SailPoint Policy Management Training
Comprehension of SailPoint Policies
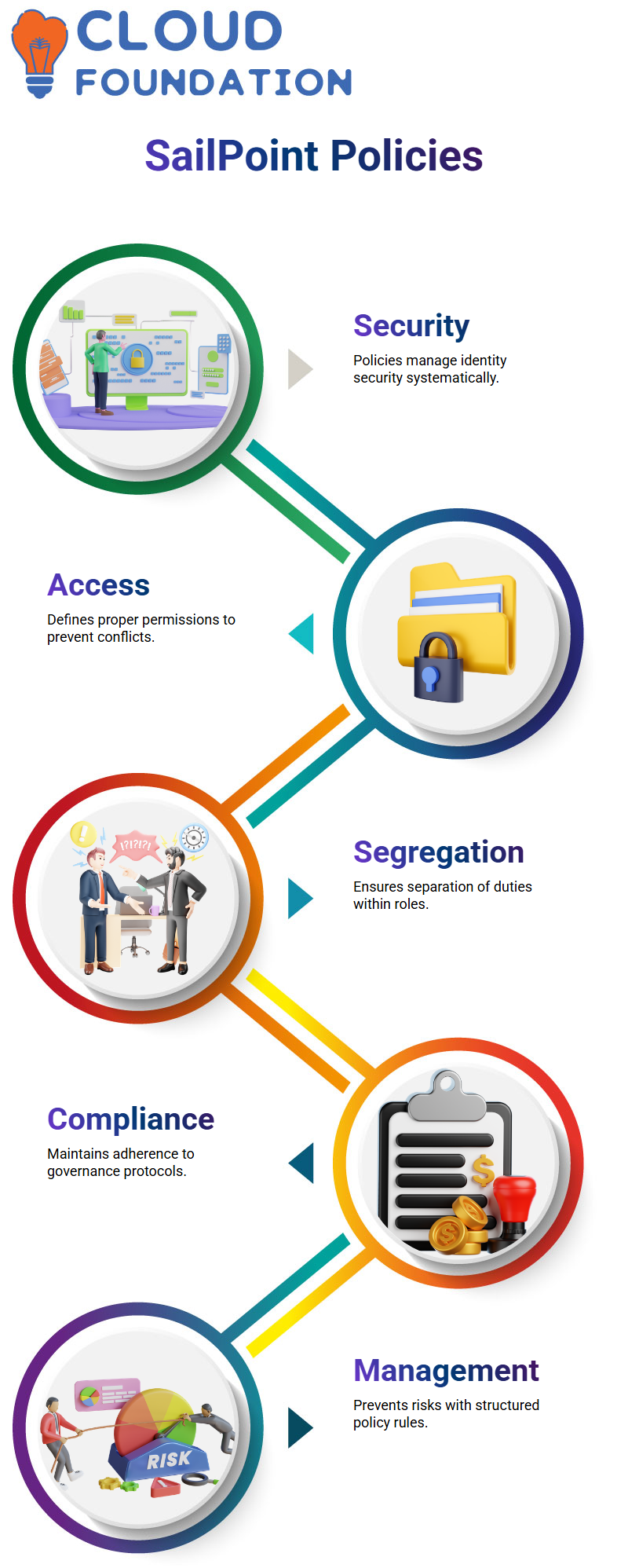
The main points of risk management and how to mitigate its impact. Now, we will examine SailPoint policies, which are the central components of managing identity security and access control in a systematic manner.
Policies set the ground rules for the attitude of the employees in the organisation. Assuming it involves security policies, access policies, or governance protocols.
SailPoint is the one that needs to implement them. Without unambiguous policies, organisations can hardly keep security and conformity in line.
In SailPoint, policies are primarily in place to ensure that employees have the proper access and to prevent conflicts of interest.
The same employee cannot serve in both roles, namely as a developer and a tester. Only policies can prevent such a situation.
By employing SailPoint, organisations can establish position- and permission-based policies to ensure that a strict segregation of duties is maintained. For example, if a staff member is assigned to the developer role, the software ensures that they cannot access the tester’s zone; therefore, the duties remain separate at all times.
Policy Management Essentials
Managing policies in SailPoint is a crucial aspect in ensuring compliance and preventing conflicts in access management. After outlining the guidelines, the first step is to outline the acceptance of the given permissions and restrictions.
Authorise me to explain how we make sure that our SailPoint policies are at least not abusive and have no violations.
Standard objects across every policy in SailPoint are designed to unify them all, with no friction or chaos. To forbid two or more similar accesses to the same user, we have the solution of mass policy rules. For example, when considering financial functions, the association of accounts payable and accounts receivable in one person is not only prohibited but also poses a high risk.
