Okta Authentication and Policies
Understanding Okta Authenticators
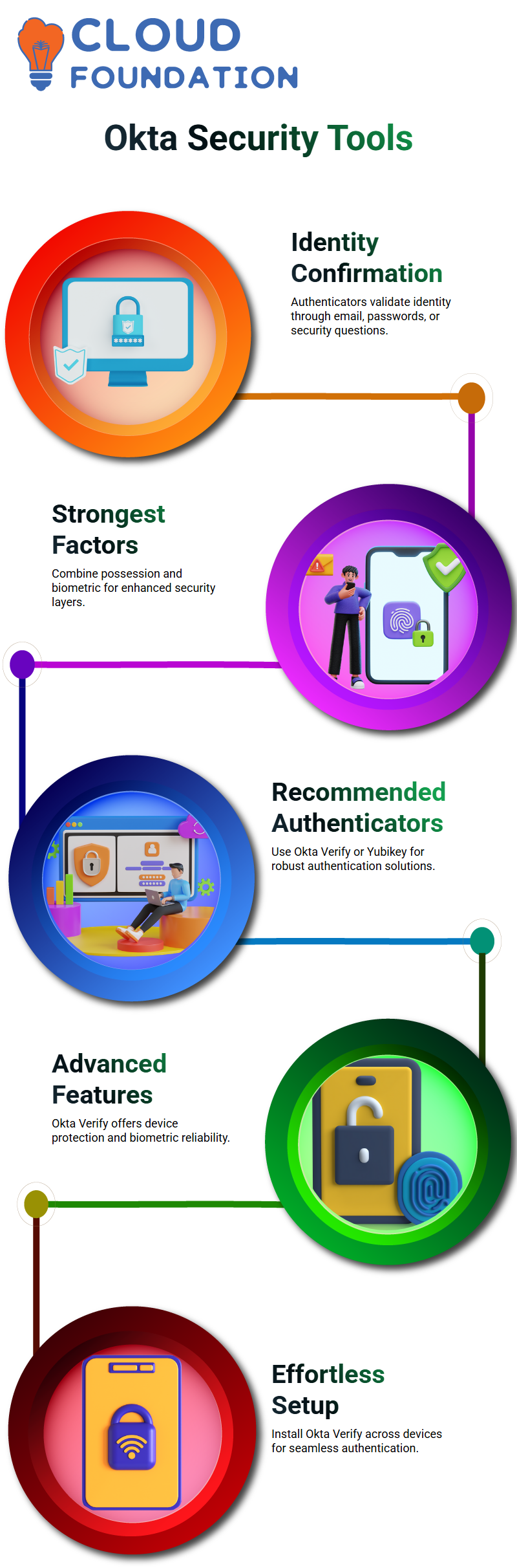
Okta authenticators are your primary security tools. In the past, these might have been known as multi-factors; now with Okta they’re called authenticators – these determine how identity can be confirmed – such as email, password and security questions are some examples.
Okta takes security seriously, providing an extensive list of supported authenticators organised according to factor type and method. These authenticators include possession, knowledge, biometric, or combinations thereof such as email being owned versus password being known. Security questions also rely heavily on knowledge.
Possession and biometric factors often combine to form the strongest factor. Knowledge factors, like passwords or security questions, can easily be stolen or compromised; by contrast, possession plus biometric adds extra security layers; for instance Okta Verify provides biometric-enabled authentication capabilitieswith hardware protection features, device binding functionality, user presence support, etc.
To satisfy stringent security requirements efficiently you’ll require both Okta Verify as an authenticator as well as your biometric signature to meet them; doing this significantly reduces compromise risks considerably and makes compromise risks significantly smaller!
Okta’s Recommendations for Authenticators
Custom authenticators such as OTPPS should generally be avoided to minimize risks to security. Google Authenticator, while functional, is generally disapproved of by Okta; therefore I advise opting for Okta Verify or security keys like Yubikey which provide strong device-binding authentication solutions instead.
