CyberArk Training | CyberArk Course Overview
Identity and Access Management (IAM) is crucial for contemporary cybersecurity approaches, providing a solid structure for handling digital identities, regulating resource access, and protecting confidential information.
In today’s interconnected digital landscape, where cyber threats are ever-evolving, having a structured approach to authenticate users, authorise their actions, and ensure compliance with regulatory requirements is crucial.
Utilising IAM solutions helps businesses simplify user provisioning, enhance authentication methods, and enforce detailed access controls in various IT environments.
This opening paragraph establishes the foundation for delving into the crucial role IAM plays in strengthening organisational security postures and promoting a culture of trust in the digital world.
CyberArk training is essential for companies to protect their data and effectively secure access to critical systems.
CyberArk Introduction
CyberArk is a pioneer in privileged access management (PAM), delivering complete solutions to defend enterprises against cyberattacks targeting secret accounts and credentials. Understanding CyberArk basics is crucial for effectively managing and protecting privileged accounts in a company’s network.
As cyber-attacks become more sophisticated and frequent, privileged access must be secured. Its technologies and services let companies discover, manage, and connectsecret accounts and credentials across on-premises, cloud, and hybrid environments to protect their most valuable assets.
CyberArk helps companies strengthen their cybersecurity, reduce data breaches, comply with regulations, and build digital trust and resilience.
This technology allows businesses to manage and defend their privileged access, protecting their most important assets from cyber incursion.Enrol in CyberArk courses to gain a deeper understanding of cybersecurity and learn how to implement secure strategies using CyberArk tools.
CyberArk tutorial for beginners
Privileged accounts are accounts with elevated permissions and access to sensitive information. Eloquent personal accounts have elevated permissions, meaning the password is only known to the user and is used for privileged operations.
Elevated personal accounts are used for tasks such as rebooting a system, running installers, patching servers, making configuration changes, or adding members to a system. Elevated operations involve adding users to a system, running ransomware, or stealing customer or user data.
Private accounts are the most influential accounts in an organisation, giving access to sensitive information. For example, if a team of 10 monitors a thousand servers, they may be reluctant to change their passwords frequently. However, changing a password can be weak, as the hash value is the encrypted value of the password.
After gaining knowledge of the organisation’scritical assets, they shut down all services and ran ransomware to encrypt data and steal information from critical customers. Disrupting the business involves stopping services, running ransomware, encrypting data, and stealing information.
By signing up for CyberArk online courses, you can enhance your skills in cyber security and learn more about the advanced features of the CyberArk software.
CyberArk tutorials
Installing a PVWA application requires a combination of user accounts, system health checks, policies, reports, and domain IDs. By integrating a specific domain with CyberArk, users can log in using their existing domain IDs without creating additional IDs.
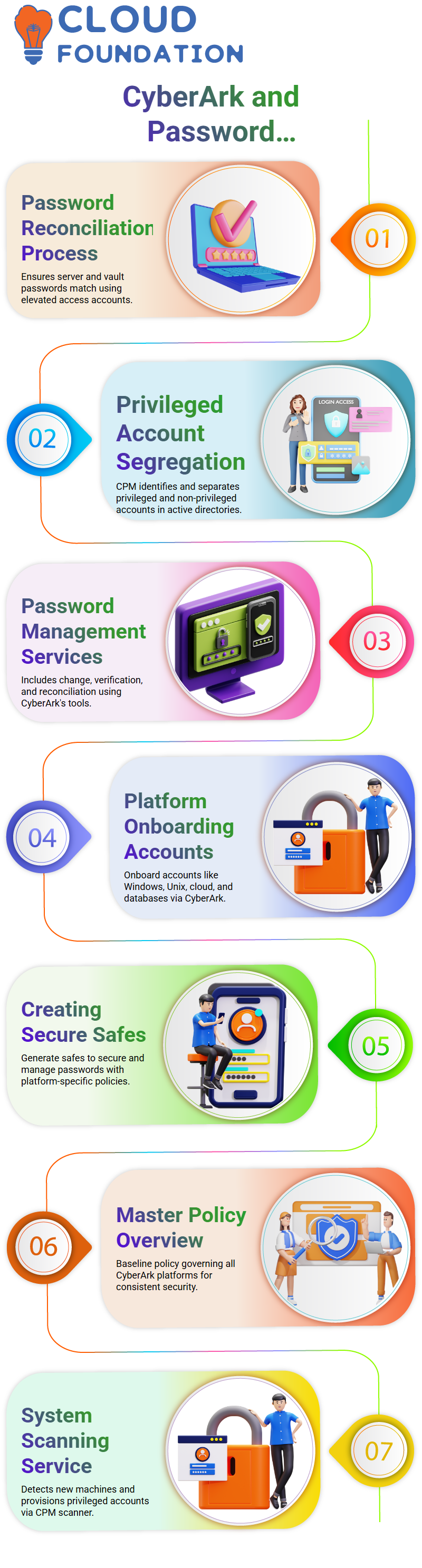
CyberArk is a PAM solution that enables two tasks: password and session management. Password management involves three main functions: verify, change, and reconcile.
