Sailpoint access risk management Tutorial
SailPoint Risk Management
Risk management is like the protective layer over an organization’s security which guards the empathetic data and identities from opportunity dangers. But it’s not sufficing if we speak about SAILPOINT, as it gets tied to the route of identity access and application permissions that this system entails.
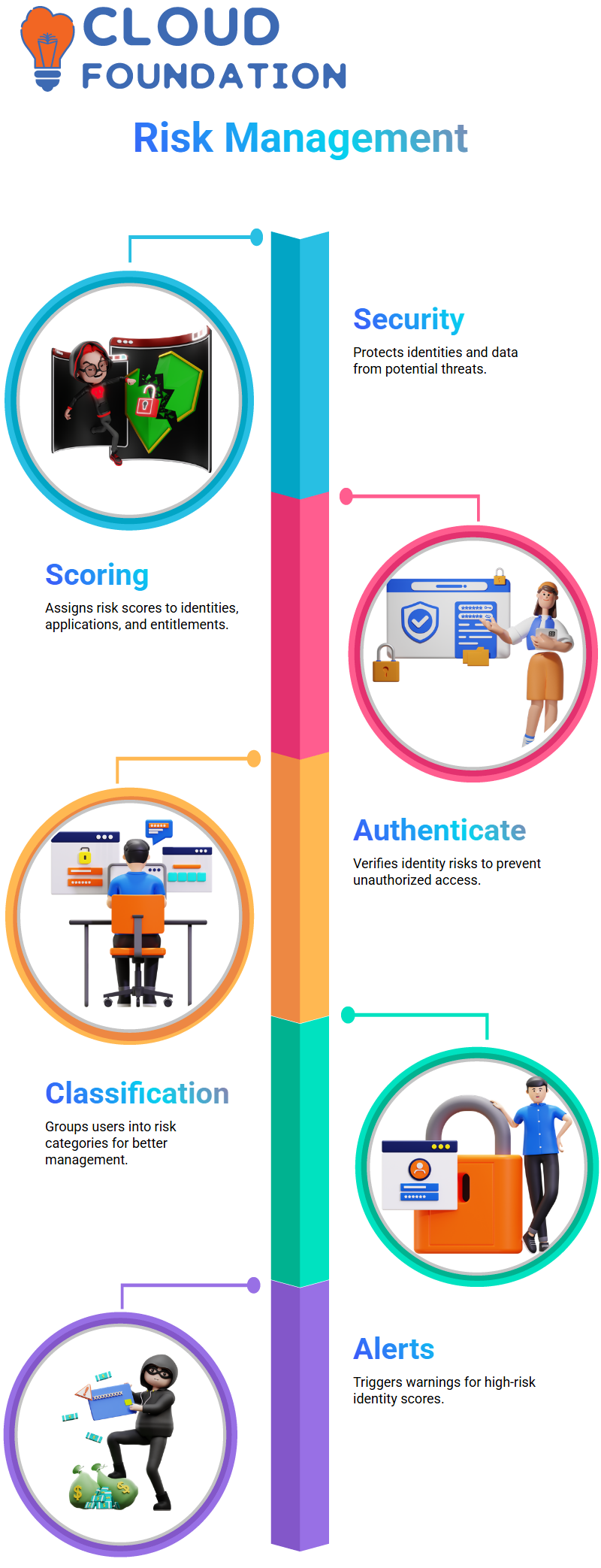
One of the major tasks of companies in identity access management space is to grade the risk level of access.
The dais from SailPoint is quick to bring in under one roof, the ability to outline risk management blueprints, run the risk, and carry out the evaluation by assigning risk scores to varied identity assets, applications, and entitlements.
In one case, banks verify the risk profile before the sanction of a loan. SailPoint also follows this process when it checks the identity risk by authenticating fortunate access and assignment of entitlements preventing the unauthorized use.
