SAP GRC Configuration Training
SAP GRC Configuration in Healthcare Projects
My hospital is currently preparing for a Joint Commission audit, and part of my responsibility includes reviewing training materials to ensure compliance standards are upheld – SAP GRC plays a central role here.
As part of my role managing revenue cycle platforms, I manage technologies like Epic EMR systems and SAP in the background.
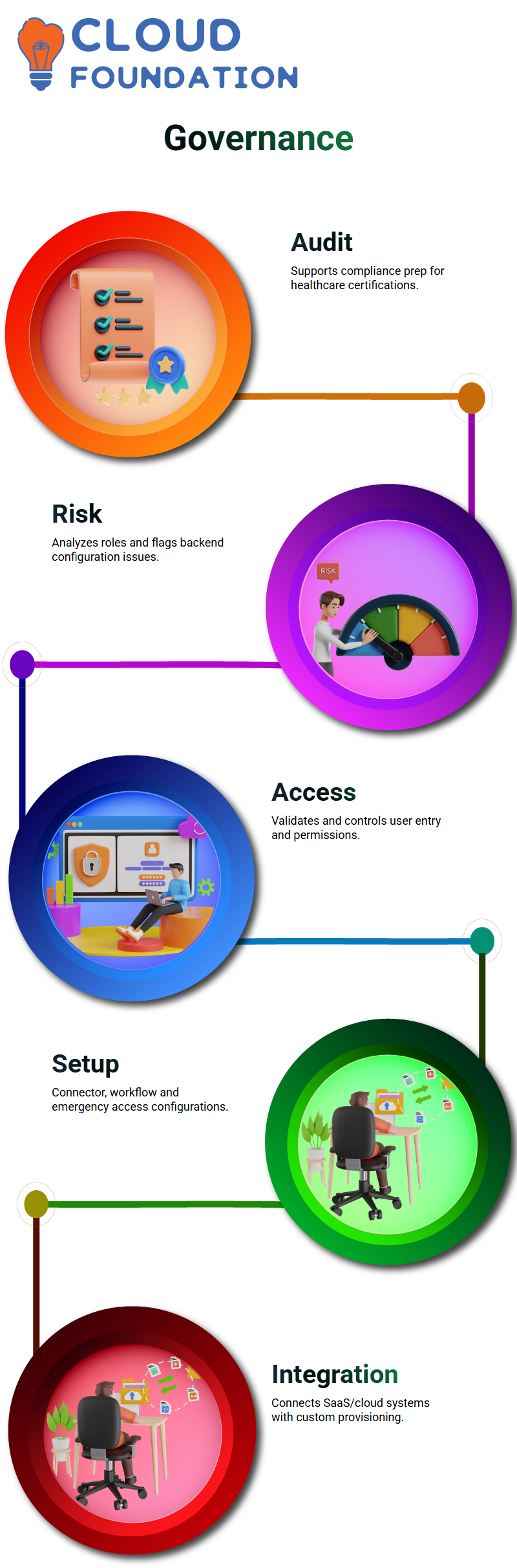
While my direct interaction with SAP may differ depending on its configurations or use case, its GRC configurations have proven indispensable, from risk evaluations to access controls – this forms the backbone of governance for my environment.
Before diving into these tasks directly in the GRC box, I reviewed connector configuration settings–they reside within the SAP GRC access control section and play an integral role in our setup.
SAP GRC configuration settings open a wide variety of doors – change logs and mitigation rules are just two such areas. At the same time, workflow setup and emergency access management can also be utilised with SAP GRC.
I frequently utilize it to conduct risk analyses across roles that help my organisation remain compliant and audit-ready.
SAP GRC features an exceptional feature called Risk Terminator that I find particularly helpful for role creation in backend systems: this tool flags any risks even if they don’t originate inside its application; previewing any possible issues caused by changes to role assignments is key in helping backend users make informed decisions about changing role assignments and assignment changes.
SAP GRC Settings and Customisation
As part of my introduction to SAP GRC, I start by exploring its data configuration settings.
