How SailPoint Native Change Detection Improves Identity Security
What is SailPoint Native Change Detection?
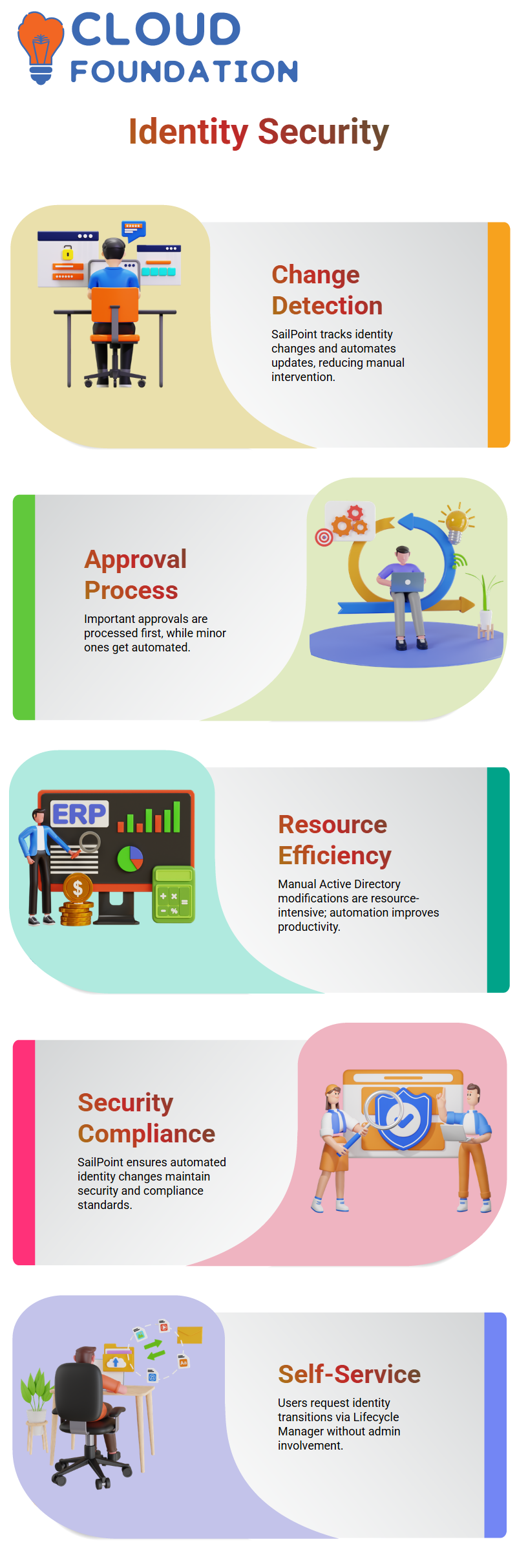
The native change detection tool is a significant part of the identity security process. SailPoint alters such services to best fit the customer’s needs.
Whenever an attribute is changed, SailPoint safeguards the tracking of alterations and takes the required actions.
By the action of SailPoint in automatically detecting and updating the original, manual intervention is no longer an issue, and the management of identity becomes more productive.
The act of manually modifying the Active Directory by an organisation can have the exact nature of being resource-intensive.
The way forward is to verify the transformations to be automated by SailPoint software while sustaining the required level of security and conformance, respectively.
With SailPoint, companies can make their approval process more competent – the most important ones will be processed first, while less important ones will be automated.
SailPoint Self-Service Form
Did you know Sailor also has an option of a self-service form? Taking advantage of this property is not prevalent, but it is pretty useful.
Through the proper self-service setting, users can ask for help without disturbing the admin. On the one hand, users who are not direct holders of the credentials can still have the power to request the transitions of identity by this one-time setting in the Lifecycle Manager.
SailPoint Audit Capability
SailPoint can keep logins, login attempts, failures, and user activities for auditing purposes.
Using the administering and related settings in the app, the system can collect indispensable data to affirm additional security and monitoring.