Okta Verify stands out among your options as being most reliable; using it will let you benefit from its advanced security features like device protection and biometric reliability. YubiKey may be suitable if device-bound security meets your requirements; nonetheless it’s wiser to avoid weaker authenticators which might compromise your security infrastructure.
Getting Started with Okta Verify
Let’s dive right in with Okta Verify setup: you likely already use its app on your phone to receive push notifications; did you know there’s also a desktop version? Windows users can access Okta Verify MSI/EXE versions in settings and downloads; Mac users should search their Mac App Store. And finally if running a small organization this file could even be shared via Google Drive for easy installation!
At its core, Okta Verify ensures an effortless authentication experience across devices by directly installing software onto them with deployment tools that install software directly onto users’ computers or phones. Individual users may download Okta Verify from the App Store as an individual user to register devices like their laptop and phone under their account for seamless and secure authentication across devices.
Understanding Okta Configurations
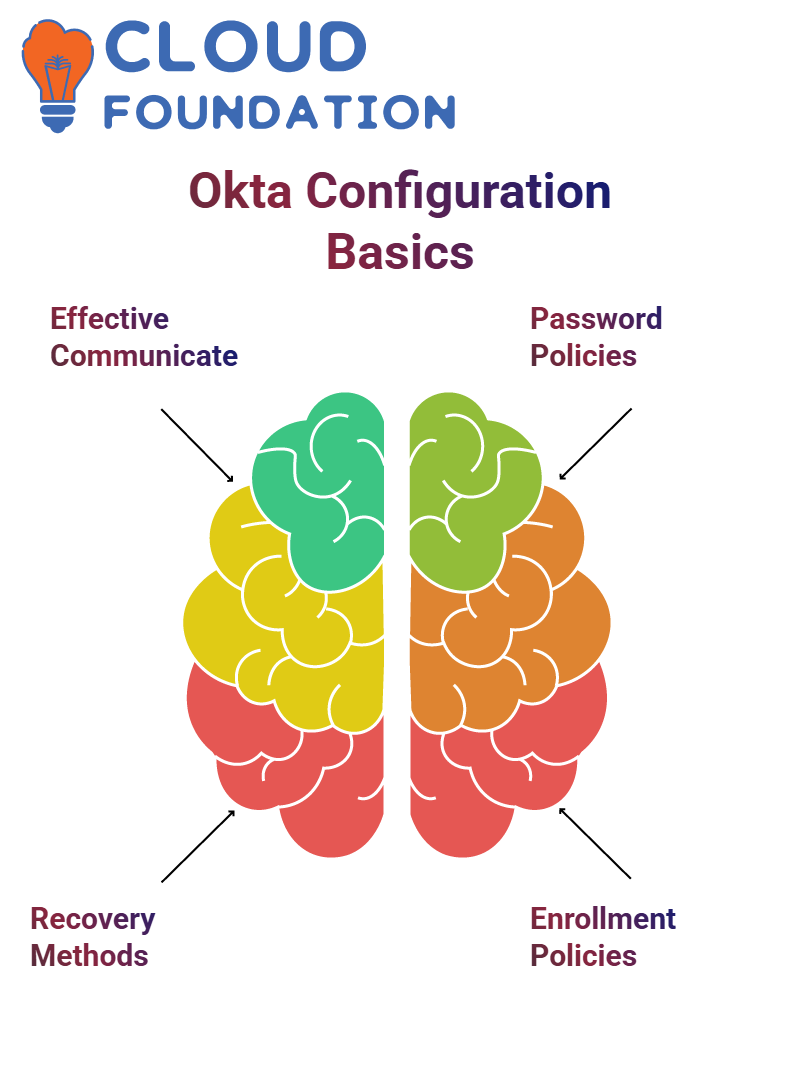
As soon as you implement Okta for the first time, it’s essential that all changes are communicated effectively to your team and stakeholders. Doing this ensures everyone knows why updates have occurred while eliminating unnecessary concerns about future implementation – for instance when configuring Okta Verify push notifications ensure all steps have been completed for a seamless deployment experience.
