How Saviynt Prevents Access Violations with Automated Workflows
Saviynt’s Role in Automated HR Systems
Saviynt utilises its HR application, with workflows configured specifically to examine access requests against policies.
If it submits two different invoice creation and approval requests simultaneously, Saviynt evaluates them separately and accepts or declines them accordingly.
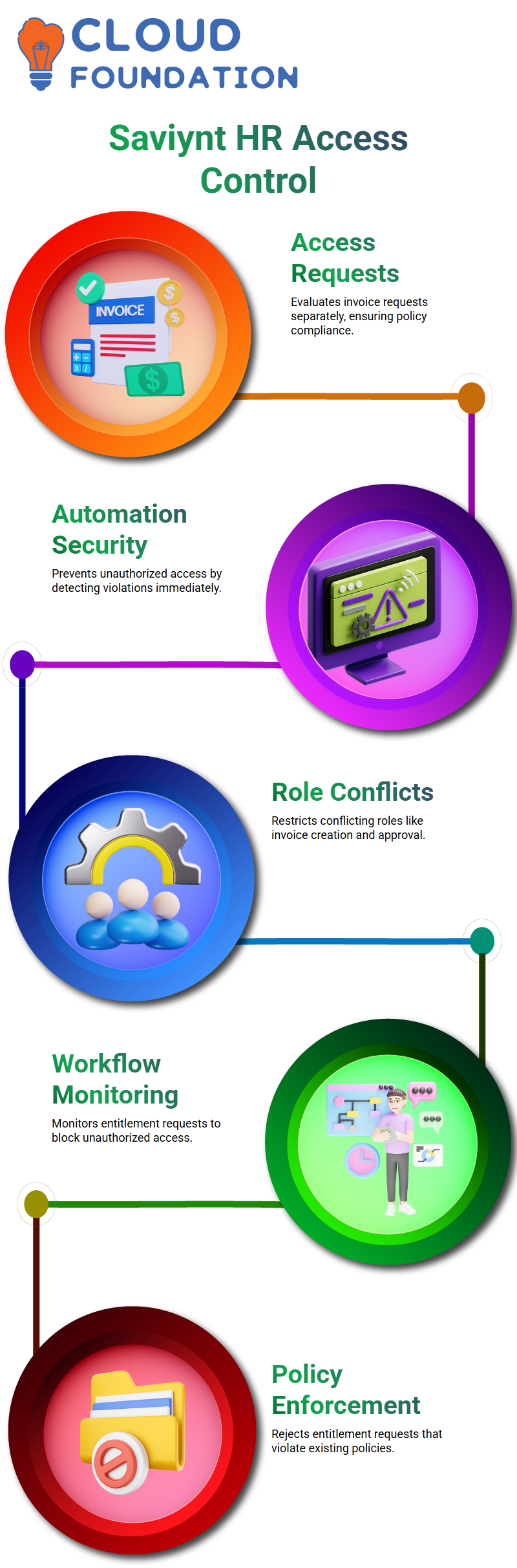
Saviynt stands out in its automation: as soon as an employee submits a request, its workflow checks for violations immediately, safeguarding organisations against financial or operational risks by protecting against employees exploiting Saviynt to gain unauthorised access to their system.
How Saviynt Prevents Access Violations
Saviynt ensures that no single user can simultaneously occupy conflicting roles, such as creating and approving invoices, by using workflows to monitor entitlement requests and prevent any violations before they occur.
When someone applies for one entitlement, such as creating invoices, Saviynt automatically prevents them from accessing another entitlement, such as approving invoices.
Saviynt provides HR application management that oversees these entitlements to access through the application, as requested by the user through Saviynt.
A workflow evaluates his request against existing entitlement conflicts and automatically rejects any requests that cause conflicts, thereby protecting against potential violations.
Workflow Configuration in Saviynt
Configuring workflows in Saviynt has been an eye-opening experience.
I use workflows to automatically reject requests with conflicting entitlements, a practical approach that ensures compliance from day one.
Saviynt’s workflow quickly assesses my request against predefined rules to detect violations immediately, protecting users against potential risks by rejecting requests that violate those rules.