Raising the risk factors in SailPoint is an important part of carrying out high-risk user identification Properly set identity risks release the security people find the weak spots fast and thus be able to give the security assessment
By applying SailPoint, companies are also able to break down risks into different categories such as permissions, characters, and access This is the only way to conduct certification which is not only quicker and more intent but also aspired at the users who have high-risk access privileges.
How SailPoint Helps in Risk Scoring?
Mastermind is an interesting character in all the identity scoring party which is nothing without the kind-hearted handshake of SailPoint Major customers of SailPoint have gone through with the certification process more frequently, like once a month, which is the most competent way to identify high-risk users
Productivity and security find their way in SailPoint to measure the threat level of registered identities, and later they are placed in risk groups of low, medium, and high
This makes risk classification more exact and adaptable for the company to have the ability to set the bands according to the risk they are dealing with. Organisations can specify the number of bands, making the risk classification more definite and adaptable
SailPoint’s configuration sanctions admins to specify the limits beyond which a user’s risk score would sound the alarm and generate alerts Above the 750-point Mark, one of the policies is broken, and the responsible stakeholders are as well as the managers are the ones informed.
SailPoint Risk Management Solution
Mitigating identity threats is a cornerstone of today’s cybersecurity environment, and SailPoint is just the right solution for organizations examining to be assured SailPoint’s friendly.
Entitlement management policy states that the users dismiss be eligible to ask for additional access once a certain entitlement is already in place
There is nothing to worry about with SailPoint’s policy engine, as it guarantees that a user choose not to get an entitlement that is contradictory to the current one.
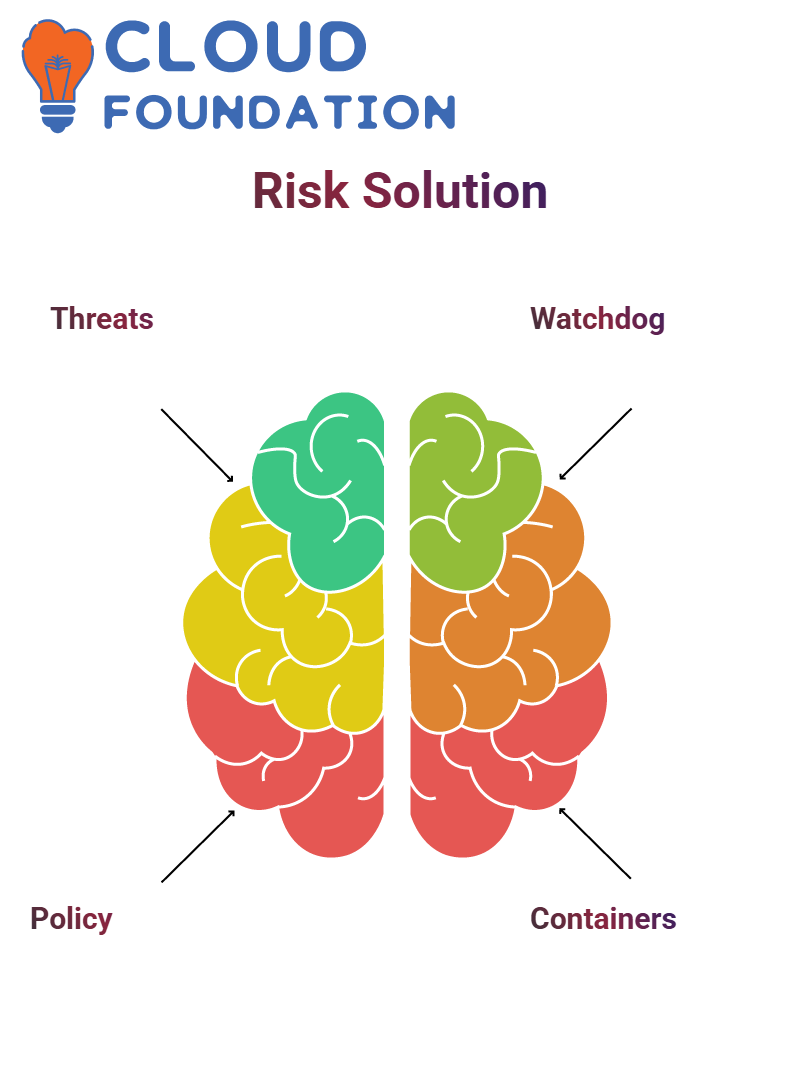
Despite its rating blown out of all magnitude, SailPoint is in work on a kind of a watchdog for excess risk.