Other than that, it grants the use of security intelligence and analytics features for SailPoint users in surveying through missions and customs exhaustively and more easily, where compliance is concerned with saving valuable data for auditing targets.
SailPoint Audit Events
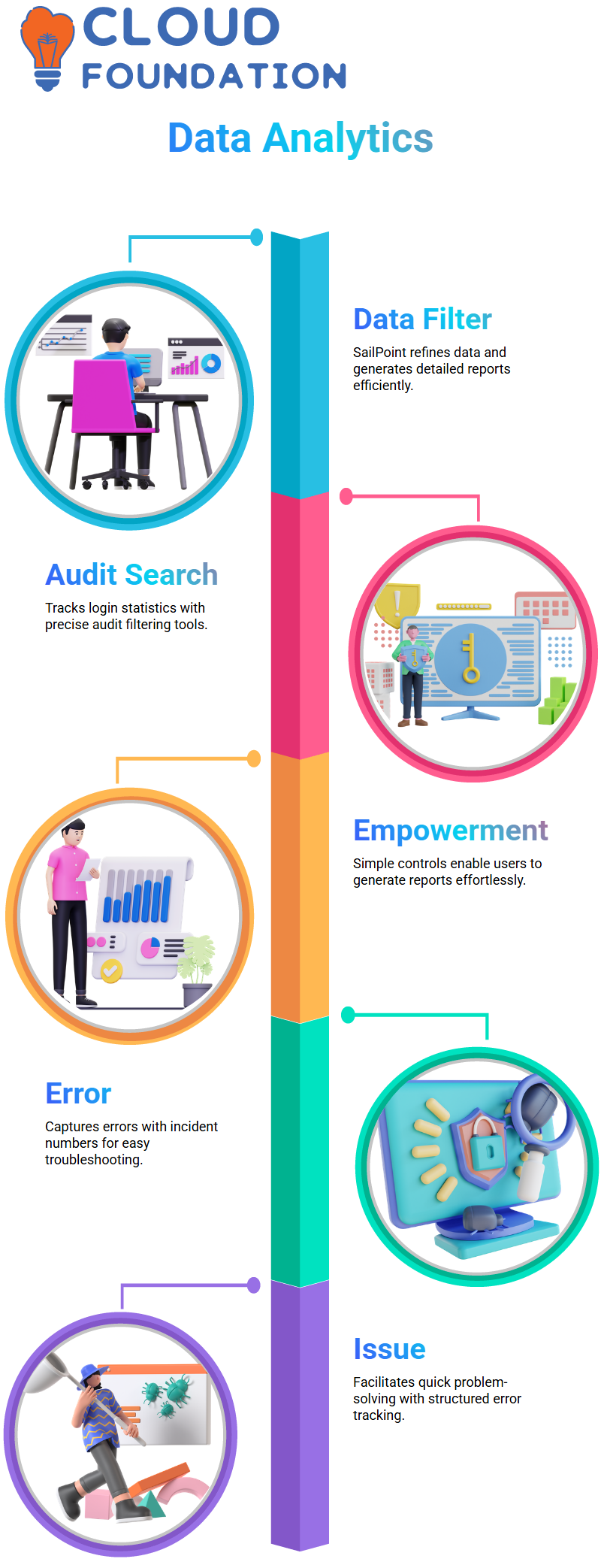
The process of SailPoint’s e-filing audit events. So, for example, if you want to track login actions, such as a successful login in or a failed login attempt, SailPoint records these events instantly.
It doesn’t make any difference if you log in as an administrator or successfully deal with the login failure problems. The SailPoint system will make these operations very simple. All a person needs to do is set the audit settings of the organisation, work, etc.
An occasion when activities like forwarding work items, conveying emails, or resolving email failures are performed would be created.
Not every task generates an incident; only those remarkably chosen to do so. By employing these solutions, data can be lodged in a way that is convenient for auditing.