Saviynt Workflows in Action
Saviynt workflows are specifically designed to identify and stop segregation of duties (SOD) conflicts.
For instance, predefined conditions within workflows enable Saviynt to determine whether any entitlement violates policies. For example, it requests access to both HR Floor and Manager Floor roles simultaneously, Saviynt identifies and rejects such requests immediately due to SOD conflicts.
Saviynt workflow relies heavily on attributes such as roles, risks, and entitlements to facilitate this goal. Functions have been established that map these entitlements and ensure compliance.
For instance, the HR Floor role may be associated with one function, while the Manager Floor role is associated with another.
Saviynt then evaluates requests against these functions to detect risks quickly and mitigate them effectively.
Exploring Saviynt Flow Management
Saviynt Managing flows within Saviynt is one of my greatest passions.
Using flow ratios and flow managers is particularly engaging, as this allows users to easily attach these flows to risks seamlessly.
Name risks appropriately (for instance ‘Active Directory Risk”). Once defined, these risks must then be linked with rules called rule sets.
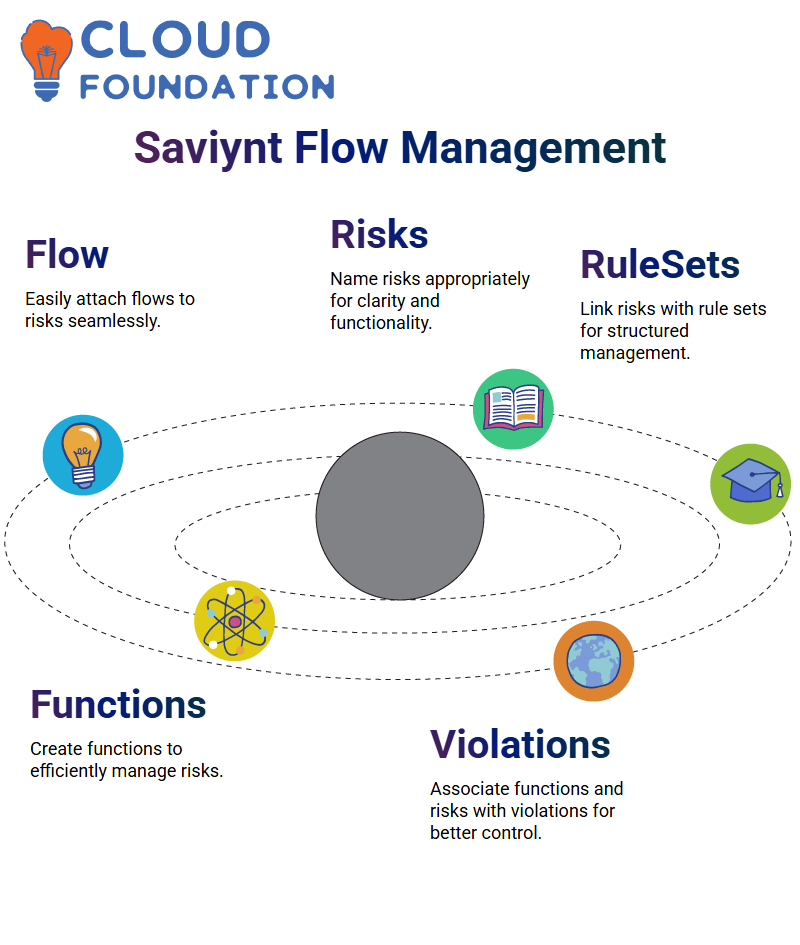 To create them successfully in Saviynt, their association must be clear and functional.
To create them successfully in Saviynt, their association must be clear and functional.
Attaching Functions to Risks in Saviynt
Saviynt functions play an essential part. I begin by creating two functions: Function One and Function Two. Both functions directly relate to risks for developing an efficient framework.
By associating these functions and their risks with Saviynt violations, we can more efficiently and effectively manage them.
Saviynt’s Rule Sets and Violation Handling
Rule sets are vital tools in Saviynt for managing and mitigating risks, so I attach specific rule sets directly to particular dangers for compliance purposes.
One such example of a risk-attached rule set can be observed when examining the Active Directory Demo.