Okta Authentication and Recovery Settings
Okta allows you to clearly differentiate authentication and recovery methods; email and security questions should only be used as recovery measures; passwords remain mandatory as authenticationmeasures and Okta allows customisable password policies so they align with your organisation’s security standards.
Configuring Okta Enrollment Policies
Enrollment policies in Okta are key for managing authenticator setup. The default policy can be edited or replaced with custom ones – for instance requiring Okta Verify password authentication while turning off email authentication and security questions as authentication measures – tailor these policies specifically to groups within your organisation.
Customising Rules in Okta Policies
Okta makes it simple and effective for businesses to add personalized policies with Okta’s powerful Rules Engine, providing flexible controls over when and to whom these rules should apply – for instance if a user does not possess authenticators which meet requirements during sign-in, Okta prompts enrollment during their next sign-in, ensuring security measures are enforced effectively.
Navigating Okta Applications
Okta has organised its applications into three distinct groups, the admin console, browser plugin and user dashboard. Each application requires individual attention with specific configuration settings – knowing this enables efficient administration of these services.
Understanding Okta Policies
Okta makes policy management effortless by making authentication and sign-on policies easily visible across applications. Imagine having 20 applications where it is imperative that everyone follows one uniform policy–Okta simplifies this process: simply go into its Policy Section, add all applicable apps, and ensure everyone abides by a consistent set of regulations.
Take for instance the Okta dashboard: it showcases various policies and their rules; but be mindful that catch-all rules cannot be edited except for limited details. With Okta you can tailor policies specifically to your needs by specifying user type, device state, platform platform IP or risk level to create robust yet flexible policies.
Enhancing Security with Okta Authentication
