DevSecOps Tutorial
What is DevSecOps?
DevSecOps is an integral element of any successful development process and must be prioritized as part of our security approach to ensure team member protection and an enforcing an acceptable working environment for everyone on our teams.
DevSecOps (Development Security and Operations) is an term that encompasses development and operations working together to collaborate effectively on automating tasks efficiently, while still meeting security criteria such as firewalling, role-based access control systems, tripwires or any other required measures.
Security audits tend to be undertaken near the end of a production pipeline and usually consist of manual tasks or use of automated tools.
Concept of DevOps
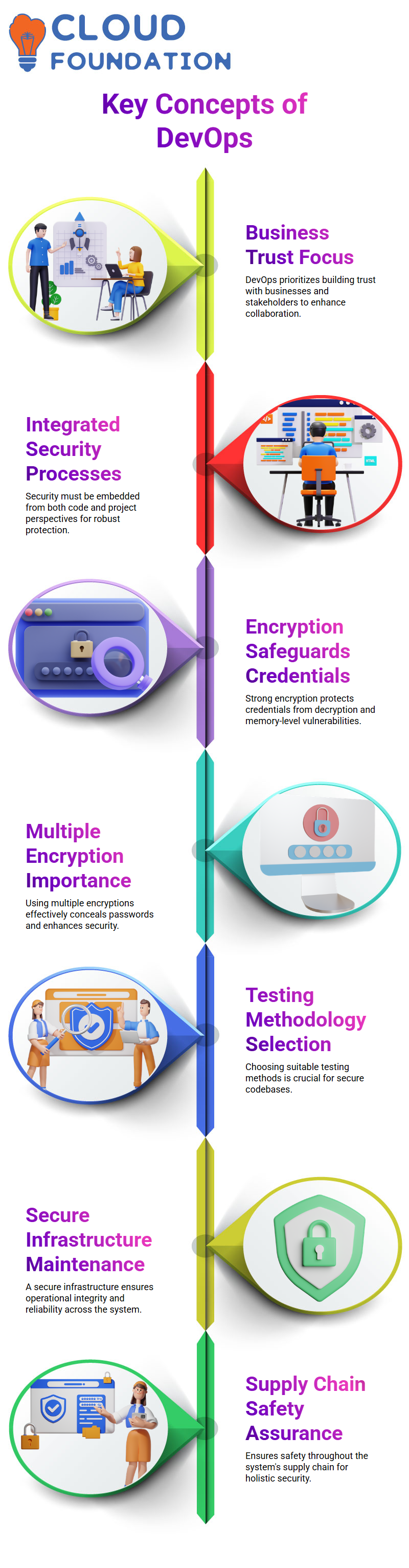
DevOps is an approach which places priority on building the trust of businesses and stakeholders.
Security in software development processes cannot be overemphasized and must be built-in from both code level and project aspect perspective.
Asserting the need for encryption to safeguard credentials against decryption and memory level exceptions.
Multiple encryptions should be employed in order to conceal passwords effectively. When testing code security it is key that we select appropriate testing methodologies for our codebases.
Maintaining a secure infrastructure is of crucial importance both to business operations and infrastructure itself, to ensure both its integrity and reliability are upheld. This guarantees safety at every point along the system’s supply chain and in itself.
SDLC Waterfall model
SDLC waterfall model has proven problematic during development processes, leading to numerous issues and leading the team down a difficult path of troubleshooting.
To address this, they implemented various methodologies including big bang, more straightforward approaches, iterative methods and agile processes in an attempt to solve this problem.
The SDLC waterfall model has been implemented through multiple life cycles, each one with their own set of obstacles to face.
Agile methodologies have evolved significantly over time from their original form as months-long processes to weeks or days long ones, automating various tasks including code quality assurance, code coverage analysis, package creation, etc.
It has enabled them to streamline processes and increase overall efficiency.
The SDLC waterfall model has proven an immense challenge during development and caused numerous complications.
