Workday P2P Tutorial on Bank Account and Payment Processing
How Companies Can Simplify Bank Account Setup and Payment Processing in Workday P2P
In today’s fast-paced business environment, efficiently managing settlements and payments is crucial.
Companies need a structured process that ensures payments are accurate, timely, and secure.
The following guide outlines the steps involved in executing a settlement run—from setting up a company’s bank account to implementing payment routing rules—ensuring smooth financial operations.
Step 1: Setting Up the Bank Account
The foundation of any settlement run begins with creating a bank account for the company.
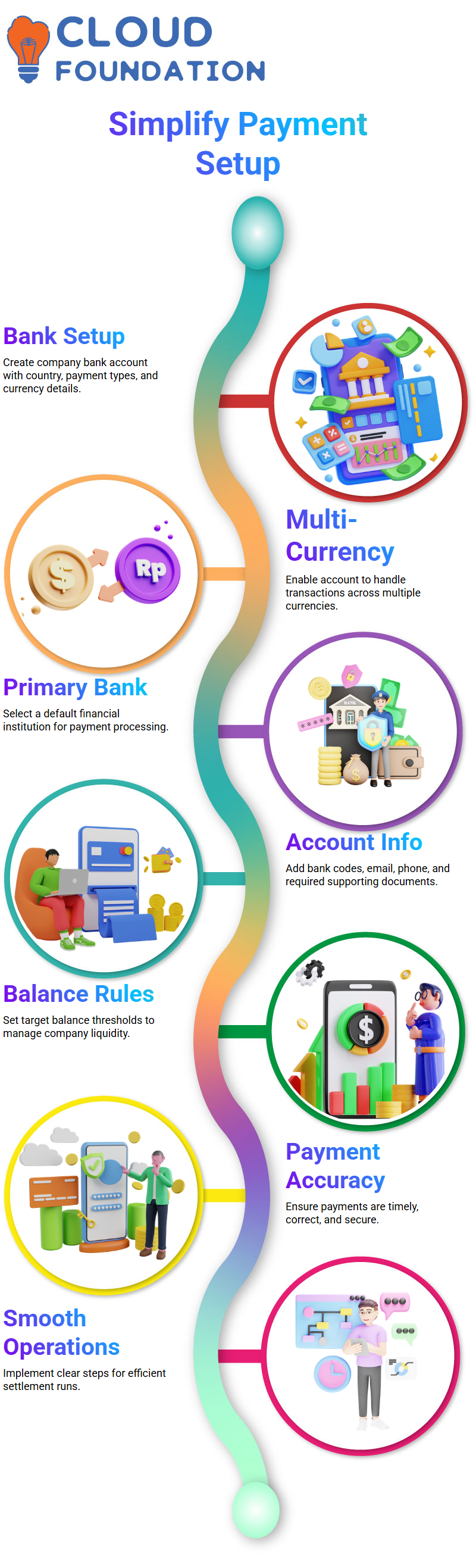
For example, a bank account named “Tara” can be created, with details such as country, payment types, and supported currencies defined.
Key points in this setup include:
Multi-currency support – allowing the account to accept transactions in various currencies.
Default financial institution – selecting a primary bank for processing payments.
Detailed account info – including bank codes, email, phone numbers, and supporting documents.
Target balance settings – establishing thresholds (e.g., 25,000 units) to manage liquidity.
This structured setup ensures the company has a reliable foundation for handling financial transactions.
Step 2: Configuring Payment Rules and Processes
Once the bank account is active, companies must define bank routing rules and payment categories. These rules govern the processing of various types of transactions, ensuring that funds flow correctly and securely.
For example:
Supplier payments – categorised by supplier type and amount.
Expense payments – managed under a separate set of rules.
Way accounts – configured to prevent misrouting of funds.
By applying filters and categories, businesses reduce errors and ensure payments don’t end up in the wrong hands.
Step 3: Settlement Runs and Payment Scheduling
With accounts and rules in place, companies can initiate settlement runs—the process of batching and executing payments.
Highlights include:
Payment scheduling – defining processing timelines (e.g., nine days to complete a payment cycle).
Flexible invoice handling – allowing users to add, remove, or adjust supplier invoices.
Discount management – enabling businesses to optimise payment terms.
A completed settlement run provides real-time updates, helping finance teams confirm that payments were processed accurately.
Step 4: Leveraging Print Check Work Areas
Even in an era of digital banking, many companies still require print check processing for specific transactions. The system allows users to:
Generate checks for manual payments.
Track large payment volumes.
Refresh and monitor the check status.