The value of developing workflows is an indispensable way to oversee violations at Saviynt.
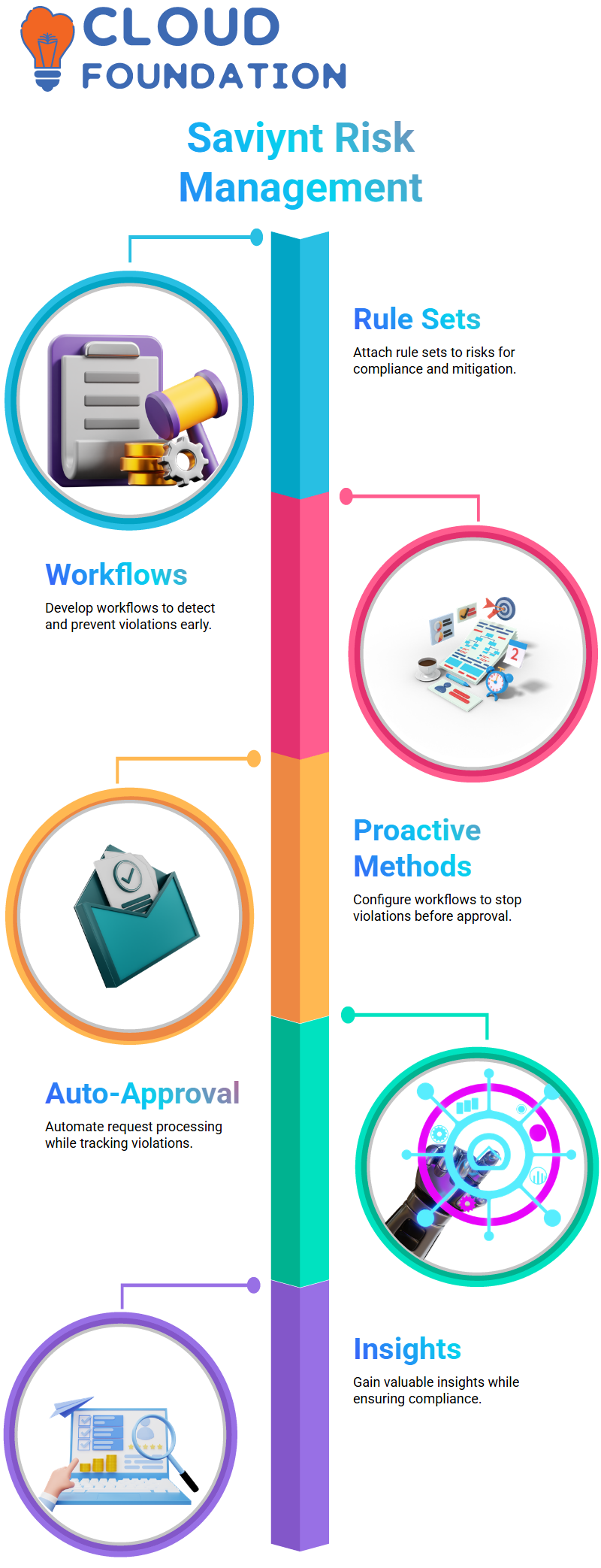
By establishing these processes, I can detect and prevent potential infractions before they escalate further.
Proactive and Detective Methods in Saviynt
Saviynt offers both proactive and reactive risk mitigation. By configuring workflows for proactive prevention, I ensure violations are identified before approval processes even commence.
Saviynt enables workflows set for auto-approval to process requests, while highlighting any violations and providing valuable insights, thereby tracking noncompliance.
This approach provides me with valuable insights while ensuring compliance.
Managing User Access in Saviynt
Saviynt is an efficient tool designed to simplify identity management and access control, enabling the effective detection of user access or entitlement violations.
Saviynt provides an effortless means of tracking down any violations of existing entitlements or those coming up short due to inadequate permission levels, without breaking a sweat.
A user in Saviynt encounters a violation caused by conflicting entitlements. Addressing it should be easy to navigate to their account application, open their demo, and verify their entitlements.
