Azure Active Directory Module |What is Azure Management Groups?
Azure Active Directory Groups
To begin with, gaining a solid understanding of Azure Active Directory (Azure AD) and the different types of groups it offers is essential. One of the most important among these is the Security Group, which is widely used to control access and permissions within Azure environments.
Alongside this, the Office 365 Group plays a vital role in enabling team collaboration. These groups are commonly used in Azure to organize shared mailboxes and resources effectively.
In our Azure solutions, the primary focus is on Security Groups. These can be created and managed through various Azure-supported methods such as the Azure portal, CLI commands, or programmatically.
This flexibility allows for the creation of an infrastructure that aligns with your preferred management approach for Azure resources.
Azure Active Directory & Group Management
We are going to discuss Azure Active Directory and take a look at the different group types that are available Indeed, security group is the one type that is indispensable when it comes to the management of access and permissions surrounded by Azure.
The other one is Office 365 groups that are closely associated with the aspect of teamwork These are more about the shared mailboxes or resource organization inside of Azure surroundings
In our evaluation of inside fixes Azure, one of the classes of groups that we pay attention to is the security groups A security group can be created in a few different ways: the Azure portal, the CLI commands, or programmatically Each of the above-mentioned methods is flexible when it comes to the Azure resource management.
Managing Directories in Azure Active Directory
Azure Active Directory invitations a useful element; you can generate several directories tailored to your needs.
When you first sign up for a free trial, a default directory is set up for you. Although, you are able not only to produce and add directories at will but also to switch processes as indispensable, which implies a high level of independence to administrators and at the same time, an extremely useful tool for supervising detailed customer conditions in Azure.
Each directory can specify its own user pool, be connected to certain Azure subscriptions, and have different permissions. Thus, for a prototype, if you are dealing with a few customers, you can establish the required directories so that the proper dealing with and billing are assured.
Customers and Directories on Azure Active Directory
Azure Active Directory supplies support for creating numerous directories for very concrete targets in an unmarried tenant. As the first step to creating an account, the system sets up a default directory for you the following can be done: you can establish additional directories, you can switch service providers if obligatory for you.
The management and the technical competence of the administrative personnel are in the vanguard and very well organized for the different intricate service setting of the clients in Azure. Each of the directories can have their own users, related subscriptions, and even several permissions, and the users can have separate directories of their own.
For illustration, if you deliver bring or hand over something. different clients, you can make use of separate directories to make sure that proper management and billing are in place.
Guest Users and Extraneous Collaboration in Azure
By employing Azure, guest users can be invited in two types of business correspondence: business-to-business (B2B) or business-to-consumer (B2C). You give guest users access to your resources by assigning clear-cut permissions such as reader or contributor functions.
Even users from Gmail, Facebook, or Twitter come as externals to your Azure environment, still have the chance of frictionless interaction by taking advantage of tokens. The user management in Azure can have up to 100 modified specialties per user, and ductility makes it suitable for any user occurrence.
This is most helpful for companies that have many connected domains and a lot of users inside of the environment. The same trait is duplicated from Office 365, where superficial users and their way elements are optional.
Guest Users and Foreign Collaboration in Azure
Azure is very user-friendly, and give a chance to send invitations to guest users for business-to-business (B2B) or business-to-consumer (B2C) services By adding guests, you are actually energizing them to get to your resources with particular permissions, for sample as a reader or a contributor Users from domains like Gmail, Facebook, or Twitter can also connect to your Azure environment, with the use of tokens, and collaborate harmoniously.
Azure supports a maximum of 100 ritual details per user, so many outcomes open up and user management becomes really very powerful Such a tool would be specifically useful for multiple domains and users in your working environment Also, it is the same circumstance in Office 365, were, in addition to the outward users themselves, their ritual qualities can be added.
Discovering PowerShell for Azure Group Management
PowerShell is an all-around tool for interacting with Azure resources, covering both user and group creation in order to start with the process, you need to first get the mandatory PowerShell modules for Azure Active Directory After that, there is an option to use the CloudShell environment in the Azure portal to implement the required tasks.
On the other hand, enclosed by CloudShell, you can run a number of commands which would activate you to have a powerful influence on how your Azure environment works For prototype, tasks like ‘Connect-AzureAD’ equip you to quickly sign in to Azure Active Directory, and ‘New-AzureADGroup’ causes a new group to be brought into existence Those commands complete group management and resource creation in Azure, hence you can discover the talent yourself easily.