SailPoint potentially solves a vital obstacle regarding both, the new and the old users. The company’s solution nurtures the implementation of the new hires’ activities and the managing of operations that fall into the category of legacy entitlements for the existing employees too.
SailPoint’s Distinctive Role
A sample should give clarity and show why SailPoint is exceptional—it relies on containers that are prime for managing duties automatically.
These containers combine together sundry tasks and permissions so that method simplification is achieved. SailPoint’s hierarchical structure makes sure that the capacities has the right structure and that are linked dynamically.
Be it business functions or IT tasks, SailPoint seems to be creating for itself a very nice environment for expandable identity management.
Role Assignments Tracking in SailPoint
By productively managing role assignments, SailPoint becomes the sole identity governance role. Not only that but when a role contains a certain entitlement which has been disapproved, SailPoint will widen the role alone, search and add the indispensable entitlement.
![]()
Approval processes are consistent with the lane of entitlement requests so that there are no worries related with user access management.
Approval Workflows in SailPoint:
Sharply contrasts to traditional methods, SailPoint sets approvals with business rules, which are fixed at runtime.
If both the requestor and approver are identical, SailPoint automatically approves the request thus, eliminating the need for redundant steps.
Approvals can be setup through role owners or managers thus adding flexibility to access control.
SailPoint Role Management
Implementation of SailPoint’s role management, not only gives structured and automated access, but it can assign the users with entitlements according to some predefined standards.
