SailPoint Lifecycle Management Documentation
SailPoint Lifecycle Management
Discover how SailPoint simplifies the complexities of lifecycle management.
If you need to duplicate the file or oversee the sequence, SailPoint will provide the solution for you.
Picture yourself in the world settings, and that you have made the file to import it only — it’s like a flawless movement. SailPoint comes along and ensures that the element you have called, and only that element, is edited, while the rest of the residue remains the same.
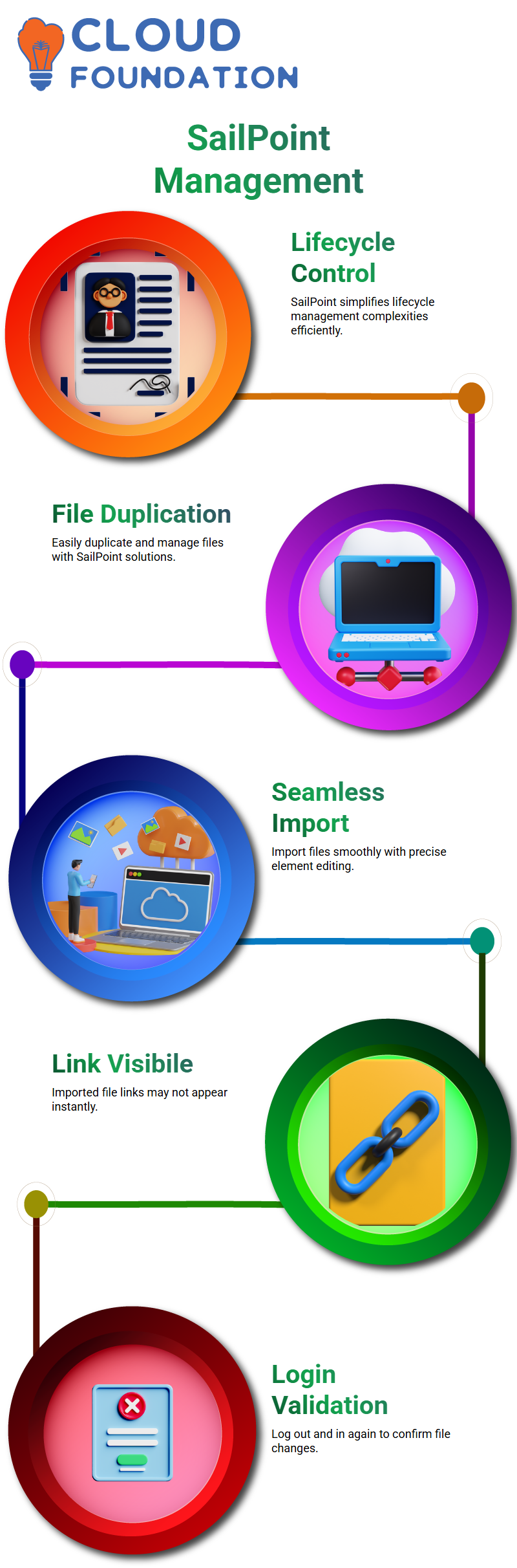
File Import in SailPoint
Allow me to show you a thrilling part of SailPoint: when the files are imported, you may notice that the links don’t appear all of a sudden.
This is so because changes are checked during a few logins.
To confirm the revisions, you have to log out and log in again.
Approval Processes in SailPoint
With the help of SailPoint, the decision is ultimately yours regarding the arrangement of approval processes, and you can delegate tasks to multiple individuals, such as application owners, managers, security officers, or nominated identities already known to you.
The system’s flexibility allows for approvals to be handled quickly, tailored to your specific needs.
For example, when an application owner leaves and the system is no longer operated, SailPoint provides a substitute approval option, ensuring continuity in approval flows.