The first function checks if the password in the vault matches the password in the target machine. The verification process is successful if the password is the same in both the vault and server ABC. If it differs, the verification process fails.
The second function checks if the password on the target machine and stored in the vault is the same. If so, the process continues to check the string. For example, the process is successful if a deposit is deposited in a bank and there is an entry in the passbook. However, the method may fail if there is an ambiguity in the passbook.
The third function is change. When an account changes its password, it is prompted to change it. This process can be done using alt-ctrl-delete or by pushing alt-ctrl-delete. The CPM then requests the account change its password per the desired frequency, such as every seven days. The updated password will be stored on the server and the cyber app vault.
What is Reconcile?
The reconciliation process is a crucial step in password management, where another account with elevated access intervenes to ensure the same password is available in both the server and vault. This process is essential for ensuring that the password change, verification, and reconciliation work effectively.
What is CPM?
The CPM will identify all privileged accounts in the active directory and segregate them into secret and non-privileged accounts. The account can be deleted or onboarded in cyber out if it is not being used. Cyber acts generate complex passwords, which are vulnerable to cyber-attacks.
Two services are added to the CPM: the central policy manager (CPM) scanner service, which scans the system and allows enterprises to detect new machines and provision privileged accounts, and the password manager service, which is used for change, reconciliation, and verification.
CyberArk is a platform that allows users to onboard various types of accounts, including Windows, Unix, applications, websites, cloud services, and database services. To onboard an account, users must select the appropriate platform and create a safe one. The platform can be imported from the marketplace, a CyberArk repository.
To create a safe, users must create a copyrighted secure and select the CPM to change, verify, and reconcile the password. There are two CPMs available for Windows domain accounts and local accounts. A master policy is the generic policy through which all platforms are governed. It is the baseline policy for any policy.
What is a Policy in CyberArk?
A policy is another requirement for onboarding in CyberArk. A policy is a baseline for something, such as a Windows policy for local, desktop, and domain accounts. For example, if onboarding a Windows account, a Windows policy would be needed for local, desktop, and domain accounts.
Implementing checks-in, check-out, exclusive access, one-time password access, user authentication, session management, session recording and saving, activity audit, and retention period is essential for maintaining security and isolation during mission-critical activities. By implementing these settings, organisations can ensure their systems remain secure and secure for their users.
What is PSM?
PSM is a crucial tool in preventing attacks and ensuring security. It records sessions and activities and acts as a jump server, allowing for the establishment of connectivity from various devices. Organisations need to implement PSM to protect against potential attacks and maintain security.
The PSM server is a Windows server designed for any target machine, including Unix machines. It is intended to connect to any session, whether it’s via PuTTY or PVW. A planning capacity is required before installation, considering the number of users, type of users, and duration of connections. This planning capacity is calculated using the PSM server’s sizing calculation formula.
Prerequisites for the PSM server include the RD Connection Broker and RD Web Access Session Connection. The Windows Server must be a domain server, and the user logged in during installation must be a domain user with local admin rights. These prerequisites ensure the proper functioning of the PSM server and its ability to handle concurrent sessions.