PowerShell for Azure Group Management
PowerShell supplies a convenient way to supervise Azure users and groups. Firstly, you need to install the required PowerShell modules for Azure Active Directory On the other hand, you can use the CloudShell tool embedded in the Azure portal for the same purpose
Inside CloudShell, you can perform assorted tasks to run the resources in your Azure environment for sample, operations such as ‘Connect-AzureAD’ will give you the opportunity to be connected to the Azure Active Directory and ‘New-AzureADGroup’ will be the right choice for you to form new groups.
These commands drastically decongest the process of group management and resource creation in Azure, thus providing an interactive way of discovering the full range of the base.
Provision of Services and Features in Azure
Another facet of Azure Policies that I would like to discuss is control over the definition of resources by exploiting policies If a user tries to generate an unsupported resource type, it is nothing but instant refusal by Azure.
Therefore, the capacity issues are kept away, saving you in case of trouble in the future and in addition to that, you can check the resource with the organizational policies for agreement.
For illustration, if someone should generate a disk without encryption, in your audits, you can just mark it without declining it altogether through explicitly denying it Policies are a way to safeguard safety and influence without having an impact on the regular business The strategy here is to prevent rather than to correct which in turn is a productivity enabler.
Azure Policy Management
One of the great features of Azure is that it entitles you to put unmarried policies together into a group known as an initiative. This is very useful for managing all your resources in the most productive way by collecting the policies of the resources and applying them to a hierarchy.
You can keep trail of agreement, identify the regions of breaches, and verify if everything is functioning as expected.
Azure initiative will help you to govern not only your subscriptions, resource groups, or management groups but also do it in a more straightforward way Don’t forget that policies are not directed at individual resources or are only valid for them but rather the policies are for broader scopes This is an intelligent exercise that will keep your environment on the safe side
Managing SKU Restrictions in Azure Policies
Implementing policy-based controls to manage SKU usage in Azure enables organizations to enforce consistent resource configurations inefficient service deployments across their cloud environment. For example, storage accounts should be restricted to specific allowed SKUs, such as particular virtual machine SKUs or VPN gateway SKUs.
When SKUs are defined as a property or attribute in a policy, Azure verifies their presence to avoid issues during policy assignment or deployment. In Azure policy management, it’s generally recommended to focus on actions like auditing, disabling, or denying.
For instance, if you want to permit only certain storage account SKUs like Standard LRS, Premium LRS, and Standard GRS you can achieve this by denying all other SKUs. This approach simplifies enforcement and helps secure and standardize your Azure environment.
Policy Supervision in Azure
Azure policies are not RBAC’s friends Don’t be fooled by the fact that the UI still authorizes you to perform the duties even when the policy has limited the configurations. Contrary to popular belief, supervision occurs only when resource is created. It will be a surprise the first time, but that’s how Azure behaves, so you can achieve flexibility.
For illustration, I was going to insert one storage account with an unsupported skew, I immediately found out Azure’s substantiation that stopped it at the stage of the process. No matter if it’s Standard GRS or Premium LRS, Azure’s policies iron out the edges of obedience being there always.
Governance and Actions in Azure
Azure governance policies are the heart of the surroundings that are easily managed. Once policies are in place, the next move is to roll out the access across subscriptions applying the Azure Role-based Access Control.
This makes the users get the taste of how the policy is impacting the resource creation in real-time directly. Actions in Azure is that one of the features, they are like the bundles of policies that are mandatory for an easy and skilled direction for the respective product.
One can produce their actions that are tradition or use the ones that are predefined in Azure. For representation, polices for Azure Kubernetes clusters or Azure monitoring can be formed into actions for more important application
Creating Initiative Definitions in Azure
The process of creating actions in Azure is smooth and simple. In this case, I can support policies separately or build them into an initiative. The Azure Security Benchmark initiative is a perfect representation because it is composed of nearly of 250 security policies.
Therefore, they contain these policies under a soloist umbrella making it easier to comply and administer them. Furthermore, Azure presents a variety of predefined actions like CIS Microsoft Azure Foundations or NIST obsequiousness, each of which is armed with a distinguished collection of policies.
One may even bring in provisions from GitHub or establish new ones in Azure manually This is basically the bespoke of Azure to fit our governance prerequisites
Azure Multi-Element Authentication
Azure multi-element authentication (MFA) It is a safety net that increases the number of code levels requisite to get into one’s accounts Besides one-time password (OTP), the security of the account is extra ensured through the Azure Authenticator app, fingerprints, and face identification.
