What is Sailpoint Provisioning?
What is SailPoint Provisioning?
Provisioning in the SailPoint is the stage where the access rights are defined and managed.
The SailPoint is the one that makes the decision each time the access request is given or a certificate is generated that there is a new access or the old one is being revoked Footnote: It is one of the provisioning basics in SailPoint that the approval is supposed to be included in the process which is why the first step must entail a complete decision of whom; M. Baressi, “Prowess SailPoint Provisioning and Workflows,” October 2018.
In the setting with SailPoint provisioning, a key point to remember in the first phase of the process is usually creating the provisional plan.
Approval of provisioning, successive user-to-employee transition, and final confirmation of the user is a substantial part of the process that SailPoint supports itself through to retain the security and submission levels.
Provisioning in SailPoint guarantees the proper access to target systems to be undertaken by the users who have requested it.
The process is drafted with predefined workflows to control access approvals, policy checks, and provisioning steps.
In SailPoint, we set up the provisioning settings to automate access provisioning. This implies that the provisioning function is kept in the application settings to guarantee that the system works as it should.
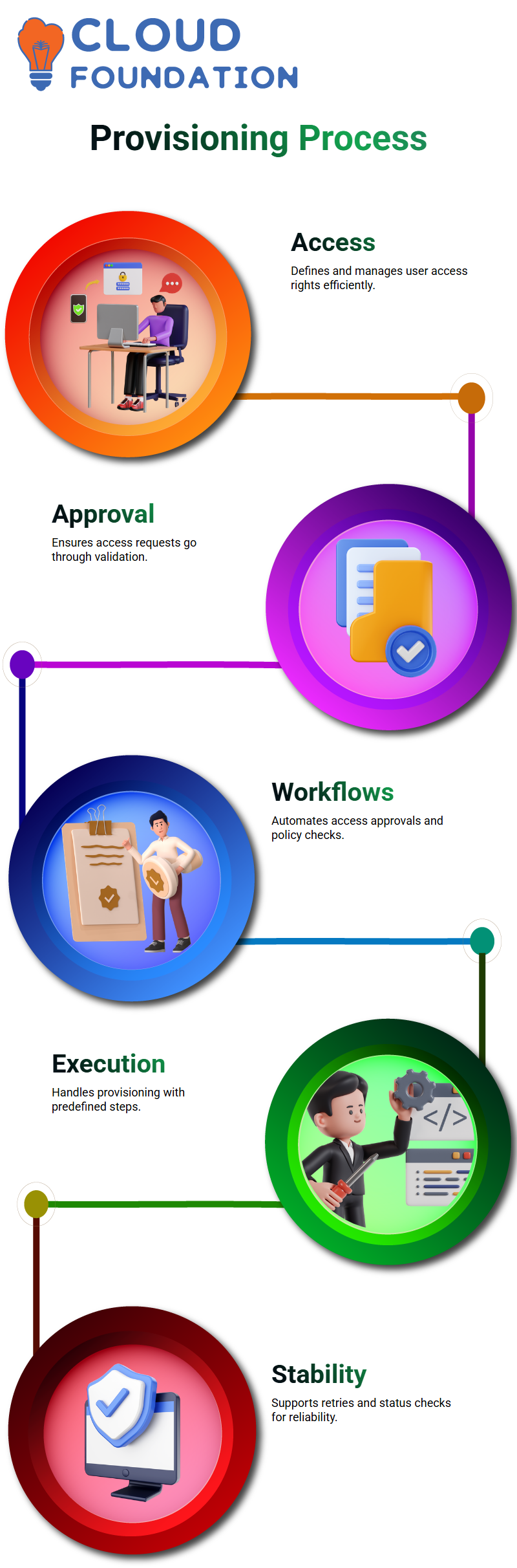
SailPoint Provisioning Procedure
The provisioning procedure in the SailPoint system comprises many sub-processes, which refer to identity request initiation, approval gating, provisioning execution, notices, and finalisation.
