PingOne Administration Guide
Setting Up and Managing Ping One
When implementing modern identity and access management (IAM) solutions, PingOne offers a robust platform for creating secure, scalable, and customizable authentication environments.
This guide walks through the setup process, the role of administrator environments, and how to configure users, groups, authentication methods, and integrations with external tools.
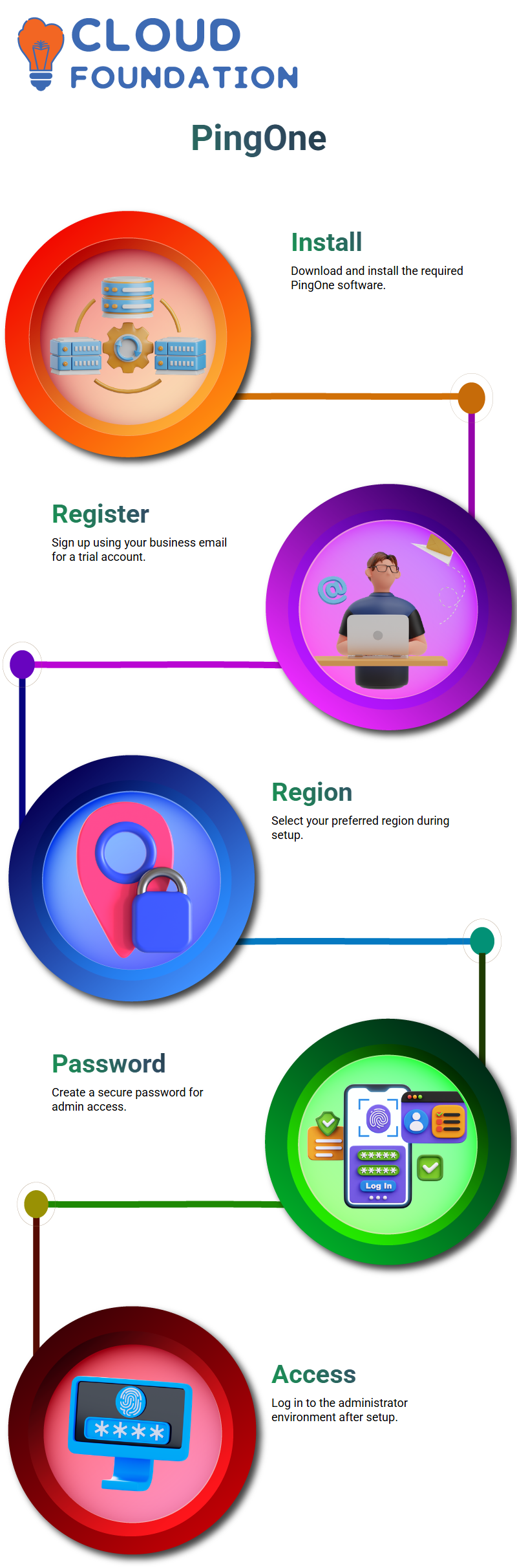
PingOne Setup Steps
Download and Install Software
Begin by downloading the required software (sometimes referred to as “Pink Fairy” in training guides). Once installed, you’ll be prompted to create an administrator environment.
Register and Trial Setup
Provide a business email address for login.
Register for a 30-day trial (extendable to 120 days).
Choose a region such as North America or another location of your preference.
Create Login Credentials
Define a secure password.
Use this password to log into your administrator environment.
PingOne Quick Start & Configuration
Ping One lets you build multiple environments tailored to different stages of your deployment:
Administrator Environment – The foundation for managing organisational settings.
Development, Stage, and Production – Flexible options for testing and scaling.
Application-Specific Environments – Each application can run in its own isolated environment.
When choosing services, you can integrate PingOne MFA, PingID, or other external providers for authentication.
