What is SAP Security ?
Welcome to the SAP Security blog!
I will be helping you gain more knowledge on SAP Security and cover several relevant topics like sap security courses in this article.
Overview, Introduction to SAP Security
The SAP Security system comprises several individual parts. Of paramount importance in its structure lies system authorization – its most essential aspect being user responsibilities and rights within its hierarchy ,this ensures each person within is granted different degrees of access within it allowing the administrator to maintain optimal system safety practices through system authorization rules practices and processes.
SAP Security definition OR Define SAP Security
SAP Security refers to an Assortment of Tools and Procedures designed to monitor access rights on various system components as well as what activities each user may perform on them.
Any enterprise running SAP applications should prioritize SAP Security to protect their data, applications and resources.
Administrative and technical controls should be combined in order to prevent unauthorised access and usage of SAP data, software and computer resources, which must remain safe at both production and nonproduction settings.
What does SAP Security do and what is SAP Security used for?
SAP Security contains various capabilities designed to protect data, including encryption, authentication and integrity protection that help in keeping information private and safe from leakage or corruption.
Additionally, SAP Security features many security functions – data validation, scanning, and data authentication capabilities that can further increase data protection – that can further strengthen security measures on your systems.
What is SAP Security used for?
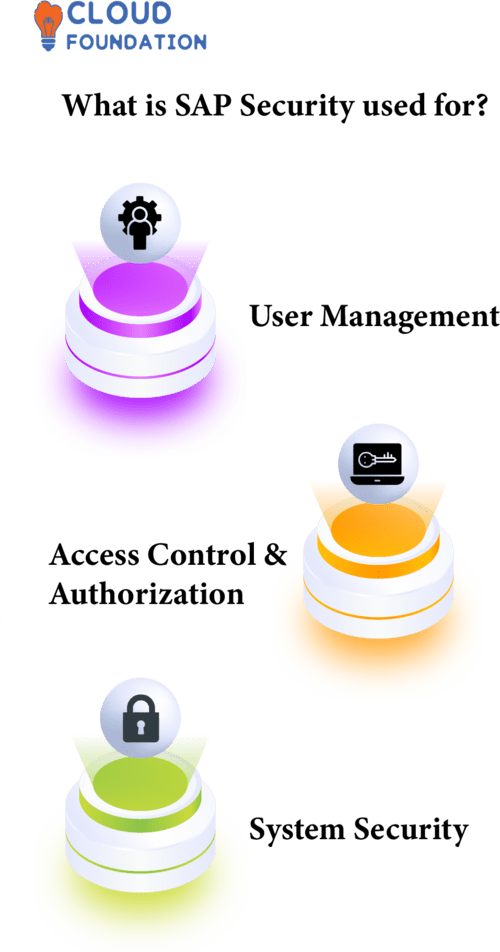
User Management: This involves setting up, controlling, and keeping track of user accounts to allow authenticated access to sensitive data through user credentials as well as controlling and restricting individual’s use of sensitive areas within the SAP system.
Access Control and Authorization: Two essential aspects of SAP security include access control and authorization. Establishing what users may and cannot do inside the system through approval, restricting user access to certain system components through access control ,this could include data, features or programs.
System Security: System security serves to safeguard systems and their data against harmful activity that might compromise them and their content. In doing so, intrusions from unknown parties, malicious assaults, data loss and theft must all be protected against by employing safeguards that ensure these measures are correctly set up and functioning as promised.
How does SAP security work?
 SAP Security works by authenticating users and giving them access to various applications and data. Authentication involves verifying an individual’s identity by having them log-in using username and password credentials; following that step, they may gain entry based on their authorization level to specific apps/data sets.
SAP Security works by authenticating users and giving them access to various applications and data. Authentication involves verifying an individual’s identity by having them log-in using username and password credentials; following that step, they may gain entry based on their authorization level to specific apps/data sets.
Role-based access control (RBAC) is one of the primary forms of authorization used in SAP Security, assigning users roles that have set of permissions associated with them that determine which applications and data a given user can access based on his/her role assignment.
This ensures that only needed data reports can be accessed, protecting sensitive material from unauthorised parties.
SAP Security plays an invaluable role in protecting data by helping to ward off attacks from malicious sources.
To achieve this goal, they employ authentication and encryption technologies that ensure only authorized users have access to applications, keeping unauthorised people away from sensitive files and applications.
In addition, SAP Security employs various defense mechanisms against attacks including firewalls and intrusion detection systems – an approach known as perimeter protection that makes using SAP more secure than ever.
Every SAP system must include SAP Security, so businesses need to implement an extensive security plan in place. Organisations can protect sensitive data while still giving authorized users access by employing authentication and authorization technologies.
Why SAP Security and what are the benefits of SAP Security?

