PingOne Integration Training Tutorial
PingOne Setting Up SMTP Services in SAR
To begin, log in to the SAR mail system and navigate to the tab. From there, access your account and extend your trial if needed. Once complete, head to the inbox to verify test emails.
SAR provides multiple ways to connect with your organisation’s SMTP service:
1. Using Your Organisation’s SMTP Server
Navigate to the Domains section.
Add your organisational email domain.
Configure SAR to send emails directly from this domain.
2. Configuring the Sender Section
Edit details one by one, such as the domain and credentials.
The SMTP server will still be pinged, but the email will appear to come from your organisation’s official address.
3. Testing the SMTP Setup
Copy and paste your credentials (e.g., Gmail username and password).
Send a test email and verify delivery in your inbox.
If successful, MFA (Multi-Factor Authentication) can be enabled using the configured account.
If SAR blocks free services, you can generate OTPs through MailOSAR to complete the authentication process.
Expanding Beyond Email: SMS and Voice Integration in PingOne
SMTP isn’t limited to just emails. SAR also supports SMS and voice call notifications.
Organisations can integrate services like Tivoli or other internal communication tools, extending authentication beyond email.
Streamlining Authentication: PingOne with Google & Yahoo in Salesforce”
In the ever-evolving landscape of web applications, ensuring seamless and secure user authentication is a must.
Recently, we’ve successfully configured Google’s Gmail account as an identity provider (IdP) for a Salesforce application, and now it’s time to test it out.
The steps involved in setting up Google and Yahoo as identity providers, linking them with Salesforce, and introducing multi-factor authentication (MFA) to strengthen security.
Along the way, we’ll also touch on some advanced identity management techniques, such as password less and progressive profiling authentication.
Step 1: Setting Up Google as an Identity Provider
A Gmail account is an identity provider for our application. After enabling the IdP and logging into the Single Sign-On (SSO) portal, we went to the Authentication and Policies Configuration section and created a new login policy.
Once the login policy was in place, we edited it to include the Google IdP.
At this stage, we added Google to the list of authentication providers and configured the necessary settings. With everything set up, we proceeded to test the login flow.
Step 2: Linking the Google Account to Salesforce
The next phase was to access Salesforce using the Google account we had just configured. When attempting to log in, we encountered a prompt asking to link the Google account to the Salesforce user.
This step is required only the first time, as linking the accounts enables seamless future access.
After successfully linking the accounts, we were asked to enter the Google password. This first password is temporary and valid for the initial login.
Once we changed the password, that password would be used for subsequent logins.
Upon logging in again, the system prompted us for multi-factor authentication (MFA), adding an extra layer of security to the login process.
This is where the experience becomes more secure, ensuring that users are verified with more than just a password.
Step 3: Handling Yahoo Accounts with Google Credentials
For users who have Yahoo accounts, there’s a slight variation in the process. After linking the Google account to Salesforce, we attempted to log in to a Yahoo account.
Here, instead of a new password, we used the Google password for access.
However, since we’re authenticating with Google, we couldn’t simply log in with the system’s default credentials.
To resolve this, we had to go back to the external identity providers section and adjust the settings for Yahoo.
Step 4: Enabling the Yahoo Identity Provider
We added Yahoo as an additional identity provider. This involved navigating to Yahoo’s developer tools to obtain a client ID and secret.
We used this information to configure the integration in the Salesforce application.
Once the application was updated with Yahoo’s credentials, we ensured the identity provider was enabled in the settings.
After saving these changes, we tested logging into Salesforce again, now with the ability to authenticate via both Google and Yahoo accounts.
Step 5: Advanced Authentication Policies
When configuring external IdPs, such as Google and Yahoo, advanced authentication policies can enhance both security and the user experience.
These include the identifier first policy and password less authentication.
Step 6: Integrating MFA for Extra Security
To further enhance security, we have enabled multi-factor authentication (MFA) within our policies. The system now requires MFA to authenticate users, adding a layer of verification beyond just a password.
This is especially important in scenarios where password less authentication is enabled, as MFA ensures that even without a password, the user’s identity is verified through secondary methods (e.g., an OTP or biometric scan).
This step was crucial in ensuring the integrity of the authentication process.
PingOne Identifier First Policy
The identifier first policy prioritises identifying the user based on their domain before triggering authentication. This is especially useful for external IdPs, such as Google or Yahoo, but is not necessary for internal applications.
It’s essential to note that this policy determines which identity provider to use based on the user’s email domain.
