Microsoft Azure AD Training Courses
Azure Active Directory
Azure Active Directory plays an indispensable role in user authentication and access control. When we register for Multi-Factor Authentication (MFA), Microsoft Authenticator is often the default solution.
However, Azure Active Directory allows for flexibility. If someone prefers Google Authenticator during registration, they can opt in, making Azure Active Directory an extremely versatile authentication solution.
Microsoft Azure Active Directory serves as the foundation of authentication and access management within its ecosystem, serving every application that requests user data through it to ensure a secure environment.
Microsoft does not give third-party applications direct access to user accounts through Azure Active Directory; instead, they rely on the Graph API as an intermediary service to securely retrieve and deliver data to applications.
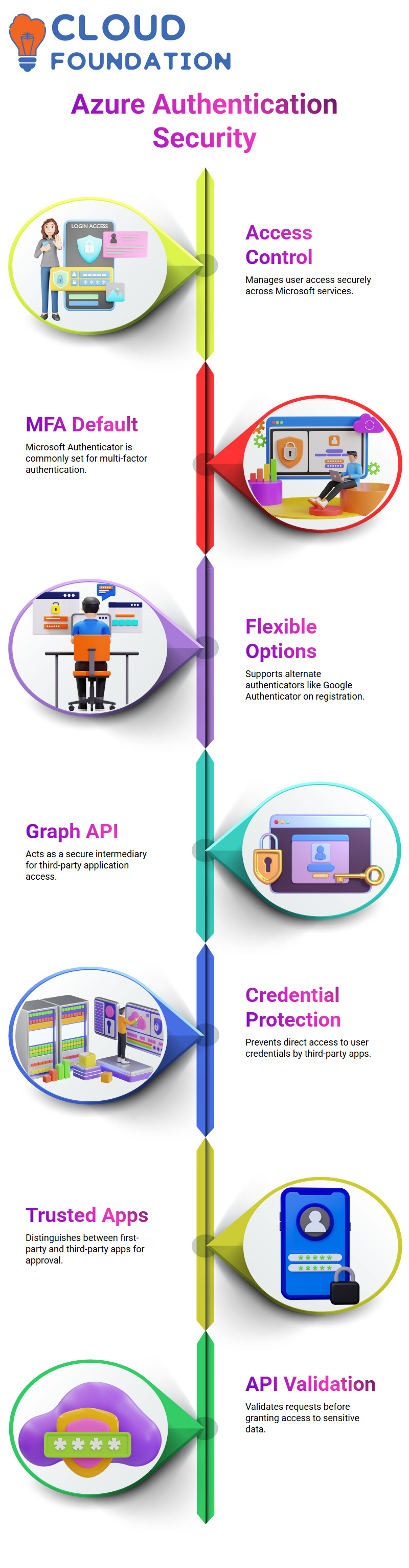
This ensures no outside application can directly interact with user credentials without first going through Azure Active Directory.
Security in Azure Active Directory
Security is of utmost importance in Azure Active Directory, where the platform distinguishes between trusted first-party applications, such as Outlook, and those requiring explicit admin approval, including third-party applications that must undergo access approval procedures.
First-party apps, such as Outlook, can be trusted, while third-party ones must undergo strict approval procedures before being added as trusted first-party programs.
Microsoft enforces a policy that requires requests from third-party applications to be made through APIs and that Azure Active Directory must validate these requests before granting access, thereby preventing unapproved apps from accessing sensitive information.
Security Features in Azure Active Directory
Azure Active Directory’s Security Centre provides an assessment platform to gauge the safety of your environment.
Working in tandem with Microsoft Defender, this feature generates security insights and recommendations.
Organisations can monitor their security score within Azure Active Directory and take measures to increase it, helping ensure compliance and minimising vulnerabilities.
These insights enable organisations to take immediate steps toward greater protection.
Azure Active Directory Authentication
A QR code to log into an application; its certificate connects with Netflix’s servers to generate a session key that verifies you as an authorised user before giving access.
Ultimately, this authentication process ensures you get access. Azure Active Directory plays a crucial role in authentication.
