What is SailPoint Password Policy
Introduction of SailPoint in Identity Management
Each time a company hires a new employee, a mandatory condition is to give them access to financial applications very quickly. SailPoint is the one responsible for it.
We put the logic into the joiner celebration to verify that the account holders are created inside SailPoint uniformly.
Instantly, when the joiner incident is loaded, SailPoint starts an account creation process across the entire set of multiple identity systems.
Among the many payroll things and several authentication contrivances like Okta, SailPoint carries out a smooth onboarding process that aligns with organisational authentication standards.
In SailPoint, identities are derived from corporate sources, that is, authoritative systems or curated ones.
If employee details come from these sources, they are represented as identities.
On the contrary, if data is obtained from applications, it will be kept separately in the identity section.
These few words are enough to know that SailPoint is the one that will help you identify those to whom you are giving access and security, and deal with it too.

SailPoint Identity Snapshots
Have you ever considered how SailPoint maintains its identity records at different times? While pursuing the individual timeline, the system stores identity snapshots like photos. A way of recording every action, for example, account creation, update, or removal from the servers. It precisely reflects when the change was taking place.
In SailPoint, the colour green reveals the given access, and the removal of access is marked with red A visual distinction like that makes it easy to grasp the identity change instantly Still, there would be a case that dealing with the whole history of SailPoint feels more like a maze than securing to a definite point of change.
Supervising Identity Filters in SailPoint
SailPoint’s identity filters are inherently intended to make setting the scope of policy surveillance on a subject basis for the users, if a corporation opts for representation, to have the password connotation only for the sub-groups, these filters can be used.
Generally speaking, setting up the identity filters characteristic by SailPoint leads to a situation wherein the policies get enforced right across the board to the suitable users, across all the particular applications.
SailPoint Password Synchronisation
Aggregation is a key aspect of SailPoint, which lets the company pull identities into the system. During this fashionable step, password rules can be automatically enforced to comply with all the applications’ regulations.
On the other hand, synchronisation might differ. For example, the passwords have already been set for the application users.
Upon the implementation of SailPoint, the first thing a company has to do is decide whether synchronisation is required or users have to reset their credentials.
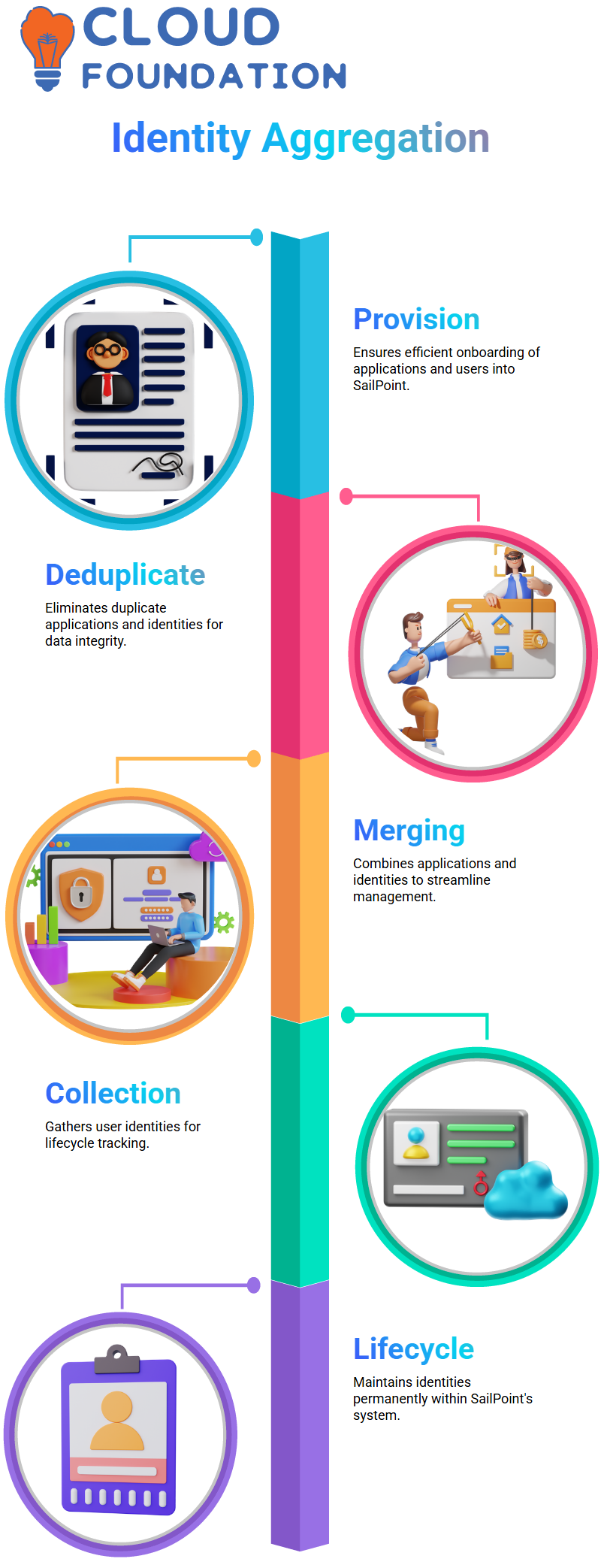
SailPoint Aggregation Methodology
Aggregation is the utmost priority for the capable provisioning of applications and users into SailPoint, and junking duplicates is the primary emphasis of the process.