This function is designed for both the process of fixing errors and the requirement of obedience; thus, it has become the most essential tool in the IT arena for a long time.
Use of SailPoint’s Sophisticated Analytics
SailPoint’s high-tech analytics can filter data, among other things, and produce several complete reports. For example, you can select a search type such as ‘audit’, which is perfect for limited searches of user logins and similar statistics.
SailPoint is also helpful in helping you with filtration, and you may know that you don’t even have to do much, such as executing the provoked button and beginning the report at your fingertips.
Such user empowerment is the primary reason conformance teams love this product the most.
Another characteristic of SailPoint is that user system logs include error message details.
In case of specific issues – a server crash or task failure –, the software captures the errors in the celebration alike. It gives them each an incident number and a short and sharp description of the cause. This makes the process of resolving issues capable and straightforward.
Correlation Rules in SailPoint
SailPoint helps keep identity management safe and straightforward by presenting a variety of tools that can be automatically matched through correlation rules. When working with identity traits, correlation is key in ensuring users get the right access.
Several times, we have a default setup that isn’t working, and we need standard correlation rules to do the job well.
SailPoint allows us to make and adjust these rules so that they are an exact match for the user’s identity.
I’m familiar with SailPoint, and premise correlation rules take a specific strategy; you can’t do whatever you want.
A sample is when a specific default setup with multiple features is not enough, where correlation rules are the ones that will come into our support.
By providing these rules, we can better explain identity and its compatibility with the system.
Correlation rules in SailPoint dictate the relationship of identities to application features.
Creation and Adaptation form in SailPoint
The most obvious way to do this is by using the Lifecycle Manager in SailPoint, where we can only change the forms through it.
When initiating a business process, we check if the forms function well according to SailPoint’s identity programming policy.
If a form is not set manually, SailPoint can auto-generate it at runtime based on the elements in the identity mapping.
Nevertheless, custom-tailoring the process is always a good idea to make it more expedient.
To build a habit form, go to the policy tab and specify traits like first name, last name, email, and password.
Save the form and see how it looks. This function guarantees that the collection of only imperative data is performed, thus avoiding unnecessary garbage.
Configurations in SailPoint
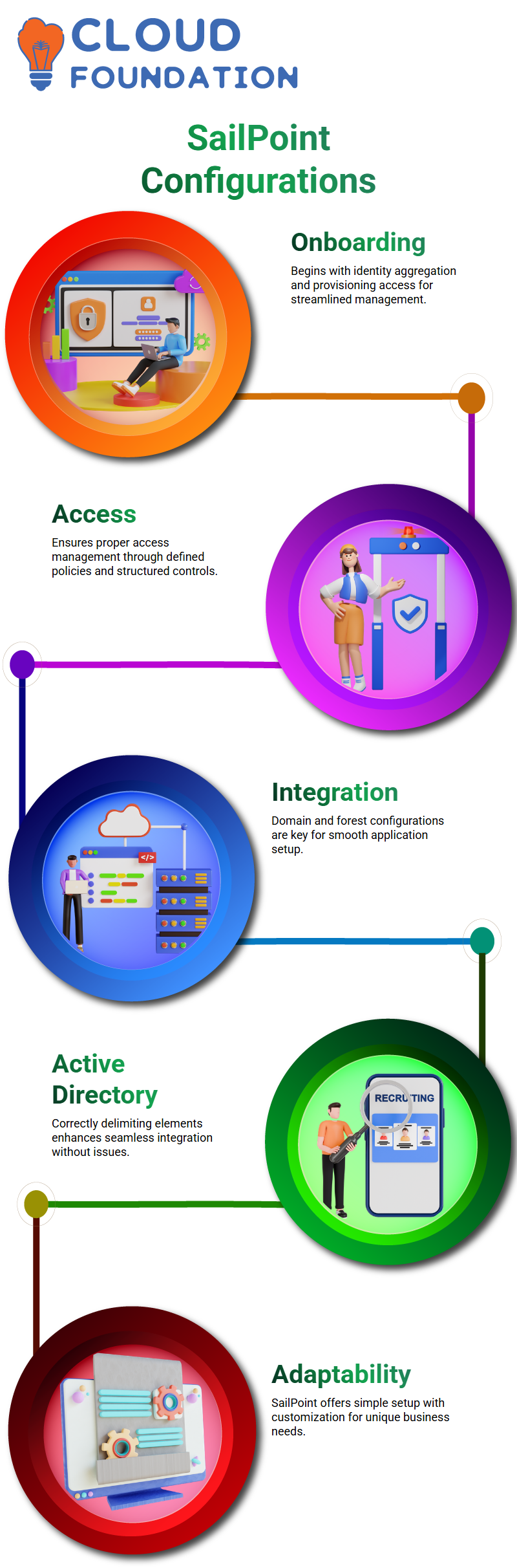
The first step in the application process at SailPoint is onboarding from scratch.