SAP Security’s goal is to secure company resources against unauthorised access and manipulation. As one of the world’s premier enterprise resource planning (ERP) programs, SAP is widely known for offering strong yet secure solutions that protect client resources.
Through SAP Security’s wide capabilities and advanced features it helps organisations defend themselves from external threats such as criminal actors as well as accidental data loss.
Secure access is intended to give users safe access to apps and data while safeguarding it against unauthorised access, abuse or alteration.
Benefits of SAP Security
Improved User Experience: By providing users with safe environments to access apps and data, SAP Security helps organisations enhance user experiences.
Efficiency Gain: SAP Security can assist businesses by helping them access and manage data and applications more safely, streamlining workflow and shortening job completion times with its extensive capabilities and in-depth security features.
Lower expenses:It assists businesses in lowering expenses by providing secure access and management of data and applications, which helps businesses reduce expenses.
Advantages of SAP Security
Better Compliance: Businesses may achieve greater compliance with industry norms and laws with SAP Security’s help.
Access control and data security regulation exists across many sectors, and SAP Security assists companies in meeting them all while creating an IT environment which meets industry compliance.
Greater Visibility: SAP Security also gives enterprises better insight into their IT infrastructure, helping businesses gain better insight into user access and usage patterns as well as any possible security threats – lowering risks associated with data breaches while helping organizations maintain secure operations for data and applications.
Secure: SAP Security uses advanced encryption algorithms and authentication techniques to protect data against unauthorized access and hostile attacks, providing your information the maximum protection against unwanted access or intrusions.
Scalability: SAP Security can easily meet any company’s demands with its scalability feature, meeting any company of any size’s security needs with ease.
From protecting small to larger enterprises alike, and in any environment or circumstance imaginable – making it the optimal solution.
What is SAP security software and how to use SAP security?
Businesses often utilise SAP Security software as an effective defensive measure against risks including malware, data theft and other damaging acts.
It serves as a comprehensive set of technologies which protect networks and data security as well as shield organisations against outside threats; and prevent unauthorised access to vital business assets like valuable information or intellectual property.
Security software provides capabilities such as encryption, access control and user authentication to identify possible risks and take necessary measures in order to detect and prevent unauthorised access to data and networks.
In addition, network activity monitoring capabilities help keep an eye on network activity as well as identify abnormal behaviour quickly for intervention purposes.

SAP Security’s core characteristic lies in its ability to detect and react to harmful behaviour, from malware, spyware and other harmful software through behavioral analysis techniques used for unusual activities and investigations to identify risks such as phishing attacks or ransomware which it then takes steps against.
Additionally, this program offers strong security against unauthorised access. It may be used to monitor user behaviour as well as restrict network and data access.
Furthermore, certain user accounts or websites or programs could even be blocked due to this strong protection offered.
It also offers several data security capabilities that may help manage access, encrypt data, and protect it against unauthorised access.
How to Use SAP Security?
An Access Control List (ACL) is the starting point in creating SAP security; an ACL determines which users and at what levels have access to particular system regions, user roles may then be given accordingly, for instance one might receive “manager” permission with access only granted in accountspayable section while another user could gain “accountant” status and gain entry in accounts receivable section.