Think about the case of being a replacement.
Firstly, by moving an app to SailPoint, we ensure it is not duplicated anywhere. The app is merged, consumers are collected, and the identity lifecycle is permanent.
SailPoint Applications
Enacting the Application Onboarding process with the SailPoint tool involves not just adding new accounts.
It involves consolidating accounts or users spread across multiple sources into a single dock, while maintaining the identity data of the…
Imagine a case in which an employee must be smoothly onboarded in five applications, each of which. Should administrators not want to create duplicates, SailPoint will allow them to link identities accordingly.
The SailPoint system enables identity reconciliation across various applications, facilitating efficient access management. Had there been duplicates, SailPoint would have appropriately linked them.
SailPoint Quick-Links
SailPoint introduces the concept of quick-link populations, where organisations can regulate who can see and use clear-cut features. The primary objective is to ensure that the ‘right’ people are present and do not have access to unnecessary infrastructure.
For example, supervisors are the only staff who can run accounts and passwords. ‘Supervise Accounts’ and ‘Supervise Passwords
These preset settings prevent attempts to carry out illegal operations while allowing for mandatory transitions.
Requesting and Tracking Access in SailPoint
SailPoint recommends a robust tracking system that enables users to view their access requests.
The SailPoint tracking system is unusual, making it easy to inquire about the status of an approved item instantly.
Therefore, a detail that brings transparency will ensure that employees are aware of the timing of their requests and can receive instant notifications when they are rejected.
On the other hand, the ability to administer accounts and entitlements significantly reduces operational costs and increases compliance.
SailPoint Password Policy Management
The password policies give a security framework for the users in SailPoint
Otherwise, security breaches may occur while a system is configured if password rules are not enforced. Some of the regulations include fixing the minimum and maximum character limits, employing upper and lower-case letters, and entering characters that are not letters
SailPoint is a tool that organisations use to create password policies that match the security standards.
By moving to the policy creation area, administrators enabled themselves to make policies fitting the role of the company’s client.
Creating a logical password policy in SailPoint is a piece of cake. The admins can list things such as the length of the password, the types of characters to be included, and history rules that would prevent the reusing of passwords.
The settings are straightforward, and taking advantage of SailPoint’s interface is effective for organisations’ submissions. Furthermore, the policies can still be implemented through other means of these tools, like Eclipse or object browsers.
Discernment Identity Management with SailPoint
When dealing with identity management for a company, SailPoint’s operations are structured around requests for access and user creation, in particular. With SailPoint, account identities are not only managed but also, simultaneously, tasks that are not carried out manually by members.
Using SailPoint, I can easily submit access requests. I began by ensuring that each identity was accepted and verifying that every worker, contractor, or peripheral contact was listed. The system enables me to conduct identities smoothly and establishes that they are under my watch.
