Prepare for Pega CSA system architect exam
The Pega CSA Life Cycle
Pega CSA plays a crucial role in real-world applications, which is why it must be highly responsible for maintaining lifecycle integrity.
The developers of Pega CSA are accountable for creating the application’s structure and ensuring that instances are mapped, stored, and retrieved correctly.
While creating designs, there is a central determinant: knowing the cycle prefix. This understanding is based on a prescribed method that guarantees not only productive user interaction but also a powerful sequence of events.
When we ponder an ordinary ordering system such as Amazon as an prototype You pick out the products you like, put them in your cart, state your address, pay for the items, and make a purchase.
This series is nothing but a life cycle The same way, Pega CSA applications use the primary and alternative life cycles to direct the procedure correctly.
This is the first point where users enter their location to ensure they receive the correct service. Additionally, the screen that asks users to fill in their address is also crucial for understanding the initial stage of the life cycle.
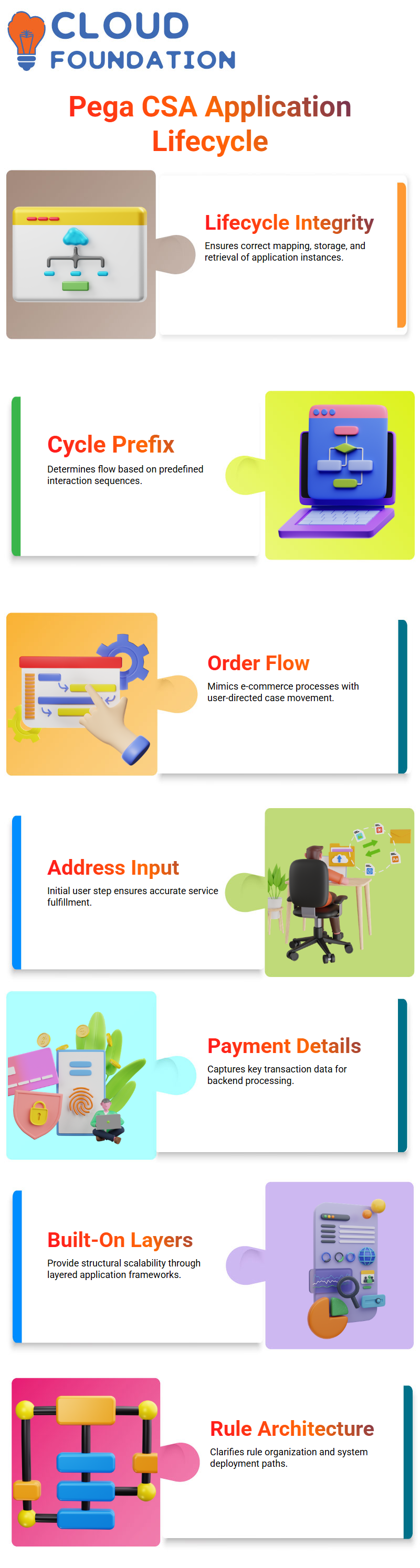
The proceeding stage is the payment gateway. Although Pega CSA cannot directly integrate with third-party payment systems, it is capable of collecting imperative payment details for final management.
Built-On Applications in Pega CSA
Built-in applications is crucial in Pega CSA. In every application, the top layer is composed of specific frameworks that ensure stability and scalability.
More developed UI kits utilise events that identify user experience views and shape the applications accordingly, as well as guide how to interact with customers and compose outcomes.
Developers invent software that uses these layers, which can be easily modified and adapted for compatibility with other systems.
To work comfortably with the Pega CSA forum, developers require a clear understanding of the application architecture. Knowledge about the appearance of rules, including their location, class formation, and initial integration capability, confirms the seamless deployment of applications.
So, the only step left now is to get into the sophisticated settings and perfection systems once we have discussed the life cycles, case steps, and the built-on applications of Pega CSA.
What types of activities are in Pega CSA?