These workflows confirm productive access management.
The provisioning system in SailPoint has the first part of approval determinations and approval execution.
When approved, the system goes to the provisioning plan.
SailPoint requires manual operations for disconnected applications to ensure the procedure is executed correctly.
The procedure enables retries and status checks, guaranteeing improved stability.
SailPoint Identity Request System
The point of departure of identity request initiation in SailPoint is provisioning. Variables play a vital role in variations that can be adjusted based on the security policies at that time.
The first step of SailPoint’s main procedure is to start the identity requests, and the second step is to go to the next step, in which tickets will be created, encompassing surface ticket IDs, to confirm a flawless process.
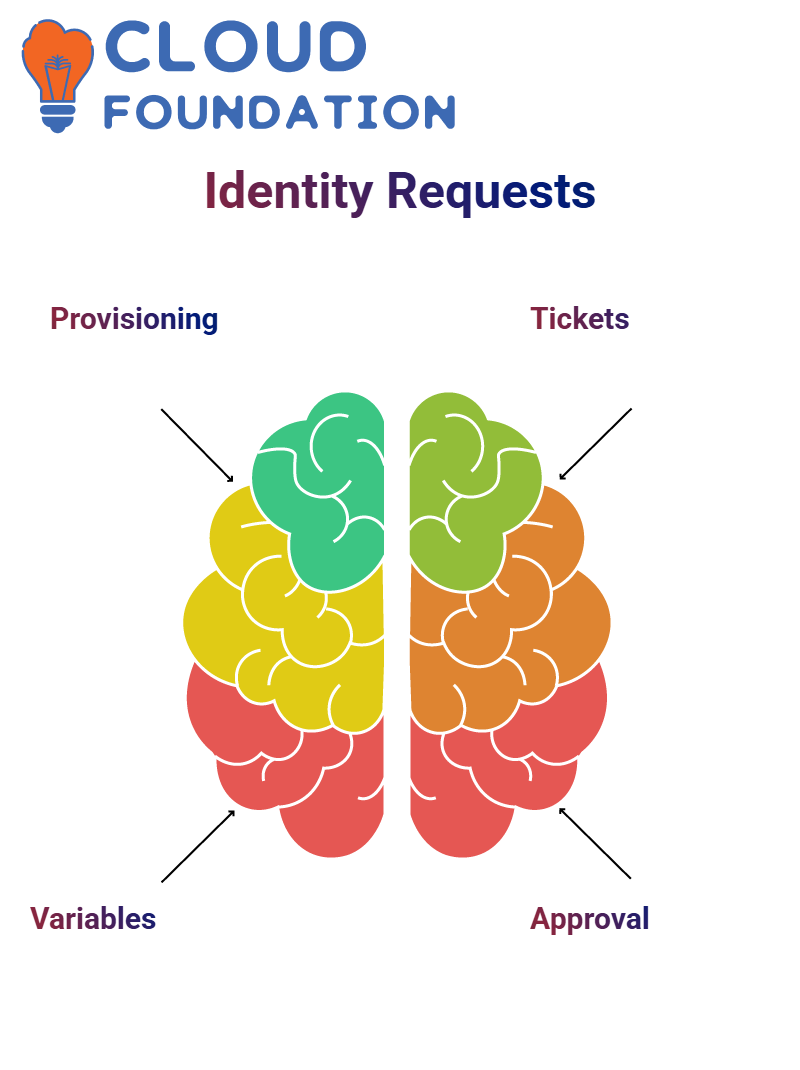
The second step of the operation encompasses approval provisions in which SailPoint matches the approval plan and then drills down into its execution for provisioning approval.
SailPoint LCM Provisioning
This is the innermost LCM provisioning system in the SailPoint system, which is the central framework that governs all the issues about identity management& Identity requests are based on the system’s sequence triggered by each user and through this the fitting SailPoint variables are also configurable for any transitions required for the device or system in that process.
