SAP GRC hands-on training
Emergency Access Management in SAP GRC
Every Monday can feel like jumping headfirst into danger–but emergency access in SAP GRC was created just for this scenario.
When critical production system issues occur, consultants from various modules often need special access they wouldn’t normally enjoy; that’s where SAP’s Emergency Access Management (EAM) takes over.
SAP GRC allows us to set up Firefighter IDs that grant temporary elevated access for specific users – this way, they may perform emergency tasks outside their regular roles and ensure quick fixes are possible. The overall goal here is to protect operations while simultaneously expediting fixes quickly.
My starting point for access controls in SAP GRC Access Controls is always SPRW Reference IMG; this serves as my foundation.
One of my initial tasks is defining connector types and their types–essential for smooth communication–under ‘Maintain Connector Settings.’ Here, I also specify connectors under SPM to provide for emergency access if necessary.
Maintaining connectors under “Access Control” ensures all actions are mapped appropriately, for instance, using connector group J-4 linked to target connector KST-T-0 CL-9900 as part of one configuration – these mappings play an integral part in provisioning firefighter IDs from the frontend to the backend SAP GRC systems.
Key Configuration Parameters in SAP GRC
As I explore SAP GRC configurations, my attention is drawn to parameters beginning with 400 series numbers. The first defines our application type–ID or role-based firefighting–with ID providing tighter controls over high activity logs than role-based.
When making my recommendation on which one I prefer, I always opt for ID firefighting as this provides tighter user identification logging capabilities and better controls overall.
Validity periods for firefighter IDs should also be set accordingly; I recommend setting it for 24 hours, as this serves as a general rule across SAP GRC system IDs to enforce discipline in how emergency access is utilised.
SAP GRC features an immediate email notification trigger that sends notifications immediately whenever a firefighter ID is used, often to controllers or owners to maintain transparency among stakeholders.
Keeping everyone updated, SAP GRC ensures all stakeholders remain up-to-date and offers complete transparency in reporting.
SAP GRC offers several options for retrieving logs, including system logs, audit logs, and session logs, which I always enable.
This is because you never know when elevated access might introduce changes that disrupt operations; logs provide our safeguard against possible disruption.
Parameters like 400007 and 400009 ensure log reports reach controllers quickly when activities commence and notifications go out when new activities start, helping SAP GRC keep strict oversight every time emergency access is activated.
Firefighter ID Roles and Parameters in SAP GRC
As soon as I logged into our SAP GRC system for the first time, the fireman login served as my reporting console.
Once set to “yes,” SAP GRC automatically collected backend logs after finishing all firefighter activities.
SAP GRC then checked to see whether notifications should be sent directly to the controller; setting that toggle to yes sent execution logs directly using parameter 4009.
At the same time, parameter 4008 ensured the system notified when someone logged in using an active firefighter ID.
As part of my SAP GRC implementation efforts, I ensured all firefighter IDs across our target applications held a valid firefighter role, allowing SAP GRC to recognise them properly as service user IDs with elevated access permission – without this role, SAP GRC couldn’t identify users as legitimate firefighters.
To effectively oversee audit logs, I assigned default users with the responsibility for forwarding SAP GRC-generated logs to controllers using specific parameters that limit access.
Setting out to determine whether firefighter owners could raise access requests themselves was an essential but subtle configuration step that created an increasingly safer access environment.
By tweaking SAP GRC settings appropriately, I could prevent unauthorised self-requests and create safer access conditions.
My configuration of SAP GRC ensured that even when someone logged in but did not perform any task, a log session was still created, making even non-activity with firefighter ID traceable and auditable thanks to proper parameter toggles.
SAP GRC Security Testing
SAP GRC allows me to identify Firefighter IDs without assigned controllers, triggering a compliance alarm. I quickly reviewed and assigned controllers accordingly.
Furthermore, Parameter 4025, which restricts firefighter access based on time window, is another vital control feature.
With role management, I created custom roles with “Z” prefixes across systems and utilised PSCG for checking existing roles.
Before repurposing S_USER_AGR objects for security testing purposes, I reviewed objects like S_USER_AGR. I applied a strong password before running background jobs to sync users and roles to make sure everything aligned perfectly.