Pega CSA presents the application of various types of activities, which differ in their execution context.
Utility activities are launched from a flow, while on-change activities respond to rule shifts made in specific locations.
Understanding these differences is of great value for managing augmented systems and introducing organised business processes.
Data in Pega CSA
By making use of the OBJBRO in Pega CSA, you have the freedom to filter the data that you fetch out of the database.
This consists of those columns you want specifically eg if it is employee name, salary, or any other field Filtering conditions such as ‘greater than’ or ‘equal to’ provide data with extreme rigor.
If we interpret filtering conditions correctly, we are capturing only exact news that has an impact on enhancing the capability of data operations.
Pega CSA is very unyielding when it comes to ways to minimise the noise and extract gems from the big data.
How to Optimise Pega CSA Workflows?
Refining parameter management in Pega CSA can be achieved by following a data model-based process which helps in the organization and managing.
The data Property Set usage has the opportunity to verify the cleaner interaction between activities also, it can be possible to derive step page from classes of a lower abstraction and managing data without difficulty.
Pega CSA professionals need to ensure that the names of the parameters are consistent with the application’s requirements.
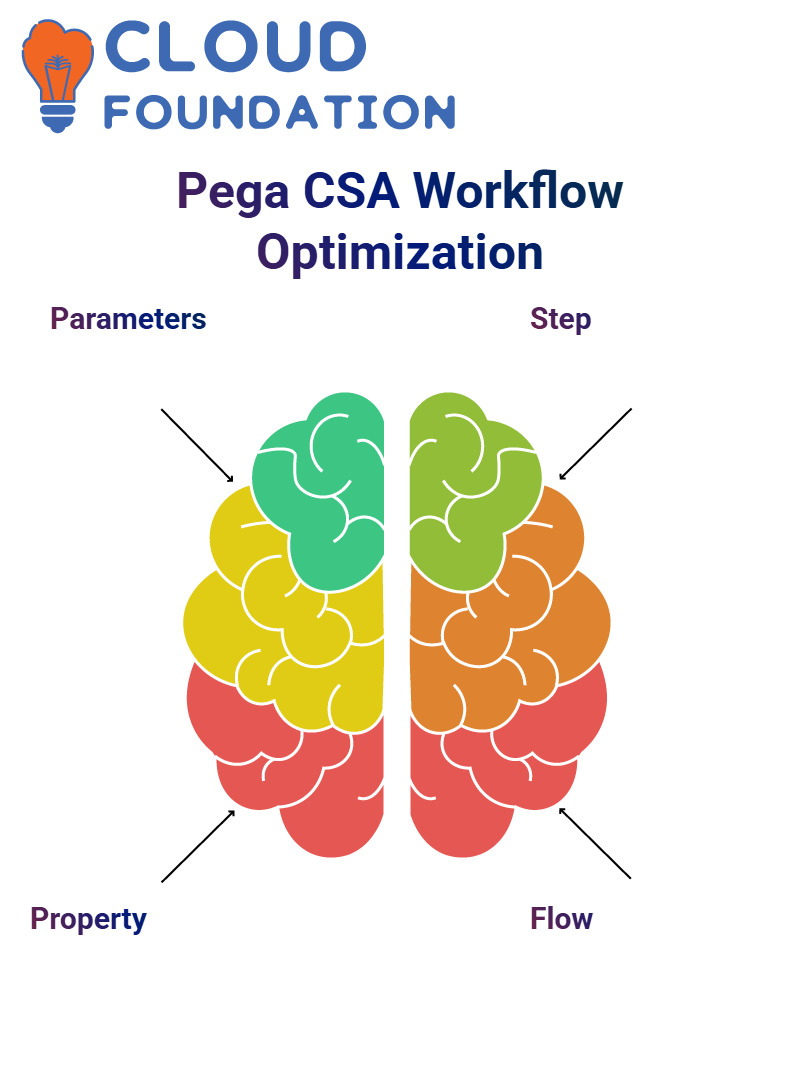 The continuity of data flow not only improves the expediency of the procedure but also refines the debugging process.