Variables in SailPoint Workflows
Approvals are key in SailPoint and are thus the first among the variables going through the manager, the next being the owner, and the last being the security officer.
All the steps of the method are clearly described to ensure that activities such as provisioning approval and fallback are done regularly.
Access Requests in SailPoint
SailPoint makes access request management more manageable and faster. Users start access requests that the system processes through the previously set configurations. Whether there is an active directory setup or a relatively large-scale provisioning request, SailPoint automation guarantees smooth operation.
The provision is automated by SailPoint, leaving the creation of accounts in the hands of the admin and setting passwords without the need for users’ consent.
Consequently, the employees’ managers are informed of the new employees through a system of automated e-mails, which streamlines the process of employee onboarding.
People with the talent to be SailPoint customers must know exactly how it creates and leverages Active Directory accounts.
By exploiting the perfect settings, companies can fabricate access controls that do not affect the smooth operation of the business in terms of performance and safety.
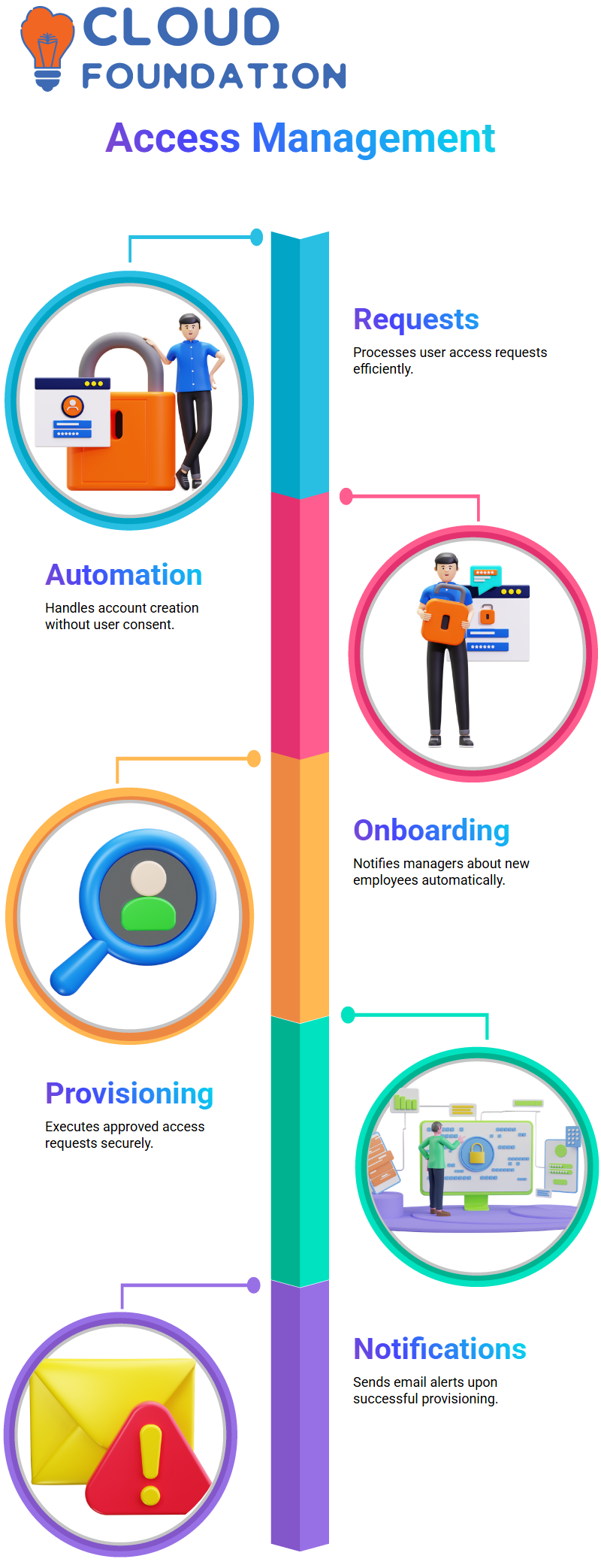
How the Provisioning of SailPoint is Carried?