A PSM (Process Server Management) solution’s most important aspect is ensuring that the necessary ports are enabled for each application. For instance, Oracle requires a 1521 port, while MS SQL requires a 1433 port. This port is crucial for session management and password management.

CyberArk Training

CyberArk tutorial on how to onboard a database account
To onboard a database account, follow these prerequisites:
1. Install the database client. This involves connecting the database server to the PSM (Protocol Service Manager) and installing the necessary agents. These agents are required for target machines, such as PuTTY for SSH-based machines, RDP for Windows-based machines, and website browsers.
2. Install the database client into the PSM. Only the legitimate application should be launched from the PSM, as per the role of AppLocker. Whitelist the application from the app locker. The path to the application icon is C drive program file x86, Microsoft SQL Server Management Studio-Common Seven IDE.
3. Whitelist the complete path. This ensures that the application will be launched from the specified location. If the path is not mandatory, update the app locker file with the updated path.
4. Run the app locker script: PSM: configure app locker. This will ensure that the application is launched from this location.

5. Add the PSM shadow user as a legitimate user to launch the application. PSM shadow users launch each local application for the administrator, and as long as they have the rights to read and execute, they can launch the application. Shadow users, appearing in the user’s group only, can launch the application when the administrator tries to throw it or connect to the database.
1. Install the database client.
2. Whitelist the application from the app locker.
3. Update the app locker file with the updated path.
4. Run the app locker script to ensure the application is launched from the specified location.
What is a Cluster Vault?
The cluster vault is a point of contact for all components in a standalone world, such as CPM, PWA, CPM, PSM, and PSMP. It communicates with the standalone production vault, allowing for automatic failover in case of a sudden failure. However, periodic maintenance activities like Windows patches may require a reboot, making failovers necessary.
Clusters have two nodes: primary and secondary. Both can become primary, connected to a public and private network. A VIP points to the active node, ensuring the primary node is accessible. A dedicated drive for restoring saves and other data is stored in shared storage.
To create a cyber cluster, five IPs are required: two public IPs, two private IPs, and one WIP. The shared drive hosts all data and database metadata hosted on the shared drive. The network and storage teams must be involved to simulate a cluster in a lab.
The preferred storage is a shared storage set of fibre channel sand disks, accessible to both the cyber or digital cluster vault node. The shared disk is updated with a single IP address representing a digital cypher or digital vault in the public network organised at TETNOS.
What is a Break-glass approach?
The break-glass approach is crucial in ensuring the recovery of the CyberArk environment in a catastrophic situation. By leveraging the backup data and the administrative level account, end users can continue working and ensuring the continuity of their operations.
The concept involves creating a break glass account with all admin privileges on servers, databases, and websites and onboarding it with the group policy. All break glass accounts have a common password, and any group of custodians can access them.
The breakglass account is always onboarded with a no change policy, as changing it would result in no access to the correct password for the custodians.
What is a CyberArktool tip?
The tool tip is to notify the end user of any changes in the script, labelling them on the screen. Complex code the address as a global constant and set it as the URL. The script will fetch the required details from the vault, such as the password and user name.
The target address might not be necessary, but it could be used for other purposes, such as fetching specific port details or strings.Attending the CyberArk Defender Training has greatly enhanced my skills in protecting sensitive data and privileged accounts.
What is an app locker in CyberArk?
The app locker is a tool that whitelists applications added to a file, updating them into the app locker of a Windows server. Shadow users can launch applications on their behalf, and any files, paths, or publisher items in the app locker are added to the component folder. This folder contains connectors and exception lists for shadow users to use.
There are three types of entries in the AppLocker file: publisher, trusted application, and direct executable. The publisher is the trusted application, and the path of the application is where the executable is located.
If there are dependencies for an application, such as a NET framework or a NET application, they need to whitelist the path of that application. For example, to open a SCP, they need to whitelist the NET framework or application path.
If they need to whitelist any executable directly, they must whitelist the Txt file.
What is CyberArk tool &What is CyberArk used for?
CyberArk is a shield that can help prevent several types of cyber-attacks. However, there is no shield in place to protect against penetration attacks. If a password is compromised, the compromised password could lead to the loss of sensitive information.