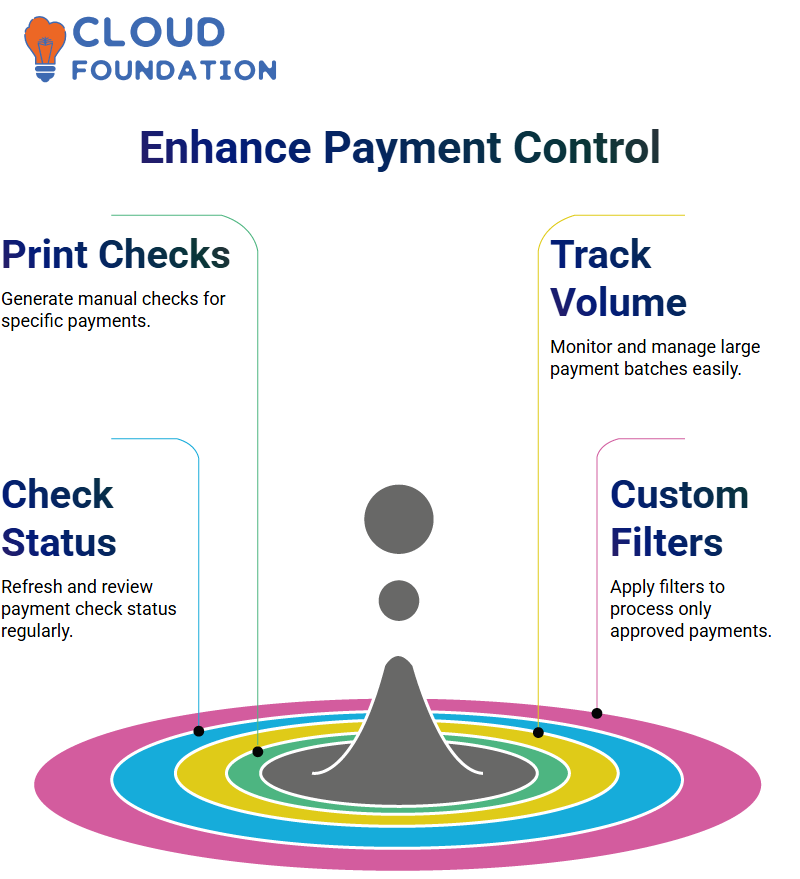
For example, a company may need to conduct an extensive daily review of recurring expenses. With a dedicated print check work area, finance teams can easily track, verify, and report these payments.
Step 5: Custom Filters for Enhanced Control
One of the most powerful features in this payment system is the ability to create custom filters. These filters help businesses:
Ensure only approved supplier payments are processed.
Flag unusual or missing payments.
Maintain complete control over payment visibility and reporting.
This functionality ensures accuracy, transparency, and compliance across the payment lifecycle.
Workday Mastering Role Management and Security in Legacy Systems
Managing roles and security in a company’s legacy systems can often seem daunting. With multiple teams, departments, and business processes, assigning the right roles to the right people is critical for operational efficiency and data security.
In this guide, we’ll explore a structured approach to role creation, security group management, and domain-specific access in legacy systems.
Understanding Role Creation in Workday
The process of creating roles begins with gathering the correct information. This includes:
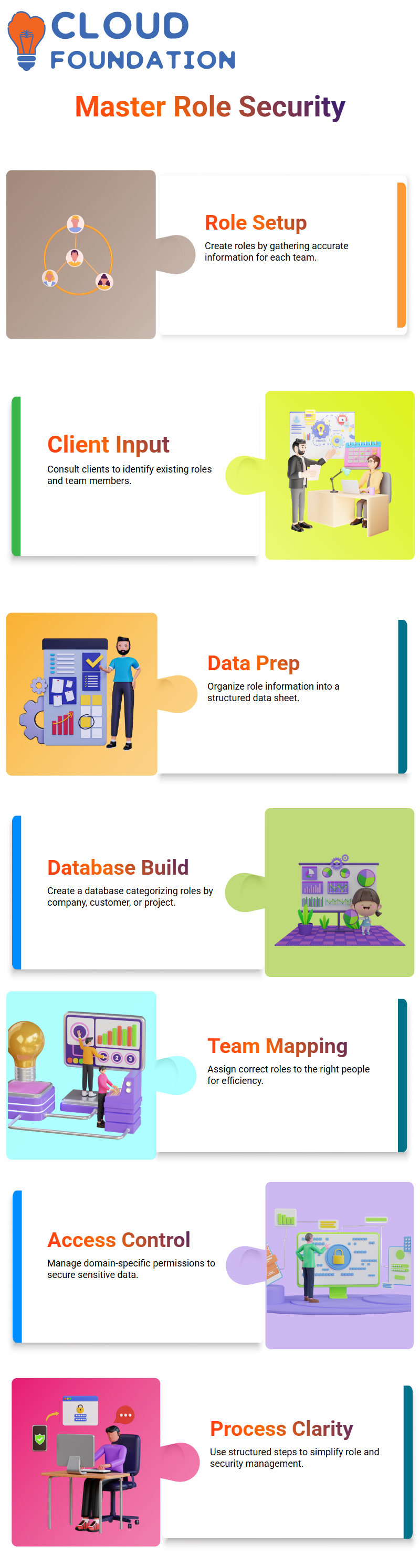
Client Consultation: Understand how many security roles currently exist and who is part of which team.