The continuity of data flow not only improves the expediency of the procedure but also refines the debugging process.
Introduction of OBJ Browse in Pega CSA
Pega CSA is used to retrieve the records of a case from a particular performer. Select and specify the properties of the register, such as case ID, and run the process.
Pega CSA will quickly retrieve the records and then store them appropriately.
A distinctively relevant point is that even though you may be asking for 10, Pega CSA will return the number of records available in that class only.
For example, if there are only seven records, then the corresponding number will be returned.
Pega CSA OBJ Browse
One imperative skill in Pega CSA is managing multiple records productively. To switch between various records or fetch one or more documents from the database, you use OBJ Browse.
OBJ Browse is the operation that retrieves many records, thus ensuring smooth data management.
Moreover, the OBJ Browse method parameters are the base name, a page list for the multiple records, and the class, which sets the source table.
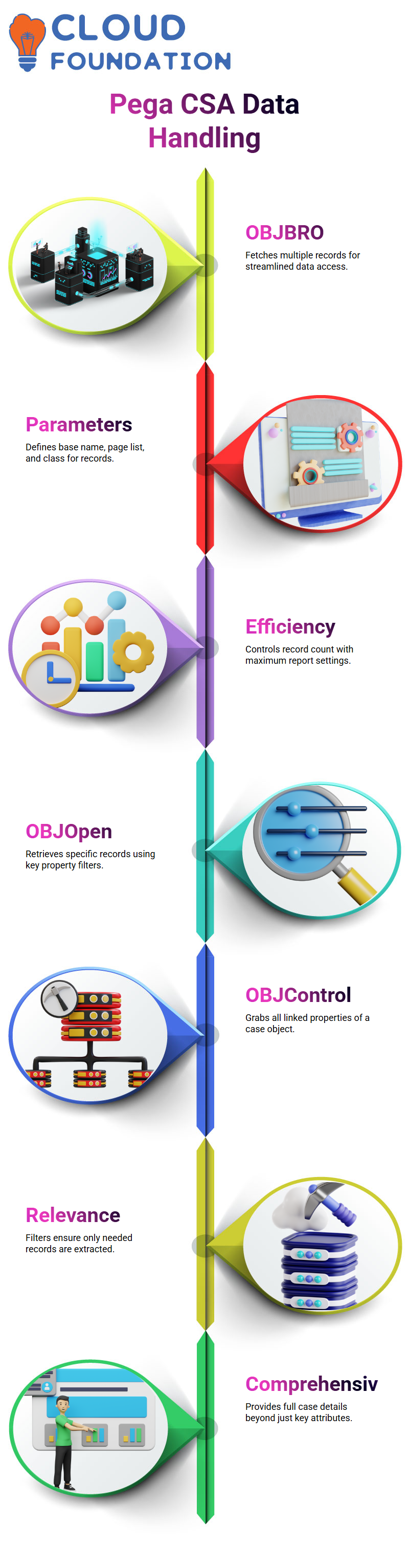
The maximum report setting allows you to specify the number of records you want to retrieve, making the process more efficient.
OBJ Open by Control in Pega CSA
One of the primary elements of Pega CSA is OBJ Open, and OBJ Open by Deal with is another. OBJ allows us to extract specific records from the database that are identified by key properties, ensuring that only the relevant reports are obtained.
Whereas OBJ Open by Control advances to the next level by bringing all properties connected to the subject in Pega CSA, this is an improved choice for us when we require a comprehensive view of a case, rather than just the object’s features.
Locks in Pega CSA
Locking in Pega CSA helps prevent data conflicts that can occur when multiple users share the same account.
According to the details, if one user holds a lock on an entry, another user cannot update it until the lock is released.
Knowledge of lock serviceability ensures that operations on records are performed error-free and that no overwrites occur.
This way, errors in a multi-user environment are reduced and conformity is maintained.