Once identities come together, it is time for access provisioning to begin. This is followed by establishing access management, and then policy definition comes.
SailPoint supplies a step-by-step procedure–from aggregation of identity to provisioning access, I navigate users through all the steps and ensure they understand SailPoint’s role leadership in multiple applications.
The configuration of SailPoint is a vital process in proficiently administering identities and access.
When a new application is installed in SailPoint, comprehending the domain and forest configuration is essential.
I have had numerous events in employing Active Directory, and I can confirm that one of the ways to delimit these elements correctly is the surest road to integration without hitches.
Rivalrous Edge of SailPoint
Compared with many other identity management tools, SailPoint is relatively simple to assemble and budget-friendly for medium-sized companies.
Although the levels of adaptation are lower, they are still good enough to be a rigid answer. Conversely, the bespoke alternatives are still available to influence how a product is developed and what it will do for an unambiguous solution.
Why Organisations Need SailPoint?
Organisations find it impossible to get their new employees onboard without the help of SailPoint or an abbreviated Identity management solution.
This is when the HR team is the first to formulate an account in their system and immediately informs the IT staff to make accounts for multiple platforms.
Refusing SailPoint would cause the process to be entirely manual, with the means of communication being emails or paper-based.
SailPoint Identity Variations
After a new occurrence occurs, SailPoint is constantly seeking those transitions in the identity field.
If the identity of a user is removed either unintentionally or intentionally from an object in the target system, then SailPoint acknowledges this change via the account aggregation process.
Account aggregation is a regular occurrence in SailPoint, running daily, and the shifts in the status of identities are updated in the system, which secures some revisions being flagged as unauthorised. This means that administrators are alerted to those adjustments they need to correct.
Deleted Identities in SailPoint
If SailPoint finds that an identity has been abolished from the target system, the identity warehouse logs the deletion details.
At the same time, the system updates the identity cube, which means that the link with the Active Directory application is broken.