When scanning a QR code to log in, Azure Active Directory acts as an intermediary between your device and the service, ensuring secure access and confirming user identities using authentication tokens passed through Azure AD.
Authentication and Authorisation in Azure Active Directory
An authentication endpoint in Azure Active Directory initiates authentication immediately. Here, you will need to provide your username and password before we can start verifying your identity.
Azure Active Directory’s token endpoint requires the application’s client secret value for authentication before issuing an access token on behalf of users (this token belongs to the application, not the user directly).
Once verified by Azure AD, an access token for the application, issued directly by Microsoft Azure AD, should appear for the user. Note: Remember that this token belongs directly to the application.
Three-step process: first, authentication; then, token issuance; and thirdly, authorisation.
Azure Active Directory rigorously verifies whether the token issued to you is valid before permitting access to specific resources; otherwise, an application won’t grant entry.
As we progress further into Azure Active Directory’s token configurations, API permissions, exposing APIs and application settings, we will also explore its conditional access policy (CAP) and security configurations.
 Multi-factor Authentication (MFA) is another key aspect of Azure Active Directory that reinforces security measures.
Multi-factor Authentication (MFA) is another key aspect of Azure Active Directory that reinforces security measures.
We will cover each element to provide you with a comprehensive understanding of how Azure AD handles authentication and authorisation processes.
Authentication Methods in Azure Active Directory
Azure Active Directory supports various authentication methods, including passkeys, SMS-based authentication and temporary access passes. Administrators have the flexibility to enable specific methods for different users.
By customising their Azure Active Directory authentication settings, organisations can ensure a balance between security and usability, and certificate-based authentication configuration as desired.
Azure Active Directory Token System
Azure Active Directory issues two different tokens when you log in to your account: an access token and a refresh token.
An access token lasts one hour, while refresh tokens last up without expiration or cancellation by you.
Once an access token expires, its refresh token seamlessly obtains another access token, ensuring uninterrupted session access.
Conditional access policies, combined with Continuous Access Evaluation (CAE), continuously evaluate your session for any suspicious activities that may arise during it.
Azure Active Directory will prompt for multi-factor authentication (MFA).
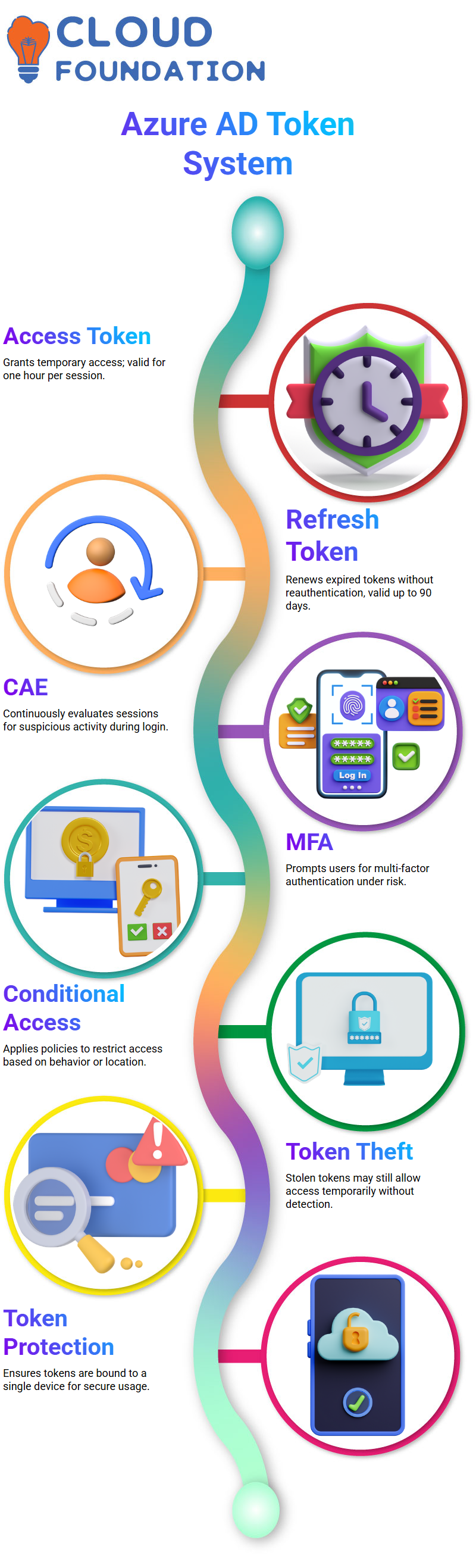
MFA only to have someone steal your laptop and still maintain access to the valid access token. Your administrator might block their identity, but the person could retain access for up to an hour with that token.