To protect against these attacks, it provides a shield to prevent intruders from entering the network. By implementing this IAM, organisations can protect against these types of attacks and ensure the security of their infrastructure.
By learning CyberArk’s cutting-edge technology and training resources, I have quickly become an expert in securing privileged accounts.
CyberArk tool tutorial | What is CyberArk Software?
CyberArktool is a web-based authentication system that allows users to connect to servers without knowing their password. This is a significant improvement over shared accounts, where multiple people can access the same assets. The system differs from interactive access, where users punch in their username and password, and non-interactive access, where the password is unknown or not shown.
The basic idea behind CyberArk is that it allows users to connect without knowing their password, ensuring that the system is secure and secure. The system is not yet fully built but will be tested and demonstrated in a future environment.
Cyber ark tool
The CyberArk layer is a security layer that allows users to authenticate to various systems, including databases, servers, firewall devices, and websites. CyberArk injects credentials into the target system, preventing credential theft, surveillance, dummy IDs, and shadow IDs. It also maintains SODs and prevents privilege escalation, as it only grants legit access to the target system.
The CyberArk layer also addresses PTH attacks, which involve weaker passwords. Once a user logs off from a server, the password is rotated, ensuring the complex hash value is not compromised. This is different from traditional methods like Quartet or QAZ WSX, which are known passwords or guessable company names.
This tool generates complex passwords, making it difficult for attackers to break them. Additionally, the password is not static; it rotates every time a session is initiated. Overall, it provides a robust security layer for users accessing various systems.
CyberArk certification training includes clear concepts
One of the most demanded certifications, which mainly focuses on CyberArk PAM, this section is a small CyberArk PAM tutorial that covers the basics of PAM.
PAM solutions, such as CyberArk, Beyond Trust, etc., have two key objectives:
- Session management
- Password management
Session management allows connecting to any target machine, regardless of its nature, including on-premise applications and cloud-hosted systems. Password management, however, enables the hashing of passwords for any target system.
PAM is the preferred term for all privileged access management, and understanding PAM terminology is essential for studying other PAM tools like BeyondTrust or HashiCorp.
The use cases of PAM tools remain the same, with CyberArk being the top choice due to its numerous features and global footprint.
It has been a global leader for seven years, with all BFSI domains, including pharmaceutical domains. Platforms like Marketplace allow users to import items from CyberArk offerings.
However, PAM solutions face financial losses, brand damage, business continuity damage, and regulatory penalties. Organisations must implement PAM solutions according to norms to avoid financial losses, brand damage, business continuity damage, and regulatory penalties. For example, organisations in Europe, America, and India must implement PAM solutions to avoid penalties.
What is included in the CyberArk Pam tutorial?
CyberArk is a PAM tool that helps safeguard privileged credentials.
It includes an enterprise password vault, which can protect three types of privileged accounts: personal, shared, and application-privileged accounts.
And also aims to help organisations safeguard their privileged credentials by providing tools to handle different secret accounts.
Enterprise password is a core component of CyberArk, storing all credentials for an organisation’s various devices, including corporate LinkedIn, Facebook, and Instagram pages.
It is stored in the enterprise password vault (EPV), a Windows server with layers of security. The vault safeguards all credentials, including the password, and encryption occurs once the password is in the vault.

CyberArk Online Training

CyberArk training and certification can include the following topics
The PSM is designed to protect against parameter compromises, ensuring that only authorised users can access the target system. For example, an IT professional can connect to a Unix or Windows server using MSDSC without having 3389 connectivity enabled. The PSM retrieves the credentials of the account they want to connect to the Windows server and injects them into the server.
The PSM records all activities, including changes in the server, visual recordings, audit logs, and keystroke logins, preventing any mischievous activity on the target machine. It also restores the tapes to the vault, ensuring that any previous recordings are reviewed and tracked.
PSM (Process Service Management) has a counterpart called PSMP, which allows users to initiate and record a PuTTY session. It offers benefits such as connecting to multiple target SSH-based devices without hard-coded credentials.
Privileged session management (PSM) is discussed in detail, focusing on the different ways to access target systems through the PVW.