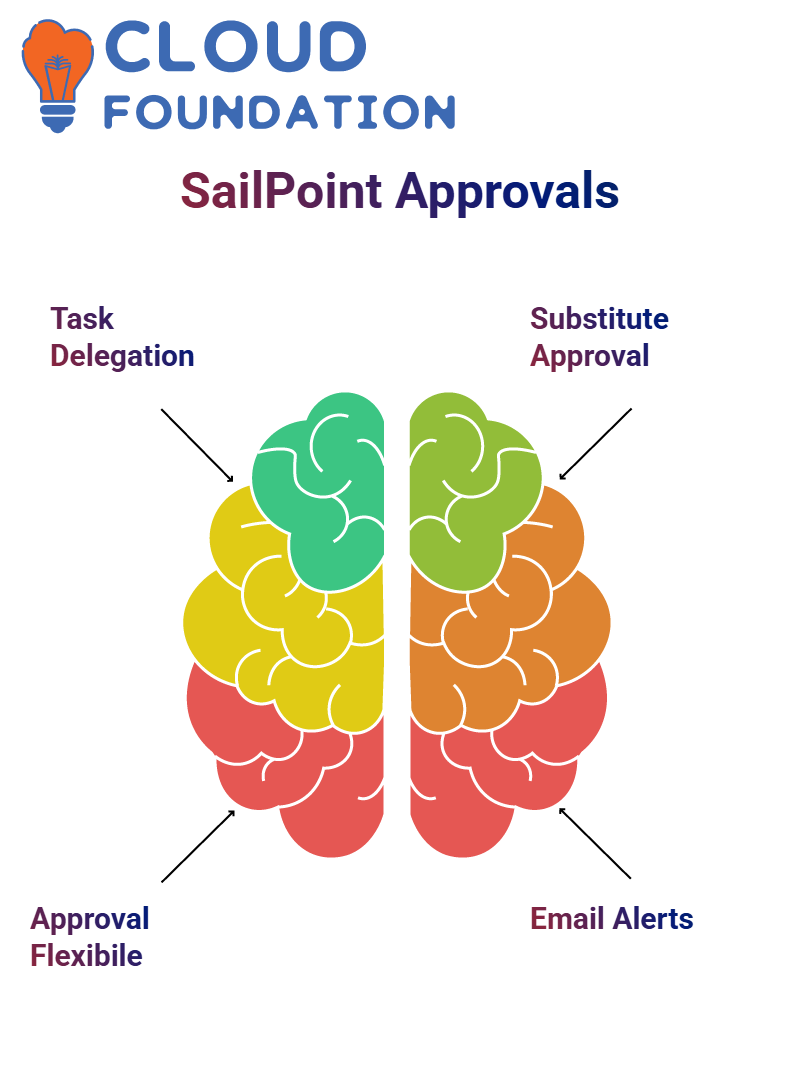
Signals Reinforcement in SailPoint
Notifications about the SailPoint system are sent via email and can be tailored based on the user’s duties.
It is possible to send a notification to the requester, user, manager, or all of them. SailPoint enables you to create email templates for messages, ensuring the clarity of communication throughout the approval process tasks.
Workflows Configuration in SailPoint
Setting up SailPoint’s system is very user-friendly when using XML. A separate process for managing the access of both managers and managed accounts could be created without the need for intricate coding.
This malleability can significantly alter the game for companies that need to refine their approach to governing identity workflows.
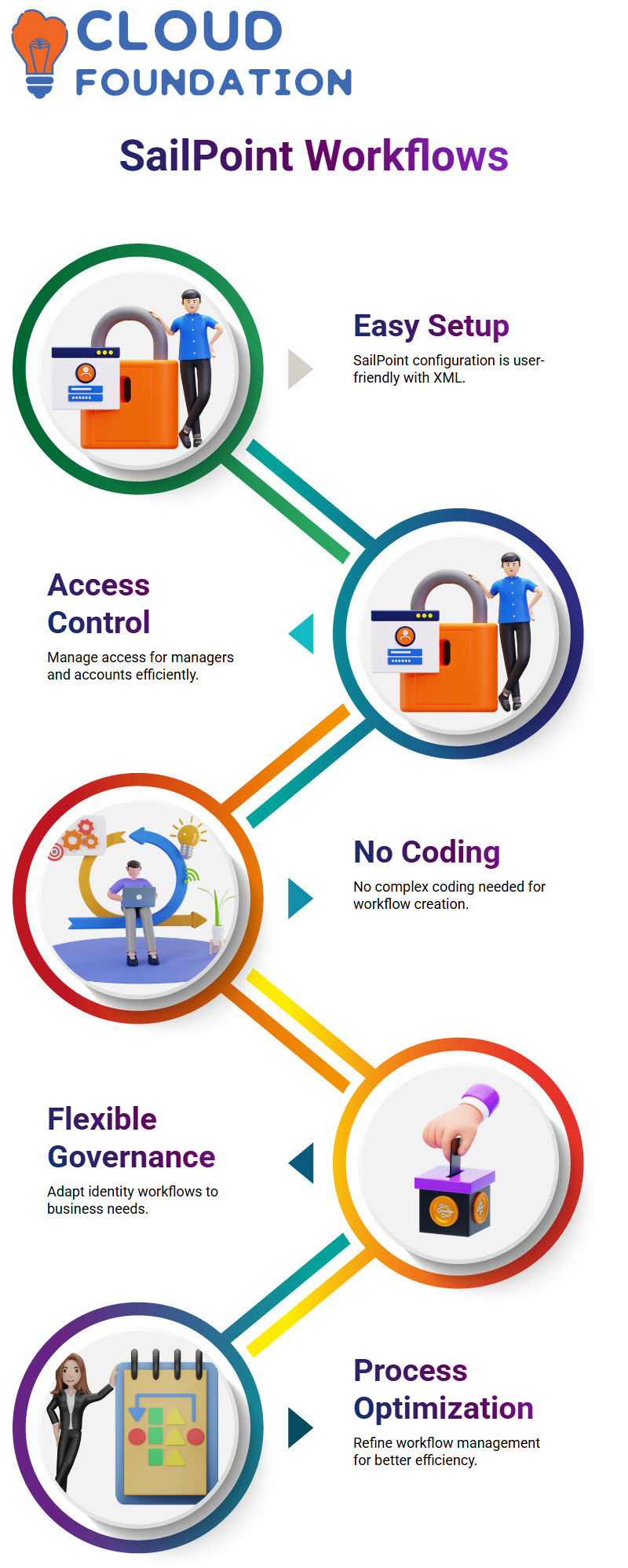
Integration with SailPoint and ServiceNow
The integration features of SailPoint provide an augmented, automated lifecycle management process. You can onboard applications and speak with ServiceNow promptly.
By using Recreation APIs and Postman, you can check and deploy workflows that allow you to access your ServiceNow system. SailPoint can handle repetitive configuration modifications and workflows without errors.
SAP GRC Integration in SailPoint
Did you ever have to receive requests from and send the bulk of your tasks to a different system? The usual approach is to have some of your functions executed by the requester, and so on.