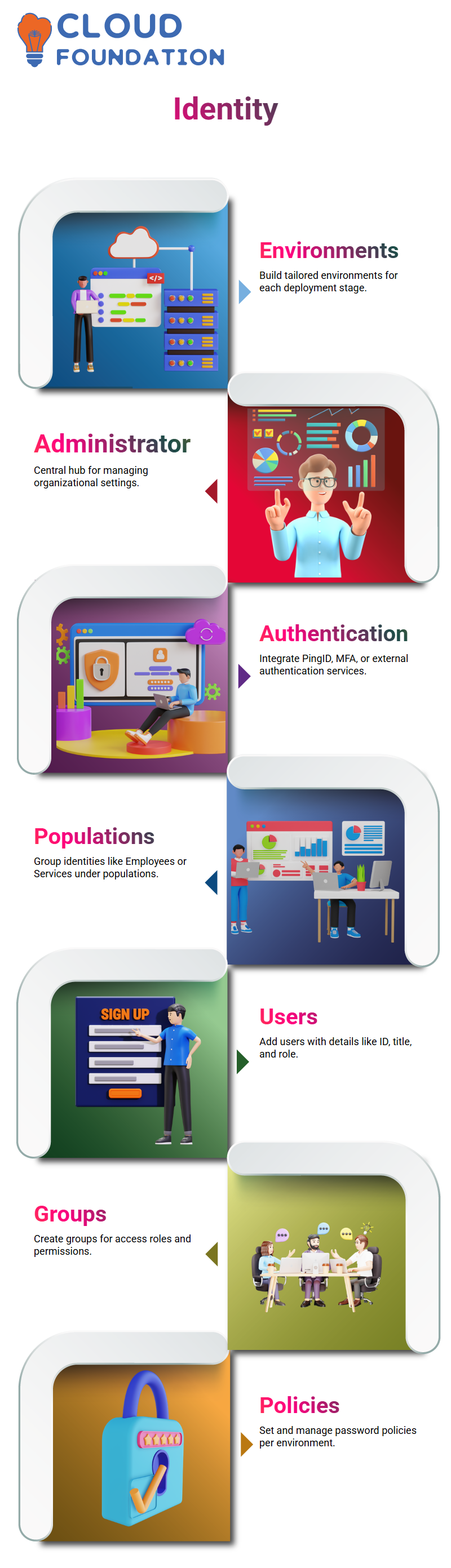
User and Group Management in PingOne
At the heart of PingOne is its directory and container system, where identities are stored and governed.
Populations
Create a population (e.g., Employees, Service Accounts) via the plus symbol.
Enable the population and set its identity provider (default or external, such as PingFederate).
Users and Groups
Add users with personal information such as IDs, titles, and roles.
Define password policies (one default per environment, editable later).
Create groups for roles like Managers, Developers, or Contractors.
Assign users to groups for SSO access and policy enforcement.
Authentication Policies and MFA in PingOne
PingOne offers versatile authentication methods to enhance security:
Password Policy – Define complexity requirements, lockout rules, and password expiration.
MFA Options – Choose from PingID, Cisco Duo, Google Authenticator, Microsoft Authenticator, or SMS/Email.
Passkey / FIDO2 – Strengthen authentication with hardware keys or biometrics.
Administrators can fine-tune MFA settings, such as passcode length, failure lock duration, or pairing modes.
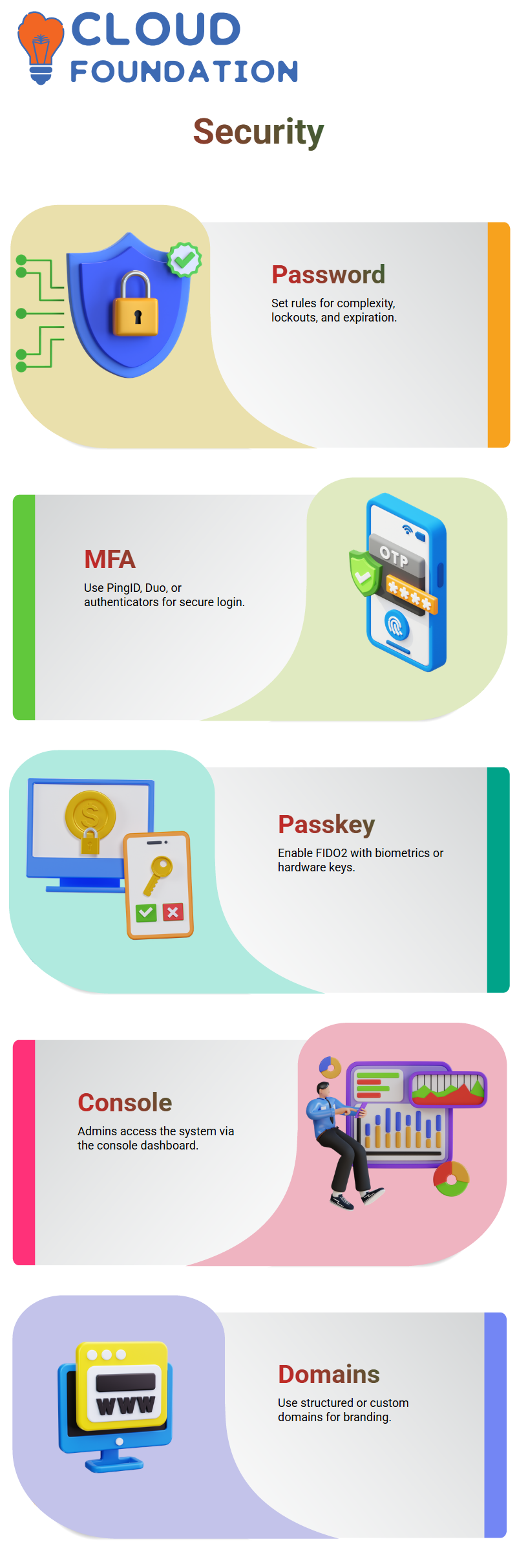
PingOne Deployment Essentials
By default, the PingOne dashboard provides:
Console Access – For administrators.