DLC life cycle in DevsecOps
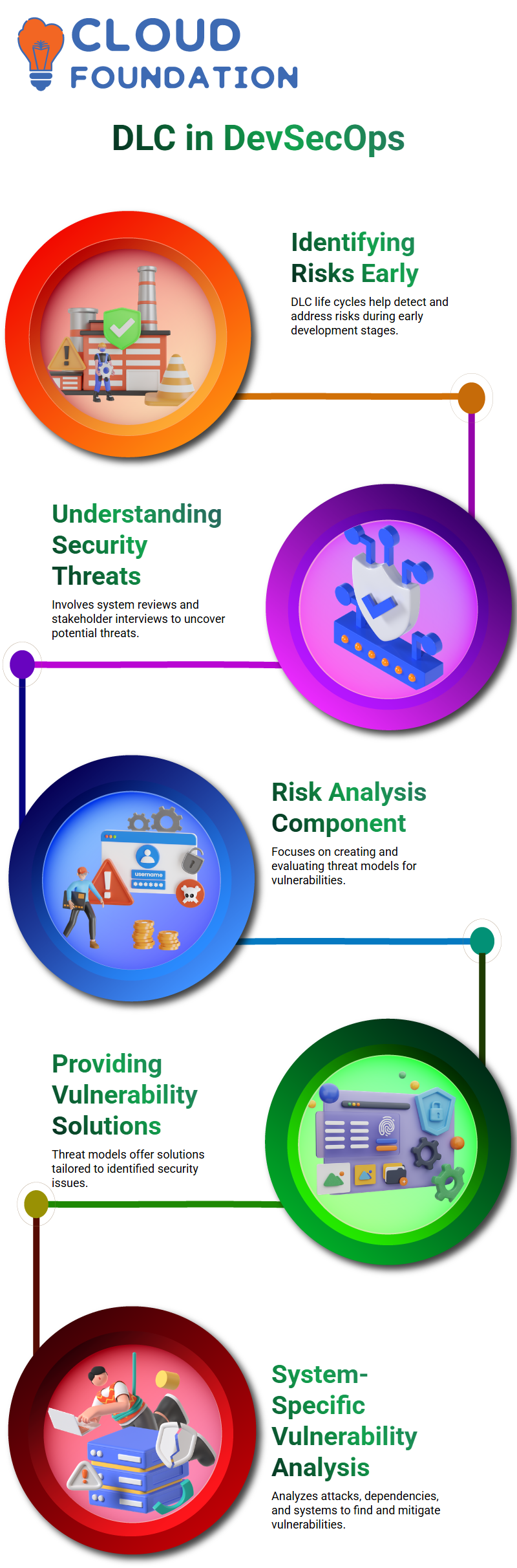
DLC life cycles are integral parts of software development that help identify and address potential risks early.
This process includes an examination of design levels, interviews with business owners, and examination of systems to understand security information and potential threats that might compromise business goals.
Risk analysis is one of the primary components of DLCs, consisting of creating and analysing threat models from different businesses and stakeholders as well as understanding their relationship to one another and with your organization.
This threat model provides assistance in recognizing potential vulnerabilities and offers solutions based on identified threats.
System-specific analyses consist of system-specific attacks, dependencies analysis and attacks analysis; all three serve to detect potential vulnerabilities while providing necessary mitigation strategies.
Architecture risk analysis (ARA)
Architecture Risk Analysis (ARA) is an essential first step toward mitigating security risks during early phases of software development life cycle (SDLC).
Architecture risk analysis is an invaluable way of mitigating security risks and assuring system safety and security.
This process includes exploring various forms of security before employing various principal tools that simplify understanding.
At any stage when considering risks, Aura analysis should be employed; such as when finalising designs or when creating security separate units within organizations.
CMM level audits must also be completed regularly in all standard organisations in order to guarantee security compliance.
Auditors play an invaluable role in conducting Aura audits from an accurate source. Today’s organizations may contain security units; however, their primary responsibility should not lie solely within these structures; rather it should involve developers and DevOps teams working collaboratively towards this end goal.
Static application testing in devsecOps
Static application testing, security testing and DST testing are used to verify both security and functionality within applications.
Coverity can help identify and resolve any potential issues related to static, dynamic or other components within an app.
Static application security testing is an integral component of security testing, helping identify vulnerabilities and threats within an application.
Utilizing tools like HP 45 (micro focused tool ), Micro Focus 45, these efforts enable security testers to quickly locate potential issues within applications while mitigating threats that exist within.
Static application testing is an integral component of security testing and various tools such as HP 45, Micro Focus and DST can help identify and mitigate vulnerabilities within applications.

