ForgeRock Certification Training Online
Setting Up Entity Providers in ForgeRock
When I create entity providers in ForgeRock, I normally advise my team to take their time and verify names, URLs, and meta-aliases again.
In ForgeRock, the SP and IDP will cease communicating to each other if there is even a slight difference.
As I go through the setup, I stress how ForgeRock wants the realm structure to remain the same, particularly when there is more than one service provider involved.
I go over each field entity ID, meta-alias, and endpoint to show the team how ForgeRock connects them behind the scenes.
When we set up a Circle of Trust, I tell them again that ForgeRock needs both sides to have the same settings.
If ForgeRock finds discrepancies, it won’t set up the trust route, and the login flow will stop working.
I keep stressing how important it is for all realms to be in sync throughout these sessions since ForgeRock reads every value precisely as it is set up.
That degree of accuracy is what makes ForgeRock so strong, but it also requires a lot of care.
Troubleshooting Realms and Meta Aliases in ForgeRock
I always check to see if the ForgeRock realms match first when something doesn’t function.
I’ve seen a lot of teams make an SP in one realm and an IDP in another without making sure the meta-aliases match.
I make sure to make it obvious that ForgeRock won’t let the authentication flow happen until these variables match.

In one situation, I saw that the SP realm had a different meta-alias than the IDP realm, and ForgeRock wouldn’t let them join.
We need to create the entities again at the top-level realm since ForgeRock respects top-level setups more uniformly across modules.
As soon as we rebuilt them, ForgeRock picked up the configuration right away.
When I help someone debug, I always make sure they know how ForgeRock reads these structures.
They not only cure the problem at the conclusion of the session, but they also learn how to confidently handle any ForgeRock configuration.
Understanding ForgeRock OIDC Scripts
We use a number of OIDC scripts at ForgeRock, including the scope script, the verified scope script, the authorize endpoint data provider script, and the claims script.
You may use the ForgeRock endpoint data provider script to deliver more user information, such an IP address, a session value, or data from an outside service.
This ForgeRock script lets you add more information to tokens whenever you need to.
You may add new key-value pairs, get information from other sources, or improve the user’s request flow without changing how the system works.
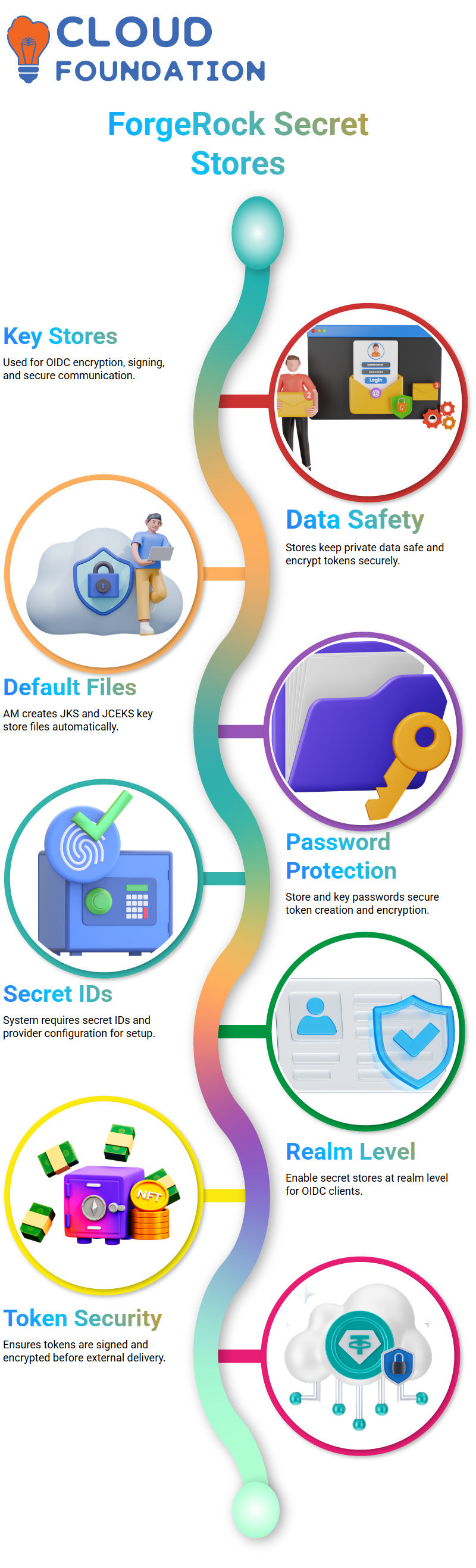
Managing ForgeRock Secret Stores
ForgeRock uses key stores and trust stores whenever we set up OIDC encryption, signing, or secure communication.
These stores keep private data safe, encrypt tokens, and sign messages between services.
When we set up ForgeRock Access Management (AM), the system creates default key store files like the JKS and JCEKS stores on its own.
The software employs store passwords and key passwords to protect every step of making, signing, and encrypting tokens.
The system can safely perform all OIDC and OAuth actions if you set these settings up appropriately in the ForgeRock secret store setup.