CAE would quickly cancel out that privilege when the device moves to an unknown location.
Azure Active Directory’s Token Protection
Azure Active Directory’s token protection ensures that authentication tokens are issued for use only once on one device, protecting users against thieves who steal session cookies or attempt unauthorised logins across different devices.
Azure AD’s security policies continually evolve to reinforce authentication integrity.
Federation and Claims in Azure Active Directory
Federation in Azure Active Directory works similarly to other identity providers, with additional layers of protection.
When users request access to applications through Azure AD, Azure verifies them, retrieves any necessary claims, and secures this information before passing it along securely.
Azure Active Directory stands out from similar systems by incorporating its identity service, making authentication smoother and more straightforward.
Understanding Azure Active Directory in Multi-Tenant Environments
Azure Active Directory plays an invaluable role in managing identities across tenants.
For instance, when creating service principals for friends’ organisations using Fentra’s Fentra App Store solution, the Fentra team will manage changes locally within each tenant where applications reside and apply them accordingly; thereafter, you’ll witness this change within your tenant as well.
Single-tenant applications are designed for your exclusive use, whereas multi-tenant apps offer broader access.
Anyone can access them, depending on the permissions granted based on Azure Active Directory’s permissions system. These accounts include those associated with organisations as well as personal Microsoft accounts.
Multi-Tenant Applications in Azure Active Directory
Azure Active Directory features multi-tenant capabilities that enable applications to be shared among multiple organisations.
Administrators can share an app ID among tenants to allow them to set up service principals and integrate the application within their environment.
 However, configuration changes for shared applications must only be made by their original owner within their tenant to maintain centralisation and prevent unwarranted modifications from being implemented.
However, configuration changes for shared applications must only be made by their original owner within their tenant to maintain centralisation and prevent unwarranted modifications from being implemented.
Azure Active Directory Conditional Access
Azure Active Directory’s conditional access functionality enables users to access applications securely.
When users flagged as medium risk are approved for access, additional authentication layers, such as multi-factor authentication (MFA), will be necessary before granting access.
This process ensures Azure Active Directory’s identity verification mechanism remains reliable.
Azure Active Directory enables client application configuration that meets compliance with security policies and risk levels, with additional authentication layers established as needed for access.
Conditional Access with Azure Active Directory
Azure Active Directory enables organisations to tailor conditional access policies based on user location, device compliance, and risk factors.
Travelling employees often access corporate resources outside the company network, without taking into account MFA enforcement, which factor could create unnecessary authentication challenges for these employees.
Azure Active Directory allows administrators to exclude trusted locations from strict multi-factor authentication (MFA) enforcement.
Currently, Azure Active Directory’s Continuous Access Evaluation feature is in preview, offering enhanced protection for specific applications.