Account Management Apps – For user and role handling.
Self-Service Portal – For profile updates and MFA enrollment.
Endpoints follow a structured naming convention, such as:
– console.ping1.region for console access
– apps.ping1.com for applications
– auth.ping1.com for authentication
Custom domains can also be configured (e.g., console.orgs.com) to align with corporate branding.
PingOne Integration for Enterprise Monitoring and Security
PingOne environments can integrate with monitoring and security tools for enterprise-grade deployments:
PingFederate – For external authentication and advanced federation scenarios.
Splunk and Dynatrace – For log monitoring and analytics.
Gateways and Webhooks – To sync users and capture real-time event logs.
Adapters and clients can be configured for MFA and SAML, ensuring seamless communication between PingOne and enterprise applications.
Core Concepts of Identity Management in PingOne
Identity management is at the heart of every modern enterprise, and systems like Ping Identity Cloud provide powerful tools to ensure security, compliance, and ease of administration.
The key concepts of logging into the Ping console, managing roles, setting up password policies, and configuring authentication methods, such as SAML and OAuth.
Accessing the Ping Console
Initially, there was some confusion regarding access to the Ping console. While trying to log in via console.ping1.com, the speaker realised the URL wasn’t working as expected.
They were advised to use the correct login portal, console.pingonline.com, instead of relying on the redirecting URL. Once the correct console was accessed, login was successful, and work could continue.
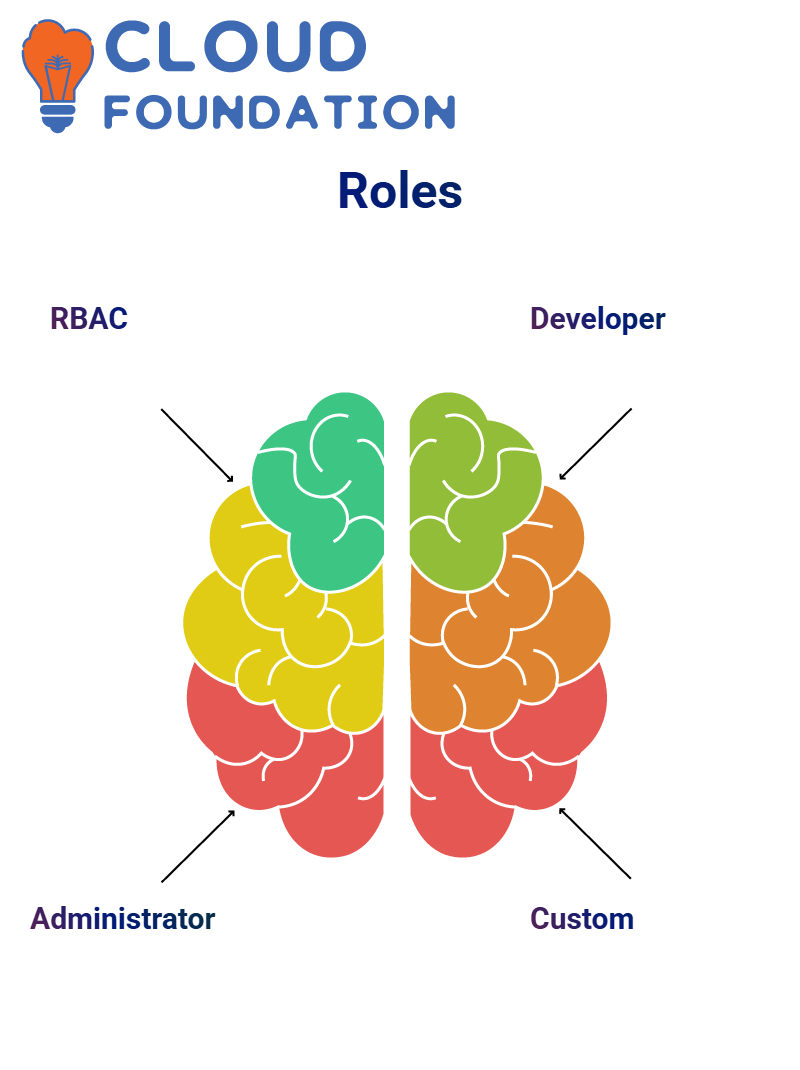
Identity Cloud Roles in PingOne
Identity Cloud offers role-based access control (RBAC), ensuring that users can only perform actions appropriate to their designated role.
