Cloud Security Tutorial
What is Cloud Security?
Cloud security is an integral component of any organisation and must be effectively managed and protected – this includes taking measures such as posture management to address this often neglected aspect.
By prioritising these areas, organisations can create a secure environment for their users while improving overall security posture.cloud services should have mechanisms in place that can quickly recover from errors or failures to maintain trust among customers while protecting against unauthorised access.
Companies need to prioritise privacy and security within their operations in order to provide their users with peace of mind. Cloud security employs object storage that stores user data securely at rest while remaining encrypted at rest.
Data stored herein can then be utilized for data and transactions that are sent over secure protocols like PLS or HTTPS, protecting personal information while simultaneously offering resilience against failures and errors in cloud services.
Resiliency refers to protecting activities while privacy safeguards information regarding activities conducted online while privacy provides protection for activities performed while resilience enables cloud services to recover quickly in case failure or error arise.
Security in the cloud is equally essential to its viability, with concepts like confidentiality, integrity and availability all playing an integral part. They ensure the safekeeping and integrity of cloud-based apps and their contents.
Cloud security involves object storage, which secures data at rest by encrypting everything stored therein and later used for transactions through secure protocols like PLS or HTTPS.
Privacy refers to safeguarding of information and activities, while resilience ensures cloud services can quickly rebound after mistakes occur.
Cloud Control Matrix (CCM)
CCM stands for Cloud Control Matrix while Star Audit refers to an audit cloud control matrix used for auditing data. CCM and Star Audit play an integral part in Cloud Security Alliance methodology which strives to protect user information.
Control Metric in Cloud Security
Control metrics are an established measure in cloud security that assess an organization’s security posture across different subdomains.
Organizations use effectiveness matrixes to assess their security standards and measure how well they meet client needs. Cloud auditing organizations will find this matrix especially essential.
Controlmetrics assists businesses in understanding the significance of regulations and the need to adhere to them in order to deliver services which fulfill customer demands and satisfy regulatory compliance. Dienstleister must abide by these laws if they wish to meet customer demands effectively and meet them successfully.
Cloud computing in Cloud Security
Cloud computing refers to the delivery of computing services over an online network to a remote customer without needing physical on-premise infrastructure.
Application-centric deployment entails creating applications and deploying them on servers rather than creating servers from scratch themselves, giving customers more freedom in developing and deploying applications on servers without creating physical machines themselves.
Cloud computing can eliminate some of the barriers associated with accessing additional computing resources. By drawing a diagram, it allows users to visualize an application deployed in the cloud and observe its functionality within an inaccessible environment.
Cloud computing involves complex hardware and infrastructure needs that must be carefully planned out, procured, and managed for success. Hardware specifications, purchasing components necessary, and overseeing all aspects of cloud computing are integral parts of success in cloud computing environments.
Cloud computing is an evolving field that offers numerous benefits and advantages, revolutionizing how we interact with data, collaborate across devices, and share information across devices. However, deployment an application on cloud computing may prove challenging for those unfamiliar with its nuances.
The six security concepts relevant to cloud computing:
Encryption access control,
Data
Media sanitisation
Network security virtualisation security
Common threads
Cryptography
Cloud Security Services
Cloud security refers to the implementation of security standards for various cryptocurrencies. These standards address multiple areas, including cryptocurrency security, which is a security standard comparable to ISO 27001. These standards address a different location, which is the cryptocurrency security standard.
Considerations for cloud security depend upon the service model being deployed – software as a service (SaaS), platform as a service (PaaS), or infrastructure as a service (IaaS).
Software as a service (SaaS) involves transmitting encrypted data over a network and then using that information to develop applications which operate over this same network.
 Application security is safeguarded against foreign attacks such as simple injection, cross-site scripting and cloud attacks by taking precautionary steps that protect it against compromise.
Application security is safeguarded against foreign attacks such as simple injection, cross-site scripting and cloud attacks by taking precautionary steps that protect it against compromise.
Platform-as-a-service (PaaS) platforms enable organizations to manage application resources while staying current with security best practices.
The deployment process also serves to verify that all networks are correctly configured with backups and replication plans in place.
Studies are performed to ensure all host machines contain the latest operating systems and security patches installed.
Platform as a Service(PaaS) and Infrastructure as a Service (IaaS) may be suitable options, however other factors must also be taken into account, including cost, performance, reliability of service.
Advantages of Cloud Computing
Cloud computing brings many benefits for businesses. One key benefit is being able to deliver computing services over an online network and making them easily available anywhere customers may be, making computing services easily accessible from any location. Businesses using this approach have seen costs reduced dramatically while increasing overall efficiency.