SAS and desk application security Testing (SAST)
SAS and desk application security play an indispensable role in protecting data integrity and protecting against potential attacks.
Testing methodologies used to uncover vulnerabilities within applications include static analysis (white-box testing) and dynamic analysis (black-box testing), both of which examine running software to reveal any possible security holes or flaws.
Runtime environments provide web applications and web services with crucial runtime environments they rely upon, while both session test techniques offer complementary techniques with their own set of steps to follow.
Comprehensive vulnerability testing is key for assuring the security of web apps and services.
SAS and desk application security play an invaluable role in protecting data integrity and protecting against potential attacks.
Testing methodologies such as static analysis and dynamic stress testing (DST), are invaluable ways to detect vulnerabilities and potential threats facing any organization.
When selecting the approach that meets both budgetary needs and organizational expectations, selecting an ideal methodology can ensure it helps identify threats early.
Open-sourced software development
Open-sourced software development is an emerging trend with numerous advantages, including increased security, lower costs and greater agility.
One of the key characteristics of open-source software development is integrating Software Development Life Cycle (SDLC).
This integration enables developers to access and manage code more effectively, thus decreasing risk and producing quality code more rapidly.
One of the core tenets of open source software development lies in its capacity to integrate seamlessly with other systems, like Microsoft Office and Google Cloud Platform.
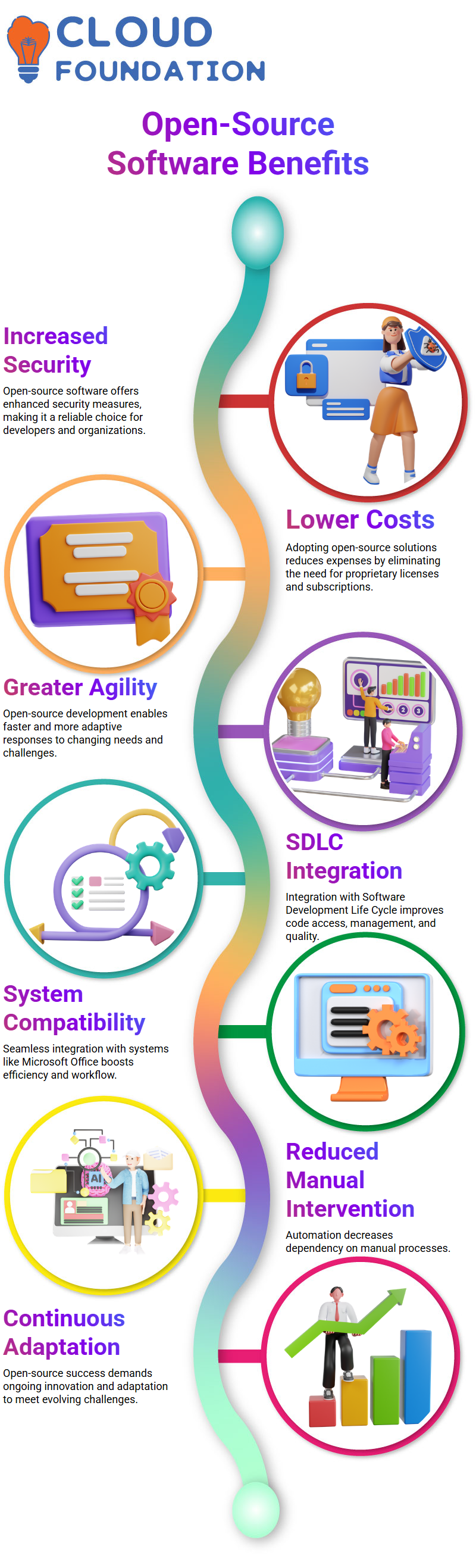
This integration empowers developers to manage their code more efficiently, decreasing manual intervention while guaranteeing all dependencies are met.
Open-source software development is a challenging field that necessitates continuous adaptation in order to be successful.
Understanding both the challenges and opportunities associated with open source software development allows developers to produce more secure software solutions which help their organizations prosper in today’s ever-evolving digital environment.
RR testing
Testing software development projects requires several crucial processes, with developers conducting various types of RR tests in order to assess its quality and functionality.