Security testing involved using SU01, PFCG, and creating a test ID named FIRE_SECURITY with elevated and identifier roles as test cases.
I finalised roles, applied strong passwords to each, and then ran background jobs in parallel to ensure everything aligned accordingly.
Firefighter IDs in SAP GRC
As I work with SAP GRC, one of my priorities is ensuring our Firefighter IDs are appropriately managed.
SAP GRC requires us to define both Firefighters and Controllers to allow the system to understand who manages access control for critical systems.
As part of SAP GRC’s access control module, I navigate through the owner section and identify who owns each Firefighter ID before verifying its existence in our GRC repository tables–not just on our backend system.
SAP GRC does not rely on backend data when assigning Firefighters; instead, it depends on information available from front-end GRAC tables like GRACUSERCON and GRACROLECON to validate if an ID exists or not. This distinction can help ensure accurate ID validation processes.
Creating Owners and Controllers in SAP GRC
Setting up Owners and Controllers in SAP GRC begins by creating users. I create users with appropriate roles, such as ‘GRAC Super User Owner’ or ‘GRAC Super User Management Controller,’ which grant them access to approve or deny user requests for approval and control of access.
SAP GRC requires assigning different roles, such as GRACFFOWNER and GRACFFCONTROLLER, so users can effectively serve as Firefighter ID owners and controllers.
I make sure not to rely on role-based firefighting, but prefer ID-based instead.
Once my roles are set up, I utilise NWBC to access SAP GRC and designate newly created users as owners and controllers in the system – this ensures SAP GRC accurately tracks approvals and logs.
Assigning Firefighter IDs in SAP GRC
After setting up the user in SAP GRC, I initiated the Firefighter assignment process by accessing their record, reviewing existing assignments, and utilising SAP’s “Add” function to incorporate their ID number.
SAP GRC searches rely on frontend GRAC tables, meaning backend availability doesn’t guarantee Firefighter ID visibility without appropriate synchronisation of backend and frontend tables.
SAP GRC’s repository sync feature ensures that it reads valid Firefighter records, eliminating the potential for errors while streamlining approval workflows for access requests.
Approving Access Requests in SAP GRC
Once Firefighter IDs have been assigned in SAP GRC, users in either an owner or controller role must approve access requests using the GRACFFOWNER or GRACFFCONTROLLER roles to validate that they’re authorised.
SAP GRC tracks every step through log data generated from its access control module, so I review these logs regularly to ensure compliance and traceability.
SAP GRC utilises additional roles called ‘Access Request Approver” for access request approval purposes.
I make these available only to users requiring verification of high-risk activities or emergency access.
SAP GRC Ownership
As part of an active SAP GRC environment, ownership changes occur regularly due to job transitions or retirements; I often receive requests to update Firefighter ID ownership accordingly.
Following SAP GRC protocols, I use NWBC’s owner/controller details update function to modify them accordingly.
With its comments section available within SAP GRC, the reason behind each change can easily be documented for audit teams.
Adjusting owner data in SAP GRC ensures a new user takes over their responsibilities seamlessly, maintaining uninterrupted access control compliance.
SAP GRC Firefighter ID Setup and Role Assignment
Let me walk you through how I set up and configure SAP GRC firefighter IDs. First, I assign ownership and control over each relevant ID by going into the “owners” section and adding in their firefighter ID; say it is FF_ACC_01.
After adding them as owners, any comments needed for clarifying why this person has taken ownership are included before saving to complete the ownership assignment within SAP GRC.
Next, I assign the controller role, usually to one individual for consistency’s sake. Finally, I associate an ID (perhaps FF_APR) with the firefighter workload so activities undertaken using that ID will be recorded and tracked efficiently within SAP GRC.