If standard options don’t meet my needs, customisation becomes my next stop. These SAP GRC settings determine how business requests interact with the solution as a whole and directly influence management workflows and reporting processes.
SAP GRC brings forth issues regarding validating user access. I review each request that comes in to ensure the name and credentials are populated accurately – this ensures integrity within access control systems.
I specialise in setting up customer integrations using SAP GRC. These configurations determine how cloud systems and SaaS applications connect.
While provisioning through GRC systems is a complex topic, I make sure these integrations reflect what’s currently trending within SAP GRC.
SAP GRC Rules and Configurations
SAP GRC rule sets are at the core of access control operations. I check existing GRC_RULE_SET sets to determine whether to stick with defaults or use other available rules from within its dropdown list.
Every SAP GRC module that I teach–XARM or ARM–incorporates rule definitions into its curriculum. As part of these courses, we explore rule hierarchies, dependencies and their impact during access request or approval processes.
SAP GRC Risk Analysis and Organisational Rules
SAP GRC enables me to delve deeper into risk analysis parameters and organisational rules, using parameter 102 as a benchmark to determine whether organisational rules apply within an application.
Furthermore, I regularly review default values provided by SAP GRC before customising them as necessary according to business policies.
Case sensitivity for all SAP GRC objects, from transaction codes and data sets, is of vital importance in terms of accurate access risk results, so I take special care to align all parameters accordingly.
With SAP GRC parameter 1023, I set default risk reports access permission or action levels and instantly observe its effects across NWBC screens – one reason I depend on SAP GRC for risk management.
SAP GRC NWBC Screens for Analysis
I utilise NWBC screens to conduct user-level SAP GRC access analysis. On these screens, I often observe default entries, report types and risk levels – depending on my setup, I can switch between permission- and action-level reports as needed.
Changes I make behind the scenes to SAP GRC SPR parameters immediately reflect in NWBC screens for enhanced workflow and transparency during risk assessments.
This real-time sync helps maintain both of these goals.
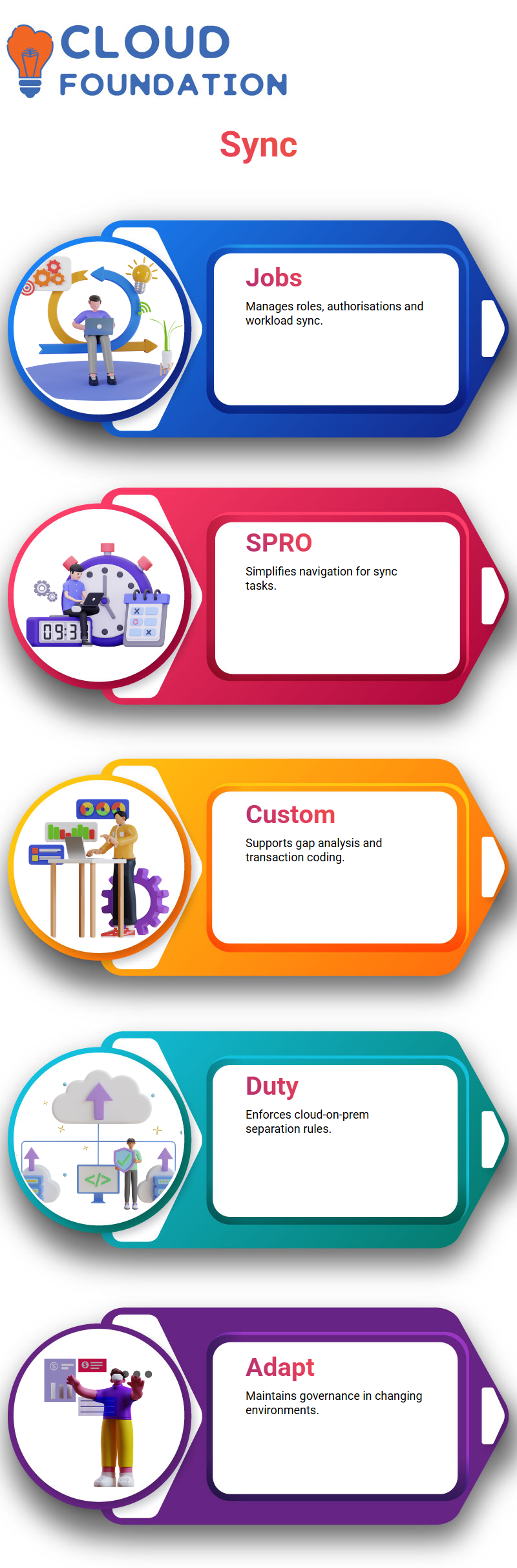
SAP GRC Synchronisation Jobs
SAP GRC contains numerous synchronisation jobs which facilitate various tasks like authorising syncing, role usage tracking and workload monitoring. SPRO navigation makes this job management simpler for me.
