentials. Okta is a renowned IAM provider created in 2009.
RSA
RSA encrypts internet traffic. It is one of the most extensively used public-key cryptosystems.
RSA assumes factoring huge integers is hard. It encrypts data with public and private keys.
The private key decrypts data, whereas a public key is exposed to senders. A private key has two prime numbers, a modulus, and a distinct exponent. Two huge prime numbers multiply to generate the modulus & public key.
The private key can decrypt public key-encrypted data. This restricts data access to an intended recipient. A user must first construct two large prime integers (typically between 512 and 4096 bits) and multiply them to produce the modulus for an RSA key pair.
The user then calculates a number of a public key by generating a random number less than the modulus and relatively prime to it.
Secure AUTH
Secure AUTH helps organizations secure and protect their most important assets with identity and access management solutions.
Secure AUTH provides MFA, secure identification and access management, and more (IAM). Secure AUTH protects enterprises’ people, data, apps, and networks from harmful cyberattacks.
Ping Identity
Ping Identity is a corporate identity management and access control system that protects and manages user identities across apps and devices. Ping Identity, a cloud-based identity, and access management (IAM) system, enables secure, unified access to an organization’s on-premises and cloud services.
It lets administrators manage application and resource access. It offers single sign-on (SSO) for numerous applications. Users can log in once and access all their apps without reentering their passwords.

CyberArk Course Price


Shreshtha
Author