How to Configure Policy Violation Alerts and Escalations in SailPoint
Policies in SailPoint
Policies are the backbone of an organisation. They strive to ensure that employees adhere to the established rules and regulations.
In the SailPoint sphere, users are set (or authorised) by policies, and security rules protect them. Although what is a policy?
A policy is simply a set of regulations that every employee must follow. With SailPoint, businesses can implement various policies that guide them through all regulatory facets and ensure security.
These active rules are instrumental in determining user assignments and their corresponding access permissions.
Identity Governance is a major cornerstone of SailPoint that helps oversee matters related to identity more definitively.
The ability to write concise and clear policies at the organisational level is one of the pivotal features of SailPoint.
It can be seen that users’ access rights are manipulated through established policies, i.e., the standards of least privilege.
No one could access the system except recognised users. A policy definition architecture eliminates arbitrary entries and establishes data security.
If a person is allowed into the production system, it is logical that they should not have access to the developer environment. SailPoint is capable of setting and retaining such regulations for enterprises uninterruptedly.
Types of Policies in SailPoint
You can find SailPoint varied policies intended for different business targets.
Some of the policies commonly adopted are Role-based Separation of Duties (SOD), Entitlement-based SOD, Useful Entitlement SOD, Activity-Based SOD, and others.
Permit’s see how Role-based SOD policies function. The organisations verify that no conflicting tasks are assigned to the same user, thus complying with regulations and preventing unauthorised access (when creating these policies).
Policy Violations in SailPoint
A potent mechanism is built into SailPoint to resolve policy violations easily. When a breach occurs, policy owners and administrators receive alerts to prompt immediate correction.
Companies can set up escalation and notification processes in SailPoint so that, in the event of a policy violation, the required action is taken promptly.
Through competent policy management, businesses can not only enrich the security framework but also reduce access control complexity.
Policy Rules in SailPoint
Elucidating the policy rules in SailPoint is unequivocally one of the most potent operations. You can develop positions like SOD (Segregation of Duties) and interpret conflicting characters to prevent unauthorised access.
For example, guidelines have been created to ensure that users are not added to the Accounts Payable ledger and that female employees are not held responsible at the same time.
You can assign more than one regulation for a single policy if required. I have found that this aspect is notably valuable for maintaining agreements across different departments. Additionally, the system enables the fabrication of a condition and tests it for potential violations before executing the actual policy.
Setting Up Policies via SailPoint
If an admin wants to create a policy, they should go to the policy setup section, where a new policy can be initiated. These policies help control the level of access and the type of application.
There are various types of policies, including activity policies, risk policies, and entitlement policies. Organisations can specify policies based on their security necessities, Alice.
Separation of Duties in SailPoint
Separation of Duties (SOD) is an essential concept in SailPoint that enables user access control to be staunch by the job.
In a good representation, a developer exclusively has access to the development context, while a tester is only allowed to the testing localities.
Through the implementation of SOD policies in SailPoint, user groups within an organisation can be controlled, and excessive rights can be prevented.
This not only ensures the data is safe but also protects the system from security risks, making it easier to verify that industry rules are followed.
Role-based SOD Policies in SailPoint
Setting up Role-based SOD policies in SailPoint is a necessary and straightforward process. The administrators take the requisite steps to outline absolutely the assignments that cannot be assigned together to a single user.
For example, a manager who has been granted the privilege of approval should not be allowed to submit their requests as well.
After such policies have been established, SailPoint will verify that access restrictions are automatically imposed. By doing so, the system ensures that users only operate within their assigned functions and don’t cross the lines of access.
SailPoint Escalation Management
When you work with SailPoint, managing your escalations properly is of great value.
If you do not wish to proceed with the escalation process and do not want to send reminder emails, you have the option to modify these actions internally within SailPoint. For illustration, you can decide to send reminders when the policy is broken by selecting the right setting.
SailPoint enables you to choose the days earlier than the first reminder and the reminder’s recurrence configuration.
You can even pick or make the reminder email template through the same application.
This adaptability gives clarity to the communication that the company requires.
Creating Objects in SailPoint
When adding new objects in SailPoint, it is essential to update the existing ID values to avoid transparently merging issues.
An illustration of an outcome would be a most apt response to a variety of mistakes, such as the policy violation reminder.
When creating a new policy violation reminder, ensure that you specify the ID values to prevent duplication. Creating the templates for these reminders is not difficult at all, and you can even customise them to suit different policy violations.