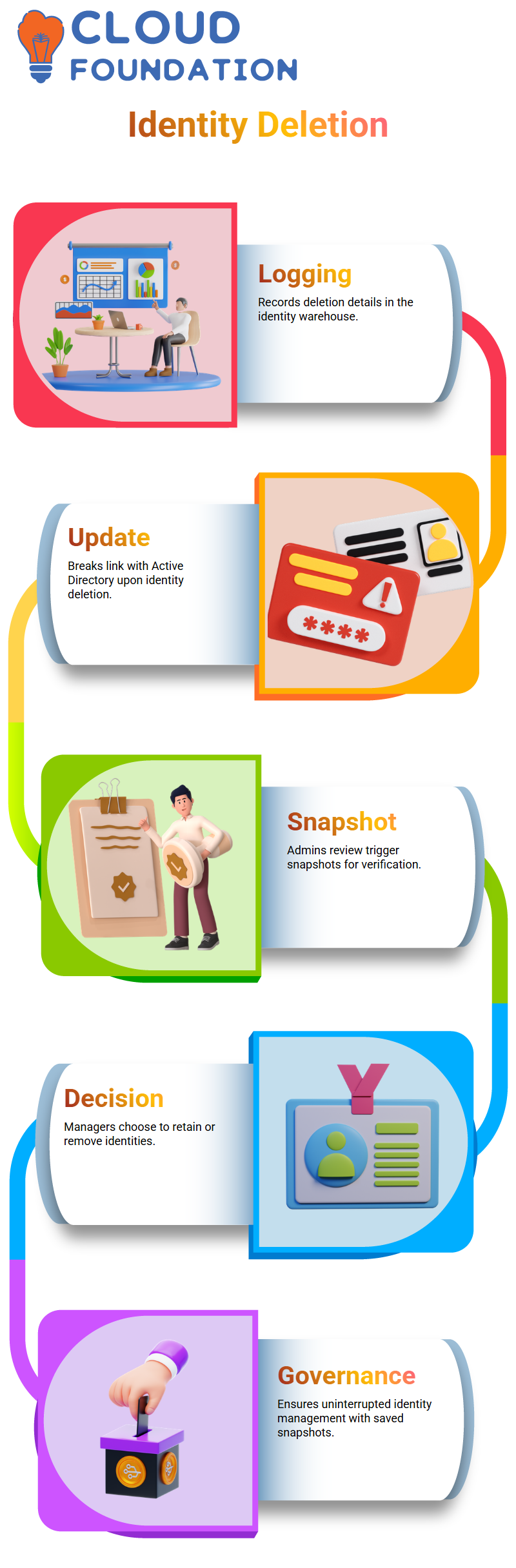
At this point, a created trigger snapshot could be reviewed by the admins to check if they agree with the revisions.
Managers can now decide whether to keep the identity or agree to delete it. SailPoint creates and saves snapshots to verify uninterrupted identity governance.
Why is enforcing concurrency in SailPoint Important?
Even if not always imperative, certain business circumstances may require that a person be able to administer the same job multiple times simultaneously.
SailPoint can do this. It allows users to change the execution of the tasks that suit their special needs.
Host Selection and Monitoring in SailPoint
The software permits the users to pick out a server where the tasks can be executed, thus carrying out the functions with the best possible load distribution.
Administrators can keep tabs on the performance of the task and take corrective actions by using the number of previous executions and the average runtime as metrics, since they provide factual data.
Email Messages for Task Monitoring in SailPoint
In addition to instant alerts internal to the application, SailPoint can also use email announcements to keep track of the task in the centre.
Administrators can set up email alerts to a particular recipient or group of recipients, making monitoring more productive and finding help in time. By employing an email template from SailPoint, users can alter their signals in different circumstances.
Users can view task statuses through the administrator console and change the task type to email, where any status shifts are communicated as emails.
SailPoint also has this quality to verify if the task was triumphant or if any failures occurred, and the system will ensure that only those nominated as recipients are kept informed.
Profiling of SailPoint Reports
With SailPoint, you can employ the built-in reports, which are presented by default and should not be touched.
Another version can replace an existing one when the need for an adapted report arises.
Debugging via XML, developing scripts with Java or SQL concerns, and securing data directly from the database are some ways to solve the problem.
Let’s discuss usage reports in SailPoint. Intuition of the database tables will be helpful and easy for the norm report creation, if the data is structured. One of the ways is to take the XML of an existing report, then individualise it, and then put it back into the system.
After creating a ritual report, it appears among standard reports and has streamlined integration into the reporting system.
One way to run a SailPoint report is to generate original typed data in tabular form, where each row determines a distinctive incident. For representation, if a policy violation report is to be executed, it will provide totals of violations and breaches related to identities and give implementable steps to remain compliant.
Another point is that policy violations can also be a part of the certification. This integration between policy violations and certifications improves audits and supplies all the mandatory data from the back end instantly. Reasonably, reports like policy names, the violator’s identity, association, and status are displayed.