SailPoint permits this communication and also the work itself to be completed in an orderly way.
While you conduct SAP GRC integration, SailPoint will be of great assistance with that task. With more direct onboarding of the SAP system, the process is quite competent.
You can easily select, assemble, and go live with applications. On the other hand, the use of SAP GRC requires specific import files, and SailPoint has the instruments imperative to make the integration simple.
Identity Properties in SailPoint
Typically, editing identity qualities in SailPoint is not allowed to prevent unauthorised modifications. Nonetheless, the situation may necessitate the amendment of specific features.
Users cannot modify data without adhering to the settings of SailPoint’s attribute mapping.
To provide a practical example, a region attribute that requires editing SailPoint settings must be changed to ‘permanent’ from ‘read-only’. When this is saved, the main person will receive this change, which can then be modified by approved users for this attribute.
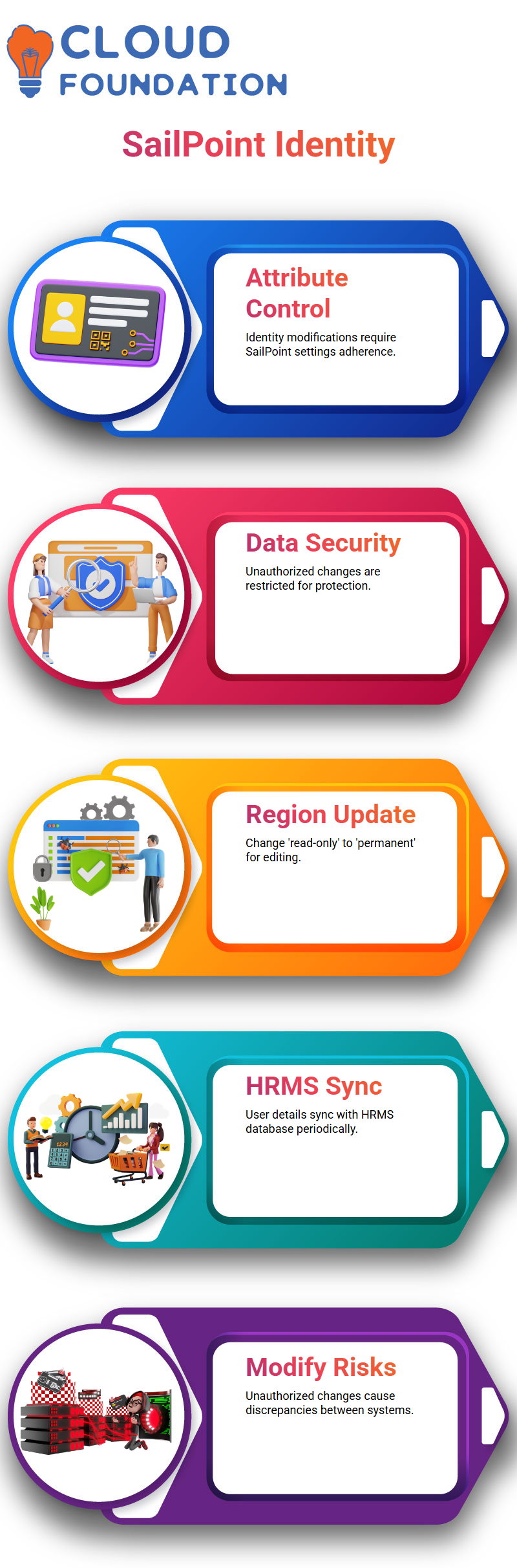
Identity Management Flow in SailPoint
The processor unit of SailPoint is a key component that facilitates the identity management process. User details should ideally originate from authentic sources, such as the HRMS database. Shifts occurring in the HRMS system are automatically linked to the SailPoint database in the next aggregation period.
