Okta Security Policies | Okta Integrations
Okta Authentication Policies
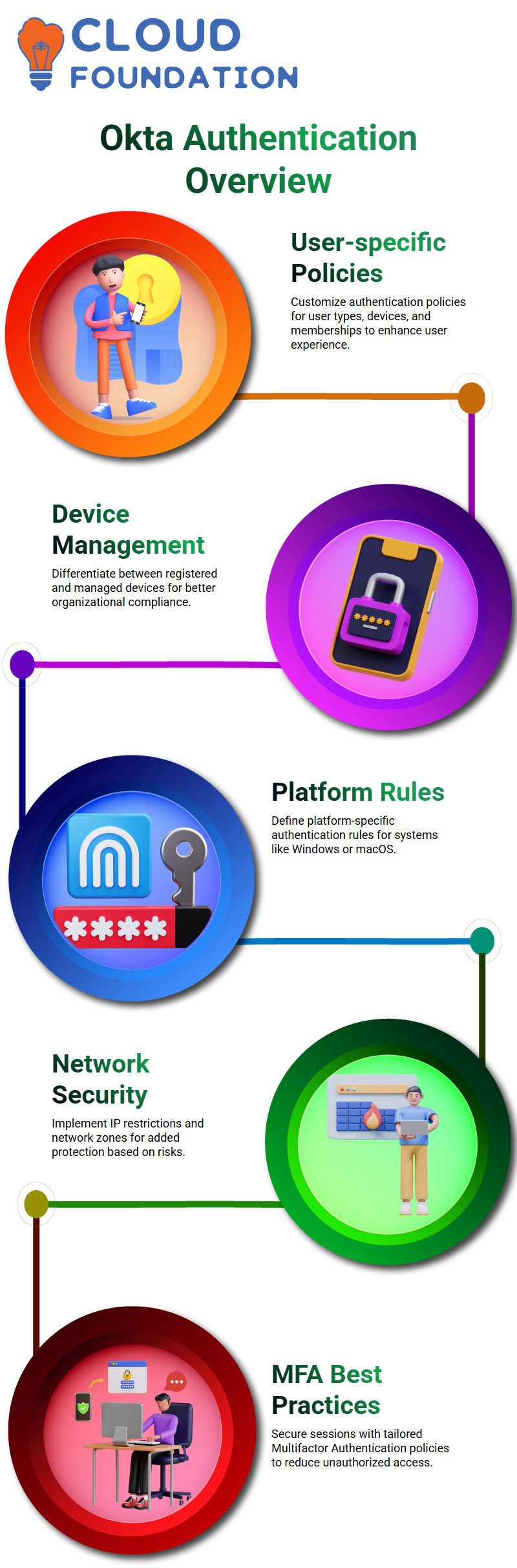
Let’s delve deeper into Okta’s authentication policies and explore how they can be tailored specifically to meet your organization’s needs. With Okta, you can specify user types, membership levels, devices, and even user types if desired, offering users an exceptional authentication experience.
Okta allows you to distinguish between registered and managed devices—for instance, an item registered but unmanaged needs to be connected through organizational norms to function.
Okta allows you to define platform-specific rules. Whether you use Windows, macos, or another platform, Okta gives you complete flexibility in customising authentication policies for every platform available to you.
Okta and Network Restrictions
Okta allows you to implement IP restrictions and network zones. For additional protection, set policies depending on risk type.
Expression language in Okta provides administrators with an extraordinary tool for defining precise rules. When crafting specific policies, you can access user properties like device profiles and security risk levels.
Global Session Policies in Okta
Okta’s global session policies offer groundbreaking advancements in session management. You can leverage MFA sessions and configure behaviour rules, such as adding cities, countries, or devices.
Okta can secure each session using Multifactor Authentication (MFA), requiring users to authenticate every time they log into Okta with either their current device or new devices – in either instance Okta will prompt for authentication again – providing additional layer of security against account compromise or fraud.
Okta’s best practices call for setting up MFA sessions whenever users sign in from new devices, although repeated prompts for MFA could become irritating to some users, thus policies must be tailored based on user behaviour to avoid irritating prompts for MFA authentication.