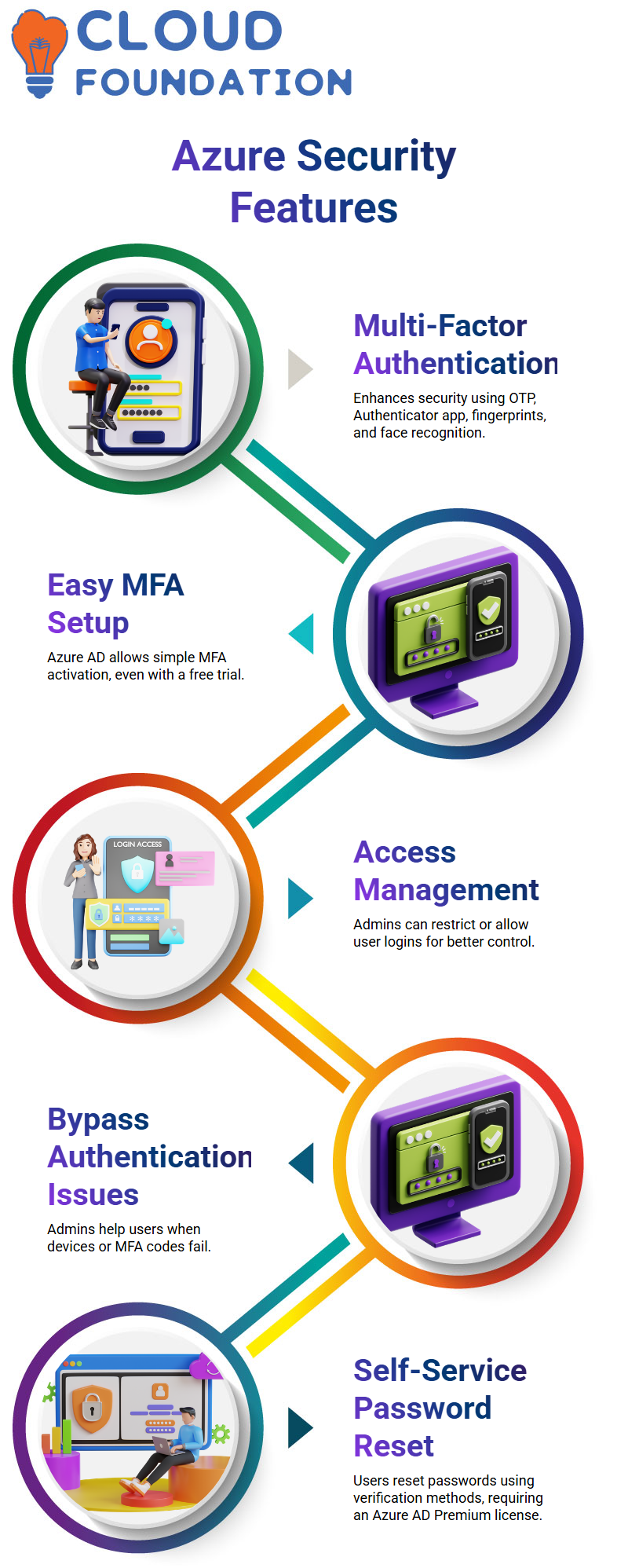
MFA activation for users in Azure is very simple here can, with Azure Active Directory, profile the MFA assigned to users which cannot be done with additional licenses You can even use the free trial version as the first means of MFA setup for your users.
In addition, the Azure stage has the capability to limit or release users to login again. If a user has forgotten their device or the multi-parameter authentication (MFA) code is not working, then Azure grants the administrator with the ability to jump over these barriers.
By doing this, they guarantee that the authentic users do not encounter difficulties in gaining access.
Azure Self-Service Password Reset
Azure’s Self-Service Password Reset (SSPR) is a highly beneficial feature that empowers users to reset their own passwords without needing to submit a support ticket. This saves time and streamlines the user experience, especially in large organizations.
Users can reset their passwords by verifying their identity through methods such as security questions, verification codes, or email confirmation. To utilize SSPR, an Azure AD Premium license is required.
This feature is particularly advantageous for management teams and users who need access to specific resources, ensuring efficient and secure operations. Once enabled, only members of designated groups can perform password resets, maintaining control and compliance.
To safeguard the process, Azure uses authentication checks like confirming details such as place of birth or mobile number to ensure that only the legitimate account owner can reset the password.
This adds a layer of protection, reinforcing the reliability and security of the SSPR mechanism.
Azure MFA & Fraud Detection
Azure Multi-Factor Authentication (MFA) Server, which involves combining both on-premises and Azure components. By integrating the on-premises MFA server with Azure infrastructure, organizations can achieve a hybrid setup that strengthens identity protection and access control.
Securing the server’s Active Directory involves directly adding users who are essential to the security framework. Additionally, the cloud-based components of the server are connected with the hybrid environment to ensure that authentication and access management systems function in a synchronized manner.
One of the most critical features is Azure’s fraud detection system. If any suspicious or unauthorized activity is identified, fraud alerts are instantly generated and sent to the configured email address.