From SailPoint, I see that making a copy of a particular object, making necessary developments, and then saving it as a new template is the quickest way.
To see the adjustments, you might need to refresh the page. Exploiting this trick, there is a far more expedient way of doing management.
SailPoint Identity Escalations
SailPoint offers multifaceted options for reminders and escalations by setting them up for multiple days; you can also initiate a follow-up action if no response is received after reminders.
The configuration for the latter encompasses the setting of obligatory identities or the writing of individualised rules for escalation emails.
For illustration, I usually prefer to set it so that escalations will commence after the third reminder.
You can simply select or blueprint templates to forward these escalations, as long as the key actions are not omitted.
Preventing Conflicts with SailPoint Policies
It’s easy to use SailPoint for preventing duplicate assignments to the same user or access denial, which the system handles automatically. For example, I’ve set the tool, and it was found that a user cannot have both the Accounts Payable and Accounts Receivable parts at the same time. Additionally, the procedure alterations serve as an extra guarantee of agreement.
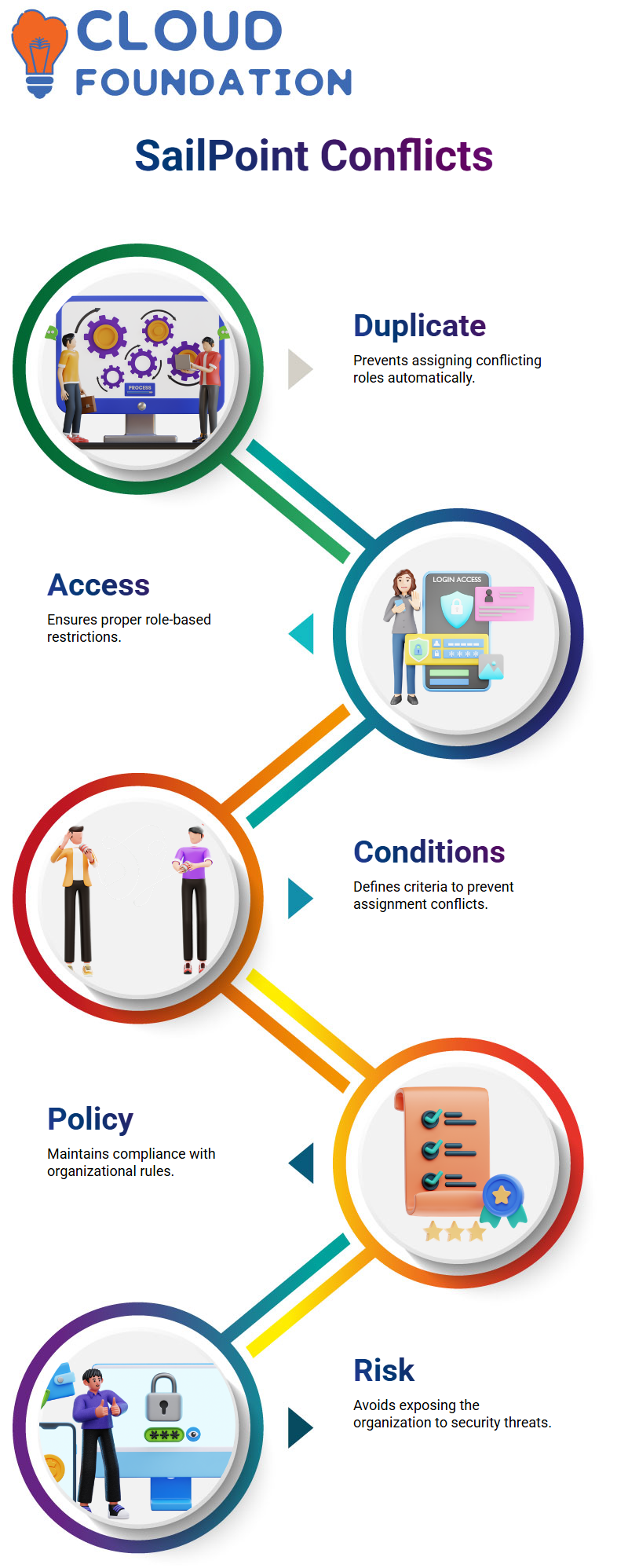
The solution to the problem arose in that I was allowed to specify precisely which conditions must be met to avoid conflicts, as well as to prevent new users from creating new characters without liability. The reason behind this forward-looking initiative is not to expose the organisation to risk, while also respecting the established organisational policies.