Okta offers numerous authentication solutions, from password authentication with hardware protection and antiphishing measures, to biometric verification with Yubikeys or biometrics that need to be preconfigured before use. Users can securely verify themselves using Okta Verify or biometrics with features like Okta FastPass; users can even set password reauthentication frequencies every two hours for added consistency in security.
Okta may pose additional security questions during sign-in that are optional but beneficial, and once signed in users can view device details (for instance Android device models) through Okta’s management dashboard – something which has proven invaluable for organisations implementing Mobile Device Management (MDM).
Okta Device Management and Policies
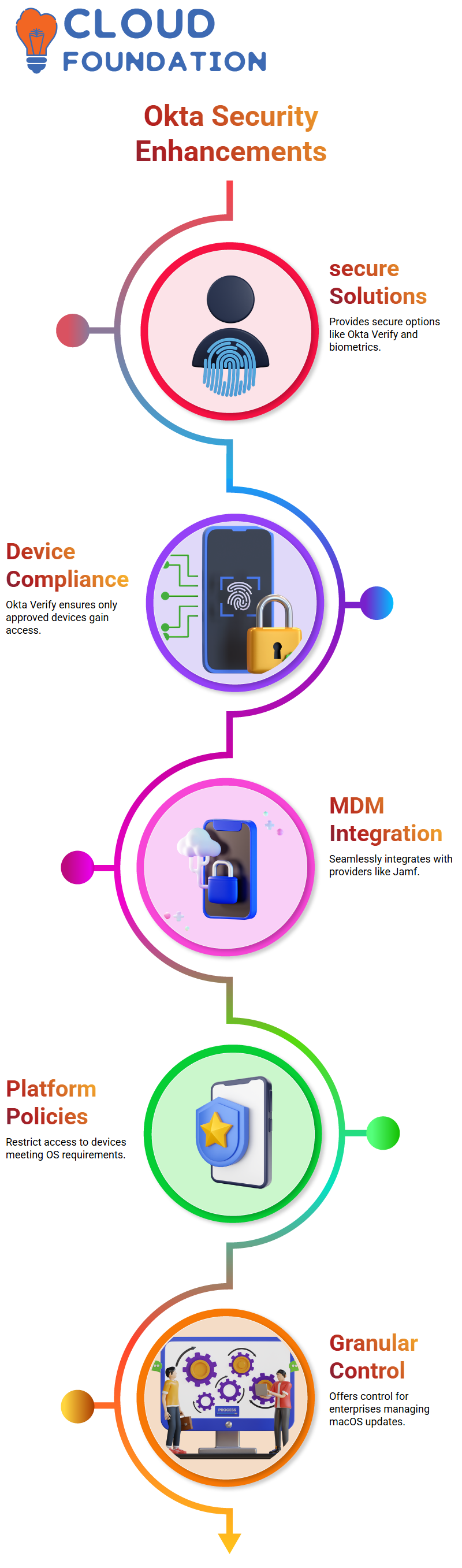
Okta Verify forms the cornerstone of device management by installing it across devices and enrolling users. Managed devices appear compliant with organisational policies, giving administrators power to enforce access rules; for instance if an unmanaged device tries to gain entry, Okta can block access ensuring company data only remains on approved devices.
Okta seamlessly integrates with MDM providers like Jamf for macOS and Windows machines. Administrators can leverage policies to enforce login restrictions to only devices where Okta Verify has been installed and recognised as being managed, increasing both security and complying with company standards. This approach ensures compliance while elevating overall company compliance standards.
Leveraging Okta for Platform-Specific Policies
Okta’s flexibility extends beyond device access control to platform-specific policies as well. Administrators using macos 12 can enforce device assurance policies to allow only devices compliant with this OS to log in – making Okta an indispensable solution for keeping track of device access in shifting IT environments.
Okta provides enterprises with the granular control necessary for modern enterprises that wish to rollout macos updates, like version 13, by making sure only updated devices gain entry. With such comprehensive and specific control available through Okta, businesses of today depend on it as essential software.
Understanding Okta and Device Policies
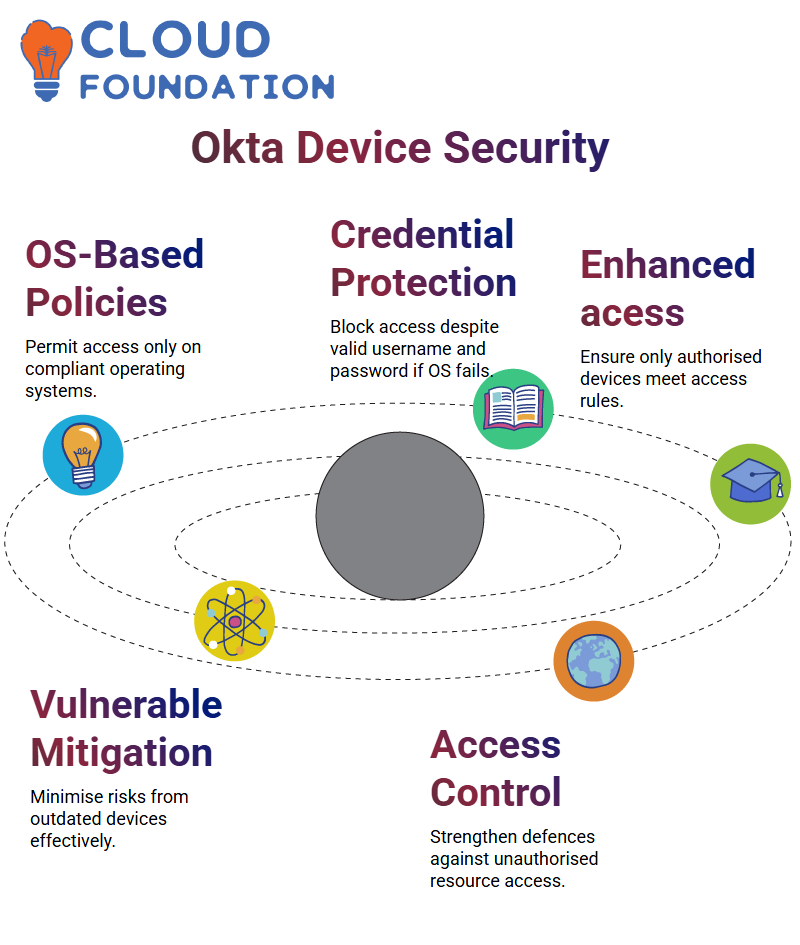
Let me demonstrate how Okta can provide security when everyone uses Mac OS 13. Using Okta, you can set a policy which only permits access if an operating system meets this version, meaning anyone using an earlier one is denied entry automatically.