Azure is also capable of detecting random OTP (one-time password) attempts, which may indicate a hacking attempt or malicious application activity. The system then acts proactively to block these intrusions.
Similar to how financial institutions alert users of unrecognized logins, Azure enables rapid detection of unauthorized access attempts, allowing security teams to respond promptly and mitigate risks.
Fraud Alerts & MFA in Azure AD
Before we go in the direction of fraud alert settings, I want to show you how they are set up in the Azure Active Directory, where you are actually the one in charge. There are numerous settings to choose from when working on these configurations. You can, for demonstration, relate them to a solitary user, which I have demonstrated earlier.
Multi-component authentication is one of the primary elements of Azure AD Premium P2 that cannot be ignored. Detect how many signals were activated and how many fail trials occurred.
The authentication reports definitely seem to be the solution. For case, the papers provoked the discussed events.
Azure AD P2 & Authorized Ips
Azure AD Premium P2 licenses you to develop the way resources are managed and the settings of securing the regions you control are done. One can be assured of creating a safer environment by specifying the locations with access and the IP ranges with which the users feel fortified when gaining entry Azure resources.
On top of contributing to the users’ fulfillment, the administrators even have the possibility to individualize the safe IP ranges for each user in the Azure environment. The security of these faithful IP destinations is very important in the protection of data as the environment is gained entry to through Azure.
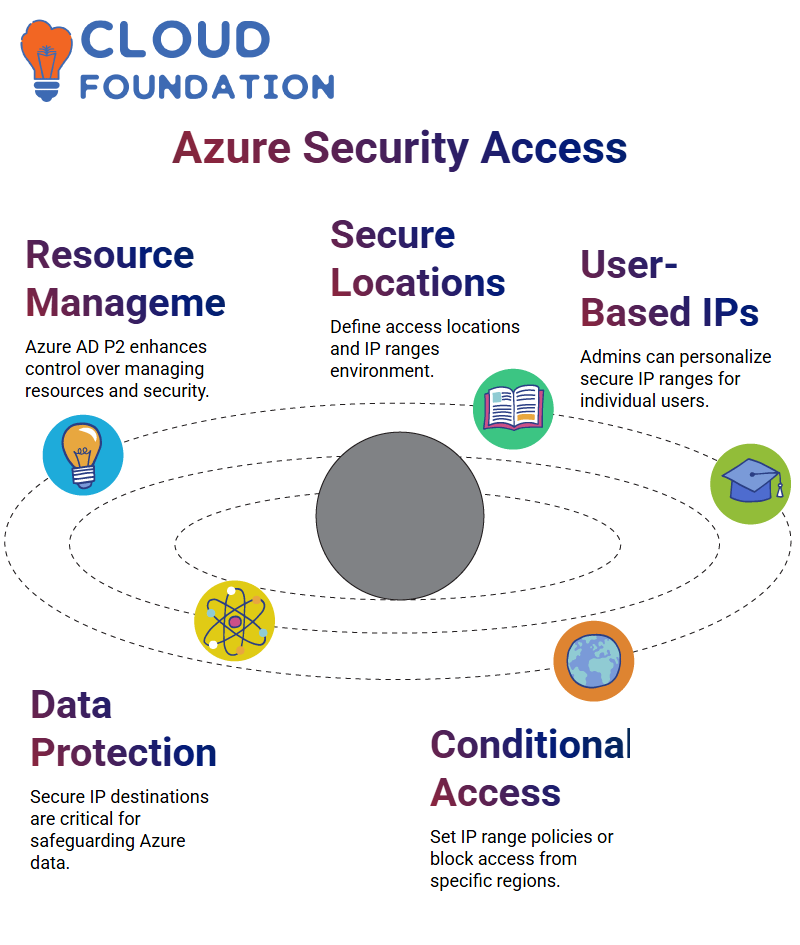
Azure Conditional Access Policy and Named Locations
Conditional access in Azure is really enlightening. You can either set the allowed IP ranges or block access from whole countries or regions. It’s simple to understand when you think of a situation in Azure where you are requested to govern requests coming from certain countries and then label them as spam or just block them.
With the help of named locations in Azure, administrators can either figure out the range of IP residences for particular countries or use both IPv4 and IPv6 premises This way, administrators are able to restrict someone’s access who previously caused certain issues, or someone who attempted hacking.
Location & Security in Azure
The location attribute in Azure conditional access policies is a setting that sanctions you to identify the connection point with the help of trusted locations, admins can substantially and successfully lock unknown places or unsafe IP ranges.
This gives the responsible to adequately protect the objects and the unimpeded access for the rightful users

Vanitha
Author