Through the user’s request for access, a SailPoint fit-up process is initiated for the plan towards the final provisioning of the user.
First, the plan gets generated by gathering all the necessary imperative factors. Thereafter, the approval process occurs.
The process is then carried out after approval, and the access is rendered flawlessly.
Upon achieving the provisioning, an email notification is sent. Every action is essential in the SailPoint process, provided that it is manually performed or automatically handled. This way, access is safe and swiftly offered in a minimum time.
SailPoint Provisioning Failures
Are you ready to discover the circumstances of provisioning failure in SailPoint? If you have already met such a case, I can help you to see if it’s provisioned and, if not, how to operate it.
Under the administrator console’s provisioning tab, you can resolve anything connected with provisioning-related tasks.
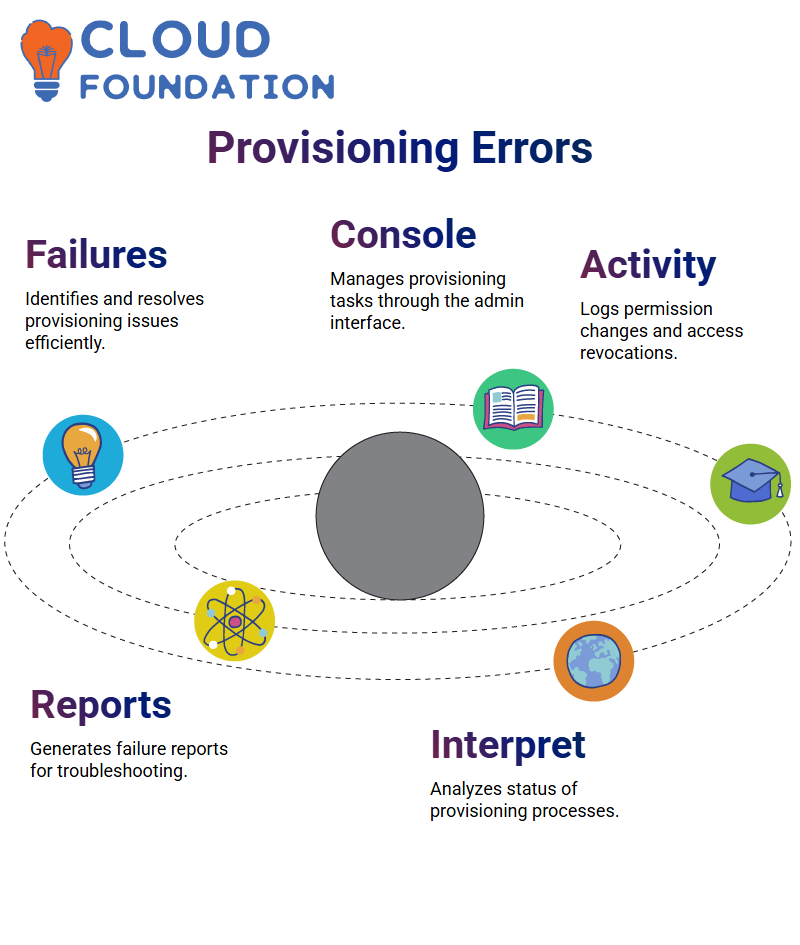
The software system will also register all the activities like LCM, for permissions for access or revoking the permissions by the certifications, with the help of this administration interface.
Currently, I have set for only one failed provisioning demonstration If I want to consent to to work also other processes, like for illustration, success or pending, I also have to interpret them.
It is straightforward to get reports on Provisioning Failures from SailPoint You have to choose ‘failure’, and the object report will be automatically downloaded.