Session Management with Okta
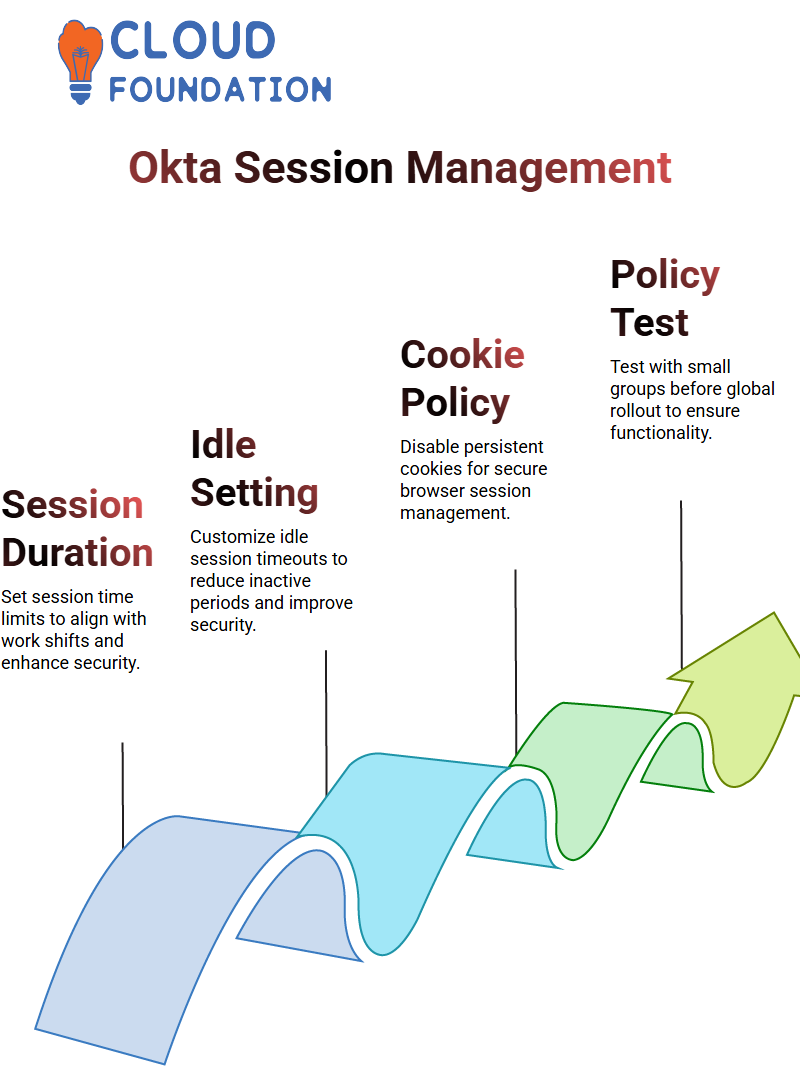
Okta makes session management an integral component of its functionality, with optimal settings being eight hours or shorter as recommended by typical work shifts and subsequent reauthentications required to protect security.
Okta allows administrators to customise idle sessions. For instance, if a user remains idle for over 55 minutes without engaging the session, Okta will prompt them to sign in again, thus reducing extended inactive periods and improving security.
Okta’s session policies can easily adapt to meet your organization’s unique requirements. Whether that means setting time limits or managing idle sessions, Okta provides flexibility that fits right in with what works best for your organisation.
Understanding Okta Session Policies
When dealing with persistent session cookies across browsers, consider how Okta settings are configured. It’s essential that these settings be disabled; otherwise, your session remains active even after closing and reopening browser windows. Disabling ensures it ends once closed—an essential setup for creating secure policies and managing session control within Okta effectively.
Okta provides complete control of session settings through global session policy settings, giving you full command over session length, for instance, by setting them for eight hours only. However, keep in mind that Gmail could require two days between logins—something Okta cannot manage in such instances but instead ensures tight policies adhere to Okta controls.