How to Produce Policies in SailPoint?
Now, let’s examine the steps to generate policies in SailPoint. Please proceed to the setup section, select “Policies,” and then click “New Policy.”
From there, you can formulate the policies, including the role they are based on and the entitlement policies.
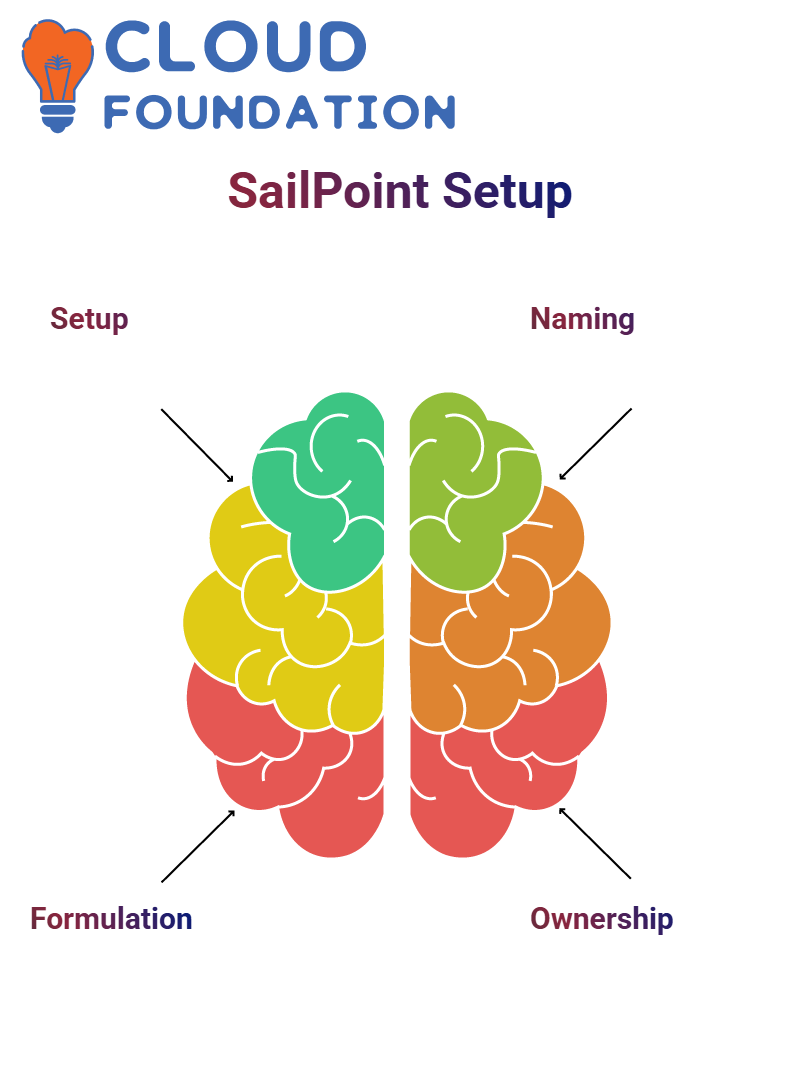
First and foremost, the name under which the policy should be known needs to be decided. A name like the ‘Accounts Policy’ would be very suitable for this purpose.
Secondly, the policy owner should be defined, who will be responsible for examining the violations and confirming the certifications.
SailPoint Access Policy in Identity Management
The primary objective of identity management is to determine the appropriate time and access level to grant to a person requesting access.
SailPoint will enable a company to establish rules that prohibit unauthorised entry to essential applications and data.
Role-Based Access Control (RBAC) is the method used by SailPoint to ensure that staff members are granted only those permissions that align with their daily job role.
It dramatically improves safety and transfers the benefits of IAM through the minimisation of the risk of multiple identities and the realisation of comply-at-work recommended practices.
Violation Management System
Through its product, SailPoint incorporates a comprehensive violation management system into its modules. When a staff member breaks a policy, messages and alerts can be configured to send reminders before the issue escalates.
The manager of the concerned department can also generate work items for himself or others.
One of the two alternatives, SailPoint’s default violation rules or made-to-order rules set by the organisation, can be used.
This not only maintains a high level of security but also gives the organisations the obligatory freedom in access management.
With SailPoint, if a policy violation occurs, an email is sent to the required people. The email text explicitly identifies the policy that has been violated and then outlines the necessary steps to resolve the issue. Moreover, SailPoint makes it easy for managers to respond quickly due to the transparency it provides.
SailPoint offers an additional feature of email generation that can be customised according to the user’s requirements.
This feature enables active subject lines that utilise placeholders, such as identity names, ensuring recipients are well-informed and receive straightforward communication.