Manual updates may be allowed for some properties. SailPoint recommends against direct modification of main features, such as email or last name.
Modifications without permission may result in discrepancies between SailPoint and HRMS facts, although the latter is considered the original data source.
Segregation of Duties in SailPoint
Managers can formulate SOD rules by specifying a group of entitlements that combine to result in prohibited access for users. Those who violate the rules receive notification from managers for review.
In SailPoint, the policy application process involves outlining rules, activating policies, and conducting compliance checks. Once the policy is activated, SailPoint performs the user monitoring to ensure that they conform to the set access restrictions.
Configurations for Policy Checks in SailPoint
Different checks about the policies that you can perform in SailPoint.
This type of policy can be set up as a strict or relaxed system, with logging of violations remaining an option for both.
Users who have the authority to do so can have SailPoint reject requests that violate the policy or log the invasions without stopping access approvals.

SailPoint’s Role in Identity Management
In addition to policy execution, the SailPoint system is the primary component of the identity management aspect of the job.
It is not new that the residents of the town can make noise wherever and whenever, and that the procedure for addressing this issue remains unchanged.
The nexus is not just the changers, but also those involved in transit hubs and other chokepoints, as well as the instruments with devices that enable them to adjust the travel mode choices of individuals along the transport superhighways.
User Identity with SailPoint
It is best to perform user identity management with SailPoint because it is a highly systematic system that is the preferred approach for this purpose. Imagine you have to change the name of a user in your system.
Changing this is not something you can do just because it occurs to you.
These details will then go to SailPoint, and when the subsequent aggregation is performed, they will be automatically uploaded.
Nevertheless, it comes with a condition – you can also set your preferences. For demonstration, if you want to change the reports about the region, you have the option to perform the update in SailPoint.
Consider that in the Entitlement Catalogue, you can review access permissions, for example, by taking a particular application as a case. In SailPoint, all users are displayed who have access, along with their associated entitlements.
SailPoint is the first dais to introduce the modern generation of functions such as the Access Certification and Separation of Duties (SOD) These features get the company back on the observance circuit by assuring that the users are not in a conflicting state of usability and they are also prowess and clearness in creating and managing the SOD policies.
SOD Policies in SailPoint
As the SOD rules are the life of your conformance in SailPoint, they are regarded as an absolute necessity.
For representation, imagine that you do not want to allow users to possess both ‘Approve’ and ‘Input’ access concurrently. This is the good side of SailPoint.
One defines a new policy in which rules are clearly stated, detailing which features and entitlements of a user are also applicable to another user.
Once the new policy has been set up in SailPoint, simulations can be run to see which users have violated these rules. The Managers are tasked with the responsibility of appraising the violations that are automatically assigned to them, ensuring that there is no mix-up of unauthorised combinations.
Commands Run and Control in SailPoint
SailPoint is the best way to oversee and manage your policies efficiently. For illustration, you can turn on and do the tests to find out the examples of SOD violations after you have intended the SOD policy.
SailPoint supplies these configurations for testing in a disabled state to determine beforehand the impact of their implementation.
Using SailPoint, any breach is accurately recorded, and you have the option to ban users who do not comply with the company’s rules.
This transparency protects the company, ensuring it remains compliant while still maintaining control over user identity.
SailPoint Violation Policy
SailPoint is capable of managing identities; however, violations of a particular kind can still occur due to improper access conduct.
If a user violates a policy, it is their manager who must take the necessary steps to resolve the issue.
Therefore, the task of the head manager is to decide on access, i.e., either to grant it or withdraw it based on clearly defined rules and conditions.
When authorising the access, the user must interpret the time frame.