ForgeRock Training

Configuring ForgeRock Secret Stores
When you set up secret stores in ForgeRock, you let the system see your key store file, choose the provider, and provide it the secret IDs.
From the ForgeRock security directory, specify the right path, and link the default passwords.
These numbers originate from the ForgeRock security package, and they let the platform access and sign encrypted data.
You may set up hidden shops in ForgeRock either globally or at the realm level.
I always recommend turning on the secret store at the realm level when we make an OIDC client.
This way, the client will utilize the right signature and encryption keys.
This step makes sure that ForgeRock signs tokens correctly and encrypts important data before delivering it to apps outside of ForgeRock.
Why ForgeRock Encryption and Sign in Matter
When someone asks me how ForgeRock keeps client communication safe, I refer them right to its encryption keys, signing keys, and secret store settings.
These functionalities are now embedded into the ForgeRock platform to keep OIDC and OAuth exchanges safe.
Older versions didn’t have these secret store capabilities, but ForgeRock now uses permanent secret stores, Base64-encoded secrets, and cryptographic aliases to provide a tiered security paradigm.
When ForgeRock provides encrypted data to a client, the client uses key pairs set up in the system to decode it.
This makes sure that only services that are allowed to read sensitive values may do so.
Setting up the ForgeRock secret store properly adds another layer of security to our OIDC clients, tokens, and user characteristics.
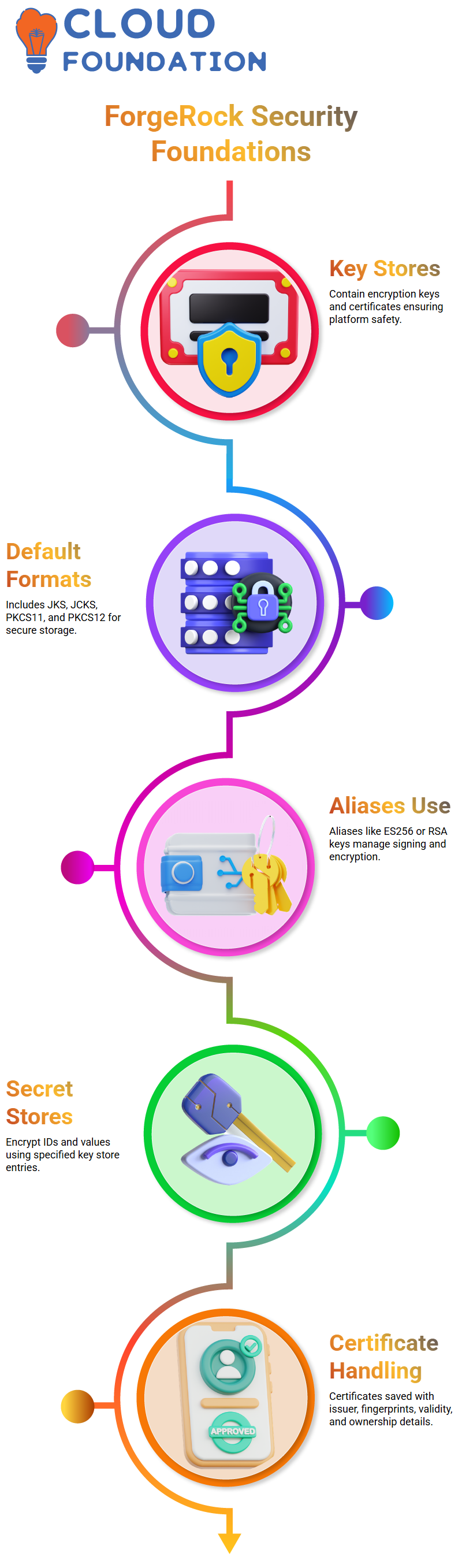
ForgeRock Key Stores and Security Foundations
Key stores are very important to ForgeRock because they contain the keys and certifications that keep the platform safe.
When I set up a server or show someone around the security portion, I always mention that ForgeRock comes with default key stores like JKS, JCKS, PKCS11, and PKCS12.
These formats may seem complicated, but if you look into them in ForgeRock, you start to see how they all function behind the scenes.
These key stores within ForgeRock hold the encryption keys, trusted certificates, and different aliases that the system needs to work safely.
You will see aliases like test, ES256, or RSA-based keys when you open the ForgeRock settings and look at the keystore entries.
ForgeRock sends some of these for testing, but in practical projects, customers usually use their own certificates instead.
I constantly point out how ForgeRock utilizes these entries to sign, encrypt, and check the data that comes in and goes out.