After configuring their ACL, users can be granted access to certain programs or resources using access control policies.
These policies specify which users or groups of users may access particular system sections – an individual might, for instance, be granted access to one database but not another – using access control policies as an authorization method.
Furthermore, access restrictions can restrict individual parts of a system such as financial data or client files using these policies.
Before users gain access to resources or programs, their identity must first be validated through authentication – usually accomplished using login/password credentials – then access is granted through authorization procedures.
Data encryption is another element of SAP security that should not be overlooked. By scrambling data, data is kept safe during network transmission – making sure only authorized users may decipher it later – this feature of data protection especially comes into its own when dealing with sensitive customer or financial records.
SAP Security Modules
SAP Identity Management– This module is responsible for authenticating users and assigning appropriate roles to them, managing accounts, passwords and authorization of users as well as making sure only authorized individuals gain entry to certain portions of the system with access rights granted accordingly.
SAP Access Control– This module ensures compliance with access control laws and regulations, such as who has access to which data. In addition, this component ensures all entries into and exits out of the system are recorded for monitoring purposes.
SAP Risk Management– This module assists in the identification and control of potential security risks by pinpointing weaknesses, analysingreports , their effects, and developing defenses against such dangers. Furthermore, this module assists with overseeing the creation and functioning of security measures, making sure they operate as intended.
SAP Authorization and Auditing– This module is responsible for assigning privileges and authorising users within an SAP system, granting only those areas in which access has been approved for them to access. Furthermore, system auditing ensures all accesses are tracked and recorded accordingly.
SAP Security Monitoring– This module assists in keeping an eye out for any unusual activity on the system and can detect attempted data modifications/deletions as well as unauthorised entry attempts into it.
SAP Security Logging– This module assists with documenting user access to the system and monitors that every access event occurs without authorization or without being tracked, watched and stopped as appropriate.
Components of SAP Security
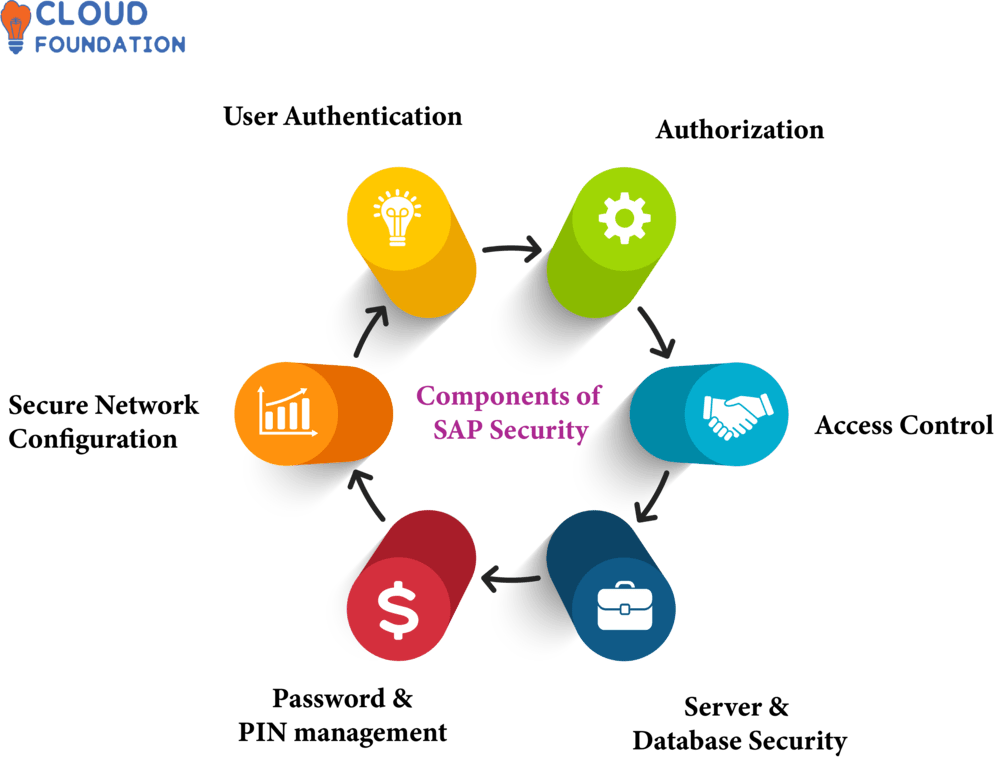
What Are the Best Ways to Learn SAP Security?
In order to truly comprehend SAP security, the ideal method would be team up with an experienced SAP expert who could offer practical guidance and mentorship.
Working closely with such a professional may equip you with all of the knowledge and insight into its concepts that is required in deploying and maintaining it correctly as well as further exploring what drives its ideas behind its foundations.
Learning SAP security through classes and books are effective strategies. Books offer in-depth examination of its components as well as instructions on how to set them up and administer them.
Learning SAP may seem daunting at first, but with proper support and resources it could prove worthwhile.
SAP Security Certification
As this certification verifies expertise required to protect SAP systems and applications and increase their usefulness, any firm must prioritize security to enable trusted decision-making processes.
As experts who possess SAP Certification can be such an asset to any organization, more and more employers require this credential for employees who participate in initiatives related to SAP.
Security experts recognize the inherent security concerns with using SAP applications, including data breaches, unapproved access and malware infections. Therefore, it’s vital to appreciate how important protecting them can be for businesses using them.