Applying Okta Policies
Start small when applying policies within Okta. Don’t rush; first, create a test group of 10 users who can evaluate them before rolling them out globally. Once everything works as intended, document your process through screenshots or recordings before rolling out policies to everyone.
I learned my lesson the hard way. Early on, when applying policies universally to myself as well, including myself, that can quickly result in being locked out from working properly—trust me on that one! To avoid such headaches in testing policies, always exclude yourself.
Exploring Okta’s Profile and Development Features
Okta does not enable self-service registration by default, which makes sense in workforce environments. Allowing this feature would mean anyone could create accounts independently within Okta; thus making the platform unsuitable when managing company-related accounts. But this feature may still be enabled and customized as desired for customer identity use cases like user subscription management on platforms like Zoom which utilise Okta to effectively manage customer identities using its flexibility.
Okta offers support for numerous identity providers for configuration. Popular choices such as Apple, Facebook, LinkedIn, Google, GitHub Microsoft PayPal & Salesforce come preconfigured allowing Okta to seamlessly integrate its login system with various webpages making them flexible enough to meet different organisational requirements. For instance integrating Google with Okta provides seamless login solutions – ideal for adaptive organisational environments!
Okta Integration with Google IDP
Let me demonstrate how Okta can integrate with Google Identity Provider (IDP). A Google account is essential when setting up this integration; otherwise, no progress would be possible in setting it up and proceeding with customer identity products available through Okta.
Okta provides flexible authentication solutions in many instances; however, certain circumstances require integration with platforms like Google IDP. Selecting Google as the IDP provider in Okta requires access to Google Admin Console and a G Suite account; your environment might already possess either of these credentials!
Integrating Okta with Google IDP creates seamless login experiences. Suppose a client lacks credentials but still needs to log in. In that case, Okta provides authentication through their Google account, which then passes all relevant details directly to Okta for seamless login experiences.
Okta’s Role in Social Login
Okta simplifies customer login methods by offering social login options like Google, Apple, or Microsoft sign-in buttons across various platforms, eliminating the need to create accounts from scratch!
Customer-oriented tools often benefit significantly from social login capabilities. By employing Okta, businesses can enable users to log into existing accounts like Google. This feature streamlines customer acquisition.
Okta as the First Line of Defence
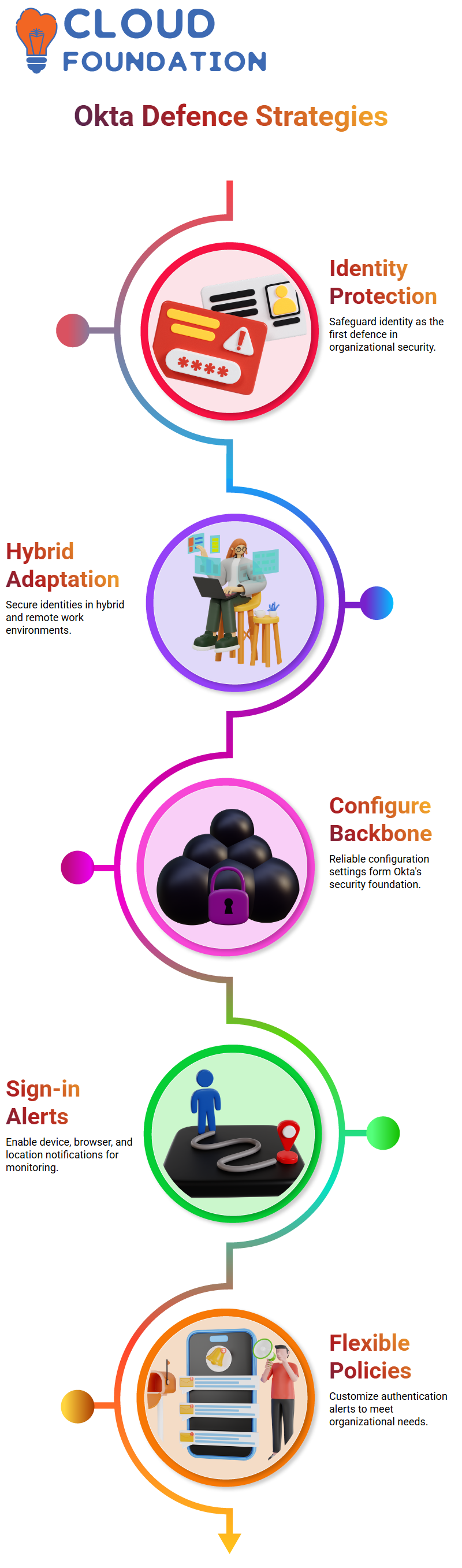
Identity is paramount to security; think of it as your first line of defence for your organisation. In the past, corporate networks were typically isolated – you logged on and went about your day – however now, due to hybrid and remote work arrangements, things have changed considerably; should your identity become compromised, the security of the entire organisation could be at stake; which is why Okta plays such an integral part in safeguarding identities.