Super Administrator: Has complete access to all configurations across the organisation.
Tenant Admin: Manages every tenant and SSO environment within their scope.
Application Owner: Can manage their assigned application but cannot alter directories or organisational data.
Developer: Granted API access to build and integrate applications (e.g., through MFA API using a client ID token).
Role Limitations
Each role comes with restrictions. For example:
- An administrator can manage and delete applications but not user attributes.
- An application owner cannot manage users or organisational data.
- Developers need an appropriate role assignment in addition to API access.
Custom Roles
Organisations can also define custom roles by combining permissions, such as environment admin and identity data admin. This flexibility allows teams to tailor access to their specific security needs.
Managing Users and Authentication in PingOne
The discussion highlighted real-world challenges, including failed login attempts resulting from password errors.
Users were prompted to reset passwords and ensure they were using updated credentials. In some cases, login attempts were made across different environments (e.g., auditor vs. administrator environments) using the same email address but different credentials.
Keep track of which environment you are logging into, and always follow secure password reset procedures.
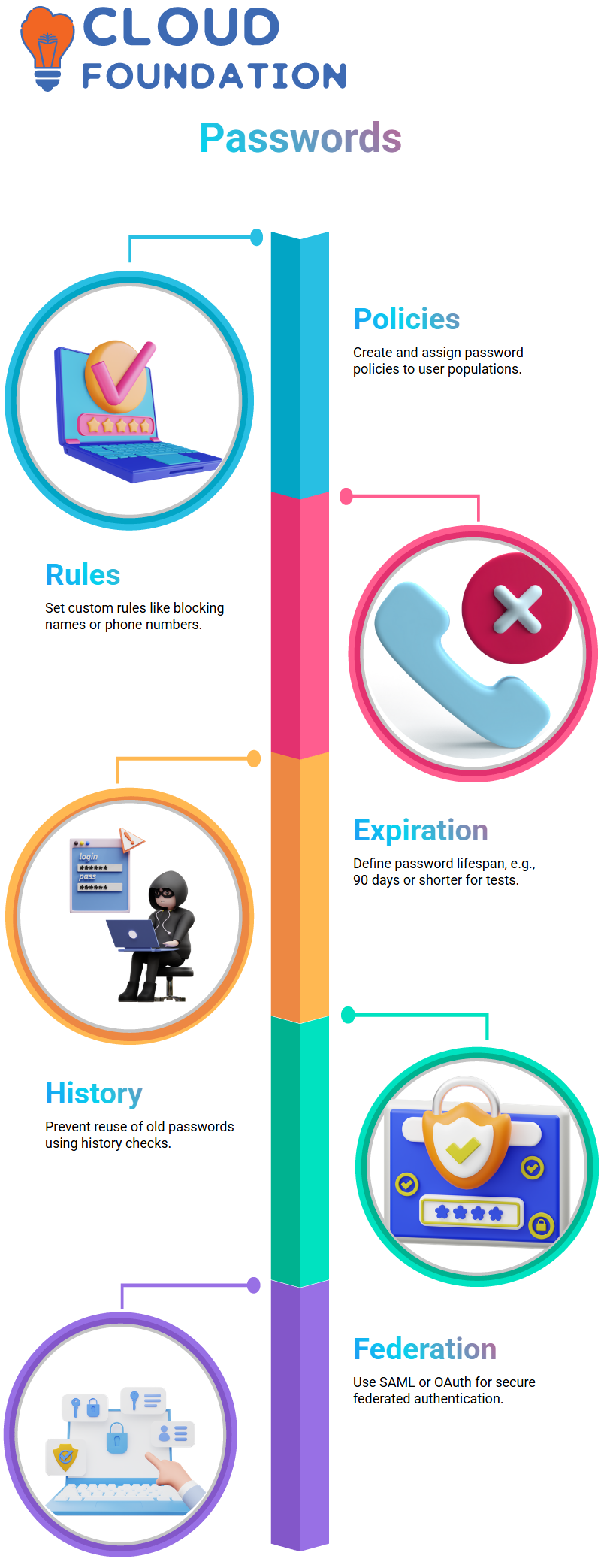
Password Policies in PingOne
Strong password policies are fundamental to securing identity systems. In this case, the user created a custom password policy in the Ping directory:
By default, one global policy exists.