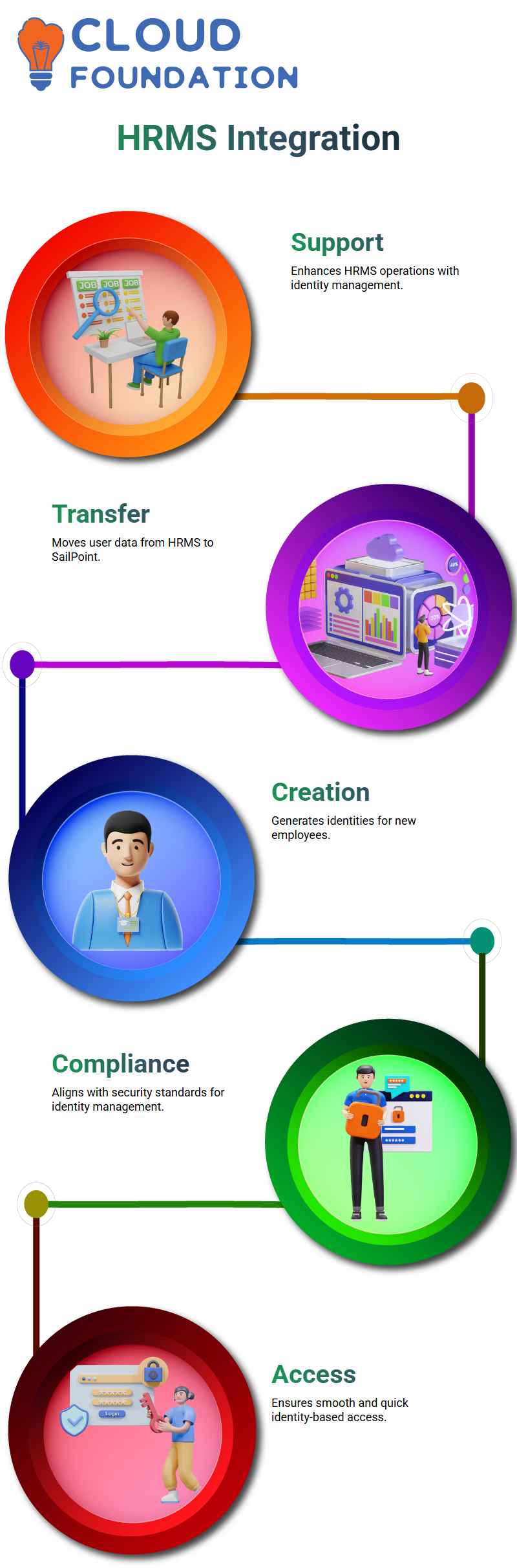
HRMS Integration with SailPoint
One of the significant benefits of SailPoint is its ability to support HRMS operations. The processed user data is transferred from HRMS to SailPoint, thus deciphering the identity creation process.
All fresh recruits are given an identity in SailPoint, a service-oriented architecture compliant and thus in line with organisational security standards.
I trust this process will ensure smooth and quick access management.
Identity Workflows with SailPoint
Automatic identity governance is the base of the system. With SailPoint, we can easily do workflows in identity management, access control, and password management without much difficulty.
For illustration, if a company has a new member, SailPoint would automatically identify default qualities for the individual, recommend the right applications, and assign other categories of entitlements according to the guidelines they fill in. Conducting identity checks on a large scale becomes a trouble-free job.
SailPoint’s Lead in Identity Management
SailPoint still holds the top position in the identity management industry, consistently maintaining complete control over access rights. Although every identity management solution still has complex issues, SailPoint has mitigated many of these challenges through several key product qualities.
A good example of this is the administration of account holders. SailPoint ensures that every attribute is synchronised, even the dynamically generated ones like e-mail IDs, which occur if someone were to be changed, e.g., due to a change in the employee’s department.
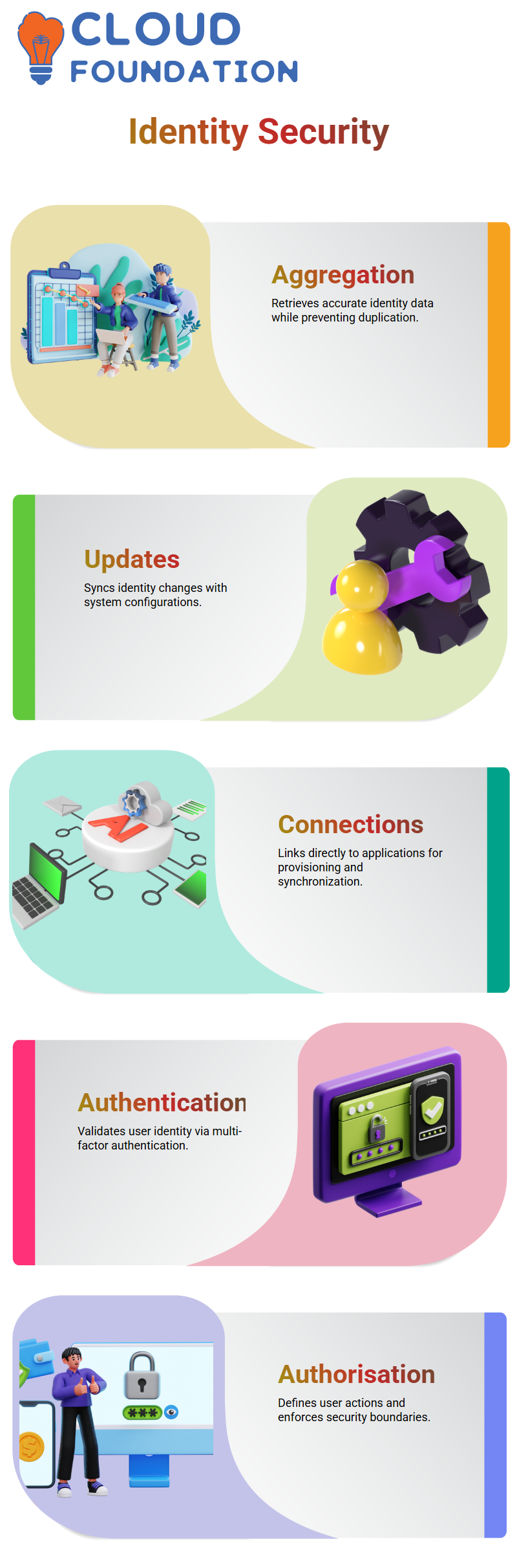
Aggregates with SailPoint
One of the most essential characteristics of aggregation in SailPoint is that it enables retrieving only correct data.