Access Approval Method in SailPoint
Watching in-depth into SailPoint workflows, we can also discover the substantiation approval configuration.
If the ‘policy scheme’ is set to ‘none’, SailPoint permits access regardless of any policy checks made.
Nonetheless, when the policy scheme is marked as ‘interactive,’ SailPoint checks the access requests to ensure compliance with the rules. If a violation is found, the access request is blocked.
This quality, provided by SailPoint, is one of the most indispensable ones in supporting the security level.
There is also the simulation quality in SailPoint that helps organisations identify policy violations before implementing the shifts.
The tool helps administrators see how policies would affect users’ access, and then they can make the required adjustments.
An additional side note on the simulations is that companies that run simulations can thus be enabled to address talent conflicts promptly and confirm that their access management plans are consistent with the established security objectives.
SailPoint Policy Implementation and Aggregation
Policy administration with SailPoint helps to secure access to applications on diverse platforms.
These policies also make it obvious that users can see what parts of the application they are entitled to. Aggregation can put together reachability and permission data from sources such as LDAP directories.
To avoid manual review of entitlement lists, SailPoint offers bug-free solutions and provides full-time access to databases.
A company can be fully protected, and its clients can feel secure by not having to participate in the process manually.
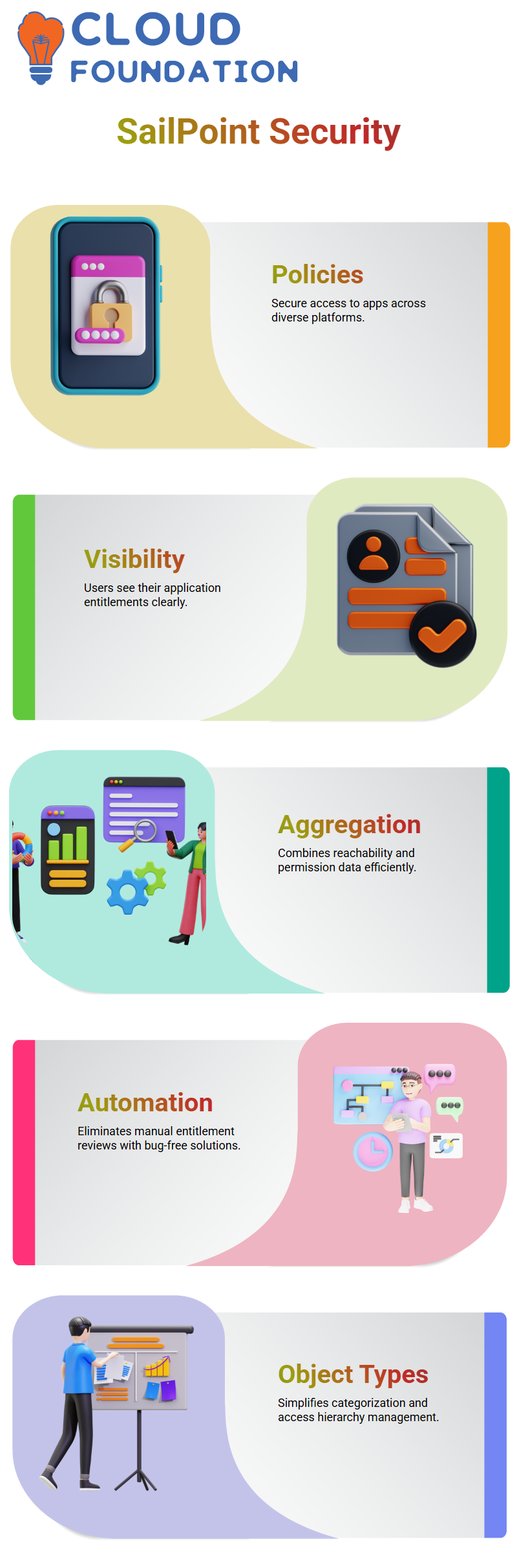
Object Types in SailPoint
Organisations gain from SailPoint’s capability to support a variety of object types, making permissions more clear-cut and thus categorisation more productive.
The addition of explicit object types, such as an “honoured group” or “role-based access,” can help administrators make data aggregation easier.