SAP can assist with this by offering its Security Certification which offers an in-depth knowledge of security-related challenges and the strategies necessary for their management.
After successfully passing certification examination, applicants become SAP Security Associates. An SAP Associate certificate covers all SAP application versions while Security Associate credentials may focus more on specific performance or products.
Security Associates possess qualifications necessary for many security-related positions, including SAP Security Administrator, Analyst Engineer and Architect roles.
Is SAP Security a Good Career Option?
SAP Security has become an increasingly sought-after career field within the computer sector, making an appearance of growing relevance among young individuals who wish to make a name for themselves.

With access control, identity and access management and user authorization capabilities all included as standard components of this comprehensive solution, this complete security solution ensures businesses remain protected from online dangers such as dangerous software installations, data losses or any unauthorised entry attempts.
CloudFoundation offers comprehensive SAP security training courses tailored for beginners as well as experienced experts alike, featuring best practice demonstrations.
You may find instructor-led live classes as well as both on-premises and online SAP security courses here.
I will be helping you gain more knowledge on SAP Security and cover several relevant topics like sap security courses in this article.
Overview, Introduction to SAP Security

The SAP Security system comprises several individual parts. Of paramount importance in its structure lies system authorization – its most essential aspect being user responsibilities and rights within its hierarchy ,this ensures each person within is granted different degrees of access within it allowing the administrator to maintain optimal system safety practices through system authorization rules practices and processes.
SAP Security definition OR Define SAP Security

SAP Security refers to an Assortment of Tools and Procedures designed to monitor access rights on various system components as well as what activities each user may perform on them.
Any enterprise running SAP applications should prioritize SAP Security to protect their data, applications and resources.
Administrative and technical controls should be combined in order to prevent unauthorised access and usage of SAP data, software and computer resources, which must remain safe at both production and nonproduction settings.
What does SAP Security do and what is SAP Security used for?
SAP Security contains various capabilities designed to protect data, including encryption, authentication and integrity protection that help in keeping information private and safe from leakage or corruption.

Additionally, SAP Security features many security functions – data validation, scanning, and data authentication capabilities that can further increase data protection – that can further strengthen security measures on your systems.
What is SAP Security used for?