Detecting Violations in Saviynt
Saviynt makes violation detection seamless. Simply scrolling through a study model reveals risks and entitlement clashes for easy analysis.
Should users possess conflicting access, Saviynt will immediately flag this as an unauthorised action and notify administrators to address it promptly.
To investigate further, open your violation report in Saviynt and view its insights regarding risk, entitlement, and function associated with each issue, making decision-making much more accurate and efficient.
Mitigating Risks in Saviynt
Saviynt makes eliminating violations simple. Select an entitlement that needs to be rectified through its remediation feature and click to activate this change.
Once confirmed, Saviynt automatically generates the removal task.
Once a task appears in your Pending section, it’s time to process it through the Provisioning Job Panel.
 Click “Start Job,” submit your task, and let Saviynt do its magic – conflicting access is now resolved instantly.
Click “Start Job,” submit your task, and let Saviynt do its magic – conflicting access is now resolved instantly.
Understanding Query Structure in Saviynt
Saviynt’s reporting system relies on structured queries to access relevant identity data.
The process involves accessing multiple tables, including user, account, and relationship tables, to ensure accurate results.
By leveraging Saviynt’s query engine, administrators can efficiently and securely manage identity governance by identifying active users, resolving entitlement conflicts, and streamlining account provisioning processes. This ensures efficient identity governance practices.
Analysing Reports in Saviynt
Saviynt analytics reports are invaluable tools for organisations managing large-scale identity management programs.
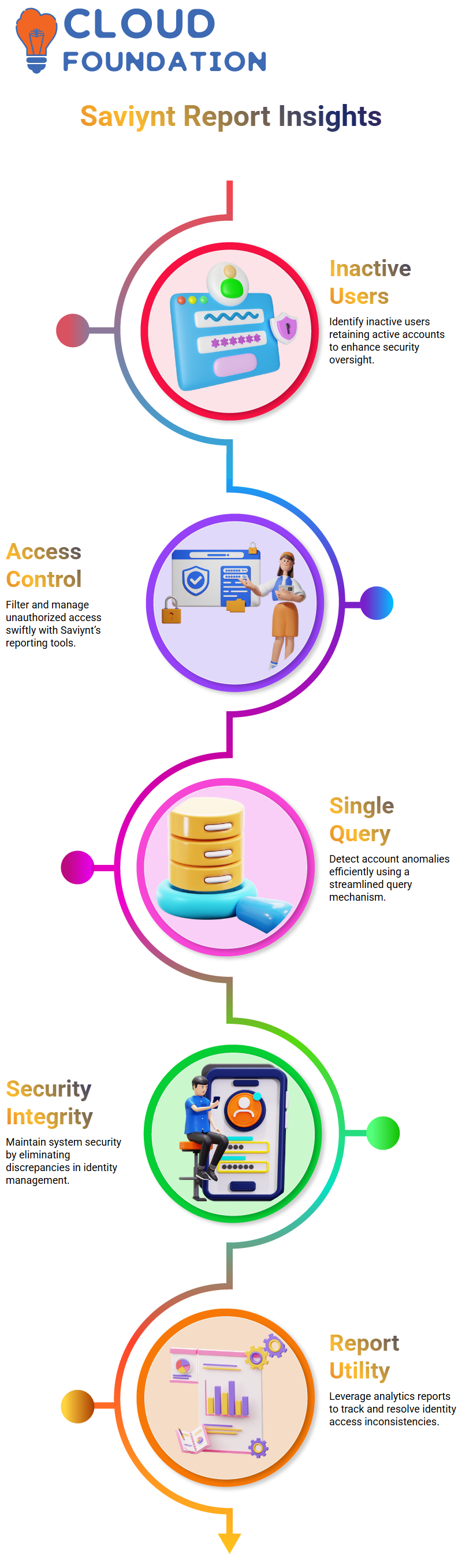
Have you ever wondered which of your inactive users still have active accounts? Saviynt’s reports offer vital insight to track and address such discrepancies effectively.
Saviynt enables administrators to quickly filter and identify inactive users with active accounts using a single query, thereby maintaining security integrity by eliminating unauthorised access within the system.

Vinitha Indhukuri
Author