If there are any developments in the configuration of qualities in Windows, SailPoint guarantees that it updates these modifications in its forum.
By employing defined connectors, SailPoint directly links to applications. Therefore, it checks the connection before proceeding to provisioning and synchronising data. If a connection cannot be established by SailPoint, identity management tasks cannot be carried out.
Authentication and Authorisation with SailPoint
Authentication and authorisation are the cornerstones of security in SailPoint. When you authenticate to a computer system, the process confirms your identity, and SailPoint affords secure access via IAM by utilising multi-factor authentication.
Having been authenticated, SailPoint then defines which actions you can do within the system—this is authorisation.
From entering only specific files to adjusting the system’s settings as a user, SailPoint controls the users’ every move, ensuring that they remain within the limits of their rights.
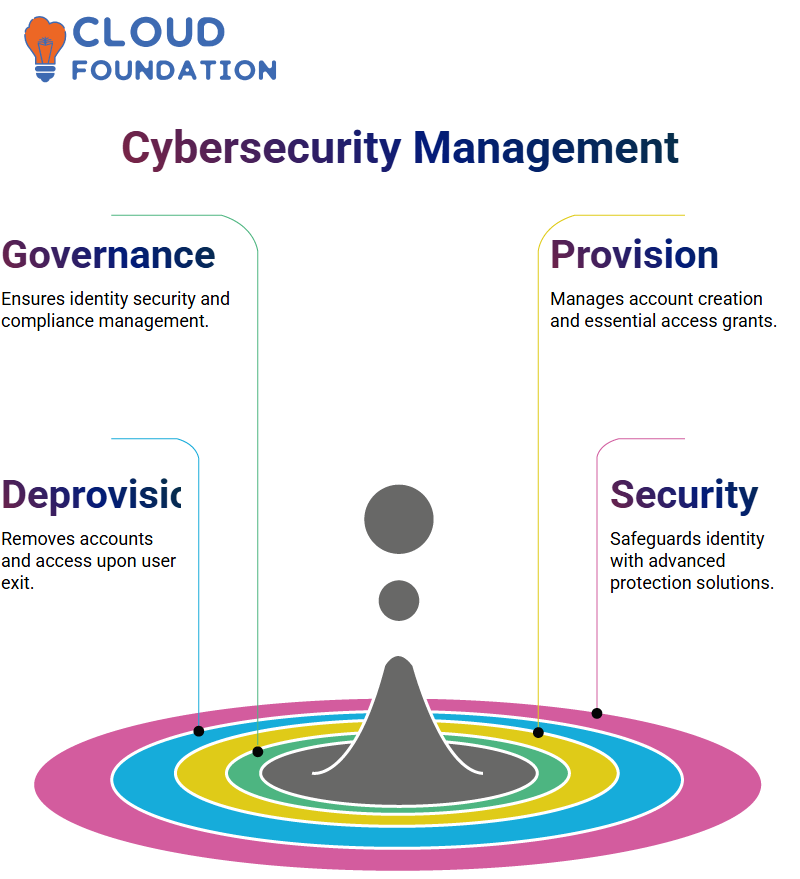
Cybersecurity in SailPoint
Cybersecurity is vulnerable without (SailPoint).
If proposals, identity governance and administration, network security, compliance management, and the best solutions to safeguard the organisation. SailPoint is at the forefront of such solutions.
SailPoint is the top runner in identity management, making it the safest choice for companies worldwide. The instruments sold by SailPoint provide a painless and quick solution to even the most complex processes within a company while verifying security and capability.