Why Organisations Need Okta
Many organisations are turning to Okta for security, yet not everyone appreciates its value. Okta should not simply be seen as another tool; rather it forms the backbone of any successful security setup authentications and defence strategy- , with configuration settings lasting until next update, making the platform even more reliable than before.
Key Okta Notifications to Enable
Okta offers numerous notifications that are essential to its effectiveness, with sign-in notifications being an eye-opener. Every time someone logs in from a new device, browser, or location Okta detects this event and issues an alert – this behaviour is easily configurable to fit into any organization – from five authentications all the way up to fifteen authentications at a glance – Okta makes that possible for you.
Behaviour Detection with Okta
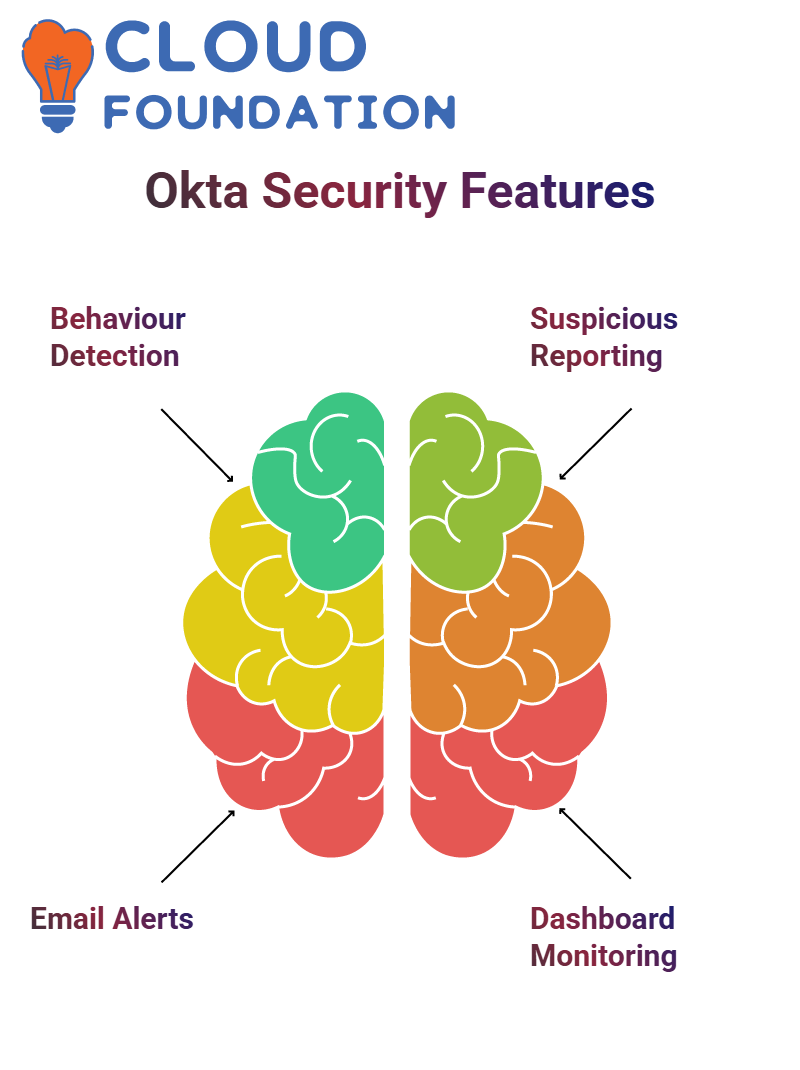
I highly endorse Okta’s behaviour detection feature. This feature compares criteria such as city, country, and device authentications to any suspicious activity that might arise immediately and flags it for immediate addressing by information security personnel or administrators. Okta makes customising settings suitable to any organisation easily possible!