Cloud computing services offer businesses cost-efficient options to develop and connect remote systems via the internet, helping reduce hardware expenses while creating and maintaining stable network infrastructures.
Cloud computing allows anyone accessing services at any time and from any place – no matter their time zone or physical location – making it ideal for businesses that rely on remote operations for operations and operations management. Cloud computing offers flexibility.
Users have access to services at any time and from anywhere – making this flexibility especially helpful in responding to changing time zones and unexpected circumstances.
Cloud Security Alliance in Cloud Security
The Cloud Security Alliance has identified nine of the most serious cloud threats as defined by them CSC as common threads such as UH security stretch which make up what are commonly referred to as the Notorious Nine (NC9).
Common threads UH security stretch are utilized in cloud computing environments to gain access to virtual environment data and resources.
The Alliance methodology emphasizes the significance of maintaining an effective security posture across various cloud platforms and technologies, taking account of different platforms and technologies. By employing vertical and horizontal scaling strategies to implement in their business systems, businesses can ensure optimal performance of systems while mitigating potential issues that might arise from cloud services.
By prioritizing security, businesses can ensure their systems can handle increased workload and maintain competitive edge in the market.
Scalability in Cloud Security
Scalability is another essential feature of cloud computing. Before becoming cloud users, users were forced to purchase and configure resources themselves manually – an process which took considerable time and resources.
Through cloud computing users can instantly add resources as required or remove them as soon as they no longer require them.
This method works quickly, relieving you from any worries about disposing of resources in an efficient fashion.
Two ways of scaling
Horizontal scaling
Vertical scaling
Horizontal scaling: Addition involves increasing the size of an existing server pool by increasing their number, such as through adding extra servers into it. A load balancer with three servers could handle this increase quite efficiently.
Horizontal scaling makes adding and removing servers easy; should a user not wish to add anymore servers they simply cease doing so.
Vertical scaling: Vertical scaling involves adding resources to an existing server, such as increasing RAM memory or utilising more powerful processing chips; or replacing hard drives with solid state drives (SSD). Vertical scaling entails expanding upon and upgrading an already established infrastructure.
Vertical scaling involves adding more resources, like RAM memory modules or solid state drives to an existing server – for instance RAM expansion or better processing chips – so as to better handle workload.
Blockcha in technology in Cloud Security
Blockchain technology boasts high levels of integrity and has found widespread application, from cryptocurrency such as Bitcoin to building solutions on AWS or Azure which mimic Ethereum blockchain architecture.
Connectivity for non-traditional devices used for network data collection. Examples include Amazon Echo and Google Home smart speakers.
Blockchain technology provides an efficient, safe solution for managing data integrity across distributed, decentralised ledgers.
Block storage in Cloud Security
Block storage can be an invaluable way of safeguarding data security. By employing various encryption techniques and fine-grained control measures, users can strengthen their own security measures while guaranteeing an environment free from insecurity for their files.
Block storage is an alternative data storage strategy which uses multiple servers linked together in one data disk for long-term data retention and protection.
These servers use BitLocker encryption, to keep data protected while in transit and at rest. AES or alternative encryption techniques (BitLocker encryption, for example) may also be utilized as necessary for data security.
Block storage can be utilized in numerous circumstances, from protecting data at rest and in transit to keeping files on dedicated drives safe from being compromised.
Encryption in Cloud Security
Encryption is the process of changing human-readable information into something indecipherable by end users and back again; decryption reverses this process for subsequent viewing by returning it back into its original form. Cryptography involves both encryption and decryption processes with key management being an essential element in both processes.
Encrypting data is an integral component of modern technology, but it also presents numerous obstacles. One key concern lies with potential key loss; therefore key management must be centralised so all resources’ keys can be kept safely stored together in one centralized place.
By doing this, no third parties are able to decrypt your messages or packets – providing another level of protection.
Virtualisation security in Cloud Security
Virtualisation security is an integral component of modern technology that must be prioritized accordingly. There are various considerations which must be met before moving forward with virtualisation solutions.
Cryptography, an increasingly-important element of data security, plays an integral part. Encryption keys play an integral part of virtualisation security – an intricate process which must take careful account of various factors to be effective.
By default, cloud setups permit outgoing traffic from trusted cloud resources; it is still wise to be wary of potential flaws and ensure all necessary security measures are implemented and properly applied.
 By understanding their security needs and concerns, users can create an efficient environment for their applications. Virtualisation Security comes with its own set of considerations including hypervisors and post-operating systems that need to be secured properly.
By understanding their security needs and concerns, users can create an efficient environment for their applications. Virtualisation Security comes with its own set of considerations including hypervisors and post-operating systems that need to be secured properly.