Okta excels at protecting against potential attackers with valid credentials despite them having them; even if someone enters their username and password correctly, their device must run Mac OS 13 before proceeding further.
Okta’s Role in Enhancing Security
Okta has enabled us to implement stringent security measures while keeping end-user experience uncluttered and seamless. Policies based on operating systems help minimize potential vulnerability from outdated devices.
Okta makes an exceptional contribution by helping administrators set clear rules, guaranteeing only compliant devices gain entry. This adds another level of protection when managing user authentication and access management.
Why Okta Is Essential for Access Management
Okta has proven invaluable as part of my security system’s defenses, making enforcement policies such as restricting user access with outdated OS versions much harder for attackers to exploit vulnerable systems.
Okta’s focus on compliance and security provides organisations with an efficient means of maintaining control over who can access their resources, protecting against unauthorised access. Every policy implemented with Okta strengthens your defenses against unwanted access.
Managing Office Networks with Okta
As soon as it comes to protecting office networks, one of the first tasks should be identifying gateway IPs. Consult your network team and take down these details; for instance if given 191.680.0/14 as your range then that includes IP addresses from 191.660.1-191.660.254. This basic structure forms part of Okta’s seamless implementation.
Okta allows you to easily define trusted IP ranges, making it simpler and faster for you to ensure that no office network IPs are flagged as malicious. For instance, when using proxy solutions like ZScaler or Netskope with Okta you simply input their ranges, specifying both start and end points so these IPs remain recognized within your network as safe.
Utilizing IP Zones in Okta
Okta provides block IP zones to prevent certain addresses from accessing your systems, simply by inputting these IPs into its interface and automatically blocking them. Dynamic zones also add another level of security; for instance if your organization operates within the US you could configure Okta to restrict access from certain countries like Russia and Iran based on specific criteria – providing additional layers of protection!
By default, Okta disallows Russian IPs unless special permissions have been granted; this ensures compliance with international regulations while protecting against potential threats to your system. Okta’s robust policies enable organizations to block IP addresses that pose risk while strengthening security across their organization.
Customizing Authentication Policies with Okta
Okta provides organizations with the flexibility to tailor authentication policies according to their unique requirements, for instance enabling only password authentication within office networks – without multi-factor authentication (MFA). This facilitates smoother internal processes without jeopardizing security.
Okta’s session policies make implementing global session rules simple and effective. Once your network settings have been configured in Okta, they can easily be integrated across authentication policies – making Okta an invaluable addition to any existing framework.
Blocking High-Risk Regions with Okta
Imagine that your employees travel to high-risk regions where cybersecurity threats are abundant. Okta can help secure access to your network from these areas by restricting IPs directly through its platform – this ensures even if credentials become compromised, unapproved entry won’t happen!
Okta can also protect employees against coercing them into divulging login details by blocking certain regions and enacting stringent access policies, helping reduce security branches.
Preventing Proxy-Based Threats Using Okta
Proxy tools such as Tor are commonly utilized by hackers to conceal their activities; with Okta you can identify and block these proxies to ensure network security remains strong. Hackers frequently rely on proxy tools like Tor to operate unseen; with Okta you stay one step ahead!