For internal users, there’s no need for this policy since the system uses a default authentication method for employees.
External consumers, however, will be directed to Google or Yahoo based on their domain.
Password less Authentication in PingOne
A password less authentication policy streamlines the login process by eliminating the need for traditional username and password fields. Instead, users are directed straight to MFA.
This reduces the friction in the authentication flow while maintaining security via multifactor verification.
PingOne Promptive Authentication
Another option we explored is promptive authentication, which enables users to authenticate without providing a password.
After successful registration, users can authenticate themselves through additional attributes, such as their email address or mobile number.
This approach ensures a streamlined registration and login process, and the system can prompt users to provide these details when needed.
Customising User Experience with PingOne
Beyond SMTP, PingOne offers extensive customisation for login experiences, application portals, and self-service management. Here’s how:
1. Branding and Themes
Add logos, symbols, or create entirely new themes.
Customise login, registration, and error pages with organisation-specific designs.
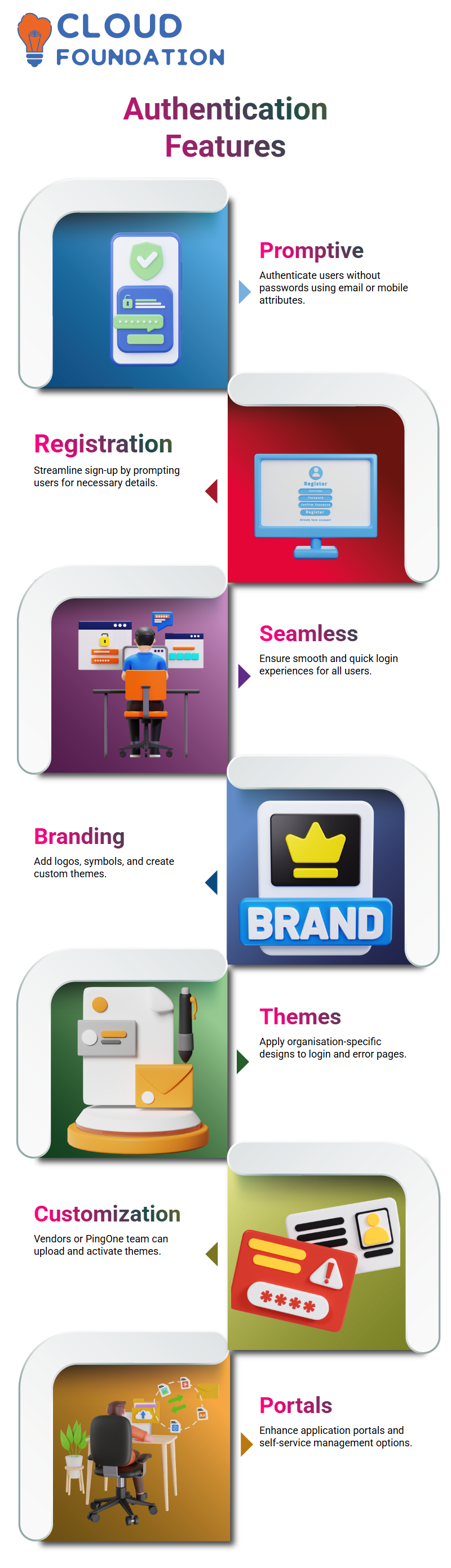
Vendors or the PingOne team can upload and activate themes on your behalf.
2. Application Portal Management
Access configured apps like Salesforce (SP1, SP2, SP3, etc.) via the portal.
Drag and drop favourites for easier navigation.
Choose which applications appear by enabling or disabling the “access” option.
This makes it easier for users to navigate dozens of applications while keeping the portal clean.
3. Self-Service Portal
The self-service portal empowers end-users to:
Manage profiles and MFA devices.
Enable/disable session information.
Review and accept consent agreements.
Admins can also configure email notifications (e.g., password resets, OTPs, device pairing), ensuring they align with organisational requirements.
Troubleshooting MFA Integration in PingOne
While testing the MFA integration, we ran into a few hurdles. Initially, MFA wasn’t being triggered as expected.
We unselected the MFA feature and added a password less option to resolve this issue. After saving the changes, the system successfully redirected users to the MFA step as intended.
The troubleshooting process involved verifying that the MFA device was correctly linked to the user’s account and that the correct sequence of authentication policies was applied.

Vinitha Indhukuri
Author