User Management: This involves setting up, controlling, and keeping track of user accounts to allow authenticated access to sensitive data through user credentials as well as controlling and restricting individual’s use of sensitive areas within the SAP system.
Access Control and Authorization: Two essential aspects of SAP security include access control and authorization. Establishing what users may and cannot do inside the system through approval, restricting user access to certain system components through access control ,this could include data, features or programs.
System Security: System security serves to safeguard systems and their data against harmful activity that might compromise them and their content. In doing so, intrusions from unknown parties, malicious assaults, data loss and theft must all be protected against by employing safeguards that ensure these measures are correctly set up and functioning as promised.
How does SAP security work?
 SAP Security works by authenticating users and giving them access to various applications and data. Authentication involves verifying an individual’s identity by having them log-in using username and password credentials; following that step, they may gain entry based on their authorization level to specific apps/data sets.
SAP Security works by authenticating users and giving them access to various applications and data. Authentication involves verifying an individual’s identity by having them log-in using username and password credentials; following that step, they may gain entry based on their authorization level to specific apps/data sets.
Role-based access control (RBAC) is one of the primary forms of authorization used in SAP Security, assigning users roles that have set of permissions associated with them that determine which applications and data a given user can access based on his/her role assignment.
This ensures that only needed data reports can be accessed, protecting sensitive material from unauthorised parties.
SAP Security plays an invaluable role in protecting data by helping to ward off attacks from malicious sources.
To achieve this goal, they employ authentication and encryption technologies that ensure only authorized users have access to applications, keeping unauthorised people away from sensitive files and applications.
In addition, SAP Security employs various defense mechanisms against attacks including firewalls and intrusion detection systems – an approach known as perimeter protection that makes using SAP more secure than ever.
Every SAP system must include SAP Security, so businesses need to implement an extensive security plan in place. Organisations can protect sensitive data while still giving authorized users access by employing authentication and authorization technologies.
Why SAP Security and what are the benefits of SAP Security?

SAP Security’s goal is to secure company resources against unauthorised access and manipulation. As one of the world’s premier enterprise resource planning (ERP) programs, SAP is widely known for offering strong yet secure solutions that protect client resources.
Through SAP Security’s wide capabilities and advanced features it helps organisations defend themselves from external threats such as criminal actors as well as accidental data loss.
Secure access is intended to give users safe access to apps and data while safeguarding it against unauthorised access, abuse or alteration.
Benefits of SAP Security

Improved User Experience: By providing users with safe environments to access apps and data, SAP Security helps organisations enhance user experiences.
Efficiency Gain: SAP Security can assist businesses by helping them access and manage data and applications more safely, streamlining workflow and shortening job completion times with its extensive capabilities and in-depth security features.
Lower expenses:It assists businesses in lowering expenses by providing secure access and management of data and applications, which helps businesses reduce expenses.
Advantages of SAP Security

Better Compliance: Businesses may achieve greater compliance with industry norms and laws with SAP Security’s help.
Access control and data security regulation exists across many sectors, and SAP Security assists companies in meeting them all while creating an IT environment which meets industry compliance.
Greater Visibility: SAP Security also gives enterprises better insight into their IT infrastructure, helping businesses gain better insight into user access and usage patterns as well as any possible security threats – lowering risks associated with data breaches while helping organizations maintain secure operations for data and applications.
Secure: SAP Security uses advanced encryption algorithms and authentication techniques to protect data against unauthorized access and hostile attacks, providing your information the maximum protection against unwanted access or intrusions.
Scalability: SAP Security can easily meet any company’s demands with its scalability feature, meeting any company of any size’s security needs with ease.
From protecting small to larger enterprises alike, and in any environment or circumstance imaginable – making it the optimal solution.
What is SAP security software and how to use SAP security?
Businesses often utilise SAP Security software as an effective defensive measure against risks including malware, data theft and other damaging acts.

It serves as a comprehensive set of technologies which protect networks and data security as well as shield organisations against outside threats; and prevent unauthorised access to vital business assets like valuable information or intellectual property.
Security software provides capabilities such as encryption, access control and user authentication to identify possible risks and take necessary measures in order to detect and prevent unauthorised access to data and networks.
In addition, network activity monitoring capabilities help keep an eye on network activity as well as identify abnormal behaviour quickly for intervention purposes.

SAP Security’s core characteristic lies in its ability to detect and react to harmful behaviour, from malware, spyware and other harmful software through behavioral analysis techniques used for unusual activities and investigations to identify risks such as phishing attacks or ransomware which it then takes steps against.
Additionally, this program offers strong security against unauthorised access. It may be used to monitor user behaviour as well as restrict network and data access.
Furthermore, certain user accounts or websites or programs could even be blocked due to this strong protection offered.
It also offers several data security capabilities that may help manage access, encrypt data, and protect it against unauthorised access.
How to Use SAP Security?
An Access Control List (ACL) is the starting point in creating SAP security; an ACL determines which users and at what levels have access to particular system regions, user roles may then be given accordingly, for instance one might receive “manager” permission with access only granted in accountspayable section while another user could gain “accountant” status and gain entry in accounts receivable section.