PSM is a jump server that establishes connectivity from the workstation to the target system, preventing any direct connection to the target system. This is particularly important for IT professionals accessing various target systems daily.
What can you learn in the CyberArk tutorial?
The central policy manager (CPM) is an integral part of PAM, performing password management. It interfaces between target machines and the vault, verifying the password and ensuring it is correct. The CPM performs three main functions: changing passwords, confirming passwords, and reconciling passwords.
Application identity management replaces hard-coded credentials in scripts with function calls, ensuring that scripts do not have any hard-coded credentials. CyberArk safeguards these credentials by providing usernames and passwords for the scripts. This ensures that the scripts do not have any hard-coded credentials.
A disaster recovery vault is a mirror image of an enterprise password vault, replicating data from production to the recovery vault in case of a data centre failure. The event notification engine is a service that CyberArk runs, allowing users to be notified of events like a production site downtime via SMTP or Outlook.
What is focused on CyberArk pas administration training?
CyberArk pas administrator training mainly focuses on Vaults.
CyberArk is a Windows-based system focusing on the Vault, the core of alldeployments. The Vault contains various safes, which are similar to lockers in a bank. Each locker has its key, and only legitimate users can access it.
This is known as the segregation of duties. In CyberArk, each safe has its dedicated member, ensuring that only legitimate members can access the accounts onboarded in their safe.
The CyberArk vault has two keys: the customer and the bank keys. The customer key is for accessing the locker, while the bank key is for accessing the account.
Only the legitimate user can access the locker. For example, if an account is onboarded with the password “vivo” (123.), only the Wintel people can access it.
Cyber security is critical to cyber operations, ensuring accounts and data security. The vault serves as a storage engine for all aspects of cyber operations, from onboarding to backups and integrations.
The vault installation requires several steps, including the setup, license file, operator CD, and private R client. By following these steps, the vault can be successfully installed and configured.
Installing a vault involves taking over the firewall, which currently has only a few rules. The allowed traffic is limited to the 1858 port and ping, the main port of cyber deployment. Adding any traffic to this console’s vault server will be impossible.
Installing a vault involves a complete takeover of the firewall, limiting the allowed traffic and ensuring that only the administrator is accessible.
The vault interface has certain services added and disabled, while the configuration file for the vault is limited to 1858.SNMP traps and other technologies to monitor and manage the server parameters in a vault environment.
CyberArk full course mainly focuses on the installations
The document provides a step-by-step guide on how to install a VMWare instance on a new server.
To create a domain server or domain controller, follow these steps:
1. Go to the server manager dashboard and add rules and features.
2. Download the server and initialise the service.
3. Validate if the static IP is still present and update it.
4. Make the static IP 155 and mark it as loopback.
5. Click on add rules and features to install the features.
6. Choose to make the server an ad server or domain controller.
7. Click on server rules and select active directory domain services.
8. Click on the add feature and restart the destination server.
9. Click Install and specify the active directory name.
10. Promote the server to a domain controller.
There are three options: add a domain controller to an existing domain, add a new domain controller to an existing forest, or create a new one from scratch.
How to Learn CyberArk?
For any technology, we need to start by understanding the basics. The same goes with CyberArk as well. Learn basic concepts and how it is used in IT security.
Attend training to get some basic idea on how to learn this IAM technology and to get hold of its basics.
You might be asking if there is any CyberArk free training to learn. Few organisations provide courses.
Where to get CyberArk training?
You can find various sources such as CyberArk training provided by the organisation, third-party vendors and various online courses.
You can even find CyberArk certification courses according to your requirements, and it will be an added advantage in your resume once you get trained.
Trainings are offered in three modes:
Self-paced training, where a learner needs to spend time learning through a set of CyberArk training videos and a tool to practise.
Online Instructor-Led training, where a professional trainer certified in this technology will be your tutor to teach all the essential concepts.
Corporate training is where an organisation benefits from CyberArk corporate training by third-party vendors for implementations or to give their employees hands-on practice.
CyberArk training cost depends on the mode of training you opt for at the third-party vendors. CyberArk training online will be affordable, and you will have enough flexibility to choose a particular time to learn this course.

CyberArk Course Price


Harika
Author