Classification of SailPoint Reports
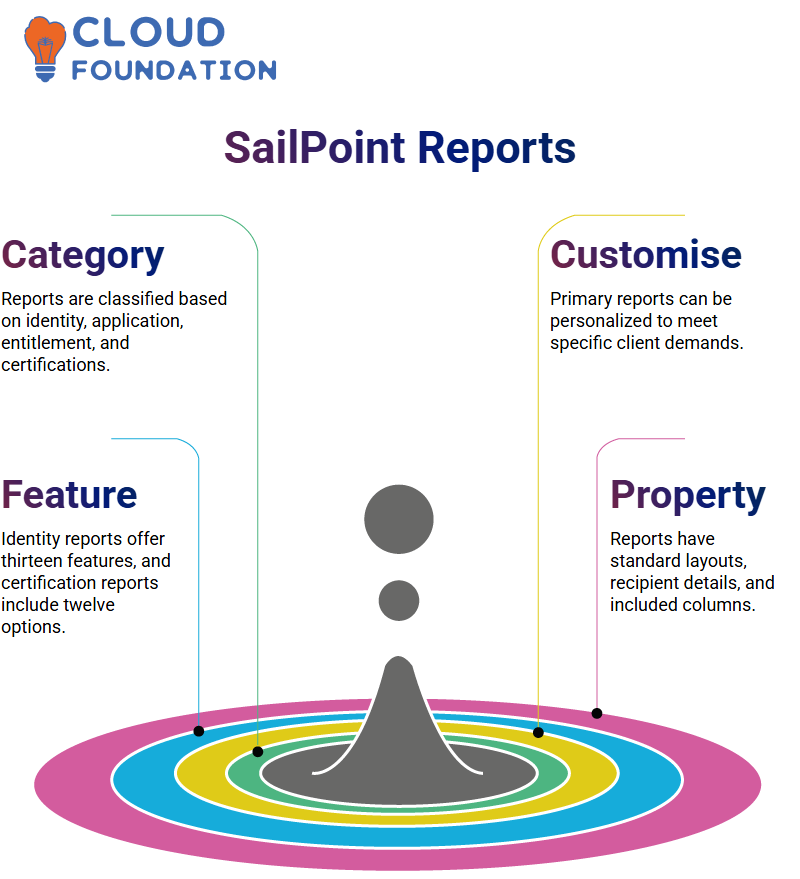
SailPoint reports are classified into several categories.
Based on the client’s demand, you can develop papers rooted in the identity, application, entitlement, capacities, certifications, and other objects.
Depending on the stipulations, the system has some primary reports that can be personalised.
For illustration, if the customer asks for a certification report, SailPoint suggests twelve reports in the access.
Examination segment. Besides this, identity and user reports have thirteen features, and entitlement-related reports are also given space for their development.
SailPoint Report Properties
Every report of SailPoint comes with the usual properties and has a report layout. Standard details in the report’s context are the report name and the recipient’s and included columns’ data are provided.
Excluded data, such as the prototype’s first name or any redundant data, is no longer vital and should be erased to keep the report fixed.
Property settings are different for a range of types of reports. For example, a policy violation report will have quite different properties from a certification-based report.
Playing with these parameters results in rich and exact data retrieval that sticks exactly to your reporting needs.
How Important is SailPoint for Companies?
SailPoint deconstructs identity management by ensuring employees get access at the right time. This avoids unauthorised entry and raises security.
SailPoint is not like gloves; it is one size for all, but it conforms to the needs of the business. The system is devised for flexibility.