Provisioning and Deprovisioning with SailPoint
SailPoint utilises both provisioning and deprovisioning to manage user lifecycle activities straightforwardly. SailPoint ensures that, upon joining a company, your accounts are not created in a multitude, and only grants the most essential tools and systems.
So, when you are about to go out, SailPoint handles the deprovisioning process, which deletes all your accounts and access at your discretion. This way, no unauthorised access can be opened, and an almost guaranteed environment exists.
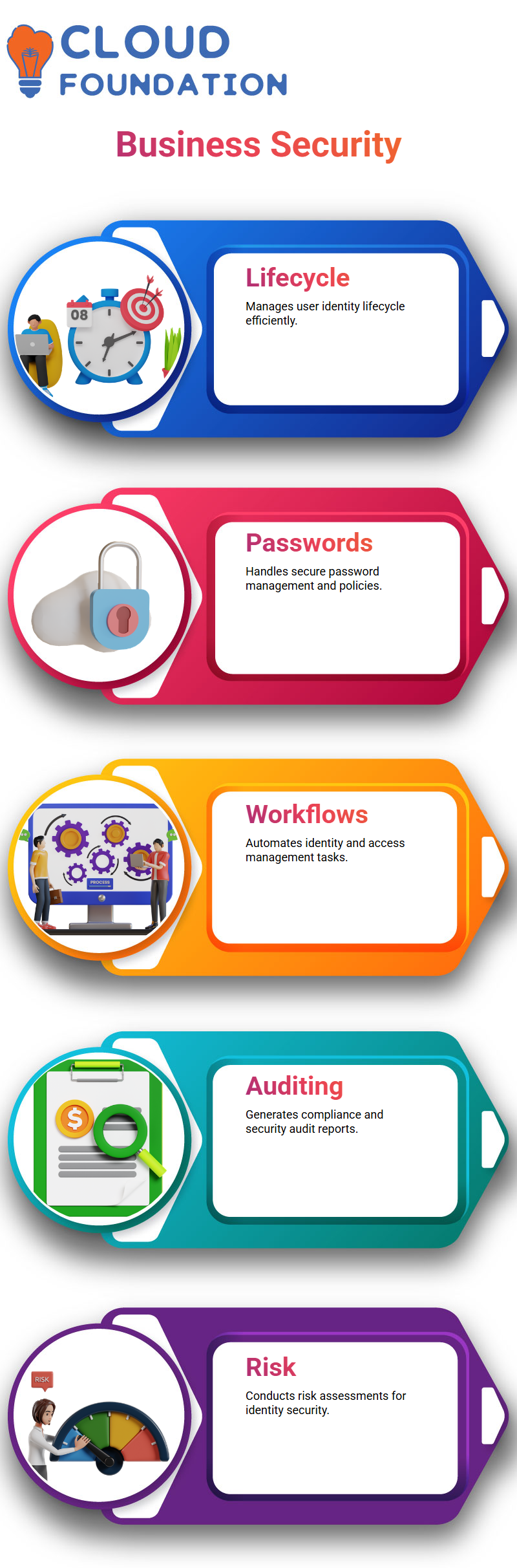
SailPoint Features for Businesses
SailPoint is a solution designed to meet customer needs, offering user lifecycle management, password management, workflow management, and audit reporting features. All in all, a very aspect-rich identity management tool.
The tool also gives organisations control over characterising group access, managing agreement policies, and conducting risk assessments.
It’s not only a question of controlling identities. It’s about finding the expedient and safe way to do that.
Integration of SailPoint and Payroll System
The method by which you compensate your employees is a crucial aspect of the business, and a payroll system is one of the most widely used systems in an organisation, playing a key role in payment. SailPoint is a must-have here for identity verification.
First, SailPoint creates your account and verifies that the authentication process aligns with the company’s requirements, ensuring security before you gain access.
When you type in your password, an authentication system is triggered. However, it is not a SailPoint module.
SailPoint is the only system responsible for opening accounts. It checks if you have the indispensable permission, and if so, it escalates nothing but your rights.
SailPoint Manager Certification
SailPoint is an essential tool for certification routines, which are decided mainly by the manager.
When a manager such as Sara Berry is certified, SailPoint will typically initiate the imperative access reviews for those under her in the reporting lines.
Assuming a second manager exists under her, the access reviews of the employees under the second manager would also be triggered automatically.
SailPoint, in the case of a senior manager, will combine access reviews for everyone supervised by the senior manager.
This classification method is a proven technique in conformity and security that should be exercised in the organisational culture.

Navya Chandrika
Author