Always remain aware of security flaws, such as their possible impact on host hypervisors when connecting virtual machines to hypervisors. Even when using containers, security needs must be carefully considered.
Virtualisation security threats include DoS attacks, post-traffic interception and VM jumping – each capable of impacting guest operating systems running atop of hypervisors resulting in serious implications for cloud service providers.
Secure interfaces in Cloud Security
Secure interfaces are key when working with customers on on-premise systems, requiring proper authentication and authorisation processes for proper integration.
API security should always come first and must not be taken for granted; its importance lies in assuring integrations remain safe while APIs do not become vulnerable.
Security controls must be in place in order to properly secure API connections as these may also be utilized by other systems, including UH. Automated platforms using specific monitoring tools may offer access to APIs.
Software as a Service (SaaS) in Cloud Security
Software as a Services (SaaS) is an approach to cloud computing that makes software apps available online through subscription to customers via an external provider, often via subscription payment models.
This approach allows users to gain access and utilize software without being concerned with updates, maintenance or installation processes.
Software as a Service (SaaS) refers to any service which allows users to easily access and utilize software applications for specific uses – for instance Google Drive, Outlook Mail, Yahoo Mail, OneDrive and Dropbox are examples. All these services can be found over the internet via email, instant messaging services such as social networks such as Facebook as well as text-messaging programs like AIM (instant message service).
Security in wealth management apps is of utmost importance in any business, especially software as a services (SaaS) providers. imunitar The measures implemented within an app’s security measures aim at safeguarding data against unauthorised access and keeping its integrity undamaged and undisturbed.
Conclusion
Cloud security has become an essential element of modern businesses, protecting sensitive information while guaranteeing the availability and integrity of cloud services.
By placing emphasis on encryption, data privacy, and resilience measures, organizations can build sound security frameworks that reduce risks while building user trust.
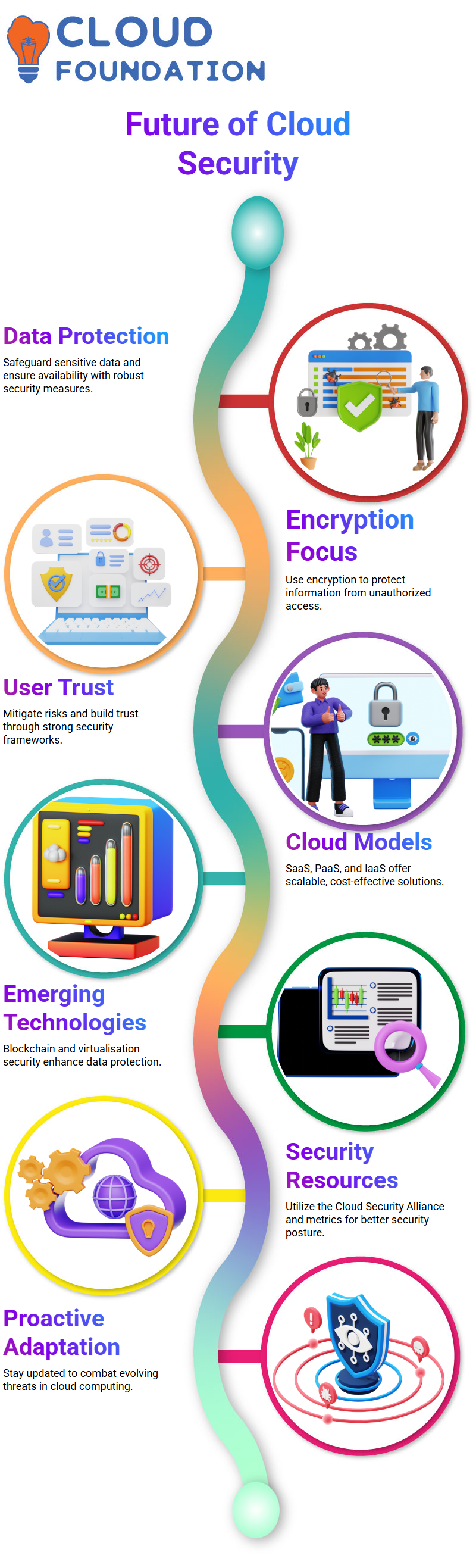
Cloud Security Alliance and control metrics provide invaluable resources for assessing and improving a security posture, while SaaS, PaaS, and IaaS cloud models offer cost-effective scalable solutions suitable for businesses of any size.
Emerging technologies such as blockchain and virtualisation security continue to shape the future of cloud security, opening new avenues for protecting data and strengthening system integrity.
As cloud computing advances, so must our security strategies; businesses should remain proactive and adapt quickly to address new risks or opportunities that emerge in this ever-evolving ecosystem.

Vinitha Indhukuri
Author