After configuring their ACL, users can be granted access to certain programs or resources using access control policies.
These policies specify which users or groups of users may access particular system sections – an individual might, for instance, be granted access to one database but not another – using access control policies as an authorization method.
Furthermore, access restrictions can restrict individual parts of a system such as financial data or client files using these policies.
Before users gain access to resources or programs, their identity must first be validated through authentication – usually accomplished using login/password credentials – then access is granted through authorization procedures.
Data encryption is another element of SAP security that should not be overlooked. By scrambling data, data is kept safe during network transmission – making sure only authorized users may decipher it later – this feature of data protection especially comes into its own when dealing with sensitive customer or financial records.
SAP Security Modules

SAP Identity Management– This module is responsible for authenticating users and assigning appropriate roles to them, managing accounts, passwords and authorization of users as well as making sure only authorized individuals gain entry to certain portions of the system with access rights granted accordingly.
SAP Access Control– This module ensures compliance with access control laws and regulations, such as who has access to which data. In addition, this component ensures all entries into and exits out of the system are recorded for monitoring purposes.
SAP Risk Management– This module assists in the identification and control of potential security risks by pinpointing weaknesses, analysingreports , their effects, and developing defenses against such dangers. Furthermore, this module assists with overseeing the creation and functioning of security measures, making sure they operate as intended.
SAP Authorization and Auditing– This module is responsible for assigning privileges and authorising users within an SAP system, granting only those areas in which access has been approved for them to access. Furthermore, system auditing ensures all accesses are tracked and recorded accordingly.
SAP Security Monitoring– This module assists in keeping an eye out for any unusual activity on the system and can detect attempted data modifications/deletions as well as unauthorised entry attempts into it.
SAP Security Logging– This module assists with documenting user access to the system and monitors that every access event occurs without authorization or without being tracked, watched and stopped as appropriate.
Components of SAP Security

What Are the Best Ways to Learn SAP Security?
In order to truly comprehend SAP security, the ideal method would be team up with an experienced SAP expert who could offer practical guidance and mentorship.
Working closely with such a professional may equip you with all of the knowledge and insight into its concepts that is required in deploying and maintaining it correctly as well as further exploring what drives its ideas behind its foundations.
Learning SAP security through classes and books are effective strategies. Books offer in-depth examination of its components as well as instructions on how to set them up and administer them.
Learning SAP may seem daunting at first, but with proper support and resources it could prove worthwhile.
SAP Security Certification
As this certification verifies expertise required to protect SAP systems and applications and increase their usefulness, any firm must prioritize security to enable trusted decision-making processes.
As experts who possess SAP Certification can be such an asset to any organization, more and more employers require this credential for employees who participate in initiatives related to SAP.
Security experts recognize the inherent security concerns with using SAP applications, including data breaches, unapproved access and malware infections. Therefore, it’s vital to appreciate how important protecting them can be for businesses using them.

SAP can assist with this by offering its Security Certification which offers an in-depth knowledge of security-related challenges and the strategies necessary for their management.
After successfully passing certification examination, applicants become SAP Security Associates. An SAP Associate certificate covers all SAP application versions while Security Associate credentials may focus more on specific performance or products.
Security Associates possess qualifications necessary for many security-related positions, including SAP Security Administrator, Analyst Engineer and Architect roles.
Is SAP Security a Good Career Option?
SAP Security has become an increasingly sought-after career field within the computer sector, making an appearance of growing relevance among young individuals who wish to make a name for themselves.

With access control, identity and access management and user authorization capabilities all included as standard components of this comprehensive solution, this complete security solution ensures businesses remain protected from online dangers such as dangerous software installations, data losses or any unauthorised entry attempts.
CloudFoundation offers comprehensive SAP security training courses tailored for beginners as well as experienced experts alike, featuring best practice demonstrations.
You may find instructor-led live classes as well as both on-premises and online SAP security courses here.

Ankita
Author