Such activities could include thread modelling, code review, configuration reviews, architecture risk analyses and build time checks – among many others.
At the RR test time, it is critical to perform an architecture risk analysis to detect vulnerabilities within source code.
Testing requires careful attention to ensure that both environments and code deployment go as expected, otherwise testing could proceed without successfully placing code within them.
If an environment is unfit, testing could still proceed but without code being installed successfully into it.
Software testing, especially regression and functionality testing (RR testing) is an integral component of software development, consisting of various tests designed to validate both quality and functionality in code.
By conducting comprehensive architectural risk analyses, assuring code conformance to relevant standards and performing rigorous build time checks, developers can help guarantee both the quality and safety of their software products.
Secure supply chain
DevStack places great emphasis on providing a secure supply chain and having local cache to store information securely.
Security context also forms part of its philosophy as it gives guidance for pods and containers.
Security in supply chains, the importance of using tools like Opa, Gatekeeper, Hive and pod security policies are of utmost importance.
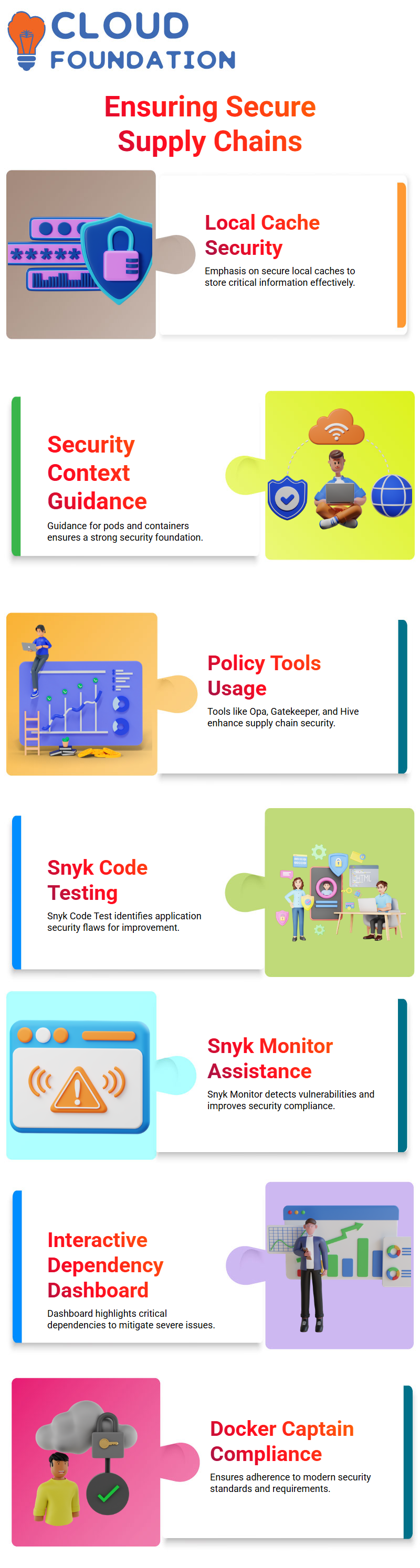
Snyk code test
Snyk Code Test and Snyk Monitor can assist in detecting security flaws within applications, while using tools like Docker Captain can ensure compliance with current security standards and requirements.
Snyk provides an interactive dashboard to identify dependencies like body-parser and qs that contain high severity issues and allow users to make sure that their application does not depend upon any that pose vulnerabilities.
Conclusion
DevSecOps represents an essential shift in software development and operations by embedding security into each stage of software development lifecycle (SDLC).
DevSecOps ensures security is no longer an afterthought in development by emphasizing proactive security measures, automation and collaboration among development, security and operations teams – and ensures security becomes part of its core components of operations.
Early threat identification, secure infrastructure design and rigorous security testing methods such as static application security testing (SAST) cannot be understated.
Integration of open-source software development, architecture risk evaluation and secure supply chain practices further contributes to creating a resilient and secure software environment.
Utilizing tools like Snyk and comprehensive testing approaches, companies can identify vulnerabilities early and quickly address them for safer and more dependable software apps.
As digital technologies advance, DevSecOps remains essential in making sure software not only functions but is secure – protecting both businesses and their stakeholders from liability risks.

Navya Chandrika
Author