In the absence of role mappings, access assignments can lead to orderliness, security risks, and inefficiencies.
It usually requires organizations to spend time at the beginning of the setup phase to make sure that the right mappings are set up.
Business owners and application managers hold an indispensable position in the division of labor, shaping this up by matchmaking who does what.
Mostly, it is the Achieve excellence sheets that are applied to get the imperative entitlement assignments affirmed before implementation in the SailPoint software.
SailPoint and Bulk Access Assignments
SailPoint is featured with a strong point that it can conduct multiple (bulk) entitlement assignments at a time The bulk entitlement assignments are often created by companies who use tools to generate structured Surpass sheets that are then configured in SailPoint’s system.
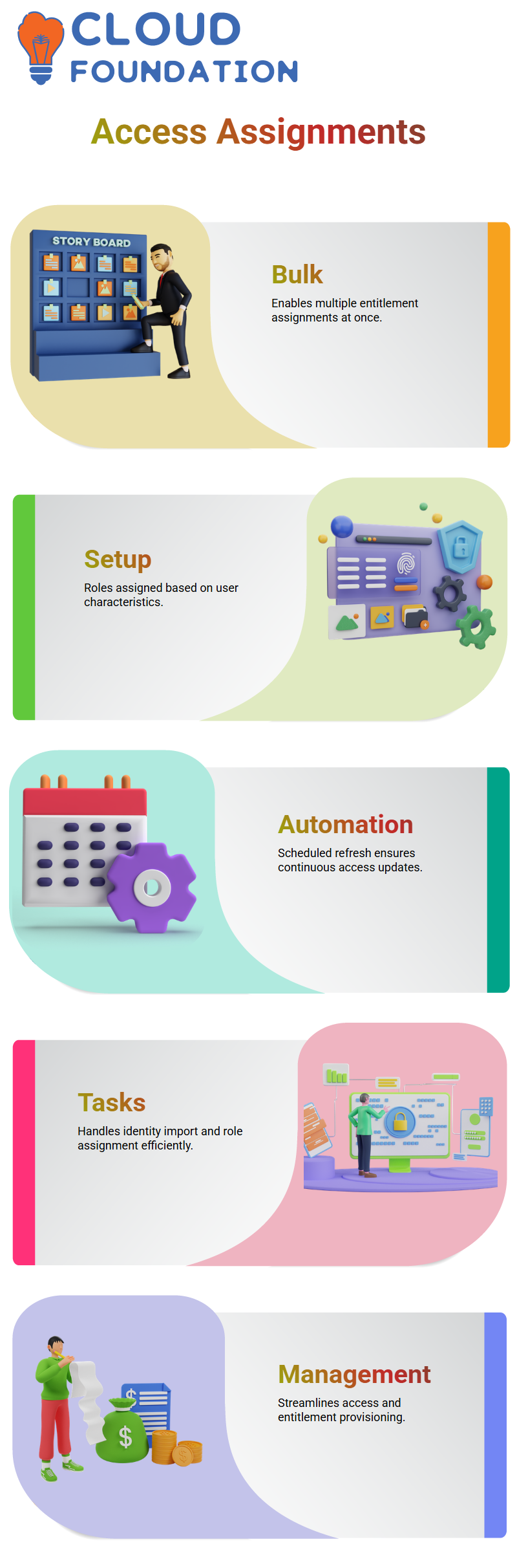
During the setup process, bulk role assignments are made based on user characteristics like the department or location.
When configured, SailPoint automates the assignment process by means of scheduled refresh tasks; thereby, users get the right access continually, subject to their eligibility.
SailPoint Tasks
SailPoint is a powerful identity governance dais where tasks are one of the essence parts of process automation.
Tasks expedite the work of the different operations with much competence, such as identity import, role assignment, and access management.
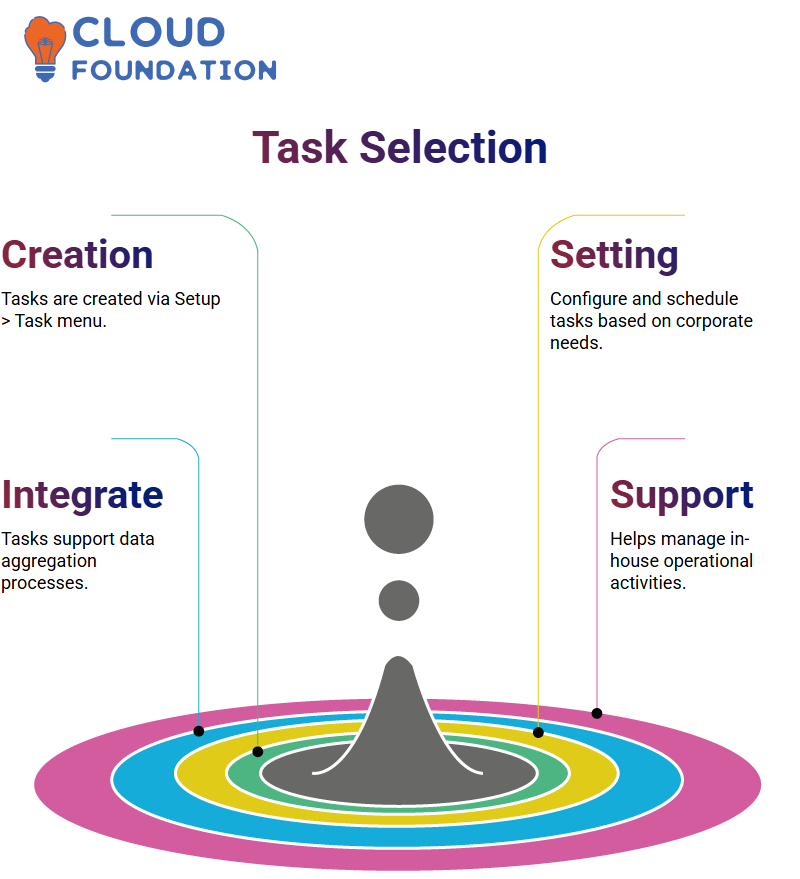
Selecting Tasks in SailPoint:
A new task can be created in SailPoint by first going to Setup > Task. Here you can go through all tasks setting and scheduling protocols based on your corporate requisites.