Data Preparation: Compile the information into a structured data sheet.
Database Setup: Build a database to categorise roles based on company, customer, supplier, or project.
Each role is defined using key attributes:
Self-assign Permissions: Determines if a user can assign the role to themselves based on HR privileges.
Security Assignment: Restricts a role to specific business processes or single-person assignments.
Visibility Controls: Roles not yet assigned can be hidden to reduce clutter.
Supporting Roles: Specifies whether a role belongs to leadership, accounts, IT, operations, or none.
This meticulous setup ensures that roles are assigned and managed appropriately, maintaining both operational efficiency and security.
Role-Based Security Groups in Workday
Once roles are defined, creating security groups in finance or administrative systems becomes essential. Security groups enable companies to control access and prevent failures caused by misassigned permissions.
Key aspects include:
Group Types: Role-based groups, constraint (limited access), or unconstructed (unlimited access) groups.
Access Rights: Options like current organisation only, company hierarchy, or subordinates define the scope of access.
Assignments: Roles are generally assigned to positions, while super admin groups are assigned to users.
Understanding the distinction between role-based groups and super admin groups is crucial. Role-based groups focus on task-specific access, while super admin groups manage overarching system permissions.
Domain and Business Process Security in Workday
Access to tasks, reports, and data sources is often controlled by domain and business process security:
Domains: Represent specific areas in the system, granting access to tasks and reports.
Business Processes: Include sequential steps like initiating initiatives, reviewing submissions, and approving actions.
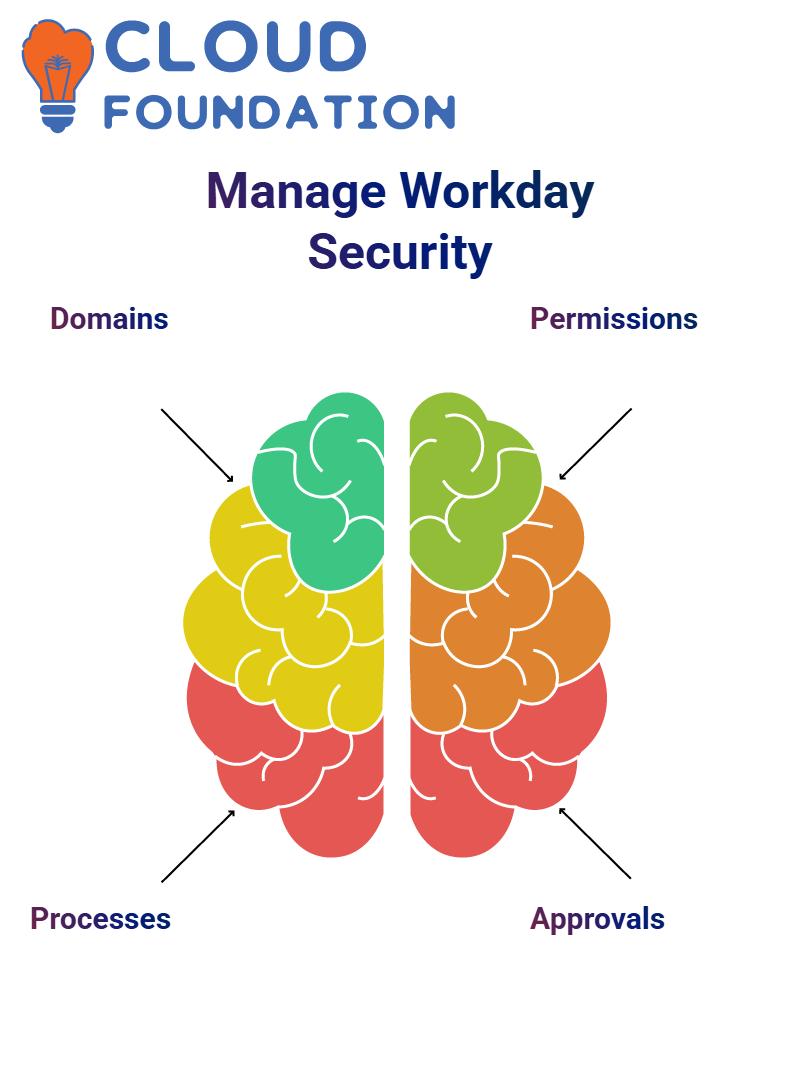 Parent-Child Permissions: Access defined at a parent level can automatically propagate to child levels.