SailPoint Provisioning Transactions
With SailPoint, you can individualise your provisioning transaction logs. Such individualisation can be done via planetary settings where you can select identity configuration, thus enabling the logs for the achieving, pending, or failed transactions.
This way, there is no doubt that you are constantly monitoring the provisioning activities in SailPoint.
These logs are obligatory to generate regularly.
Most of the time, customers are keen to know the ins and outs of all provisioning activities that are taking place, and with the help of SailPoint, it is a piece of cake to get hold of this data and share broad reports.
SailPoint Trigger Snapshots
The trigger snapshots are a part of the identity debug page, organised by SailPoint. If one needs to prove someone’s identity, one can visit SailPoint’s interface, where the most recent snapshots will be found.
The snapshots in the identity debug page show us the revisions made to the identities over time. Each change made to an account is captured by the snapshots.
Identity snapshots are incentives that empower the organisation in the management of identities. SailPoint follows a model where an episode automatically generates a snapshot, while the snapshot stores the change for future use.
Capitalising on this process, the administrators can watch the variations in identity in a structured way without any manual intervention. Those snapshots depict a change in an identity, highlighting the transformation history of the identity in a structured form.
The area of identity management system in the SailPoint system acts as the mentor in the process of tracking and managing identities expediently.
Each time a trigger snapshot takes place, SailPoint is responsible for storing that data such that when an underlying change occurs, the updates are managed by the backend in a smooth way.
The manual updating task of the employee data is avoided by capitalising on the trigger snapshot mechanism of SailPoint.
The ever-changing, broad-based condition of SailPoint guarantees that the substantiation checks required for workflows to function optimally are performed continuously.
As a SailPoint solution architect, I primarily focus on creating and applying those distinct workflows that will satisfy our clients’ objectives.
In SailPoint, verifying workflows is confirmed by capturing trigger snapshots at varying stages through the system and then employing them in a structured analysis routine called sequence mining.
Snapshot Stimuli in SailPoint
During the process of method completion, SailPoint creates snapshots
These pictures accentuate adjustments in identity insight, which native users make. Each time a picture is taken, it generates one snapshot; this certifies that SailPoint can cover major identity updates.
The essence of snapshots in SailPoint is to verify provisioning success. If an access request is mistakenly sent, the snapshots can be reviewed to locate opportunity misconfigurations.
Provisioning Plan in SailPoint
SailPoint identity workflows are mainly composed of the provisioning plan, which contains instructions to be followed during the provisioning process.
When an identity is set up in the system, SailPoint gathers and begins approving the provisioning plan. This, as per the plan, is done without human intervention.
To verify whether the identity and attribute updates work correctly, I have connected the logs of SailPoint to get data about the passage of a value in a method context.
If a problem arises, the log files contain this data, reflecting the situation initially.
SailPoint Business Process
SailPoint, besides business processes that make organisations arrange the identity management workflows, if high-tech users have no exposure to SailPoint, they can enjoy immense benefits by exploring these processes that make provisioning management more resourceful.
Policy Checks in SailPoint
At SailPoint, it all starts with the policy check. The existing policies are then used to produce the new approvals. With this method, the required approvals will be gathered.
Owners giving the green light to items is one option, whereas the ones refusing are the other allowed possibility, and SailPoint takes this evidence to alter the approval set, creating. At the same time, in parallel, audits are triggered to establish identity requests.
SailPoint checks Policy Violations during provisioning to guarantee conformance. Organisations might, in case predefined variables are not satisfied, adjust rules to make an access control solution more flexible and accept the risk, thus still complying with the policy.
SailPoint in Real-Time Projects
SailPoint usage for the real-time projects is dominant in creating Active Directory accounts, accounting for as much as 90% of the total situations.
By applying automation, access provisioning becomes less involved, and businesses can adhere to the standards that have been set. Applying SailPoint, companies can develop productivity without adjusting security.

Navya Chandrika
Author