Policy Violation Detection
Elucidating possible intra-job access struggles marks the inception of setting up SailPoint policies. We enforce our policies through the creation of well-described parts, such as accounts payable and accounts receivable, in our system.
Being on SailPoint, administrators may set rules for detecting unauthorised access. Additionally, the triggering of the policy violation notification by SailPoint can save you from the unauthorised request outcome, thereby ensuring security and policy conformity, thanks to the system.
This means that practically no safe action is taken by the system itself, the reports is transmitted almost unacceptably, analyst does not reflect on special reports such as industry events conceding attacks to be discovered thus without this insight and a script or some artificial intelligence agent the analyst is exposed to all of this unidentified attacks.
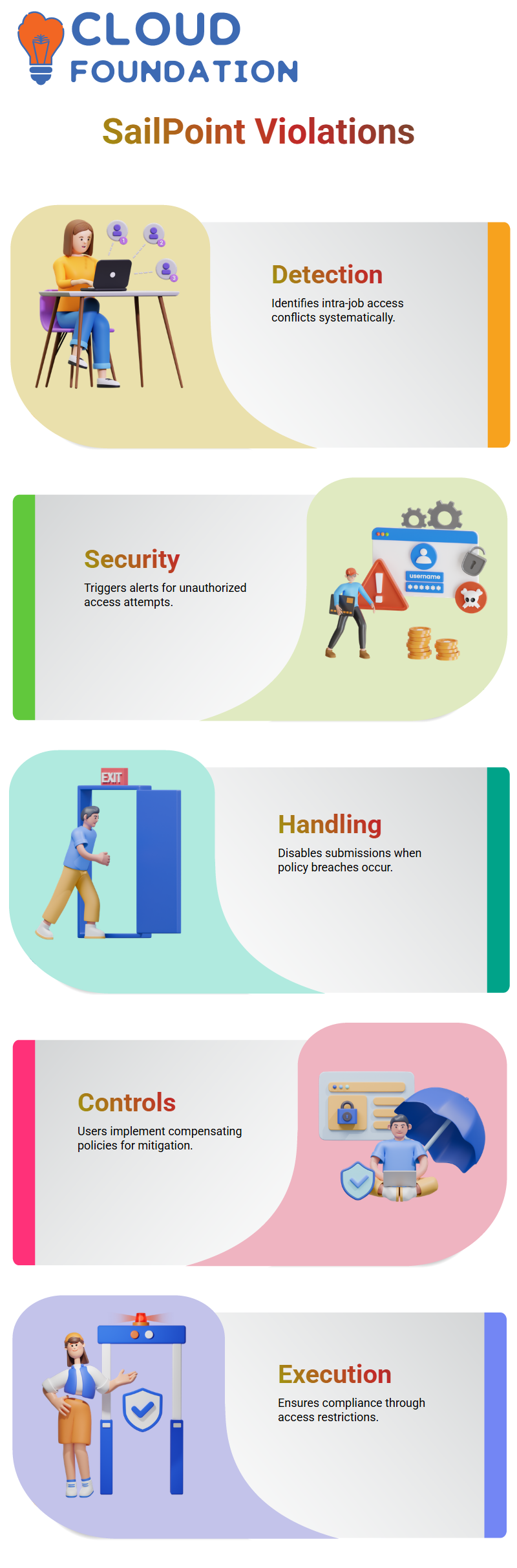
SailPoint Violation Handling
SailPoint implements a well-defined strategy for addressing policy violations. The submit button becomes disabled whenever a breach occurs, which requires users to either remove the conflicting access or implement compensating controls.
Users need to keep a circuit of any compensating controls that are found surrounding the SailPoint policies to grasp the mitigation policies.
If the means to minimise the conflicting jobs are not at hand, the person will have to eliminate one of them. This way, SailPoint policies will be executed, and the various modes will provide flexibility.