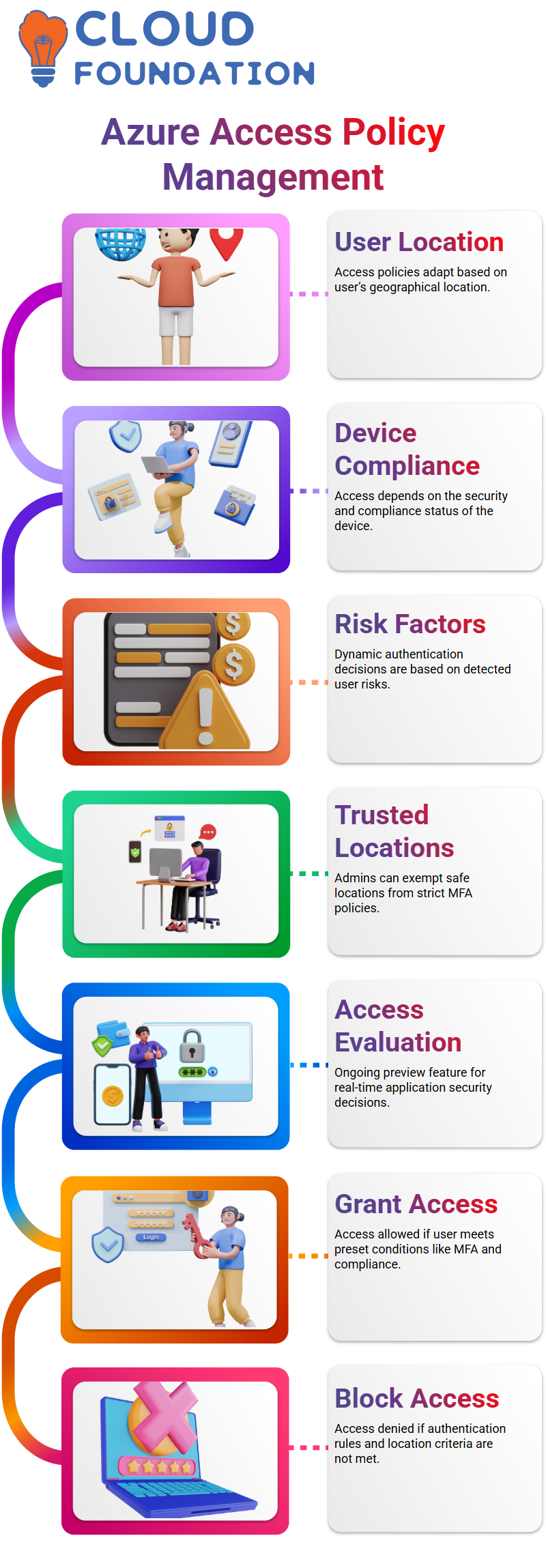
Microsoft plans to further expand this capability as part of its identity protection strategies.
Grant and Block Access in Azure Active Directory
Azure Active Directory features two primary options for user management: Grant and Block.
If certain conditions are not fulfilled, such as users in locations that don’t meet authentication requirements, access can be denied to that user, and the block function takes action accordingly.
The Grant function works differently. If users meet specific conditions, access is granted; however, additional requirements such as multi-factor authentication (MFA) or device compliance must first be fulfilled.
Azure Active Directory ensures that authentication strength, hybrid device settings, and approved client applications are enforced to enhance security.
Control Features in Azure Active Directory
Control plays a crucial part in Azure Active Directory authentication. Organisations can set policies that restrict employees from downloading company data onto personal devices, helping avoid unapproved access or leakage of sensitive company info.
Azure Active Directory monitors sign-in frequency, prompting users to reauthenticate at predefined intervals if an application requires it.
Reauthentication could occur every few hours for especially sensitive apps; persistent browser sessions can also be managed to ensure access isn’t retained even after closing browser tabs.
Continuous Access Evaluation in Azure Active Directory
Continuous Access Evaluation (CAE) in Azure Active Directory is an authentication mechanism that monitors compliance with security policies in real-time, ensuring session integrity to detect and block unauthorised access attempts quickly.
Azure Active Directory continually evaluates access permissions to ensure that authentication rules are enforced, even during active sessions—an exemplary measure for improving security by discouraging unauthorised log-in attempts and compromised credentials.