The tasks form an integrated part of the data aggregation process and the in-house support activities.
Indications of SailPoint Task Status:
Supervising SailPoint tasks helps see the background activities clearly and secures trouble-free work.
People could overview the logs of tasks and that’s where they find errors in order to fix them and also upgrade the management of identities and access.
Ritual Task in SailPoint:
Imagine I have to assemble a routine SailPoint task to update the properties of identity for just one user.
In this case, instead of creating a new task from the very start, I would rather choose to take a copy of one and modify the main parameters
The first thing is that you have to make sure that the ID values from the task copied are taken off. If you forget this action, the new item opt against be created, but instead it will amend the original one.
SailPoint Task Scheduling
Yesterday we took the time to discuss both the creation and operation of tasks in SailPoint. Today, although, we are talking about the process of monitoring and scheduling these tasks proficiently.
The tasks in SailPoint include creating the communication groups, identity refresh tasks, and certification service. If there is a need for way tasks, we can fabricate and enforce them as required.
SailPoint System Tasks and Their Worthiness
SailPoint has brought to us several tasks that could be done automatically by the system for some of the house-keeping processes.
These can be mainly about monitoring expired work items, operating sunset requests, and other management tasks surrounded by the system.
One of the many duties that fall under my part as someone who works with SailPoint is observing these tasks and making sure that they are functioning properly and without any failures.
Employing Logs for Task Tracking in SailPoint
Log records are done in the system for every time the rules are executed in SailPoint thus capturing all the details.
Admins can investigate the execution status by reviewing timestamps, and they can also verify results. This way, admins are able to make sure of identity operations without actually going to each illustration.
The logging system of SailPoint brings transparency, which is very helpful for the resolution of problems and the most competent performance of automated workflows.
Identity Governance with SailPoint
SailPoint tasks automate a lot of mundane processes and this way contribute to a more productive identity governance of an organization Identity management, risk mitigation, firm access provisioning, are the benefits received by organizations through properly structured identity management.
Performance Troubles in SailPoint
The task of SailPoint to continue the Performance system takes control of the system activities thereby makes the system’s certification, access requests, and policy updates tasks run well and smoothly.
When any of these processes get stuck, everything else related to it also stops. The administrator should immediately take action, thus verifying continued performance without interruption.
Frequency and Scheduling in SailPoint
Real-world SailPoint implementations usually organize task executions so that every five minutes they are automatically started.
In this way, the system is updated on a continuous basis and the skillfulness of the system is kept High. Thus, the task becomes late-night execution and that is a favourable arrangement, as it prevents the disturbances of peak hours.
Role of SailPoint Developers
While SailPoint administrators are in charge of the functioning of system tasks, developers are instrumental in creating tasks that are tailored to individual clients.
In the incident of a customer needing a task that is best suited for certification requests, developers come in and make it, then they integrate it into the system By applying already existing tasks, they decongest the steps and make the system functional.
SailPoint’s Business and IT Characters
One of the most widespread misunderstandings is that business jobs are for non-technical users and IT parts are for technical teams.
This is the way SailPoint does it: business parts are the logical part of a given assignment and IT jobs clarify the entitlements.
This interpretation protects that SailPoint permits access management to flow through it without it being overburdened with too many processes.
For large organizations, the induction of IT trainees relies on access provisioning systems SailPoint deconstructs the whole procedure by matching entitlements with symbolic functions.
Applying the business role model for IT training, SailPoint becomes the enabler of the automatic access to multiple applications thus minimal human intervention.
What about SailPoint that I could share with you? The business parts and IT positions in SailPoint are interchanged in such a way that the former greatly affects the latter.
The business role is what sets the standards for the user’s role assignment. If, for sample, I where the user, the business role would choose the way my role is assigned to me
On the other hand, the IT role specifies entitlements which are the set of privileges that get assigned.
These two positions are heavily interrelated, hence providing a channel for identity management.

Navya Chandrika
Author