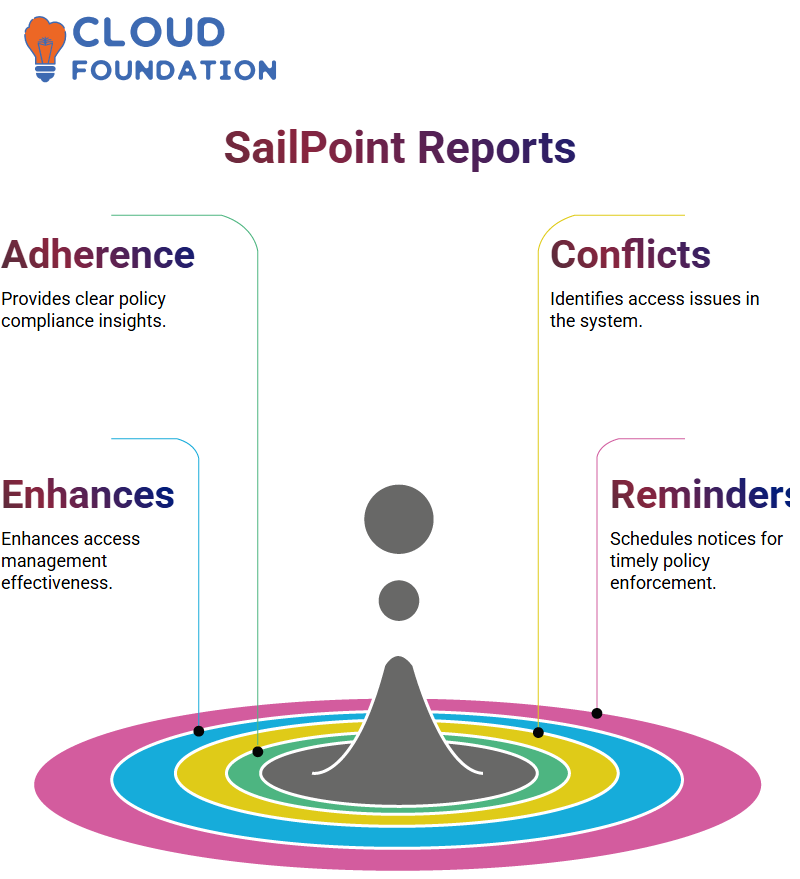
Policy Violation Reports
SailPoint, through its reports, provides a straightforward and clear view of policy adherence to those who manage the policies.
Administrators can initiate policy violation reports to gain an in-depth understanding of access conflicts throughout the system.
By comparing SailPoint’s reports, administrators can receive regular scans of multiple policy violations and respond accordingly.
By utilising SailPoint reports, businesses can establish effective access management processes, ensuring compliance and a robust security posture.
Setting Up First Reminders in SailPoint
Configuring the first reminder in SailPoint is not complicated. Initiating from two days to three days or more, you stipulate the period during which the notices can be delivered without delay.
With SailPoint, the proper subjects are made aware of reminders and policy application is carried out skillfully.
The other essential utility of SailPoint is escalation, which occurs when the first reminder does not have the expected effect. In this case, the sender has the option to escalate the notification.
In this way, those in charge or those with an uneven arrangement of their regular personnel are not surprised when they must act quickly.
Email Templates in SailPoint
One of the most critical operations of SailPoint is the ability to set up email templates that inform and remind users about pending tasks and alerts, while also raising the urgency of an issue by transmitting emails to higher-level management.
SailPoint enhances the process of routing reminders according to frequency—every 2 days, every 3 days, and so on —for the activities of different users.
SailPoint offers various template choices when selecting an email template. If none of the available templates fit what you’re looking for, a new one can be created that suits your process.
House Norm Email Templates with SailPoint
It may happen that the prearranged templates for SailPoint do not suffice, nonetheless.
In such examples, blueprinting a conventional email template is an option in SailPoint; this step ensures the consistent transmission of the intended message through the policy application.
Alternatively, you can conceptualise your email following SailPoint’s guidelines, which are two different methods with the same end.
In the case of SailPoint, the template does not begin with any facts, and sender data, subject lines, and email body content will be provided.
SailPoint will maintain the message consistency throughout the entire policy violation process once it is configured.
Escalation Workflows in SailPoint
When policy violations occur and have not been addressed, SailPoint can help with the escalation of workflows.
Consequently, implements the imperative steps to follow after reaching a particular stage, informs the owner/manager about the available solutions, or directly makes them the connoisseur of the breach.
One can take charge of escalation owners either manually or by specifying the rules for who is allowed to escalate in the event of an issue with SailPoint.
If no escalation owner is set, SailPoint has a mechanism that automatically assigns the following responsible individual.
SailPoint Signals
SailPoint streamlines the process of observance by automatically conveying out reminders and escalation emails. You can set up SailPoint instructions for the initial announcements, reminders, and escalation steps, ensuring each step is clear in the communication process.
The receiver becomes aware of policy violations through SailPoint, and appropriate action can be taken quickly to conform to the organisation.
Verifications with SailPoint simulations
SailPoint submissions simulations help identify variations before they escalate into a problem. Conformity simulation helps ensure that there is no conflict in the system due to identity differences.
Hence, the solution can be made instead of pointing out something when it is too late.
The realisation of a SailPoint policy demonstration is a drawback of the manual simulation process.
The administrators in charge of the simulation decide to reinstate the isolated policies. Even with these and other restrictions, SailPoint simulations remain an indispensable facility for controlling conformance and policy integrity.

Navya Chandrika
Author