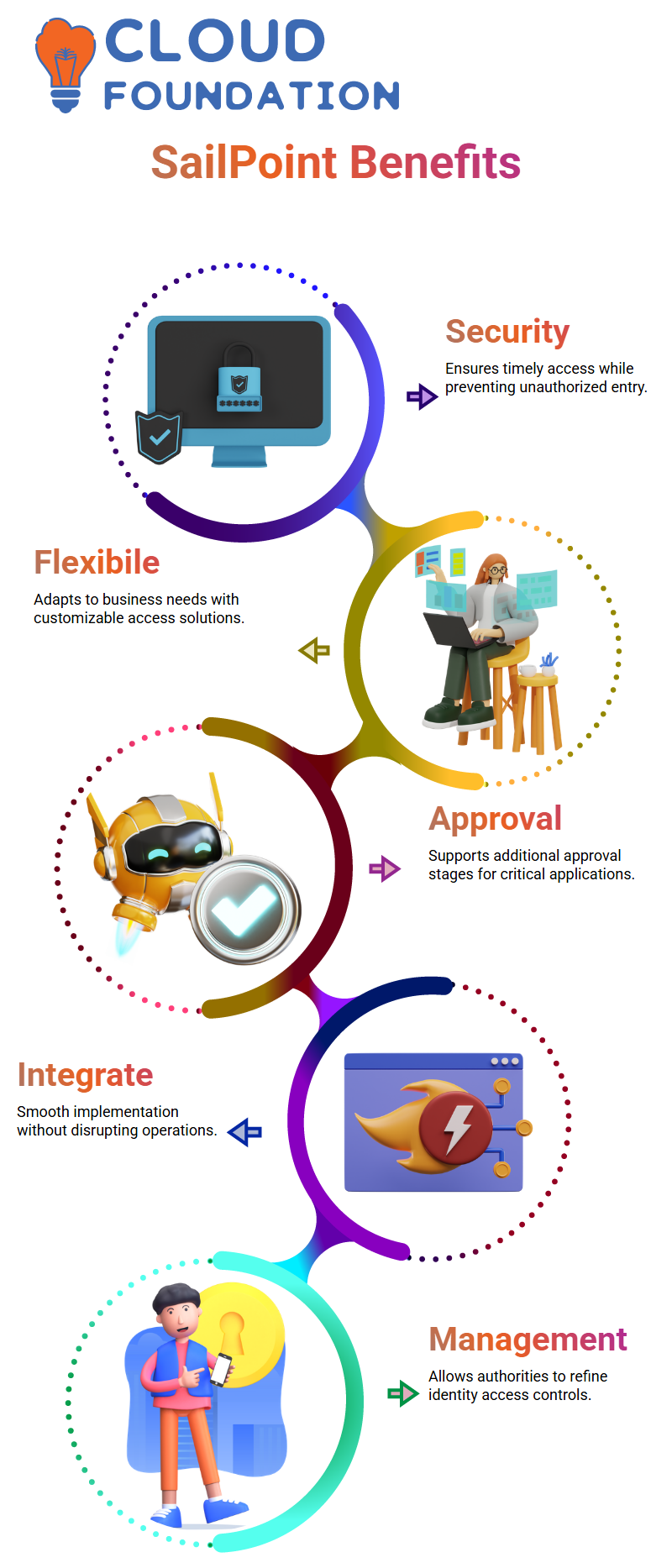
For example, if a company needs to implement a new approval system, SailPoint can provide this quality to such a company.
To give a case, one corporation may necessitate an extra approval stage for access to their essential applications.
Distinct from their SailPoint management, authorities can apply these improvements smoothly so that the running operations are not disturbed.
Business Process in SailPoint
As previously discussed, the business process was delineated, and when users click on certain elements, the method is triggered.
We have also discussed the configurations of these workflows to fit your needs. SailPoint is capable of the entire process smoothly, through automation and expediency.
Next, I’d like to go over forms in SailPoint.
A form displays itself as soon as you click the identity screen, but do you know the form generation and modification process in SailPoint?
SailPoint Features for Businesses:
SailPoint is a solution for customer needs that gives user lifecycle management, password management, workflow management, and audit reporting features. All in all, a very aspect-rich identity management tool.
The tool also bolsters organisations to have control of characterising group access, managing the agreement policies, and conducting the risk assessments task.
It’s not only a question of the control of identities. It’s about the expedient and safe way of doing that.

Navya Chandrika
Author