Okta’s Email Alerts for Security
Okta provides email alerts for critical activities like password resets or MFA changes, such as resetting or enrolling MFA methods. Anytime someone attempts to reset or enroll their own MFA method, the user is immediately informed, so if anything suspicious arises, they can report it immediately. Okta even provides a “Report Suspicious Activity” button directly within their emails to make reporting suspicious activity even simpler!
Monitoring with Okta’s Dashboard
Okta’s dashboard serves as your command centre; when users report suspicious activities, this user-friendly interface keeps you apprised about potential security threats and can help manage and monitor incidents more effortlessly than ever.
Understanding Okta Settings and Configurations
Let me introduce some key Okta settings that can make managing the security of your organization simpler. Let’s begin with logs – always monitor them regularly in order to make sure everything runs smoothly; sometimes false alarms pop up, but when something doesn’t, your infosec team needs to act swiftly- it is always better to be safe than sorry!
Customising Okta Email Notifications
Okta email notifications can be extremely valuable tools. Once users receive activation emails, they must activate their accounts within a specified amount of time—generally seven days—to complete registration and activate accounts via email. You can adjust this setting based on your organization’s needs, but I recommend leaving these notifications enabled, as it will improve overall security.
Leveraging Device Binding in Okta
Device Binding in Okta is another essential setting. This function ensures that devices are securely connected to user accounts. I find myself heavily relying on this feature, although integration with other systems may take careful planning. Keep it enabled; the results will speak for themselves!
User Activity Visibility in Okta
Okta makes user activity visibility an excellent feature to enable. Enabling it allows users to see recent activities, which can be transparent and secure; however, turning this feature off prevents users from gaining access to such data.
Okta Mobile App and Identity Engine
As for Okta’s mobile app, earlier versions allowed users to sign in through its login interface; with Identity Engine’s integration directly, however, all this has been optimized and simplified; meaning no more worrying about maintaining legacy mobile apps – everything goes through the updated system seamlessly!
Okta Threat Insight: Your Security Shield
Okta Threat Insight is my go-to recommendation for robust protection, providing your Okta tenant against malicious attempts and providing customisable alerts when threats are detected (for instance logging incidents and/or enforcing security protocols). It truly offers game-changing security.
Defining Zones in Okta
Okta Zones allow you to define trusted networks. Say your company operates offices in New York, Los Angeles and Texas: By creating IP zones named ‘NY Office’ containing gateway and proxy IPS gateways; once saved Okta Threat Insight automatically authorizes trusted access from within these zones while flagging anything outside.
Enhancing Security with Okta IP Management
Okta makes managing an intrusion prevention system (IPS) an essential element of network security, and when setting it up it should remain unmodified unless necessary. If someone may have gained unauthorised entry to your network, allowing brute-force attempts from internal or external attackers compromises security; hence it’s wiser not to add exemptions casually as later you could add sign-on and multifactor authentication policies and adjust accordingly if needed.
Blocking Specific Countries with Okta
Certain legal requirements mandate blocking IP addresses from specific countries. With Okta’s dynamic zones feature, this task can easily be achieved. By default, Okta blocks requests coming in from Russia; any user needing access from that nation must go through an approval process with both Okta and, potentially, the Department of Defence before being granted entry to an Okta tenant.