A new policy can be defined under the Password settings.
Advanced rules allow customisation, such as preventing passwords that match personal attributes (e.g., last name, phone number).
PingOne Password Policy Configuration Guidelines
Minimum length: 8 characters
Special characters, numbers, lowercase, and uppercase required
Password expiration set to 90 days (with options for shorter lifespans, e.g., 60 seconds, for testing).
History check to prevent reuse of old passwords.
Once saved, this policy was assigned to specific user populations, enabling granular control across the organisation.
Configuring SAML and OAuth in PingOne
The blog also touches on federated authentication methods:
SAML (Security Assertion Markup Language): Widely used for enterprise SSO.
OAuth: Commonly used for API-based authentication.
While the concepts are familiar, enabling them in Ping Directory requires specific workflows. A single group can be created to assign users to applications, rather than managing multiple group types.
This simplifies access control but requires careful planning to ensure proper entitlements.
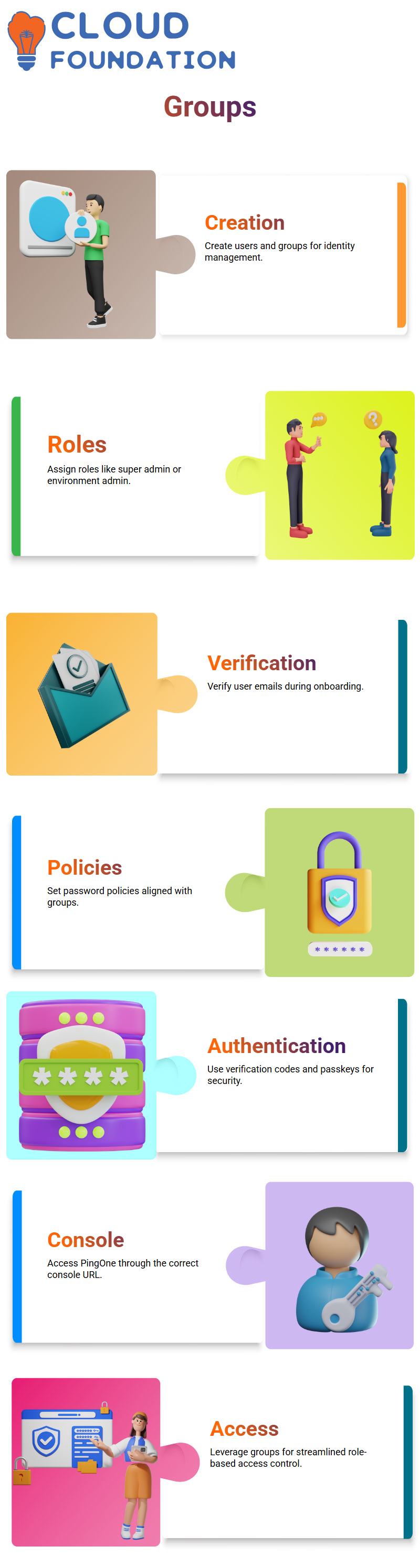
Group Management and Access Control in PingOne
Managing groups is a central aspect of Identity Cloud administration. The author outlines a typical workflow:
Create a user and group
Assign roles (e.g., super admin, org admin, environment admin).
Add users to groups and verify email addresses during onboarding.
Set password policies aligned with the group.
Users can then log in with their credentials, and administrators can enforce access by assigning roles based on groups.
Verification codes and passkeys (e.g., via mobile devices or apps like Cisco Door) further strengthen the authentication process. PingOne Access and Role Management
PingOne Access and Role Management
Use the correct console URL – always confirm the right entry point for your environment.
Understand role limitations – not every admin role provides complete control.
Implement strong password policies – customise them to block weak or attribute-based credentials.
Adopt SAML & OAuth carefully – they simplify access but require proper configuration.
Leverage groups for access control – group-based role assignment streamlines management.

Navya Chandrika
Author



 PingOne Access and Role Management
PingOne Access and Role Management 