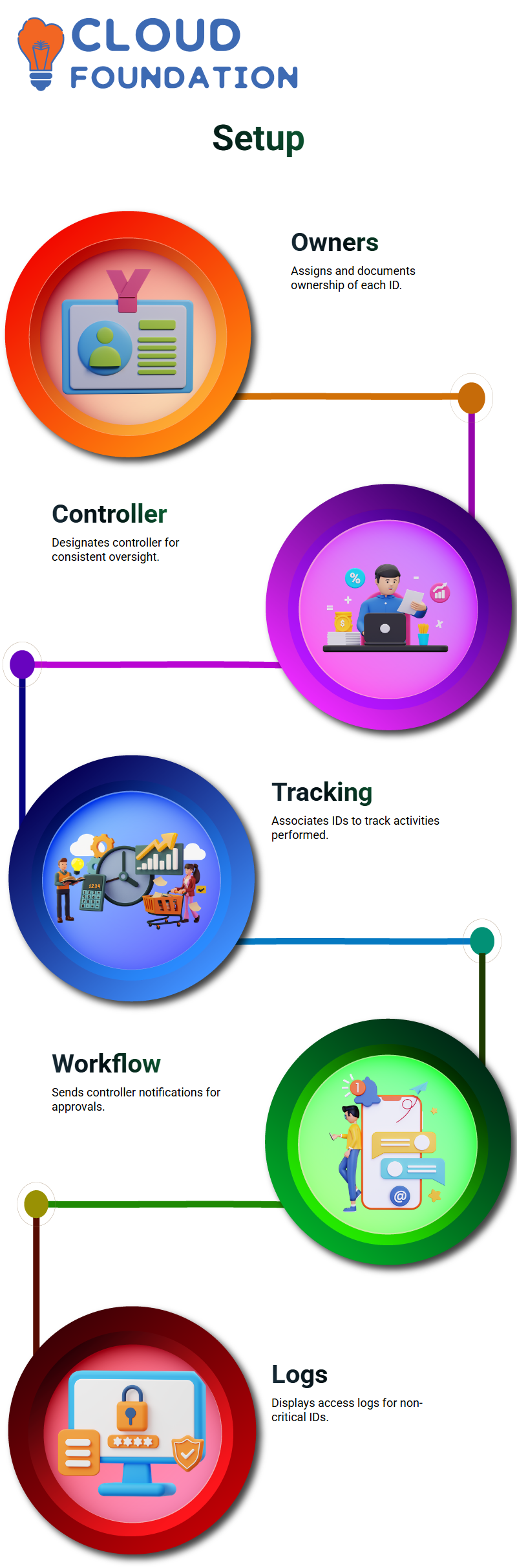
SAP GRC Log Management and Workflow Control
As soon as a firefighter logs onto an assigned system and performs activities, SAP GRC automatically records their actions, uploading logs directly back into its backend synchronisation server for review by an assigned controller.
I created a workflow in SAP GRC that sends notifications via email directly to controllers, who receive tasks in their work inboxes for approval, rejection or additional details if required.
These workflows play an essential part in maintaining audit trails and validating whether activities logged against security policies align with them.
SAP GRC can display logs for non-critical firefighter IDs without initiating workflow approval processes, just displaying evidence of system access and activities.
SAP GRC Integration
Now let’s discuss Access Request Management within SAP GRC ARMS (Access Request Management Service).
ARMS takes over provisioning through multiple approval stages when an access request is sent via SAP GRC; I initiate this process by creating a test user and submitting an access request tied to our firefighter ID number.
SAP GRC will then process this using an intuitive pre-configured workflow and, once approved, access is granted so the user can operate within the firefighter framework. This layer of integration ensures every step is traceable and managed securely.
SAP GRC EAM Configuration and Audit Considerations
Emergency Access Management (EAM) is one of the easiest yet most essential aspects of SAP GRC when it comes to configuration.
As an administrator, my role includes configuring roles within SPRO, assigning identifier roles and allocating elevated access roles such as S_TCODE or PFCG roles for emergency access purposes.
SAP GRC audits every transaction conducted using firefighter IDs, looking out for any excessive or repeated use that indicates potential flaws in role design.
Unplanned system access could lead to security vulnerabilities; I ensure SAP GRC is configured accordingly to collect evidence effectively and remain audit-ready.
Sometimes issues with SAP GRC stem not from the initial setup but instead from functional misconfigurations.
That is why understanding its whole landscape, from configuration to master data management, is critical in protecting operations in production environments.

Navya Chandrika
Author