Create zones by giving them descriptive names like ‘Block for US’ or ‘Country Restrictions.’ Next, choose which countries should be blocked such as Iran, Syria, Afghanistan, Pakistan or Russia and block IPs coming from those regions automatically; this increases security while potentially depriving users who travel there from access. However, such restrictions also prevent valid users from traveling there due to this approach being blocked out as well.
Managing Tor Traffic with Okta
Okta’s system can detect and block traffic from anonymizer proxies like Tor. This feature is particularly relevant as Tor enables individuals to hide their location and identity online, yet any attempt at accessing Okta through Tor traffic will automatically be blocked, providing added assurance that even anonymous sources don’t breach your network – an invaluable way of providing robust network security globally. This global capability plays an essential role in maintaining robust cybersecurity practices.
Utilising Okta’s Health Insight Features
Okta provides health insights with security recommendations designed to bolster your network security. Although not mandatory, following them would certainly improve system protection; for instance enabling new sign-on factors, device enrollment, or password resets is one way these recommendations may assist with increasing system safety. As tasks are completed they’re removed from Okta’s recommendations list to keep an overview of what has and hasn’t been accomplished thus letting you easily assess progress made so far and track what needs to be accomplished next.
Assigning Okta Administrator Roles
Okta offers a straightforward list of administrator roles with clearly-outlined permissions, making assigning super admin privileges sparingly essential; otherwise accidental or malicious changes increase risk significantly. Reviewing and adhering to role documentation ensures better management and security in new companies or environments.
Managing Administrators in Okta
Setting up administrators when working with Okta is of vital importance. For example, creating roles such as read-only administrators ensure that sensitive configurations remain safe while still offering visibility into them.
Configuring Reports and Logs in Okta
Okta has the capacity to store logs for up to 90 days, however you should integrate external systems like Splunk or SIEM tools for crucial projects in order to extend this window and ensure complete auditing or investigations beyond this 90 day limit.
Understanding Resources in Okta
Okta resources can be tailored to suit specific requirements. From group admins and application administrators, to resource sets containing particular applications with administrative rights assigned, Okta makes resources flexible enough to suit almost every need. If an administrator needs access rights for one specific app or resource set for multiple ones – even without your intervention! – then simply assign these roles accordingly for greater control. If someone needs specific apps managed then creating resource sets for those apps and assigning administration rights could provide exactly the solution needed.
Assigning Application Administrators in Okta
Assigning an application administrator in Okta is straightforward. After selecting a user and assigning them the role, just assign it to any resource set you desire based on their needs or use cases – whether full access or read-only permission is desired.
Connecting Okta with External Tools
Okta offers seamless integrations with several tools from Microsoft, IBM and Splunk; linking these tools ensures logs and security incidents are archived safely for future reference. As one of your first tasks to tackle in Okta implementation, prioritising integration should be prioritized accordingly.
Exploring Okta’s Identity Engine
Okta Identity Engine provides updates to authentication policies such as password policies, sign-on policies and multifactor authentication to enhance security. Staying abreast of these developments will allow you to take full advantage of Okta’s capabilities.
Understanding Okta Authentication Policies
Let me guide you through Okta’s authentication policies – everything from sign-on policies and multifactor authentication policies, all the way up to their core principles – trust me; they form the core of working with Okta; they’re essential in controlling access.
Okta’s Approach to Application Integration
Okta makes application integration a seamless experience. While integrating apps may appear routine at first, I will show you step-by-step how to utilise Okta so you’re always set up for success!
Exploring Okta’s Multifactor Authentication
Now, let’s investigate Okta’s multifactor authentication policies. Okta professionals have long discussed this feature as one of its hallmarks; after all, multifactor authentication provides peace of mind when accessing digital services today.
Why Okta is a Must-Have for Professionals
Multifactor authentication is one of the must-know features for Okta professionals, , making an essential tool in managing secure sign-ons. Okta’s approach is user friendly yet robust – an indispensable asset when handling sign-on processes with Okta.

Mastering Okta’s Day-to-Day Operations
Okta simplifies daily operations beyond policies and settings; from adding apps or tweaking existing policies, Okta’s tools make the task straightforward and manageable.

Navya Chandrika
Author