As business needs require custom transactions not covered by SAP, I collaborate with developers to conduct gap analyses and generate custom transaction codes.
SAP GRC makes these customisations seamless and is fully supportive of them, offering seamless customisation solutions.
Custom Integration with SAP GRC
SAP GRC helps ensure workflows between cloud and on-prem systems run smoothly; for instance, I use it to prevent users from simultaneously authorising procurement orders in both ARRIBA and S4HANA; using SAP GRC, this separation of duties can easily be enforced.
These SAP GRC setups enable me to keep pace with changing client environments while upholding governance across systems.
Through synchronisation jobs and custom rule configuration, this goal can be reached.
SAP GRC in Sync with Backend Updates
SAP GRC can only read what has been told it; if the sync job does not run post-update, GRC continues displaying outdated values – in my case the object still displayed its old “03” value instead of reflecting updated “02” and ’03” ones – until after I reran sync, and only then did SAP recognize its latest values.
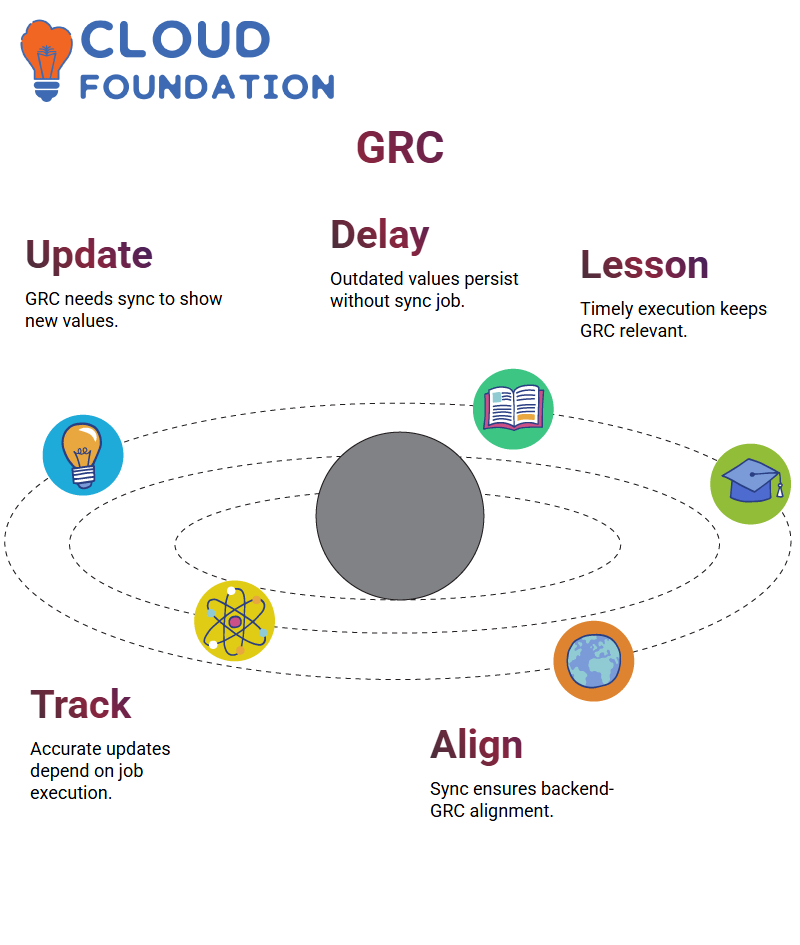
Real-world experience taught me an invaluable lesson: SAP GRC systems depend heavily on timely job executions and accurate change tracking to remain effective, and any updates without accompanying job execution won’t keep SAP GRC appropriately aligned.