Okta’s proactive approach to recognizing and mitigating risks from unconventional sources demonstrates its comprehensive security offerings. From Tor proxies and unfamiliar IP ranges to Tor botnets and Tor relay services, Okta provides all of the tools you need for effective handling.
Understanding Okta’s Role in Secure Access
Okta has become an indispensable solution in terms of managing secure access across devices and platforms, safeguarding user data in the process. By choosing Okta as part of your, data protection plan . I hope I have demonstrated its efficacy at managing access.
How Okta Protects Your Devices
Okta can help protect company devices against potential security risks, while giving employees flexibility in exploring its features on personal devices. Let me demonstrate why restricting access on company devices is crucial: Okta ensures sensitive information stays protected while giving people freedom to explore features at will.
Okta and Illegal Activities Prevention
With Okta in place, your systems can stay safe from illegal activities typically associated with unprotected platforms. I’ve heard accounts of platforms being misused for harmful reasons – that’s why having something like Okta makes a significant difference!
Why Okta’s Connection Process Matters
Connecting to Okta is straightforward and secure. While initial set up might feel lengthy, every action taken by you is encrypted using our solutions and this makes us reliable solutions that make their job easy!Okta’s P2P Network: A Secure Choice
Okta operates on a P2P network, meaning your traffic gets routed securely and is never exposed. This innovative feature ensures no one can pinpoint your true location, significantly increasing privacy. Even though Okta may seem slower at first, its protection more than makes up for any delays experienced while using their service.
Randomized Addresses with Okta
One of Okta’s signature features is its use of random addresses – each time you sign in appears from an entirely different location! This highlights their dedication to protecting user anonymity.
Using Okta for Secure Marketplaces
Okta makes online marketplace shopping safer. Unprotected access has exposed me to several risks; by adding Okta security measures you are creating an additional safeguard which ensures smooth transactions.
Okta’s Customizable Proxy Settings
Okta allows you to personalize the proxy settings according to your specific requirements, from blocking certain configurations or configurations altogether – giving it maximum flexibility. I always take care to utilize these features for maximum protection.
Okta Behavior Detection
Let me illustrate how Okta’s behavior detection directly impacts user authentication. Imagine you have authenticated from only US locations for 20 authentications in a row, then on 21st login from Canada Okta sends out an email asking whether this really is you? – providing user security through change detection systems such as Okta that evaluate location changes and require verifications.
Okta’s verification process takes into account not just countries but cities as well, for example if your last 10 authentications took place in New York and your next one takes place in Washington – triggering an identical verification process each time! Our system adapts seamlessly to changes in city, country, device geolocation IP address or state so each factor is taken into consideration and taken into account.
Okta Velocity Detection
Okta makes travel simpler with velocity detection capabilities that work on planes or trains – when used for authentication on these modes of travel, Okta allows travelers to customize how it recognizes speed changes as their location changes quickly; perfect for onboard train travel when constantly shifting locations can compromise authentication security.
Okta Authentication Policies
Okta makes travel simpler with velocity detection capabilities that work on planes or trains – when used for authentication on these modes of travel, Okta allows travelers to customize how it recognizes speed changes as their location changes quickly; perfect for onboard train travel when constantly shifting locations can compromise authentication security.
Configuring Okta for Travel Behavior
Okta allows you to tailor session policies based on user behavior. If users are traveling between cities or countries, session length could be reduced for added security while stationary users might benefit from extended session times for convenience.
Okta and User Context
Okta excels at understanding real user contexts. No matter whether someone is working from their office desk, traveling by train, switching devices frequently or accessing multiple accounts concurrently; Okta’s session policies adapt seamlessly so every user’s unique situation is taken into consideration, providing security as well as flexibility for every situation that arises.

Navya Chandrika
Author