The Role of Pega CSA Log Locking
The biggest problem when working with Pega CSA is file locking. This situation occurs when two operators attempt to modify the same file.
The first operator has closed the log; therefore, the second operator is restricted from making any alterations.
To remove this restriction, the first operator must commit or release the lock; otherwise, the second operator will be unable to access the document and will encounter errors.
As Pega CSA practitioners, we should devise effective ways to manage such situations.
Triggering Activities in Pega CSA
The triggering of an activity in Pega CSA can be done through many alternatives. A standard method is to click a button in the user interface, triggering an action upon interaction.
Setting the apt properties before executing an activity ensures that all necessary values are available.
One alternative is to guarantee that activities are recognised within the confines of workflows by naming them directly.
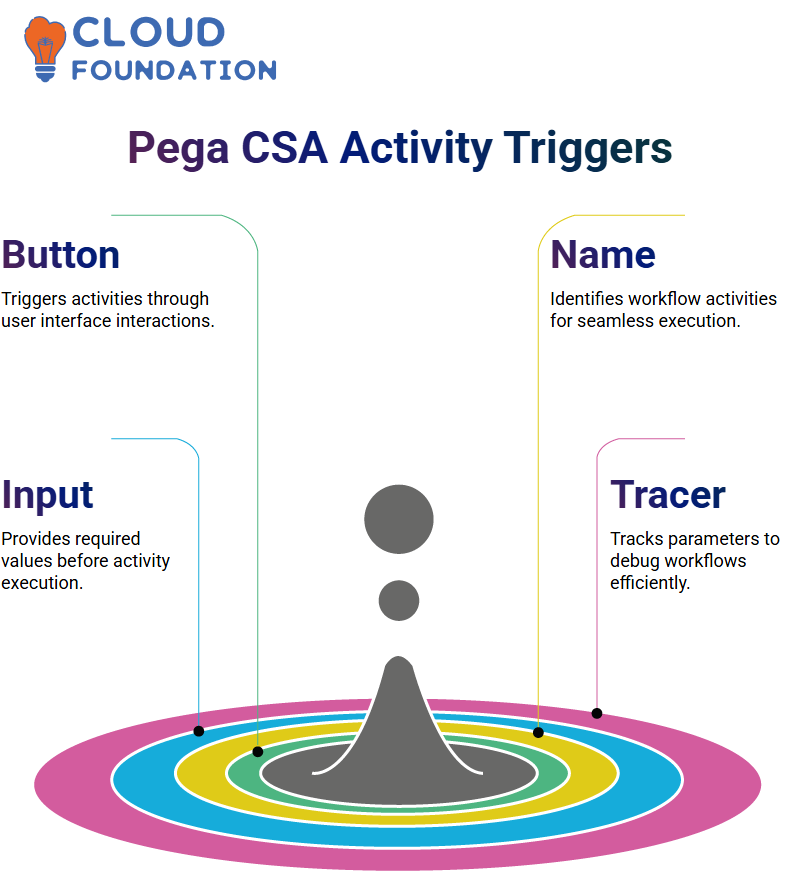
Cognisance of activity dependencies and parameter conditions enables developers to construct efficient workflows that not only eliminate errors but also provide optimal performance.
Pega CSA Parameters
When you are dealing with Pega CSA, the competent management of the parameters is very vital Parameters exercise a role of the middle man, so an activity can easily be carried out If an activity takes an input parameter it should be described before calling the activity.
Also, output parameters provide the updated facts that can be used in extended activities. Suppose a parameter is a Pega CSA one that does not appear on the clipboard by default. In that case, you must use the tracer tool to see it.
By utilising the tracer tool, the flow of parameters, including the one at fault, can be traced across multiple steps to pinpoint errors, making debugging and authentication a less strenuous process when working with complex workflows.
The Pega CSA tasks can be initiated in several ways, such as by clicking a button or through direct invocations.