If the manager wishes to deny access to the user, they need to make the correct choice of access to remove.
Non-respect events occurring with SailPoint are categorised under the names of the relevant policies.
If the description was not written at the time the policy was created, the system will have no details to display.
Policy Settings in SailPoint
For policy enforcement, SailPoint offers four alternative options: turning off policy checks, permitting violations without a warning, displaying a failure to request, and immediately failing the sequence.
These settings can be adjusted according to the organisation’s security requirements, enabling the organisation to enforce policy compliance at various stages of access provisioning.
SailPoint Requests
If a user sends a request that breaches the current policy, SailPoint will decide whether to sanction it.
When a policy violation is detected, the system immediately requests that the user refrain from unauthorised actions and prohibits them.
Moreover, SailPoint identifies and catalogues existing users with unauthorised access in the system.
The violation is detected by the system, which then brings the matter to the manager’s attention to take the necessary precautions to support security.
SailPoint Business Processes
You can engineer all business processes directly using SailPoint. You are capable of assembling workflows, updating settings, and making adjustments without interrupting the provisioning process.
Using SailPoint, the process of provisioning becomes as natural as breathing—adding or removing any elements can be done as easily as making a bank transaction.
In every provisioning request, SailPoint automatically initiates the entire process flawlessly.
Policy Simulation in SailPoint
SailPoint offers the option to simulate policies to preview their effectiveness before implementation.
This is typically conducted by administrators, who can identify rule violations that may occur from introducing a new policy change and assess the impact of that policy application.
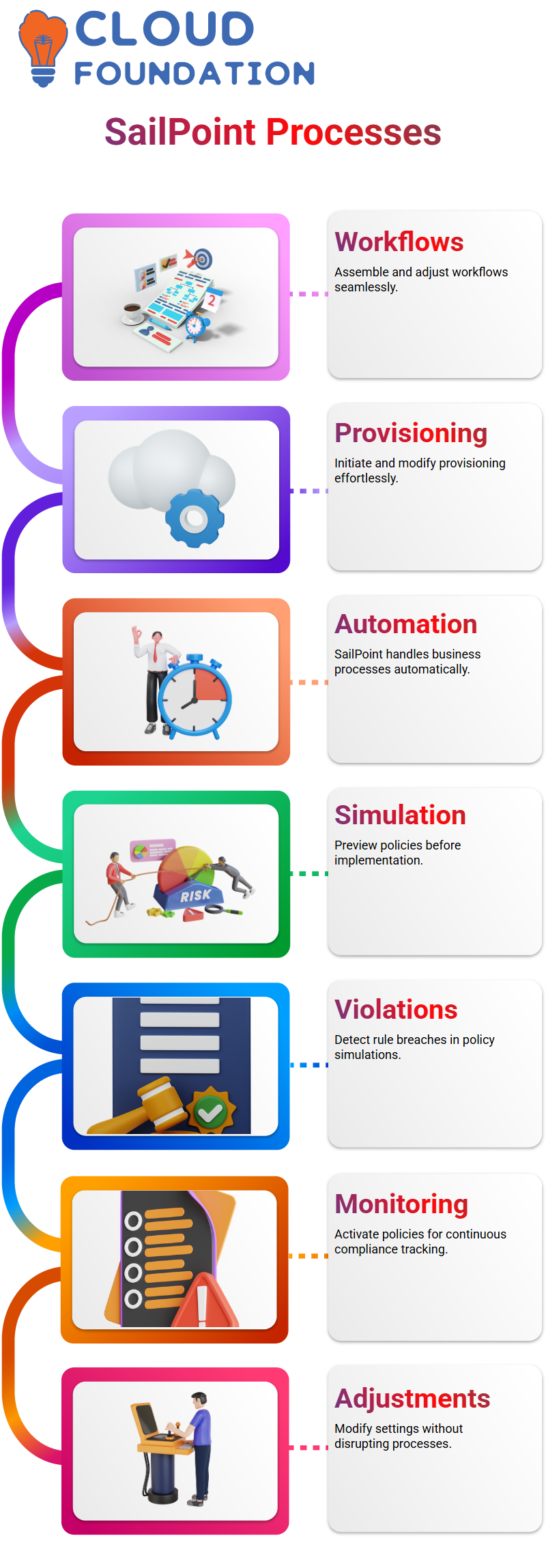
Through the conduct of a simulation, SailPoint initiates background tasks that, in turn, evaluate the level of conformity to the given rules.
Once the personnel in charge have confirmed these tasks, the policy can be activated for 24/7 monitoring and implementation.

Navya Chandrika
Author