SAP GRC Repository Sync and Future Steps
Even though I didn’t discuss repository sync and role usage sync in detail during this session, they are just as essential components of SAP GRC.
I plan to cover them more thoroughly soon, since understanding them can make or break a compliance strategy.
As part of my ongoing endeavour to master SAP GRC, I’m finishing off the setup for sync jobs. Then will explore module-based settings and fixed configurations within SAP GRC. Thanks for sticking with me so far – if this shows you have taken your commitment seriously, then let’s move on to mastering SAP GRC together! I am here every step of the way with you.
Role Creation in SAP GRC
Beginning from the transaction code (T-code), we move down through the authorisation object, authorisation field, and field values until finally reaching the field values. This approach enables SAP GRC to offer clarity by understanding this flow from top down.
When explaining SAP GRC to others, I stress how transaction codes link directly with security constructs.
Creating PSG roles or defining object field values are integral parts of the SAP GRC security setup and configuration. GRC also helps us easily link T-codes with authorisation parameters for an intuitive security setup.
Let’s say we introduce a custom transaction code into SAP GRC; naturally, this would come with its own set of authorisation fields with specific values assigned.
Once the sync job has run successfully, SAP GRC ensures data flows from backend systems into GRC Access Control by SAP structures.
Role Data in SAP GRC
At every point of creating roles using SAP GRC using PFCG, I make sure the appropriate transactions are assigned.
When assigning SU01 under one role, for example, SAP GRC immediately flagged any needed authorisation data.
SAP GRC uses red as an indication that data needs to be updated, which I could see by expanding tabs until all were red, indicating data was ready to be modified or added to.
Upon further adjustment of the authorisation data sections, SAP GRC revealed default objects related to my SU01 transaction, which contained expanded nodes that revealed fields and their values within each object.
SAP GRC visually verifies what its backend already knows–how roles govern access using these interrelated components.
Let me demonstrate how SAP GRC enabled me to meet an authorisation need: users assigned activity 01 also needed access to activity 02 by simply updating role definitions–allowing SAP GRC to directly update field values without jeopardising security or being limited in scope.
SAP GRC Role-Level Changes
Experienced SAP GRC users know that role-level changes can be tricky.
Recently, however, I observed how one colleague made changes at SU24 instead of the role level that affected how data was synced across the SAP GRC system.
As an illustration, I edited one field value and added the number ’02’ alongside existing entries in an attempt to demonstrate this point.
Once saved, however, the change had a practical impact beyond customisation rather than just being visible locally.
This distinction is significant as SAP GRC treats workbench requests as SAP-proposed changes rather than client-specific ones.
And here was where things got interesting: to meet our client’s specifications, SAP GRC needed to accept both options (02 and 03) even though its default was 3.
To address this challenge, I created a request, selected relevant transactions, and saved my changes so they reflected both options (1 & 2) at once.
SU24 Repository in SAP GRC
SAP GRC simplifies the process of mapping authorisation details with SAP SU24 transactions.
Imagine I want to add SU01 to my role; in that instance, I would enter SU24, search for “SU01”, and instantly see which authorisation objects it has attached. This step is essential in SAP GRC for validating what gets pulled into PFCG roles.
As part of my work with SAP GRC, I’ve experienced firsthand how SU24 helps surface all relevant objects, fields, and values.