Among the top processes is the registration of properties via the property set aspect, as this is done initially to activate the calling and is liable to require data for the operation to be carried out in full.
Step pages are key for updating the data in Pega CSA. Some best-case contingencies can be utilised in the case of an abstract class, e.g., a developer may decide to control data by adhering to a specific naming pattern that is unambiguous in parameter passing and retrieval.
Security and Authentication in Pega CSA
Pega CSA also offers robust security options, including external verification and password management for staff.
Operators are the ones who can decide the authentication type for safer access to the applications.
Furthermore, Pega CSA encompasses robotic automation, which involves delegating simple task execution to bots, ensuring that process automation is not weakened but rather strengthened by their participation.
Pega CSA Authentication
Authentication is a noteworthy aspect of workflows in Pega CSA. The questions asked in interviews are usually based on how the parameters are presented and followed in the activities.
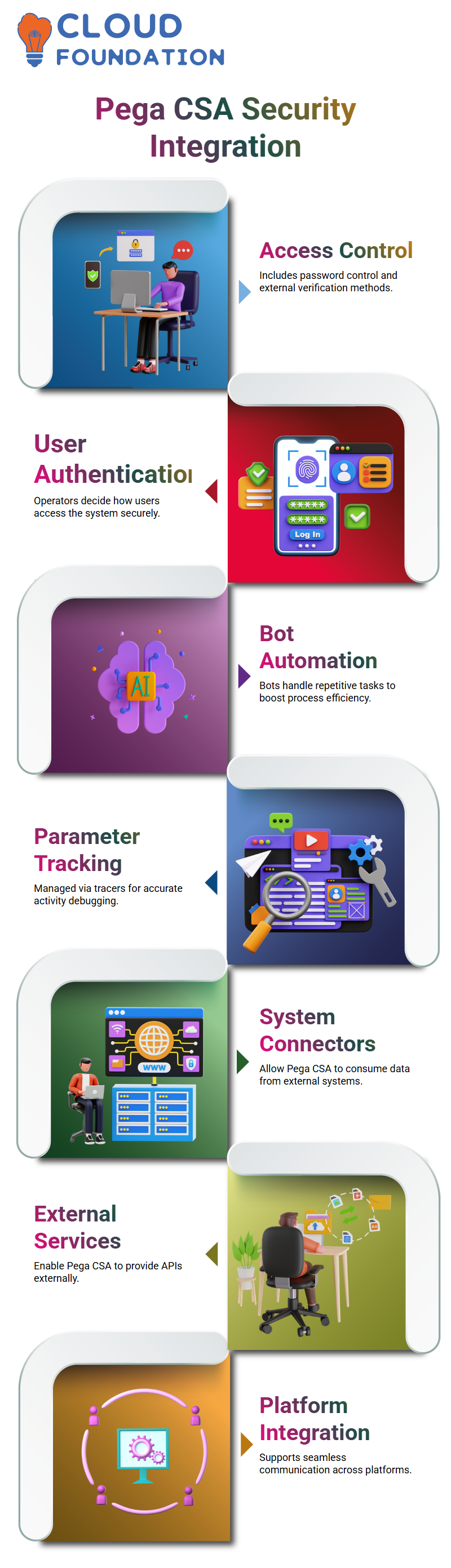
Since the parameters are not directly linked to the clipboard, it is imperative to use tracers and structured debugging methods.
Pega CSA Integration
When it comes to Pega CSA, integration can be split into two main divisions—Connectors and Services.
Through the use of connectors, we link to other systems to get data, which is an act of Pega CSA as a consumer.
At the same time, Services facilitate Pega CSA to act as a service provider itself, thus opening APIs for external systems to connect with our application.
To model flawless workflows in Pega CSA, it is essential to be aware of implementation systems that facilitate data exchange and communication between platforms.
Deploying Integration in Pega CSA
According to the Pega CSA, integration is a critical issue, as it presents the ability to connect with the Recreation API, SQL API, and SAP API.
Furthermore, Pega CSA can be linked to other systems through these connectors, which facilitate data manipulation.