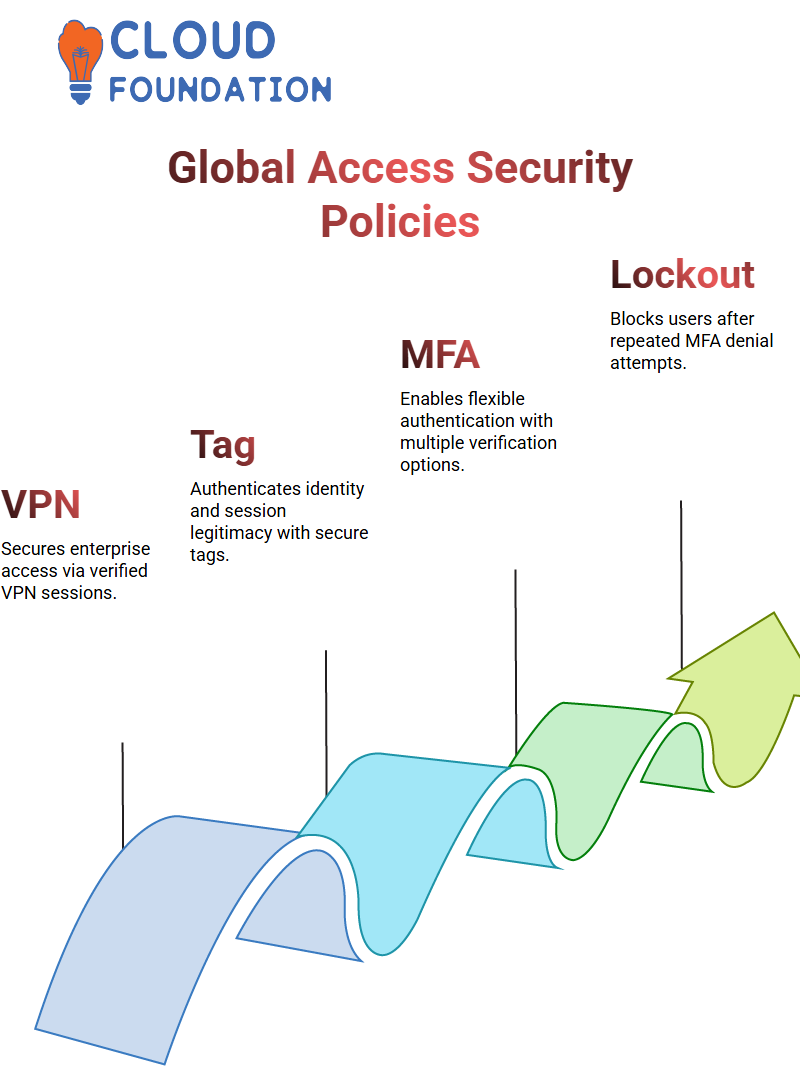
Global Secure Access with Azure Active Directory
Organisations employing Virtual Private Networks (VPNs) can utilise Azure Active Directory’s Global Secure Access policy to protect access through VPN tunnels by verifying whether each session meets legitimacy and security compliance criteria.
A secure tunnel allows access to enterprise applications; Azure Active Directory ensures its integrity by monitoring whether all VPN connections can be trusted.
Each VPN session receives a Global Secure Access tag to authenticate user identity, device legitimacy, and session security, similar to how Amazon verifies the legitimacy of its trusted orders.
At the same time, Azure Active Directory serves as a verification stamp, confirming authenticated sessions that enhance enterprise security.
Multi-Factor Authentication in Azure Active Directory
Azure Active Directory makes Multi-Factor Authentication accessible for organisations of any size. Administrators can configure policies to limit authentication to Microsoft Authenticator or provide multiple solutions.
Azure Active Directory’s account lockout settings help prevent unapproved access. If a user repeatedly denies MFA prompts, their account may be flagged for security concerns and become locked out for their safety.
Multifactor Authentication Policies in Azure Active Directory
Azure Active Directory simplifies Multi-Factor Authentication registration by requiring authentication setup during the first login.
If an organisation mandates that users configure MFA upon account creation, Azure AD removes the option to “Skip for now,” ensuring that every user registers an authentication method – be it Microsoft Authenticator, Google Duo, or third-party solutions like these.
The MFA policy also supports numerous apps like these. Administrators can customise Azure Active Directory enrollment policies with specific authentication apps to ensure uniform security measures throughout their organisation.
Fraud Prevention with Azure Active Directory
PowerShell provides an effective means for administrators to interact with Azure Active Directory. By installing necessary modules and running specific commands, administrators can effortlessly manage identity services with this technique.
As an example, using the command ‘Connect-AzureAD’ prompts for global admin credentials to provide access to Azure Active Directory management tools.

Vinitha Indhukuri
Author