Parent-Child Permissions: Access defined at a parent level can automatically propagate to child levels.
For instance, creating a supplier in a “Westwood” domain requires configuring both domain access and the associated business process. This ensures that only authorised users can perform sensitive actions.
Managing Security Policy Changes in Workday
Security is not static. Changes to domains, business processes, or roles require careful activation:
Pending Changes: All updates are recorded but inactive until explicitly activated.
Approval Workflow: Each change must be justified (e.g., client request, internal review).
Activation: The system activates the change, and relevant stakeholders are informed.
This process ensures that changes do not disrupt operations or compromise security.
Common Challenges and Lessons Learned
Even with structured systems, issues can arise:
Task Visibility: Sometimes reports or tasks don’t refresh correctly, possibly due to flag or contract issues.
Condition Rules: Certain rules might not appear as expected, requiring troubleshooting or manual adjustments.
Interview Preparation: Understanding these processes is essential for employees, especially during interviews or performance reviews.
Learning from experienced colleagues and thoroughly documenting processes can help mitigate these challenges.
Streamlining Supplier Invoices and Business Processes in Workday
In today’s fast-paced business environment, managing supplier invoices and maintaining efficient business processes is critical for organisational success.
Modern platforms provide a range of tools to simplify these processes, including configuring home pages and approval workflows, as well as managing supplier data and generating custom reports.
Let’s explore how to leverage these tools to optimise your operations effectively.

Workday Online Training

Building a Customised Supplier Invoice Platform in Workday
Creating a supplier invoice platform starts with defining key elements such as platform photo, ID, language, and functionality.
The platform is accessible via a URL, allowing external stakeholders to interact with your system securely. Key customisation options include:
Branding and Analytics: Add your company’s branding and integrate Google Analytics tracking to monitor usage.
Landing Pages: Configure confident landing pages to guide users efficiently.
Home Page Configuration: Personalise the home page with welcome messages, supplier codes, left content sections, conveyors, and RFQs (Request for Quotations).
You can define links, titles, and text for each component and restrict access to specific companies as needed.
These initial steps lay the foundation for a structured and user-friendly supplier invoice system.
Customising Business Processes in Workday
One of the most potent aspects of modern supplier platforms is the ability to tailor business processes to meet specific needs.
By default, all companies in a tenant may follow a standard workflow, but customisation is crucial when:
A company has unique requirements.
Specific units or hierarchies need different approval rules.
Using the platform’s interface, you can copy an existing business process and define rules for your company, including review times, task durations, and hierarchical consistency.
This ensures that all entities within a company hierarchy follow the same process while still accommodating exceptions when necessary.
Managing Steps and Approvals in Workday
Business processes typically involve multiple steps, such as initiation, tracking, applying rules, and creating receipts for purchase orders. Steps may include:
Action Steps: Required for specific tasks in a workflow.
Approval Steps: Ensure compliance with internal policies and supplier requirements.
Chain, Batch, Drop, and Consultor Steps: Used for complex, multi-step workflows.
The system automatically checks for step order, highlighting discrepancies and guiding users to correct sequences.
Custom conditions, such as payment terms or supplier classifications, can be applied at specific steps to maintain compliance and streamline the approval process.
Handling Exceptions and Violations in Workday
Business processes are not always straightforward. Exceptions, such as restricted access to hidden reports or inability to copy supply data, can occur. To address these, the platform allows:
Text-based reading products to resolve inconsistencies.
Relationship rules to ensure proper task flow.
Condition rules to flag missing or incorrect data entries.
This proactive approach minimises delays and ensures that business operations proceed smoothly even in the presence of exceptions or custom violations.
A critical component of managing suppliers is practical reporting. Tools like the Cal field enable users to:
Look up supplier addresses, primary or email.
Fold data for multiple suppliers in a single report.
Compare fields and generate custom reports for specific supplier insights.
Practising with long-term requirements (LREs) and consistent reporting ensures accuracy and familiarity with these tools, even in complex scenarios involving multiple suppliers or large organisations.

Workday Course Price


Vinitha Indhukuri
Author