ForgeRock Online Training

ForgeRock Secret Stores and Certificate Handling
Key stores and secret stores function together, and both are very important for a safe identification platform.
You can view IDs and encrypted values when you access the secret store mappings in ForgeRock.
These values are safe because ForgeRock encrypts each entry using the keys you specified in the key store.
Nothing within ForgeRock would be secure enough for production situations without this architecture.
The alias we provide when we create certificates in ForgeRock is very important.
In OIDC settings, authentication modules, cookie encryption, and token signing, that alias is utilized again.
When you generate a certificate in ForgeRock, the platform saves it in the key store together with information about the issuer, fingerprints, validity, and ownership.
I regularly illustrate how ForgeRock examines these certificates before letting any client or user log in during training sessions.
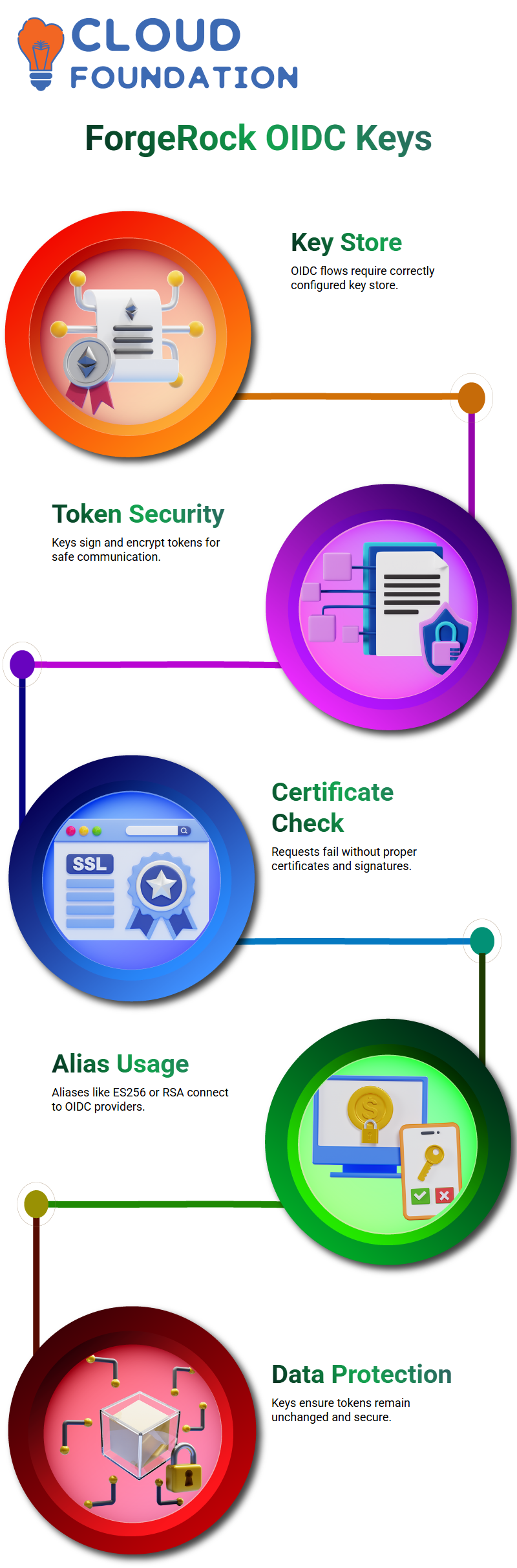
ForgeRock OIDC and the Role of Signing Keys
When I talk about OIDC in ForgeRock, I always make sure to say that none of the flows will function until the key store is set up correctly.
ForgeRock uses the keys in the keystore to sign and encrypt tokens.
For instance, if a client attempts to log in without the right certificates, ForgeRock would stop the request since it can’t check the signatures.
This is why I tell students to look at every alias in the ForgeRock keystore.
If you look for aliases like ES256 or RSA in ForgeRock, you’ll see how the platform connects them to OIDC providers and token signing settings.
These keys are needed for every OIDC interaction in ForgeRock.
When ForgeRock gets or sends a token, it utilizes these keys to protect the data so that no one else can change it.
This is the basis for safe identification processes in ForgeRock.
ForgeRock Security Practices and Key Management
These stores contain private data, and ForgeRock expects administrators to set them up appropriately.
These safe storage methods are what ForgeRock relies on for everything, from direct encryption keys to private key entries to certificate chains.
ForgeRock wouldn’t be able to check requests, encrypt tokens, or sign authentication answers if the keystore were absent.
ForgeRock also employs trust stores to keep certificates from other systems safe.
These trustworthy certificates are very important when you want to connect ForgeRock to other apps.
I regularly show how ForgeRock utilizes these trust entries to check the identity of incoming requests.
This is why ForgeRock tells administrators to always keep their certificate stores clean, up-to-date, and legitimate.

ForgeRock Course Price


Nishitha
Author