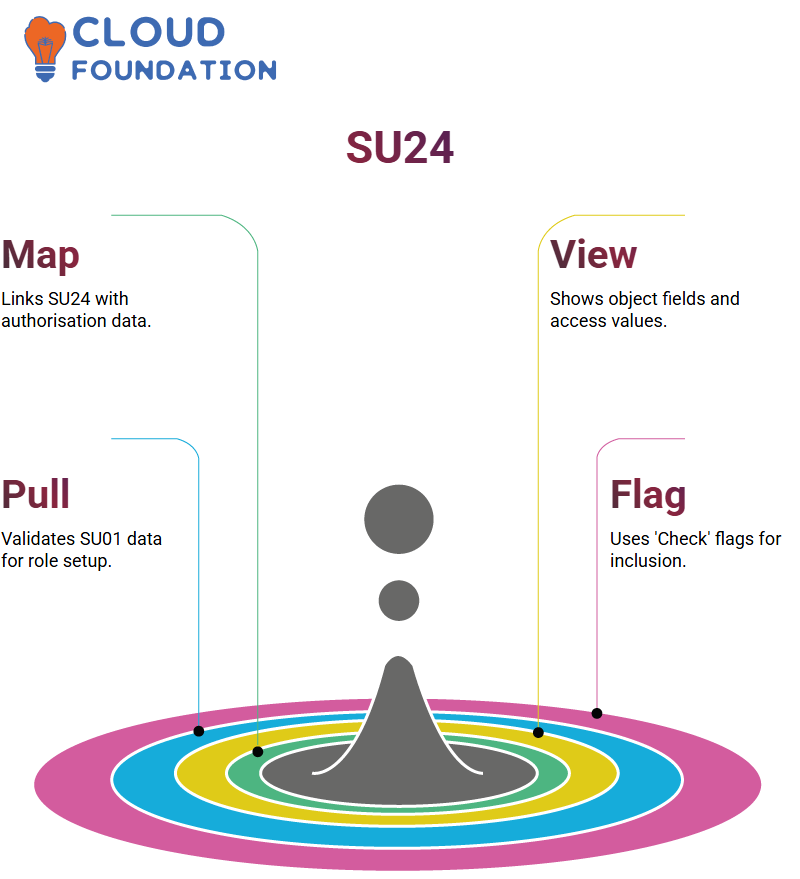
SAP GRC allows us to view not only objects like S_USER_AUTH that contain fields like ACTVT, AUTH and OBJGACT but also values assigned, like 03 or 01, that determine user access behaviour.
SAP GRC determines inclusion based on two flags, known as the check indicator and proposal value flags. Only objects with both of these set to ‘Check’ cut; its precision makes SAP GRC such a practical framework.
How SAP GRC Reads Data from SU24?
As soon as you use SAP GRC and are reviewing SU24 transaction data, all relevant information will automatically flow directly into your role setup – any change to object fields or values could subsequently affect other areas within its configuration.
SAP GRC’s draw is its close coupling between transaction codes, objects, fields and values. Any time there’s any variance – be it at field level or between objects-to-fields relationships- SAP GRC must accurately capture it, otherwise the sync between backend and GRC frontend is lost.
Field-Level Insights in SAP GRC
SAP GRC makes it simple and accessible for administrators to inspect field values associated with objects. I navigated to SU24’s Field Values section for this breakdown; for
S_USER_AUTH, which has three fields, and saw values such as 03 neatly distributed across them all – these entries serve as gatekeepers of activity within SAP GRC.
Testing SAP GRC, examining how missing indicators impacted role visibility. If an object lacked check indicators or proposal values, SAP GRC wouldn’t include it in any roles; this small detail adds immense value and shows why SAP GRC remains such an indispensable platform for risk-based access control.
I noticed something else about SAP GRC that caught my eye: default field values often needed enhancement.
After performing tests and reviewing results, we updated SAP GRC roles so they included not just value 03 but also 02 to meet changing user needs and ensure compliance. SAP GRC allows us the agility necessary to adapt roles while remaining compliant.

Navya Chandrika
Author