As for application onboarding, SailPoint enables end-users to arrange the object structures that correspond to the organisation’s access hierarchy. This creates an easy way for permission assignment and guarantees that only the users’ duties are obtained.
How Does SailPoint Conduct Target Permissions?
The centrepiece of SailPoint is its ability to perform target permission administration. Here, the target permissions specify the type of access that can be given to users within any particular application.
Instead of only employing entitlement aggregation, SailPoint enables organisations to specify explicit permissions that fully align with their needs.
For example, privileges in applications can be organised into different domains.
SailPoint has a structured method for detailing a set of permissions for a group of people, which is aligned with policies that prevent excessive access while still making it possible to be compliant.
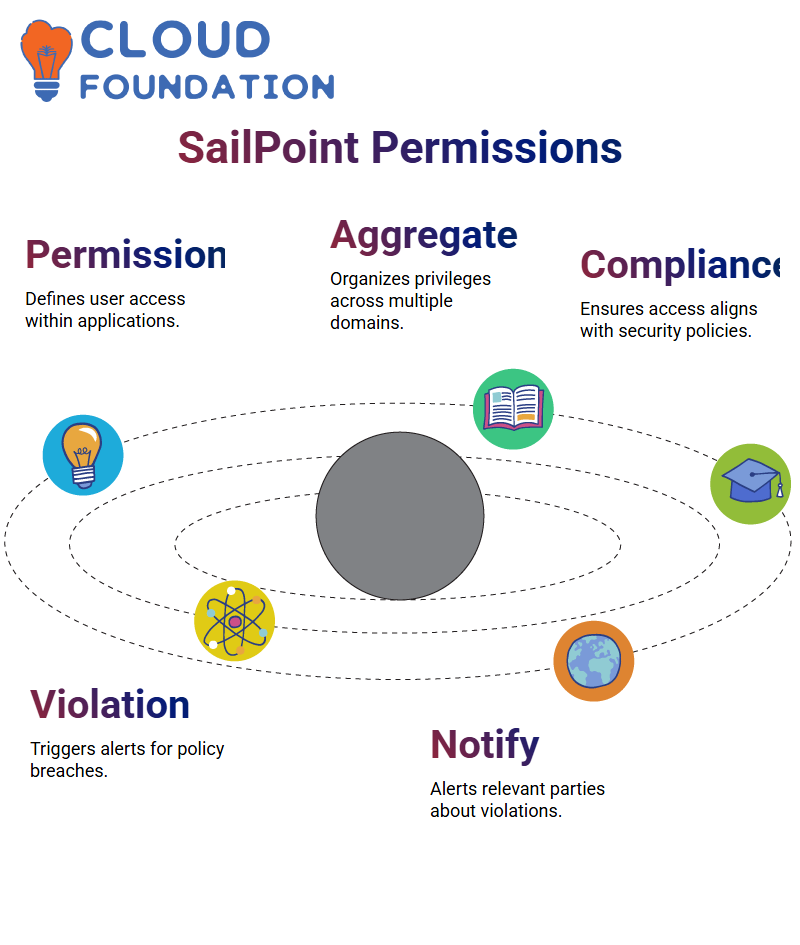
Establishing Violation Rules in SailPoint
With SailPoint, administrators can set up violation rules to ensure adherence to an organisation’s policies. For example, in case an organisation decides that the jobs ‘Prism Manager’ and ‘Prism User’ should be mutually exclusive, a violation rule can be set up in SailPoint.
Every time a violation occurs, SailPoint triggers alarms, and the relevant parties receive notifications, allowing for submission to be achieved.
SailPoint Business Rule Enforcement
There is one universal issue here, which is that companies struggle with contradictory business rules, for example, the positions ‘Prism Manager’ and ‘Prism User’
SailPoint authorises one request to be fulfilled by one role only, thus guaranteeing security and respect.
Users of SailPoint can restrict the possibility of a user holding multiple assignments that conflict with each other.
Removal of Jobs in SailPoint
SailPoint helps manage parts and access requests, but in some instances, conflicting jobs may need to be removed before an access request is submitted.
If you cannot do it, the submit button will be inactive until the conflicting role is eliminated. Here comes SailPoint, the perfect place to smooth the course.
Release does it ourselves–delete a conflicting role and observe SailPoint’s reaction. After that, the request will be accepted by the system.
This quality guarantees adherence to the policy and, at the same time, confirms that provisioning is safe.

Navya Chandrika
Author