The security settings in Pega CSA authenticate access to surface services, and error-elimination devices ensure the establishment of stable connectivity between applications.
Managing Integrations in Pega CSA
Establishing links between outer systems and Pega CSA means having an productive fault mitigation system.
If something goes wrong with an integration, we recognize certain situations as the ones which indicate the success of an operation.
If the response of the API does not indicate the expected status, we then control the flow of the process differently.
The Pega Certified System Architect (Pega CSA) certification can help a layperson developer gain a more informed perspective on their career.
It could pave the way for a high-flying artistic pursuit in the IT industry.
Pega CSA Operator Integration
Operator integration in Pega CSA is the process that defines user access and system authentication.
Those with operator IDs authorise us to manage permissions, conduct application usability testing, and compile our reports.
Members of the Pega CSA niche come from various teams, including claims processors, finance, HR, and many others.
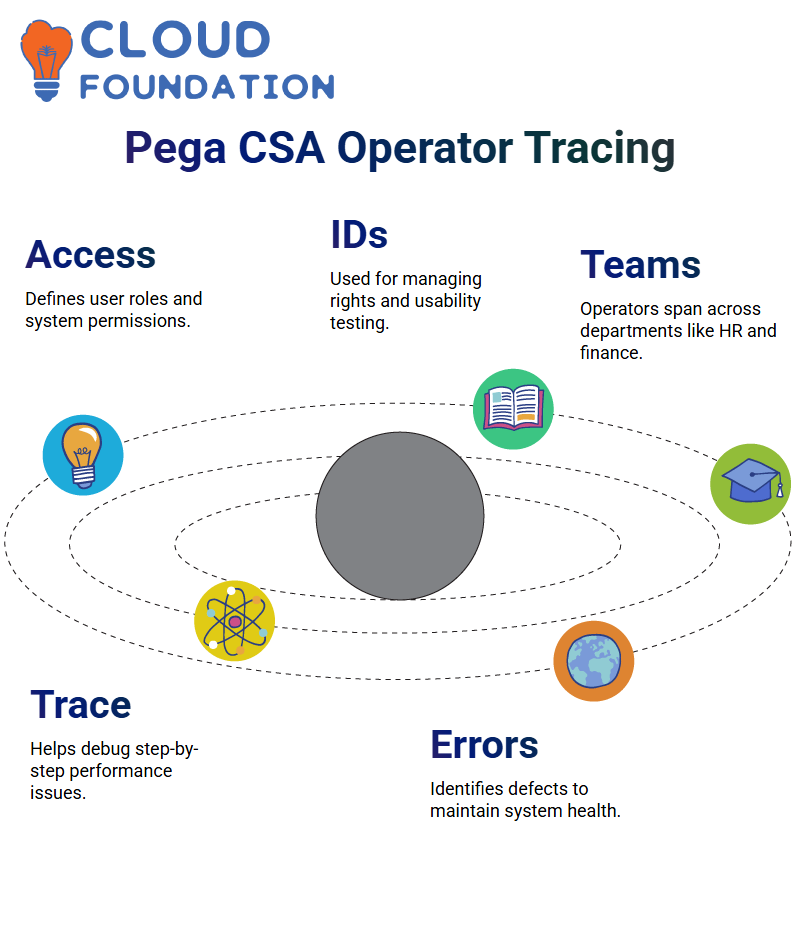 It is essential to ensure smooth operations and structured workflows, with the corresponding capacities being assigned.
It is essential to ensure smooth operations and structured workflows, with the corresponding capacities being assigned.
Troubleshooting: Employing Tracing in Pega CSA
By performing the tracing attribute, users can go further in the debugging process.
We can even trace one step at a time and simultaneously assess the implementation’s performance to identify bottlenecks and boost productivity.
Tracing in Pega CSA is the sure way to reveal all operational defects and thus ensure the system is in good condition.

Vinitha Indhukuri
Author



